TEE学习(二) ARMv8的虚拟化
TEE学习(二) Armv8 虚拟化
KVM
-
Kernel-based Virtual Machine(KVM),内建于Linux中的虚拟化技术,KVM可将Linux转变为
hypervisor,使主机计算机能够运行多个隔离的虚拟环境(VM)。KVM是Linux内核的一部分,每个VM都像普通的Linux进程一样实现,由Linux调度程序进行调度。 -
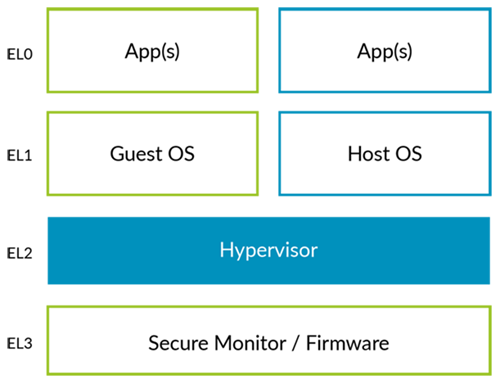
KVM是一种硬件虚拟化方法(处理器本身提供能力来让客户机指令独立运行),相当于内核中的虚拟机,实现对CPU和内存的虚拟化。KVM是type2 hypervisor。
type1 hypervisor: 直接控制硬件资源和客户机;没有宿主OS;
type2 hypervisor: Hypervisor运行在宿主机操作系统之上,Hypervisor只是宿主机操作系统的一个应用程序;宿主OS完全控制硬件和资源(CPU,内存等)。
- full virtualization: emulates a real physical machine.
- para-virtualization: core parts of the Guest OS are modified to operate on a virtual hardware platform instead of a physical machine / hardware support for virtualization, the Guest OS runs mostly unmodified.
KVM-Qemu
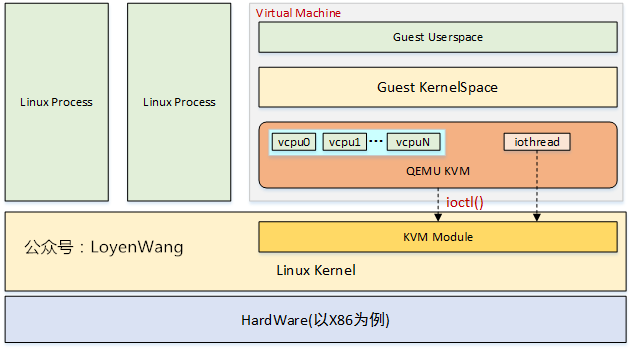
- Qemu是虚拟化的用户态部分,有模拟器和虚拟机两种模式;为每个VM虚拟机创建一个线程,针对每个vCPU创建一个线程,Guest OS/应用运行在vCPU上;模拟I/O功能。
- KVM是内核模块,初始化CPU硬件,打开虚拟化模式;通常不负责I/O。
ARMv8 virtruliazation
stage 2 translation
Stage 2 translation allows a hypervisor to control a view of memory in a Virtual Machine (VM). Specifically, it allows the hypervisor to control which memory-mapped system resources a VM can access, and where those resources appear in the address space of the VM.
Stage 2 translation can be used to ensure that a VM can only see the resources that are allocated to it, and not the resources that are allocated to other VMs or the hypervisor.
