ping img.onload 原理 ping相关协议
ping(网络诊断工具)_百度百科 https://baike.baidu.com/item/ping/6235?fr=aladdin
ping img.onload 原理 JavaScript实现 ping相关协议
<div onclick="P('183.232.231.174')">
P
</div>
<script>
// 183.232.231.174 baidu
function P(ip) {
console.log(ip);
var img = new Image();
const start = new Date().getTime();
img.src = "http://" + ip + "/" + start;
}
</script>
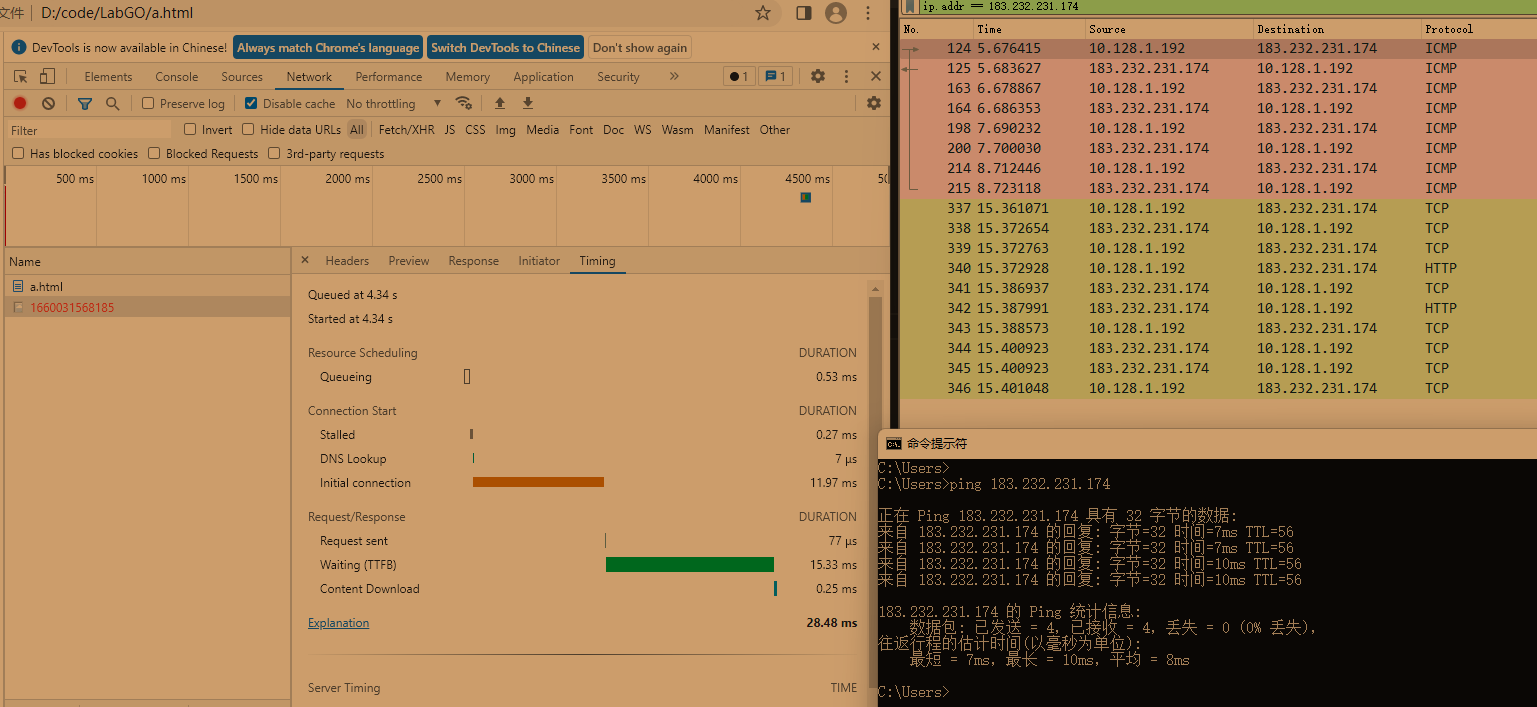
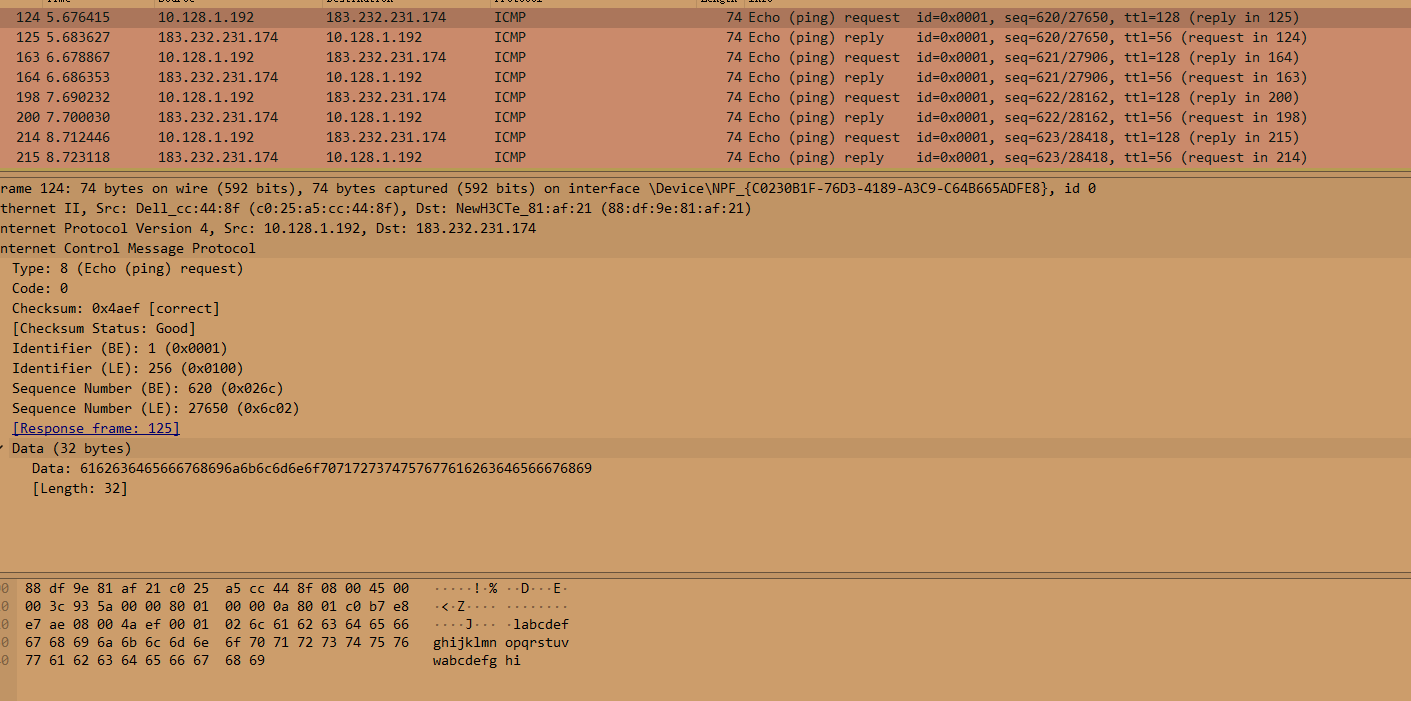

ICMP
Internet Control Message Protocol
互发
6162636465666768696a6b6c6d6e6f7071727374757677616263646566676869
abcdefghijklmnopqrstuvwabcdefghi
golang实现ping命令 - 云+社区 - 腾讯云 https://cloud.tencent.com/developer/article/1071047
C:\Users\sas>ping
用法: ping [-t] [-a] [-n count] [-l size] [-f] [-i TTL] [-v TOS]
[-r count] [-s count] [[-j host-list] | [-k host-list]]
[-w timeout] [-R] [-S srcaddr] [-c compartment] [-p]
[-4] [-6] target_name
选项:
-t Ping 指定的主机,直到停止。
若要查看统计信息并继续操作,请键入 Ctrl+Break;
若要停止,请键入 Ctrl+C。
-a 将地址解析为主机名。
-n count 要发送的回显请求数。
-l size 发送缓冲区大小。
-f 在数据包中设置“不分段”标记(仅适用于 IPv4)。
-i TTL 生存时间。
-v TOS 服务类型(仅适用于 IPv4。该设置已被弃用,
对 IP 标头中的服务类型字段没有任何
影响)。
-r count 记录计数跃点的路由(仅适用于 IPv4)。
-s count 计数跃点的时间戳(仅适用于 IPv4)。
-j host-list 与主机列表一起使用的松散源路由(仅适用于 IPv4)。
-k host-list 与主机列表一起使用的严格源路由(仅适用于 IPv4)。
-w timeout 等待每次回复的超时时间(毫秒)。
-R 同样使用路由标头测试反向路由(仅适用于 IPv6)。
根据 RFC 5095,已弃用此路由标头。
如果使用此标头,某些系统可能丢弃
回显请求。
-S srcaddr 要使用的源地址。
-c compartment 路由隔离舱标识符。
-p Ping Hyper-V 网络虚拟化提供程序地址。
-4 强制使用 IPv4。
-6 强制使用 IPv6。
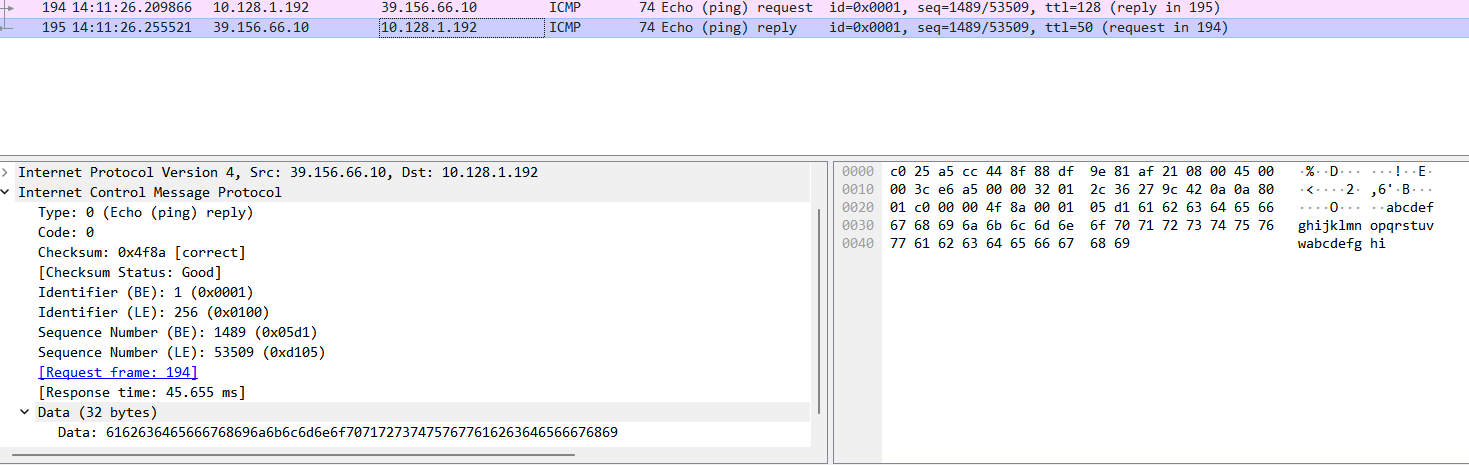
C:\>ping baidu.com
正在 Ping baidu.com [39.156.66.10] 具有 32 字节的数据:
来自 39.156.66.10 的回复: 字节=32 时间=282ms TTL=50
来自 39.156.66.10 的回复: 字节=32 时间=260ms TTL=50
