xctf-easyvm
xctf的一道逆向,考的vm混淆
先查壳,64位elf,无壳
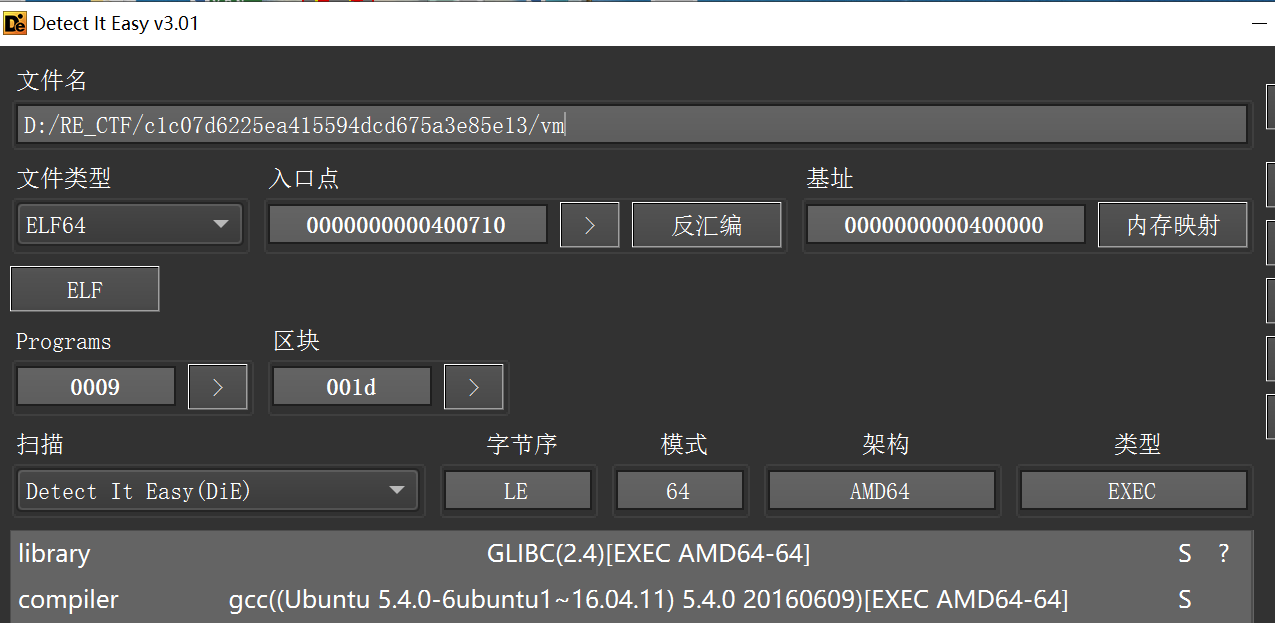
直接拖进ida分析,定位到main函数
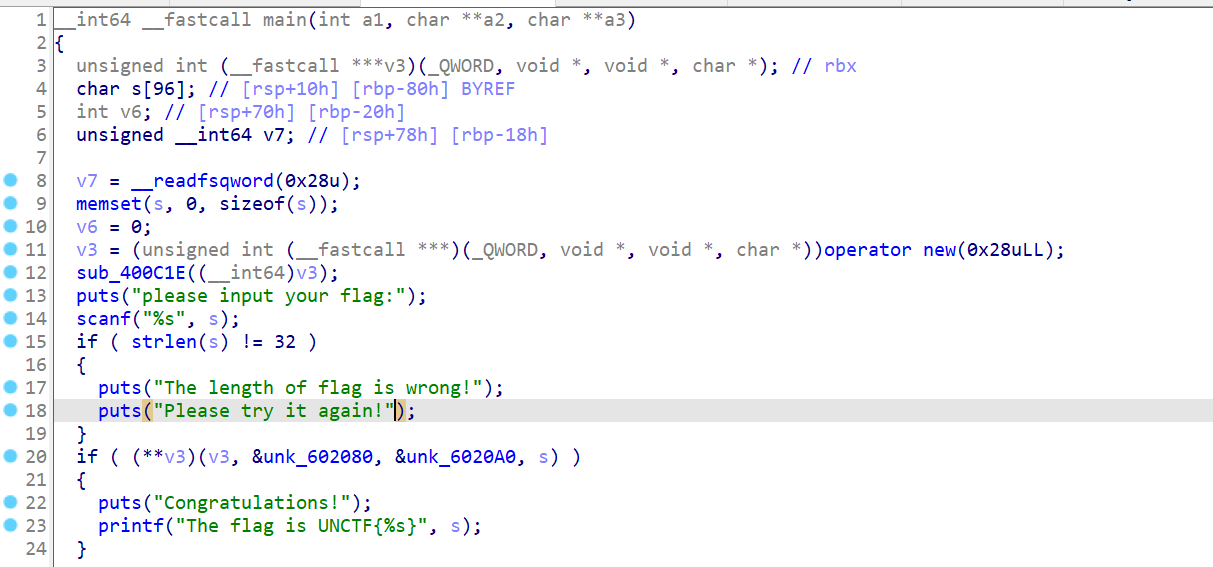
先检测flag长度,然后检验内容
动调跟进函数v3
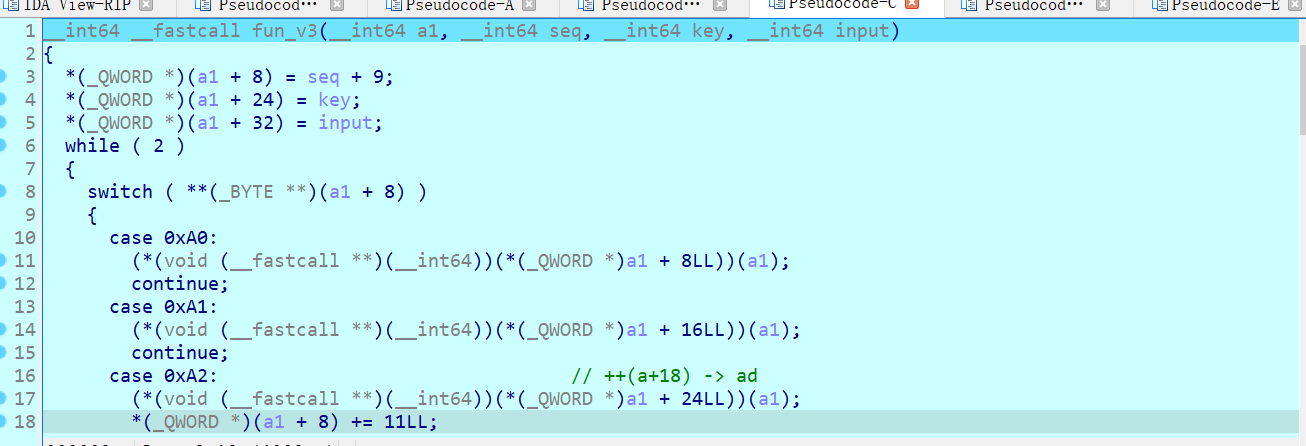
跟进之后发现是vm混淆,混淆比较简单,经过分析,发现执行流程是一个循环,并且只会执行一部分case语句
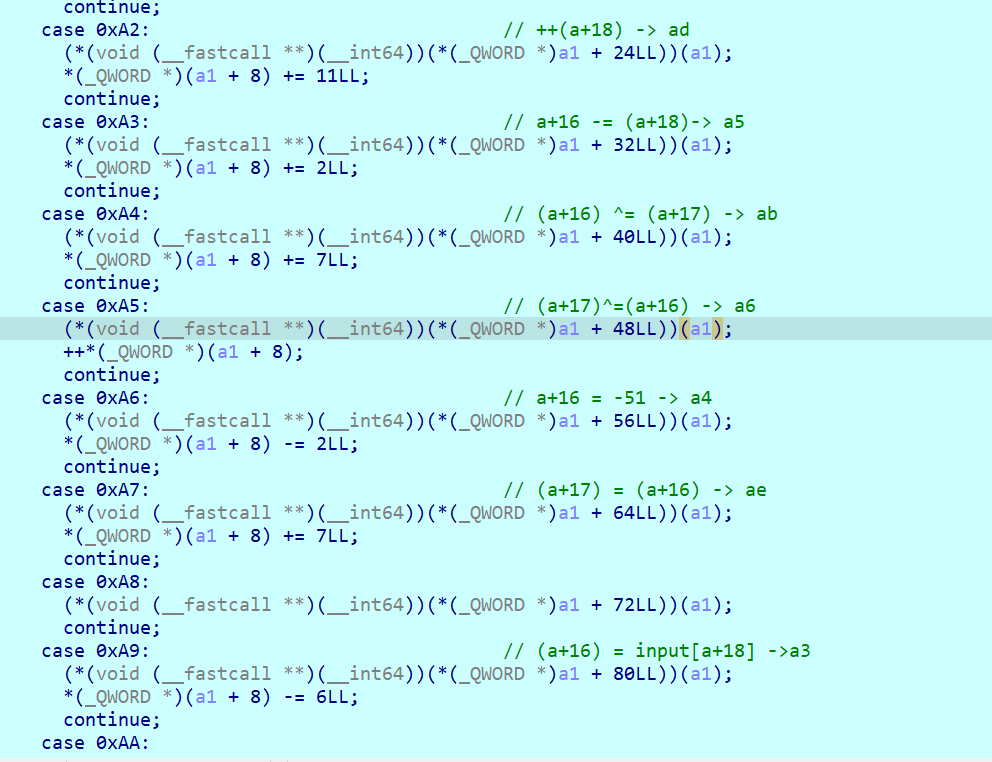
直接写python脚本跑出来就可以了
unk = [0xf4,0xa,0xf7,0x64,0x99,0x78,0x9e,0x7d,0xea,0x7b,0x9e,0x7b,0x9f,0x7e,0xeb,0x71,0xe8,0x0,0xe8,0x7,0x98,0x19,0xf4,0x25,0xf3,0x21,0xa4,0x2f,0xf4,0x2f,0xa6,0x7c] l = [] for i in range(len(unk)-1,-1,-1): tmp = unk[i] tmp ^= 0xcd if (i > 0): tmp ^= unk[i-1] else: tmp ^= 0 tmp += i l.append(tmp) for i in range(len(l)-1,-1,-1): print(chr(l[i]),end='')

