2019红帽杯ctf-reverse-easyRe
一道很奇怪的题目
先拖进ida分析,然后发现先检验了长度和输入,输入经过异或后和字符串进行比较
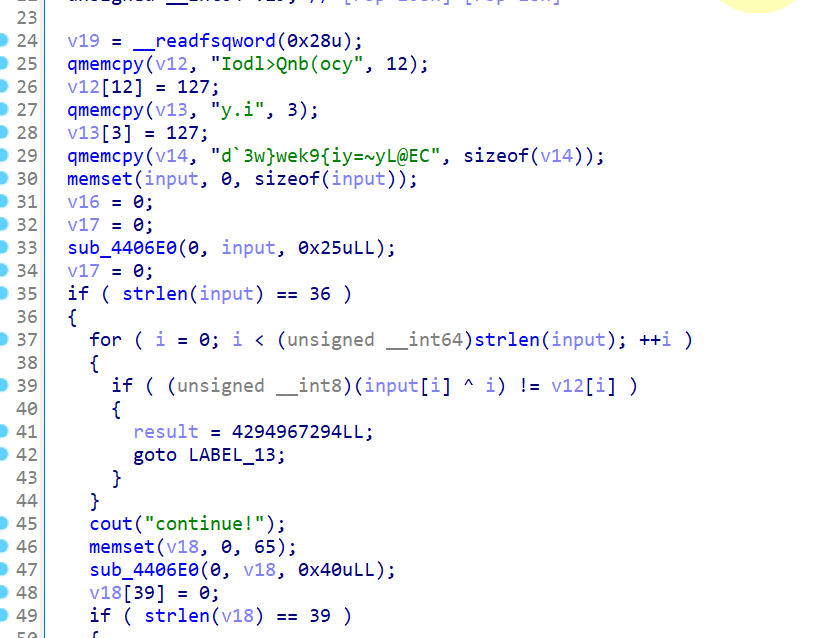
先用脚本跑出来
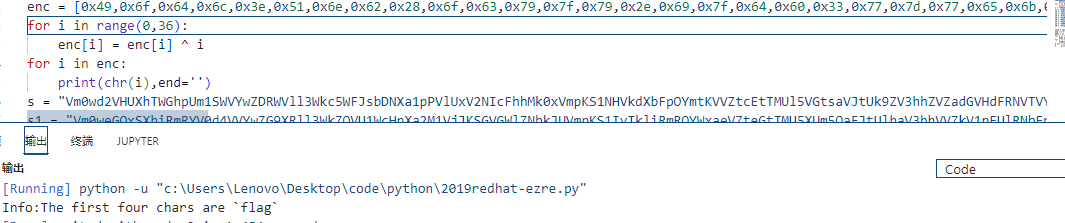
跑出来是一句提示,前四个字符是flag
不太理解什么意思,接着往后看
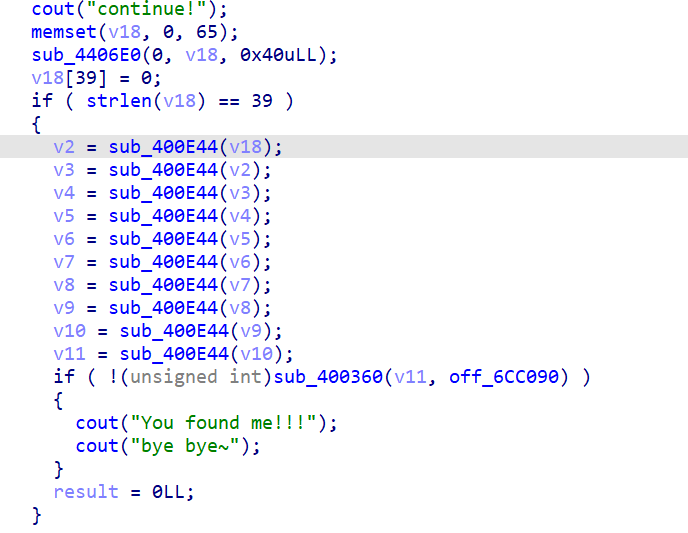
发现后面是一堆base64的处理,经过几次解码之后,得到
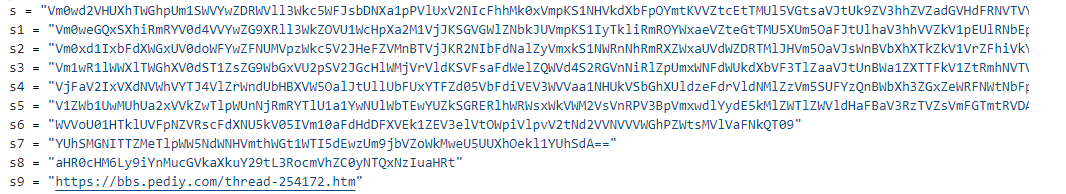
得到了看雪的一篇文章????
