从Java的角度简单修复Cookie越权漏洞
技术实在是有限,讲解cookie越权的时候可能有点简单和粗糙。这里就简单记录学习下。
首先自己写一段存在漏洞的代码code:
sendCookie.java
package cookie; import java.io.IOException; import javax.servlet.ServletException; import javax.servlet.http.Cookie; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; public class SendCookieServlet extends HttpServlet { public void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { //服务器端生成set-cookie Cookie cookie = new Cookie("name", "admin"); //设置cookie存活时间为十分钟 cookie.setMaxAge(60*10); //设置会话cookie允许的路径 //允许整个项目 cookie.setPath("/"); //将cookie中存储的信息发送到客户端---头 response.addCookie(cookie); } public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { doGet(request, response); } }
然后接收cookie中的键值,然后进行判断
GetCookieServlet代码如下:
package cookie; import java.io.IOException; import javax.servlet.ServletException; import javax.servlet.http.Cookie; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; public class GetCookieServlet extends HttpServlet { public void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { // 获取cookie的键值 Cookie[] cookies = request.getCookies(); request.setCharacterEncoding("UTF-8"); response.setContentType("text/html;charset=UTF-8"); String name=null; //判斷cookie不能为空 if (cookies != null) { for (Cookie cookie : cookies) { // 获取键 cookie.getName(); if ("name".equals(cookie.getName())) { name=cookie.getValue(); } } } if(name.equals("admin")) { response.getWriter().write("欢迎admin登陆后台系统"); }else { response.getWriter().write("欢迎xxx登陆后台系统"); } } public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { doGet(request, response); } }
先访问sendCookie然后访问getCookie:
默认是进入admin系统
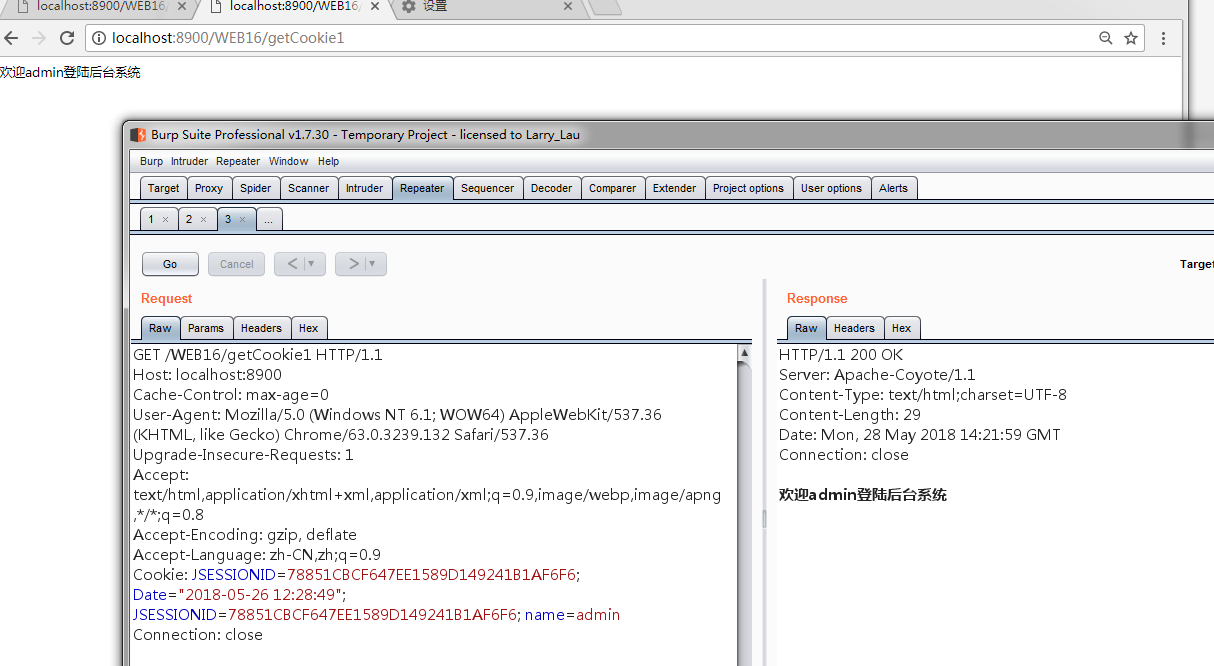
因为cookie中存储的name=admin,这里修复name=其他值
就越权进入了另一个系统
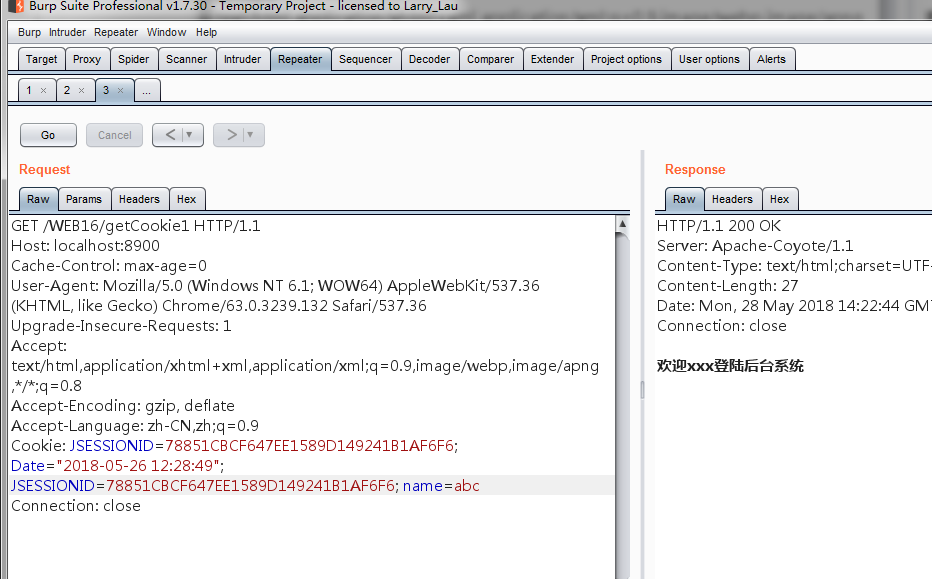
这里的问题就是没有使用session进行敏感信息的存储。
修复方案:验证session的有效性,session和用户是否匹配,以及用户当前权限
这里我把cookie的存储方式改成seesion的存储方式:
代码如下:
sendCookie:
package cookie; import java.io.IOException; import javax.servlet.ServletException; import javax.servlet.http.Cookie; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; import javax.servlet.http.HttpSession; public class SendCookieServlet extends HttpServlet { public void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { HttpSession session = request.getSession(); session.setAttribute("name", "admin"); String id = session.getId(); //服务器端生成set-cookie Cookie cookie = new Cookie("JSESSIONID", id); //设置cookie存活时间为十分钟 