如何通过修改注册表关闭、开启windows10内置Windows Defender安全中心和防火墙
- 注意!注册表改错可能会导致系统异常,改前务必导出注册表并备份。
方法一
1、win+R输入regedit,按回车键进入注册表编辑器。
2、定位到
计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SecurityHealthService

3、在右侧找到Start,修改数值数据为4。
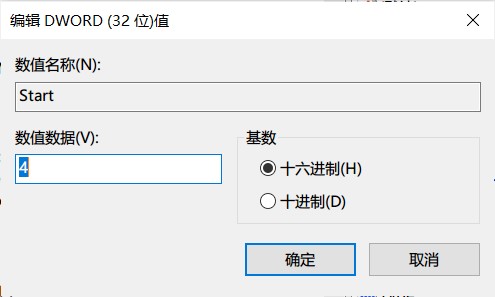
4、注销再登录/重启系统。
5、此时会看到Windows Defender安全中心不再出现,再配合停用Windows Defender,内置安全软件应该就不会打扰到你了。当然,如果你安装第三方杀软或安全软件,Windows Defender会自动被关闭。
6、想要重新开启,按上面方法就找到Start,修改回数值数据为3。
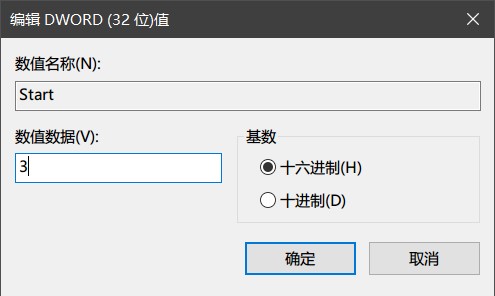
Start的值设置为0,则驱动由启动引导器加载,应该跟“随着开机,最先启动”是同一回事;
Start的值设置为1,则驱动由操作系统的I/O子系统加载,即在系统内核初始化时加载;
Start的值设置为2,则驱动/服务在启动后自动加载;
Start的值设置为3,则驱动/服务就是按需手动加载;
Start的值设置为4,驱动/服务就是被禁用的状态
方法二
1.在桌面左下角搜索框输入cmd,以管理员身份运行命令提示符。
2.输入以下命令,回车后重启。
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /d 1 /t REG_DWORD /f
若需重新启用Windows Defender,以管理员身份运行命令提示符,输入以下命令,回车后重启。
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /d 0 /t REG_DWORD /f
方法三
打开 regedit
显示名称 Windows Defender Firewall 可以且生效
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\mpssvc”将“Start”的值更改为 4 并重新启动服务器。原值为2
显示名称 Windows 安全中心服务 可以且生效
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SecurityHealthService”将“Start”的值更改为 4 并重新启动服务器。原值为2
显示名称 Windows Update 可以且生效
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wuauserv”将“Start”的值更改为 4 并重新启动服务器。原值为3
显示名称 Windows Defender Advanced Threat Protection Service 可以改但不生效
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sense”将“Start”的值更改为 4 并重新启动服务器。原值为3
显示名称 Windows Defender Antivirus Service 可以改但不生效
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SecurityHealthService”将“Start”的值更改为 4 并重新启动服务器。原值为2
显示名称 Windows Defender Antivirus Network Inspection Service 改不了
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisSvc”将“Start”的值更改为 4 并重新启动服务器。原值为3
显示名称 Windows Defender Antivirus Network Inspection System Driver 改不了
转到“计算机\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisDrv”将“Start”的值更改为 4 并重新启动服务器。原值为3
重启后生效!防病毒重启联网后才生效!