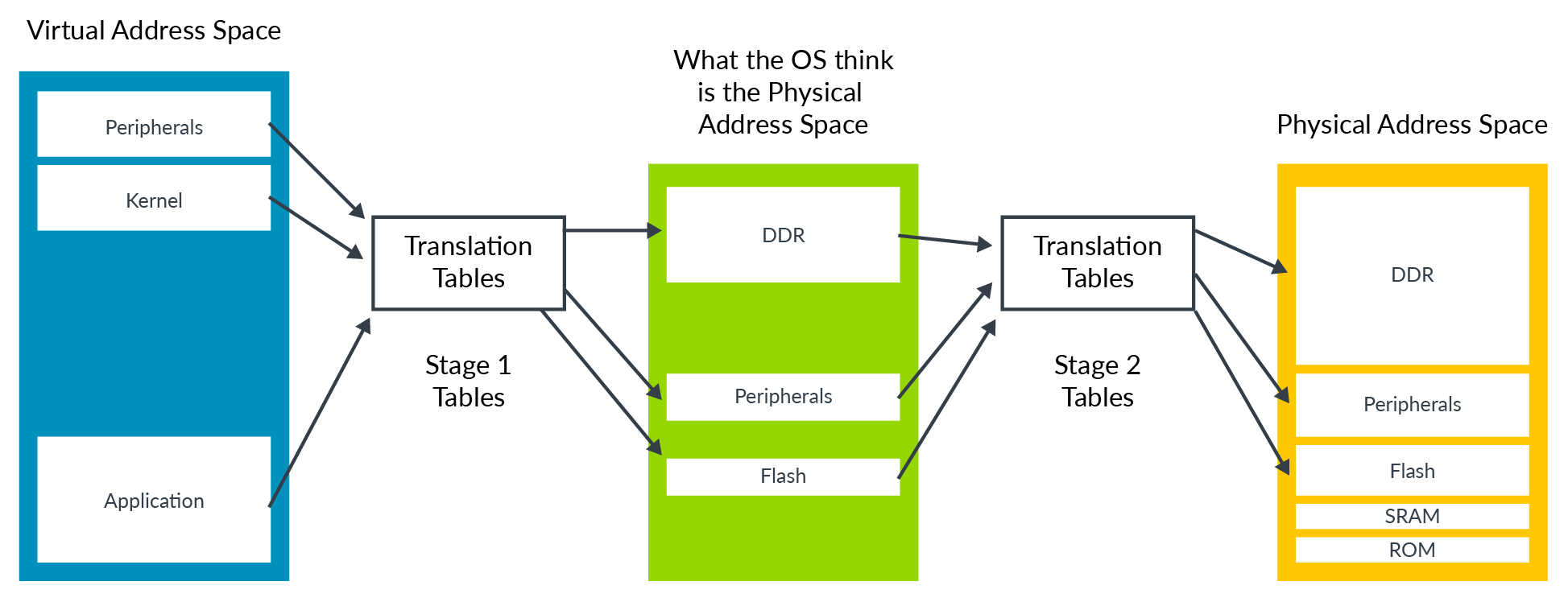
The OS-controlled translation is called stage 1 translation, and the hypervisor-controlled translation is called stage 2 translation. The address space that the OS thinks is physical memory is referred to as the Intermediate Physical Address (IPA) space.
A virtual peripheral is one that the hypervisor is going to emulate in software. The corresponding stage 2 table entries would be marked as fault, and the hypervisor emulating the peripheral access in the exception handler.
模拟外设需要知道:被访问外设 + 外设访问的寄存器 + 访问类型(读/写) + 访问大小 + 转化数据寄存器
FAR_ELx registers: When dealing with stage 1 faults, these registers report the virtual address that triggered the exception.
HPFAR_EL2 register: For stage 2 faults, it reports the IPA of the address that aborted.
ESR_ELx registers: **For single general-purpose register **loads or stores that trigger a stage 2 fault, additional syndrome information is provided. This information includes the size of the accesses and the source or destination register, and allows a hypervisor to determine the type of access that is being made to the virtual peripheral.
SUMMARY: HPFAR_EL2 reports the IPA, know the peripheral registers to emulate -> ESR_ELx registers report the size, destination register, type of access(该寄存器仅在有通用寄存器装载的模拟中被使用!) -> emulate the operation -> return to vCPU.
As for DMA,we use sMMU.The hypervisor would be responsible for programming the SMMU, so DMA sees the same view of memory as the VM to which it is assigned.
- sMMU解决了Guest OS看到的是IPA,但是DMA看到的是PA的问题.
- DMA是指外部设备不通过CPU而直接与系统内存交换数据的接口技术。在DMA方式时,CPU把这些总线让出来,即CPU连到这些总线上的线处于第三态(高阻状态),而由DMA控制器接管.