cookie.setMaxAge(60*10); //设置会话cookie允许的路径 //允许整个项目 cookie.setPath("/"); //将cookie中存储的信息发送到客户端---头 response.addCookie(cookie); } public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { doGet(request, response); } }
getCookie代码如下:
package cookie; import java.io.IOException; import javax.servlet.ServletException; import javax.servlet.http.Cookie; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; import javax.servlet.http.HttpSession; public class GetCookieServlet extends HttpServlet { public void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { request.setCharacterEncoding("UTF-8"); response.setContentType("text/html;charset=UTF-8"); HttpSession session = request.getSession(); String name = (String) session.getAttribute("name"); if(name.equals("admin")) { response.getWriter().write("欢迎admin登陆后台系统"); }else { response.getWriter().write("欢迎xxx登陆后台系统"); } } public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { doGet(request, response); } }
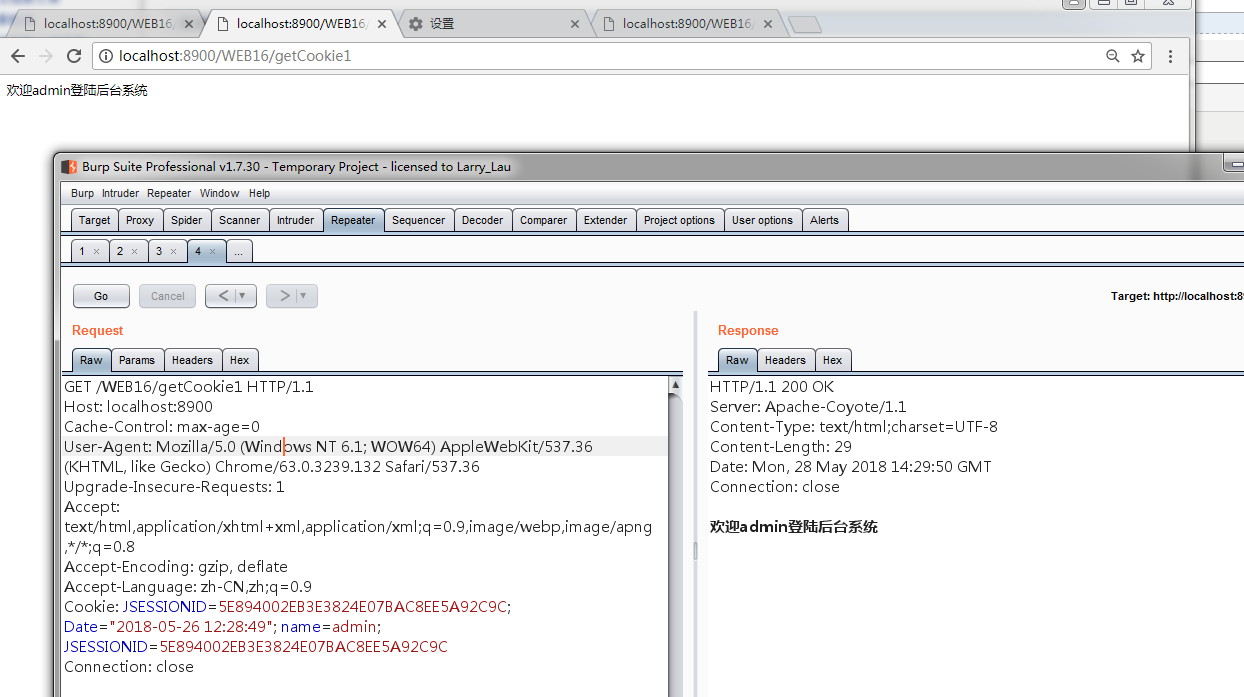
然后访问sendCookie然后再getCookie:
先正常访问:
修改name=其他内容:
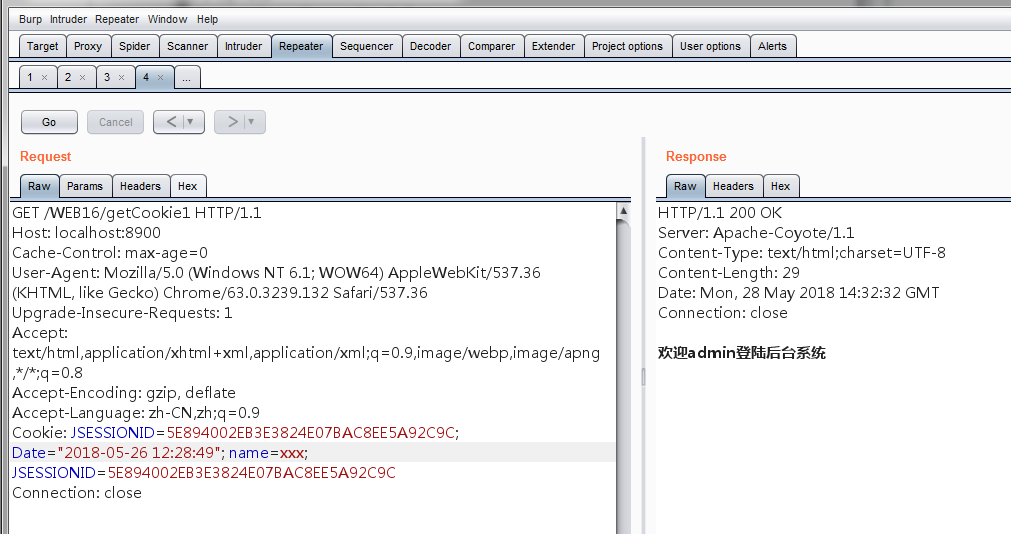
已经无法造成cookie的越权。事实证明使用session存储需要进行操作的数据更安全!
进行判断的时候不要直接用cookie存储。使用Session验证。
不忘初心,方得始终。