方法四
Disable Microsoft Malicious Software Removal Tool.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT]
"DontOfferThroughWUAU"=dword:00000001
Disable Windows Defender.reg
Windows Registry Editor Version 5.00
;Microsoft Defender Antivirus Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WinDefend]
"Start"=dword:00000004
;Microsoft Defender Antivirus Network Inspection Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisSvc]
"Start"=dword:00000004
;Windows Defender Antivirus Network Inspection System Driver
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisDrv]
"Start"=dword:00000004
;Windows Defender Advanced Threat Protection Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sense]
"Start"=dword:00000004
Enable Windows Defender.reg
Windows Registry Editor Version 5.00
;Windows Defender Security Center Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SecurityHealthService]
"Start"=dword:00000002
;Windows Defender Antivirus Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WinDefend]
"Start"=dword:00000002
;Windows Defender Antivirus Network Inspection Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisSvc]
"Start"=dword:00000002
;Windows Defender Antivirus Network Inspection System Driver
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WdNisDrv]
"Start"=dword:00000002
;Windows Defender Advanced Threat Protection Service
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sense]
"Start"=dword:00000002
ToggleDefender.bat
@(set "0=%~f0"^)#) & powershell -win 1 -nop -c iex([io.file]::ReadAllText($env:0)) & exit /b
## Toggle Defender, AveYo 2022.12.30
## changed: comment personal configuration tweaks
sp 'HKCU:\Volatile Environment' 'ToggleDefender' @'
if ($(sc.exe qc windefend) -like '*TOGGLE*') {$TOGGLE=7;$KEEP=6;$A='Enable';$S='OFF'}else{$TOGGLE=6;$KEEP=7;$A='Disable';$S='ON'}
## Comment to hide dialog prompt with Yes, No, Cancel (6,7,2)
if ($env:1 -ne 6 -and $env:1 -ne 7) {
$choice=(new-object -ComObject Wscript.Shell).Popup($A + ' Windows Defender?', 0, 'Defender is: ' + $S, 0x1033)
if ($choice -eq 2) {break} elseif ($choice -eq 6) {$env:1=$TOGGLE} else {$env:1=$KEEP}
}
## Without the dialog prompt above will toggle automatically
if ($env:1 -ne 6 -and $env:1 -ne 7) { $env:1=$TOGGLE }
## Cascade elevation
$u=0;$w=whoami /groups;if($w-like'*1-5-32-544*'){$u=1};if($w-like'*1-16-12288*'){$u=2};if($w-like'*1-16-16384*'){$u=3}
## Comment to not hide per-user toggle notifications
$notif='HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Notifications\Settings\Windows.SystemToast.SecurityAndMaintenance'
ni $notif -ea 0|out-null; ri $notif.replace('Settings','Current') -Recurse -Force -ea 0
sp $notif Enabled 0 -Type Dword -Force -ea 0; if ($TOGGLE -eq 7) {rp $notif Enabled -Force -ea 0}
## Comment to not relaunch systray icon
$L="$env:ProgramFiles\Windows Defender\MSASCuiL.exe"; if (!(test-path $L)) {$L='SecurityHealthSystray'}
if ($u -eq 2) {start $L -win 1}
## Reload from volatile registry as needed
$script='-win 1 -nop -c & {$AveYo='+"'`r`r"+' A LIMITED ACCOUNT PROTECTS YOU FROM UAC EXPLOITS '+"`r`r'"+';$env:1='+$env:1
$script+=';$k=@();$k+=gp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0;iex($k[0].ToggleDefender)}'
$cmd='powershell '+$script; $env:__COMPAT_LAYER='Installer'
## 0: limited-user: must runas / 1: admin-user non-elevated: must runas [built-in lame uac bpass removed]
if ($u -lt 2) {
start powershell -args $script -verb runas -win 1; break
}
## 2: admin-user elevated: get ti/system via runasti lean and mean snippet [$window hide:0x0E080600 show:0x0E080610]
if ($u -eq 2) {
$A=[AppDomain]::CurrentDomain."DefineDynami`cAssembly"(1,1)."DefineDynami`cModule"(1);$D=@();0..5|%{$D+=$A."Defin`eType"('A'+$_,