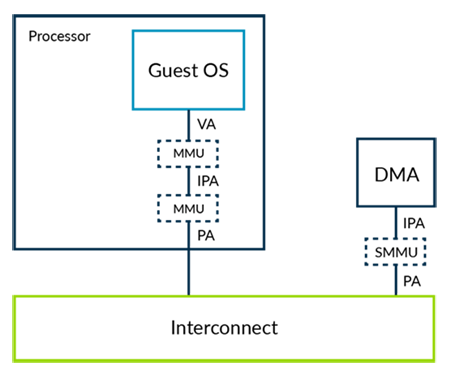
The SMMU can enforce the isolation between VMs, ensuring that external masters cannot be used to breach the sandbox. The SMMU also gives a consistent view of memory to software in the VM and the external masters allocated to the VM.
Trapping and emulation of instructions
VM --trap-> Hepervisor(EL2) --emulate--> operation --> return
Virtualizing exceptions
- interrupt: handled by hypervisor/software within VM.
- Enabling virtual interrupts:To signal virtual interrupts to EL0/1, a hypervisor must set the corresponding routing bit in HCR_EL2.
需要将物理中断发送到EL2,将虚拟中断转发到EL1(VM中)。
-
generating virtual interrupts:
-
by the core, using controls in HCR_EL2: asserting an interrupt signal(VI/VF/VSE) into the vCPU.
controlled by hypervisor -
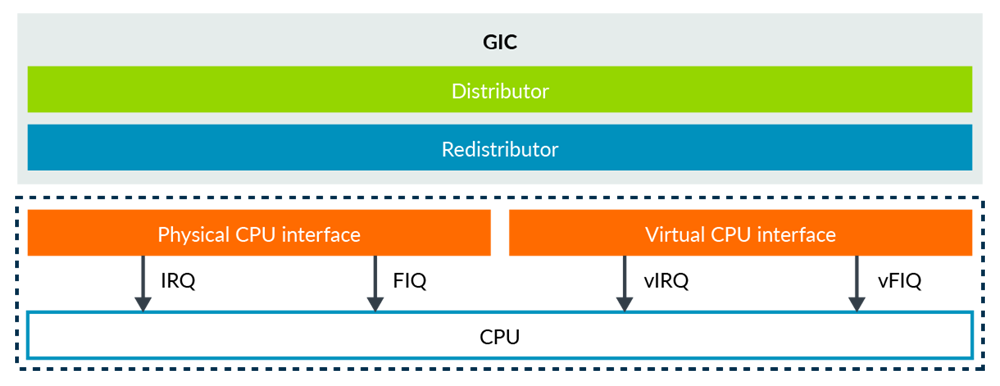
Using a GICv2, interrupt controller: providing a physical CPU interface and a virtual CPU interface.
The hypervisor can map the virtual CPU interface into a VM, allowing software in that VM to communicate directly with the GIC.![img]()
physical peripheral --interrupt signal-> GIC -- physical interrupt -> EL2(hypervisor) --configure-> GIC --virtual interrupt-> vCPU(EL0/1)
-
-
HCR_EL2.IMO: (1) Routes physical IRQs to EL2; (2) Enables signaling of vIRQs in EL0 and EL1.
Virtualizing the generic timers
Software running on a vCPU has access to two timers: (1) EL1 Physical Timer; (2) EL1 Virtual Timer.