后来又在base64字符串附近找了找,发现了另一个数组,找到了另一个函数
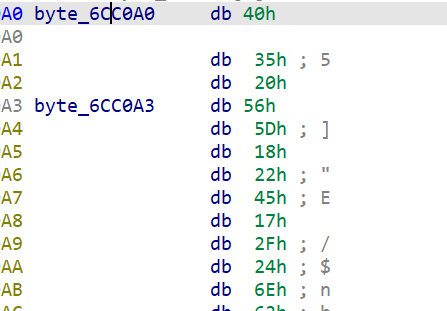
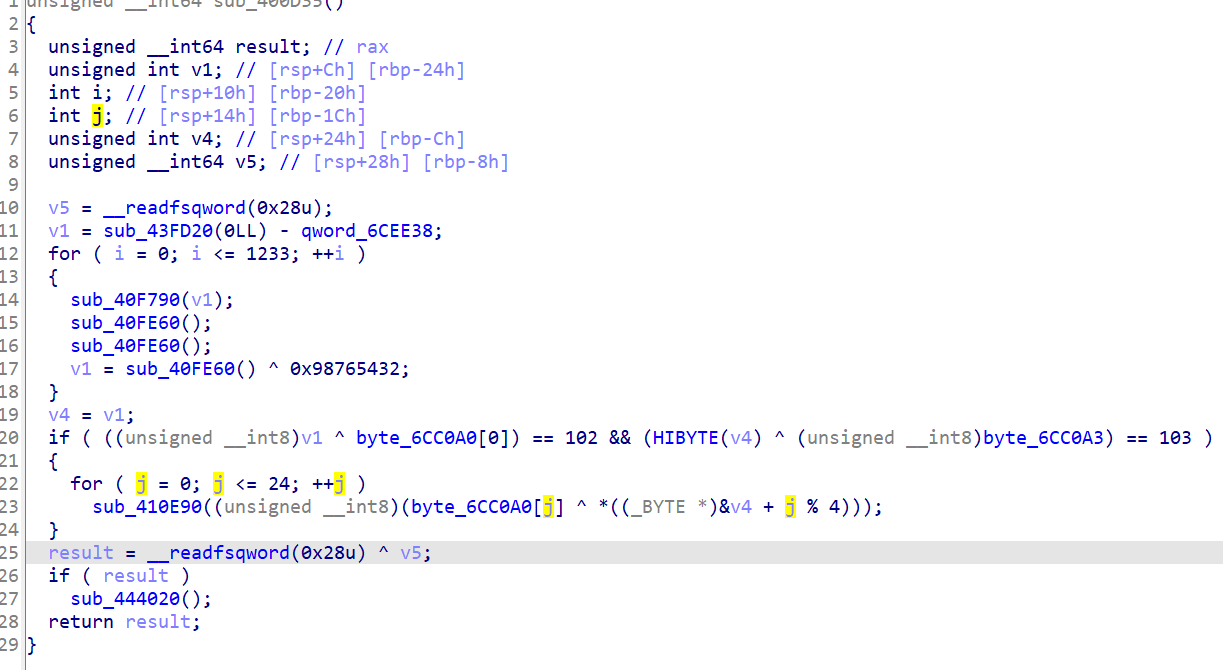
在校验的地方,把数组和异或后的结果跟‘f’和‘g’做了比较
大致就能推测出这里是关键点,根据前面的那句提示和下面的校验,下面的校验提示解密数组长度为4,而flag的前四个字符是‘flag’,就可以得到解密数组
直接脚本梭
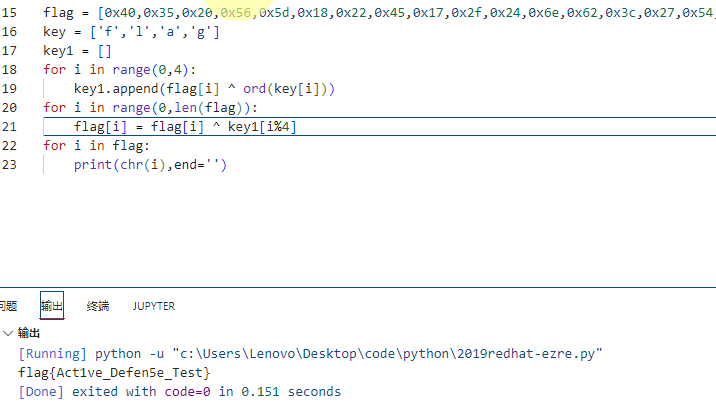
完整代码
enc = [0x49,0x6f,0x64,0x6c,0x3e,0x51,0x6e,0x62,0x28,0x6f,0x63,0x79,0x7f,0x79,0x2e,0x69,0x7f,0x64,0x60,0x33,0x77,0x7d,0x77,0x65,0x6b,0x39,0x7b,0x69,0x79,0x3d,0x7e,0x79,0x4c,0x40,0x45,0x43] for i in range(0,36): enc[i] = enc[i] ^ i s = "Vm0wd2VHUXhTWGhpUm1SWVYwZDRWVll3Wkc5WFJsbDNXa1pPVlUxV2NIcFhhMk0xVmpKS1NHVkdXbFpOYmtKVVZtcEtTMUl5VGtsaVJtUk9ZV3hhZVZadGVHdFRNVTVYVW01T2FGSnRVbGhhVjNoaFZWWmtWMXBFVWxSTmJFcElWbTAxVDJGV1NuTlhia0pXWWxob1dGUnJXbXRXTVZaeVdrWm9hVlpyV1hwV1IzaGhXVmRHVjFOdVVsWmlhMHBZV1ZSR1lWZEdVbFZTYlhSWFRWWndNRlZ0TVc5VWJGcFZWbXR3VjJKSFVYZFdha1pXWlZaT2NtRkhhRk5pVjJoWVYxZDBhMVV3TlhOalJscFlZbGhTY1ZsclduZGxiR1J5VmxSR1ZXSlZjRWhaTUZKaFZqSktWVkZZYUZkV1JWcFlWV3BHYTFkWFRrZFRiV3hvVFVoQ1dsWXhaRFJpTWtsM1RVaG9hbEpYYUhOVmJUVkRZekZhY1ZKcmRGTk5Wa3A2VjJ0U1ExWlhTbFpqUldoYVRVWndkbFpxUmtwbGJVWklZVVprYUdFeGNHOVhXSEJIWkRGS2RGSnJhR2hTYXpWdlZGVm9RMlJzV25STldHUlZUVlpXTlZadE5VOVdiVXBJVld4c1dtSllUWGhXTUZwell6RmFkRkpzVWxOaVNFSktWa1phVTFFeFduUlRhMlJxVWxad1YxWnRlRXRXTVZaSFVsUnNVVlZVTURrPQ==" s1 = "Vm0weGQxSXhiRmRYV0d4VVYwZG9XRll3WkZOVU1WcHpXa2M1VjJKSGVGWlZNbkJUVmpKS1IyTkliRmROYWxaeVZteGtTMU5XUm5OaFJtUlhaV3hhVVZkV1pEUlRNbEpIVm01T2FWSnNXbkJWYlhoWFRrWmtWMVZyWkZoaVZrWXpWR3hhWVdGV1NuUlZia0pYWVRGYVdGUlVSbXRXTVZwMFVtMW9UbFpVVmtwV2JHUXdWakZWZVZOcmFHaFNiV2hYV1d0a1UwNXNjRlpYYlhScVlrWndlbGRyVlRGVWJVcEhZMFJhVjJKVVFYaFdWRVpYVWpGa1dXTkdTbWxoTUhCWlYxZDRiMkl3TUhoalJXaHNVbTVDYzFacVJrdFNNVkp6V2tSQ1ZXSlZjRWhaTUZwdlZqRkplbUZIYUZkaGExcG9XWHBHZDFKdFJraGhSazVvVFVoQ2RsWnRNWGRVTVZWNVZtNU9WbUpIVWxsWmJYTXhWMFpzYzFadFJsUlNiSEJKVkZaU1ExWnRTa2RqUlZwV1ZteEtWMVZHUlRsUVVUMDk=" s2 = "Vm0xd1IxbFdXWGxUV0doWFYwZFNUMVpzWkc5V2JHeFZVMnBTVjJKR2NIbFdNalZyVmxkS1NWRnNhRmRXZWxaUVdWZDRTMlJHVm5OaVJsWnBVbXhXTkZkV1VrZFhiVkYzVGxaYWFWSnRVbkJXYTFaWFRURmtWMVp0Um1oTlZUVkpWbGQwVjFVeVNraGhSbWhXWWtkU05scFZXbXRqYkZweldrVTFUbUpHY0RaV2JUQXhWVEZXUjFkWWNGSmlhMHBZV1d4b2IwMHhjRWhsUm5Cc1ZqRktSMVJzWkRCVWJVcEhZMFpvVjFJemFHaFdha1poWXpGd1JtRkhhRk5oTUhCdlZtMXdUMVV5Vm5OVmJHUllZbXMxV0Zsc1ZtRlRSbHBJVFZSQ1ZtSkdjRVpWVmxKV1VGRTlQUT09" s3 = "Vm1wR1lWWXlTWGhXV0dST1ZsZG9WbGxVU2pSV2JGcHlWMjVrVldKSVFsaFdWelZQWVd4S2RGVnNiRlZpUmxWNFdWUkdXbVF3TlZaaVJtUnBWa1ZXTTFkV1ZtRmhNVTVJVld0V1UySkhhRmhWYkdSNlpVWmtjbFpzWkU1TmJGcDZWbTAxVTFWR1dYcFJia0pYWWxob00xcEhlRnBsVjFKR1RsZDBUbUpHY0ZoV1IzaGhWakZhYzFwRmFHaFNhMHBvVm1wT1UyVnNVbGRYYms1WFlsVmFTRlpITVRCVmJGcEZVVlJWUFE9PQ==" s4 = "VjFaV2IxVXdNVWhVYTJ4VlZrWndUbHBXVW5OalJtUllUbFUxYTFZd05VbFdiVEV3WVVaa1NHUkVSbGhXUldzeFdrVldNMlZzVm5SUFYzQnBWbXh3ZGxZeWRFNWtNbFpXVGxaV1ZsZEhhRkJhVjNSelRWWnNWbUZHVG10UlZEQTU=" s5 = "V1ZWb1UwMUhUa2xVVkZwTlpWUnNjRmRYTlU1a1YwNUlWbTEwYUZkSGRERlhWRWsxWkVWM2VsVnRPV3BpVmxwdlYydE5kMlZWTlZWVldHaFBaV3RzTVZsVmFGTmtRVDA5" s6 = "WVVoU01HTklUVFpNZVRscFdXNU5kV05IVm10aFdHdDFXVEk1ZEV3elVtOWpiVlpvV2tNd2VVNVVVWGhPZWtsMVlVaFNkQT09" s7 = "YUhSMGNITTZMeTlpWW5NdWNHVmthWGt1WTI5dEwzUm9jbVZoWkMweU5UUXhOekl1YUhSdA==" s8 = "aHR0cHM6Ly9iYnMucGVkaXkuY29tL3RocmVhZC0yNTQxNzIuaHRt" s9 = "https://bbs.pediy.com/thread-254172.htm" flag = [0x40,0x35,0x20,0x56,0x5d,0x18,0x22,0x45,0x17,0x2f,0x24,0x6e,0x62,0x3c,0x27,0x54,0x48,0x6c,0x24,0x6e,0x72,0x3c,0x32,0x45,0x5b] key = ['f','l','a','g'] key1 = [] for i in range(0,4): key1.append(flag[i] ^ ord(key[i])) for i in range(0,len(flag)): flag[i] = flag[i] ^ key1[i%4] for i in flag: print(chr(i),end='')




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 三行代码完成国际化适配,妙~啊~
· .NET Core 中如何实现缓存的预热?