1179913,[ValueType])} ;4,5|%{$D+=$D[$_]."MakeByR`efType"()} ;$I=[Int32];$J="Int`Ptr";$P=$I.module.GetType("System.$J"); $F=@(0)
$F+=($P,$I,$P),($I,$I,$I,$I,$P,$D[1]),($I,$P,$P,$P,$I,$I,$I,$I,$I,$I,$I,$I,[Int16],[Int16],$P,$P,$P,$P),($D[3],$P),($P,$P,$I,$I)
$S=[String]; $9=$D[0]."DefinePInvok`eMethod"('CreateProcess',"kernel`32",8214,1,$I,@($S,$S,$I,$I,$I,$I,$I,$S,$D[6],$D[7]),1,4)
1..5|%{$k=$_;$n=1;$F[$_]|%{$9=$D[$k]."DefineFie`ld"('f'+$n++,$_,6)}};$T=@();0..5|%{$T+=$D[$_]."CreateT`ype"();$Z=[uintptr]::size
nv ('T'+$_)([Activator]::CreateInstance($T[$_]))}; $H=$I.module.GetType("System.Runtime.Interop`Services.Mar`shal");
$WP=$H."GetMeth`od"("Write$J",[type[]]($J,$J)); $HG=$H."GetMeth`od"("AllocHG`lobal",[type[]]'int32'); $v=$HG.invoke($null,$Z)
'TrustedInstaller','lsass'|%{if(!$pn){net1 start $_ 2>&1 >$null;$pn=[Diagnostics.Process]::GetProcessesByName($_)[0];}}
$WP.invoke($null,@($v,$pn.Handle)); $SZ=$H."GetMeth`od"("SizeOf",[type[]]'type'); $T1.f1=131072; $T1.f2=$Z; $T1.f3=$v; $T2.f1=1
$T2.f2=1;$T2.f3=1;$T2.f4=1;$T2.f6=$T1;$T3.f1=$SZ.invoke($null,$T[4]);$T4.f1=$T3;$T4.f2=$HG.invoke($null,$SZ.invoke($null,$T[2]))
$H."GetMeth`od"("StructureTo`Ptr",[type[]]($D[2],$J,'boolean')).invoke($null,@(($T2-as $D[2]),$T4.f2,$false));$window=0x0E080600
$9=$T[0]."GetMeth`od"('CreateProcess').Invoke($null,@($null,$cmd,0,0,0,$window,0,$null,($T4-as $D[4]),($T5-as $D[5]))); break
}
## Cleanup
rp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0
## Create registry paths
$wdp='HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender'
' Security Center\Notifications','\UX Configuration','\MpEngine','\Spynet','\Real-Time Protection' |% {ni ($wdp+$_)-ea 0|out-null}
## Toggle Defender
if ($env:1 -eq 7) {
## enable notifications
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' Notification_Suppress -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' UILockdown -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' Notification_Suppress -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' UILockdown -Force -ea 0
## enable shell smartscreen and set to warn
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' EnableSmartScreen -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' ShellSmartScreenLevel 'Warn' -Force -ea 0
## enable store smartscreen and set to warn
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost -ea 0 |% {
sp $_.PSPath 'EnableWebContentEvaluation' 1 -Type Dword -Force -ea 0
sp $_.PSPath 'PreventOverride' 0 -Type Dword -Force -ea 0
}
## enable chredge smartscreen + pua
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 1 -Type Dword -Force -ea 0
}
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenPuaEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 1 -Type Dword -Force -ea 0
}
## enable legacy edge smartscreen
ri 'HKLM:\SOFTWARE\Policies\Microsoft\MicrosoftEdge\PhishingFilter' -Force -ea 0
## enable av
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection' DisableRealtimeMonitoring -Force -ea 0
rp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender' DisableAntiSpyware -Force -ea 0
rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' DisableAntiSpyware -Force -ea 0
sc.exe config windefend depend= RpcSs
net1 start windefend
kill -Force -Name MpCmdRun -ea 0
start ($env:ProgramFiles+'\Windows Defender\MpCmdRun.exe') -Arg '-EnableService' -win 1
} else {