EL1物理时钟使用wall-clock time,EL1虚拟时钟和虚拟计数器比较。虚拟计数器是在物理计数器的基础上减去一个偏移。Hypervisor负责为当前调度运行的vCPU指定对应的偏移寄存器。
Physical count - offset = virtual count
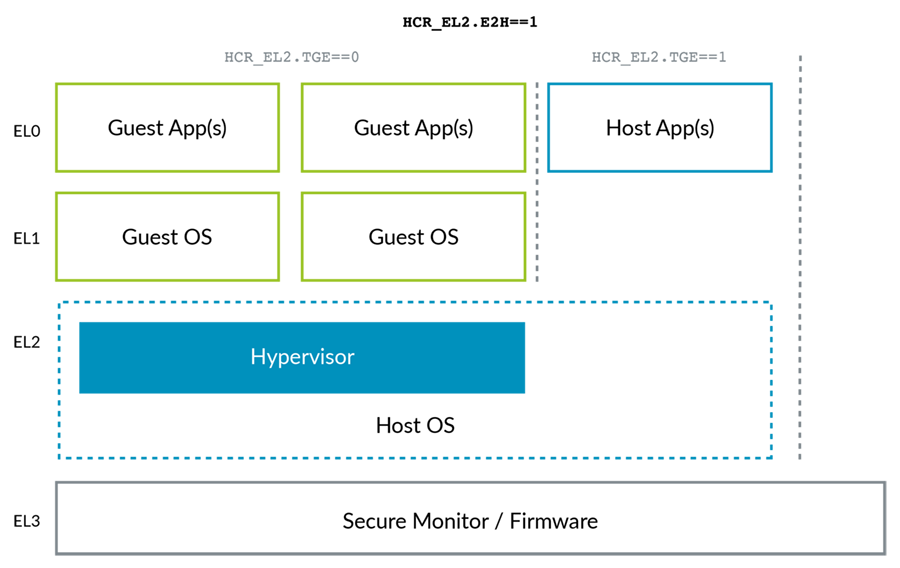
Virtualization host extensions
-
type2 hypervisor:
![img]()
Traditionally,
kernels run at EL1, but the virtualization controls are in EL2. VHE support the kernel of host OS running on EL2.HCR_EL2![img]()
-
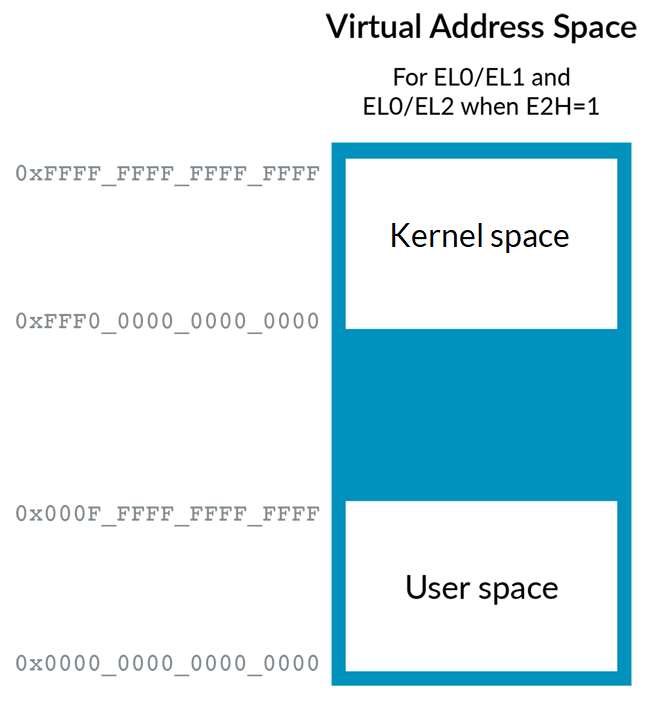
To allow our Host OS to execute efficiently in EL2, we need to add the second region and ASID support. HCR_EL2.E2H
![img]()
-
Re-directing register accesses: 将EL1的寄存器重定向到EL2.设置ECH
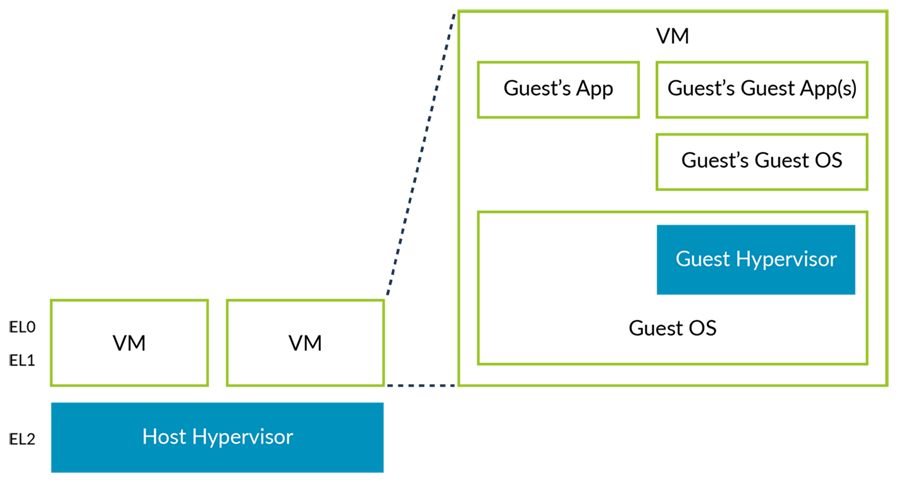
Nested virtualization
-
a hypervisor can be run within a virtual machine (VM).