来自 39.156.66.10 的回复: 字节=32 时间=157ms TTL=50
来自 39.156.66.10 的回复: 字节=32 时间=45ms TTL=50
39.156.66.10 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 45ms,最长 = 282ms,平均 = 186ms
C:\>

https://www.lifewire.com/definition-of-ping-817864
Ping is the name of a standard software utility used to test network connections. It can be used to determine if a remote device—such as a website or game server—can be reached across the network and if so, the connection's latency.
Ping tools are part of Windows, macOS, Linux, and some routers and game consoles. You can download other ping tools from third-party developers and use the tools on phones and tablets.
Note: Computer enthusiasts also use the term "ping" colloquially when initiating contact with another person via email, instant message, or other online tools. In that context, though, the word "ping" just means to notify, usually briefly.
Ping Tools
Most ping utilities and tools use Internet Control Message Protocol (ICMP). They send request messages to a target network address at periodic intervals and measure the time it takes for a response message to arrive.
These tools typically support options such as:
- How many times to send requests.
- How large of a request message to send.
- How long to wait for each reply.
The output of ping varies depending on the tool. Standard results include:
- IP address of the responding computer.
- Length of time in milliseconds between sending the request and receiving the response.
- An indication of the number of network hops between the requesting and responding computers.
- Error messages if the target computer did not respond.
Where to Find Ping Tools
When using ping on a computer, there are ping commands that work with Command Prompt in Windows.
One tool called Ping works on iOS to ping any URL or IP address. It gives the total packets sent, received, and lost, as well as the minimum, maximum, and average time that it took to receive a response.
A different app named Ping, but for Android, can perform similar functions.
What Is the Ping of Death?
In late 1996 and early 1997, a flaw in the implementation of networking in some operating systems became well-known and popularized by hackers as a way to remotely crash computers. The "Ping of Death" attack was relatively easy to carry out and dangerous due to its high probability of success.
Technically speaking, the Ping of Death attack involved sending IP packets of a size greater than 65,535 bytes to the target computer. IP packets of this size are illegal, but a programmer can build applications capable of creating them.
Carefully programmed operating systems could detect and safely handle illegal IP packets, but some failed to do so. ICMP ping utilities often included large-packet capability and became the namesake of the problem, although UDP and other IP-based protocols also could transport the Ping of Death.
Operating system vendors quickly devised patches to avoid the Ping of Death, which no longer poses a threat to today's computer networks. Still, many websites have kept the convention of blocking ICMP ping messages at their firewalls to avoid similar denial of service attacks.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号