## disable notifications
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications 1 -Type Dword -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' Notification_Suppress 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration' UILockdown 0 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender Security Center\Notifications' DisableNotifications 1 -Type Dword -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' Notification_Suppress 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender\UX Configuration' UILockdown 0 -Type Dword -Force -ea 0
## disable shell smartscreen and set to warn
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' EnableSmartScreen 0 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\System' ShellSmartScreenLevel 'Warn' -Force -ea 0
## disable store smartscreen and set to warn
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Windows\CurrentVersion\AppHost -ea 0 |% {
sp $_.PSPath 'EnableWebContentEvaluation' 0 -Type Dword -Force -ea 0
sp $_.PSPath 'PreventOverride' 0 -Type Dword -Force -ea 0
}
## disable chredge smartscreen + pua
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 0 -Type Dword -Force -ea 0
}
gp Registry::HKEY_Users\S-1-5-21*\SOFTWARE\Microsoft\Edge\SmartScreenPuaEnabled -ea 0 |% {
sp $_.PSPath '(Default)' 0 -Type Dword -Force -ea 0
}
## disable legacy edge smartscreen
sp 'HKLM:\SOFTWARE\Policies\Microsoft\MicrosoftEdge\PhishingFilter' EnabledV9 0 -Type Dword -Force -ea 0
## disable av
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection' DisableRealtimeMonitoring 1 -Type Dword -Force
sp 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender' DisableAntiSpyware 1 -Type Dword -Force -ea 0
sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' DisableAntiSpyware 1 -Type Dword -Force -ea 0
net1 stop windefend
sc.exe config windefend depend= RpcSs-TOGGLE
kill -Name MpCmdRun -Force -ea 0
start ($env:ProgramFiles+'\Windows Defender\MpCmdRun.exe') -Arg '-DisableService' -win 1
del ($env:ProgramData+'\Microsoft\Windows Defender\Scans\mpenginedb.db') -Force -ea 0 ## Commented = keep scan history
del ($env:ProgramData+'\Microsoft\Windows Defender\Scans\History\Service') -Recurse -Force -ea 0
}
## PERSONAL CONFIGURATION TWEAK - COMMENT OR UNCOMMENT ENTRIES TO TWEAK OR REVERT
#sp $wdp DisableRoutinelyTakingAction 1 -Type Dword -Force -ea 0 ## Auto Actions off
#rp $wdp DisableRoutinelyTakingAction -Force -ea 0 ## Auto Actions ON [default]
#sp ($wdp+'\MpEngine') MpCloudBlockLevel 2 -Type Dword -Force -ea 0 ## Cloud blocking level HIGH
#rp ($wdp+'\MpEngine') MpCloudBlockLevel -Force -ea 0 ## Cloud blocking level low [default]
#sp ($wdp+'\Spynet') SpyNetReporting 2 -Type Dword -Force -ea 0 ## Cloud protection ADVANCED
#rp ($wdp+'\Spynet') SpyNetReporting -Force -ea 0 ## Cloud protection basic [default]
#sp ($wdp+'\Spynet') SubmitSamplesConsent 0 -Type Dword -Force -ea 0 ## Sample Submission ALWAYS-PROMPT
#rp ($wdp+'\Spynet') SubmitSamplesConsent -Force -ea 0 ## Sample Submission automatic [default]
#sp ($wdp+'\Real-Time Protection') RealtimeScanDirection 1 -Type Dword -Force -ea 0 ## Scan incoming file only
#rp ($wdp+'\Real-Time Protection') RealtimeScanDirection -Force -ea 0 ## Scan INCOMING, OUTGOING file [default]
#sp $wdp PUAProtection 1 -Type Dword -Force -ea 0 ## Potential Unwanted Apps on [policy]
#rp $wdp PUAProtection -Force -ea 0 ## Potential Unwanted Apps off [default]
#sp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' PUAProtection 1 -Type Dword -Force -ea 0 ## Potential Unwanted Apps ON [user]
#rp 'HKLM:\SOFTWARE\Microsoft\Windows Defender' PUAProtection -Force -ea 0 ## Potential Unwanted Apps off [default]
$env:1=$null
# done!
'@ -Force -ea 0; $k=@();$k+=gp Registry::HKEY_Users\S-1-5-21*\Volatile* ToggleDefender -ea 0;iex($k[0].ToggleDefender)
#-_-# hybrid script, can be pasted directly into powershell console






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)