![img]()
-
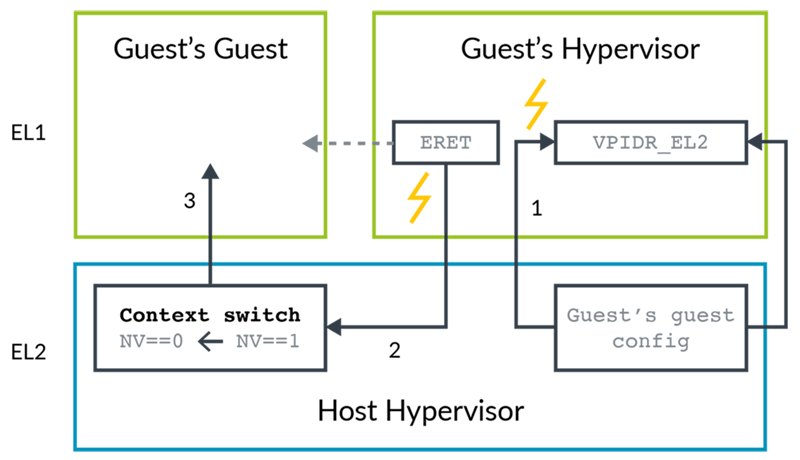
Guest Hypervisors run at EL1. New controls in HCR_EL2 allow the Host Hypervisor to trap the attempts of the Guest Hypervisor to access the virtualization controls.
-
a Guest Hypervisor setting up and entering a VM:
![img]()
Secure virtualization
-
support for EL2 in Secure state,enables use of the
virtualization features in Secure state. -
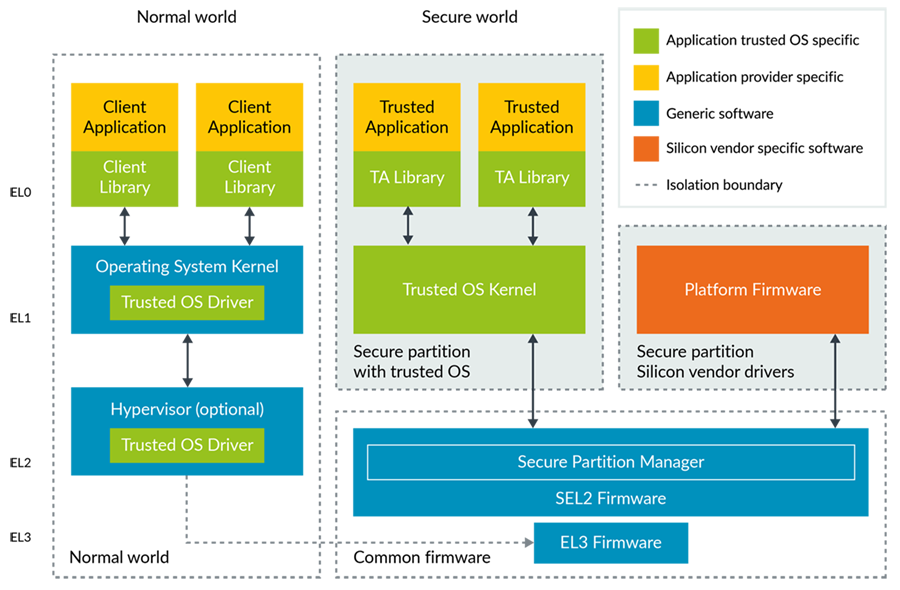
Secure virtualization allows us to move the platform firmware into
EL1. Virtualization provides separate secure partitions for the platform firmware and trusted kernels.![img]()
-
In
Non-secure state, the output of the stage 1 translation of a virtual machine (VM) is always Non-secure; InSecure state, the stage 1 translation of a VM can output both Secure and Non-secure addresses ->there are two IPA spaces for stage 2, Secure and Non-secure(NS bit).There is no NS bit in the stage 2 table entries.
For a particular IPA space, all translations result in either a Secure Physical Address or a Non-secure Physical Address.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号