LDAP学习笔记之三:389-DS(RHDS) 之TLS配置
一、生成CA证书
这里CA服务器和server是同一台机器,如果不是同一台机器注意两台机器的时区及时间是否一致
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | [root@ldap-server1 ~]# cd /etc/pki/CA/[root@ldap-server1 CA]# echo "01" > /etc/pki/CA/serial[root@ldap-server1 CA]# touch /etc/pki/CA/index.txt[root@ldap-server1 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)Generating RSA private key, 2048 bit long modulus.....................+++...............................................+++e is 65537 (0x10001)[root@ldap-server1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 # openssl req -new -x509 -subj "/C=CN/ST=ShangHai/L=ShangHai/O=IT/OU=IT/CN=ldap-server1.example.com" -key private/cakey.pem -out cacert.pem -days 3650You are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:ShangHaiLocality Name (eg, city) [Default City]:ShangHaiOrganization Name (eg, company) [Default Company Ltd]:ITOrganizational Unit Name (eg, section) []:ITCommon Name (eg, your name or your server's hostname) []:example.comEmail Address []:admin@example.com |
二、生成服务器请求证书,389或在RHDS必须在控制台中创建,openLDAP命令行创建
1.点击Manage Certificates
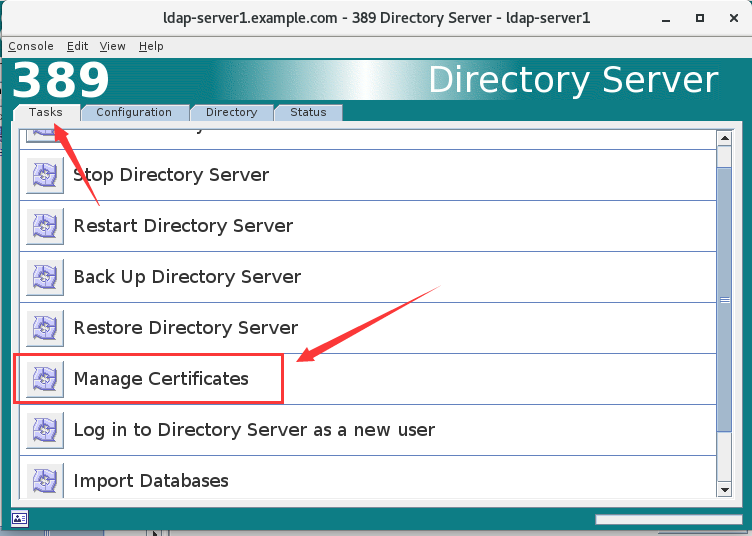
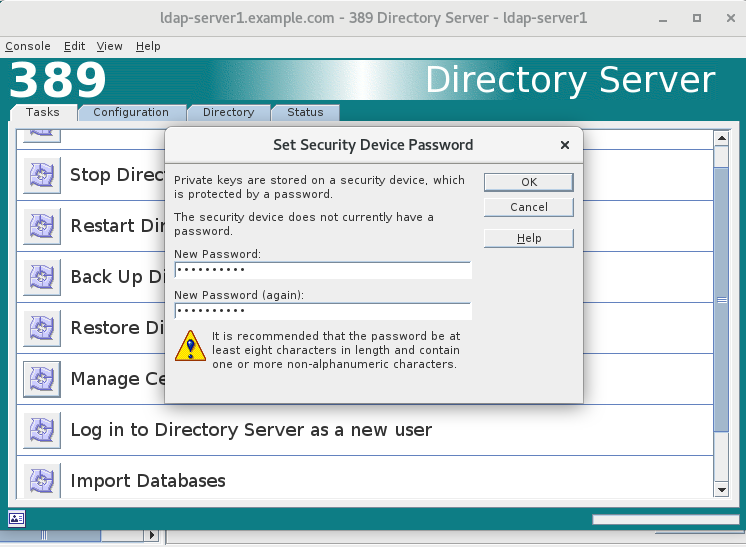
2.首次点击时会提示输入一个安全密码,务必记住此密码
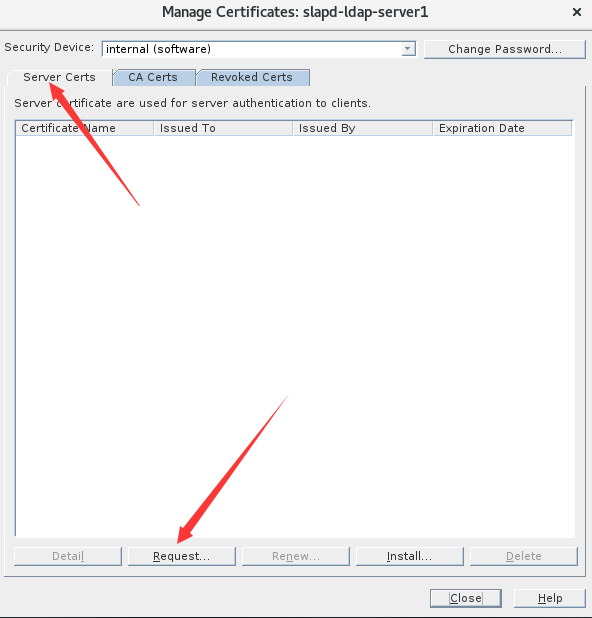
3. 创建server端请求证书
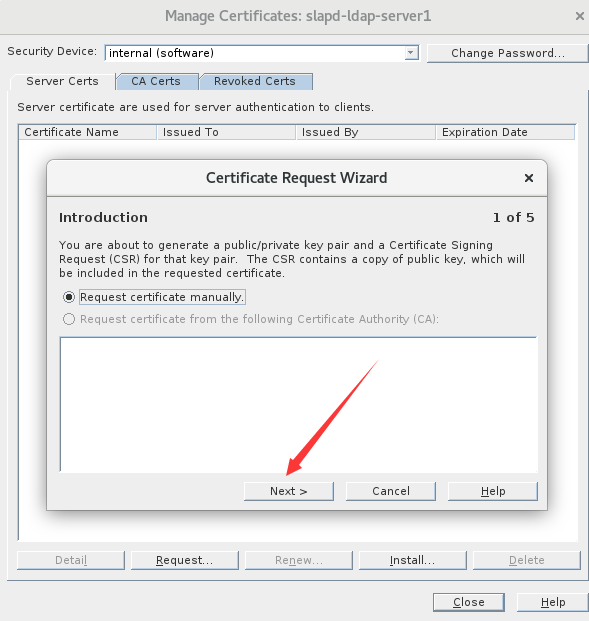
4.继续下一步
5.生成请求证书相关内容,点下一步
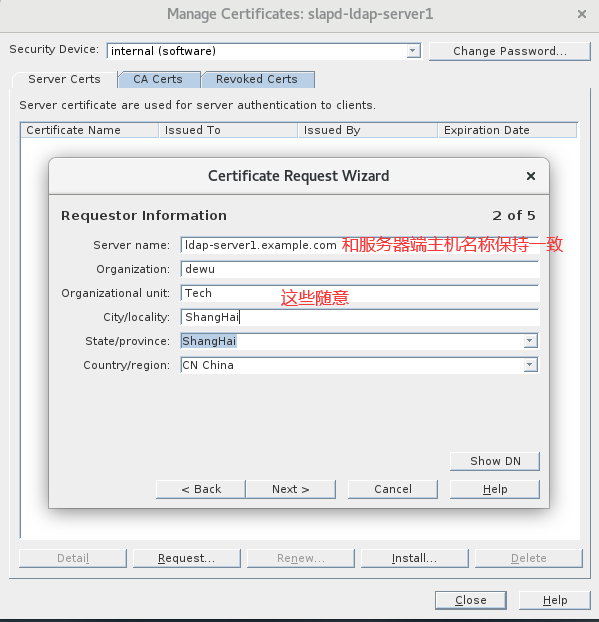
6.默认即可
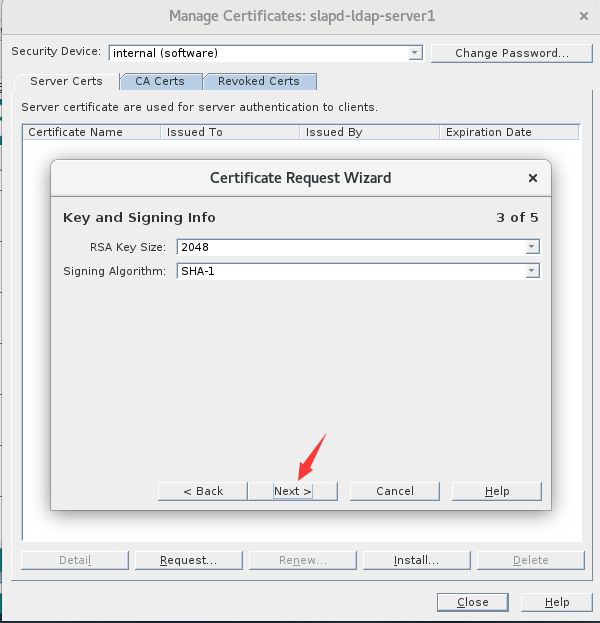
7.输入安全密码
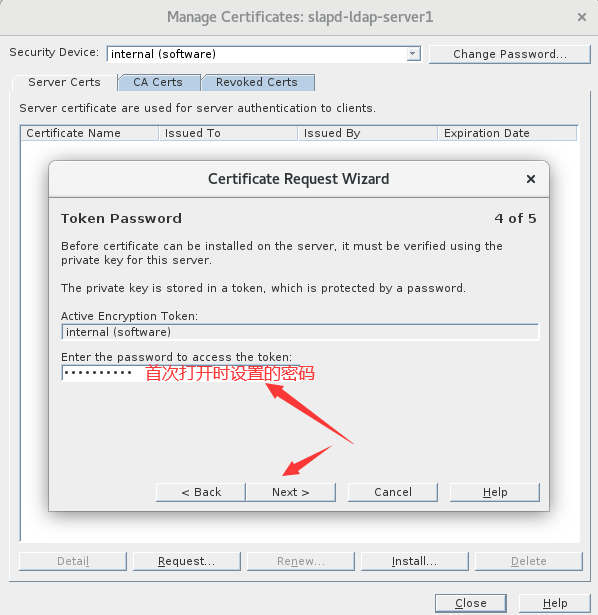
8.生成请求证书并保存
9.完成请求证书的创建
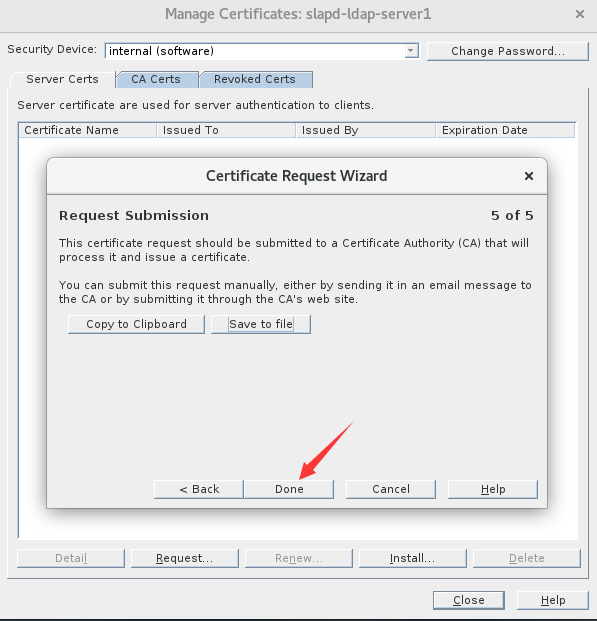
三、CA签署服务端请求证书
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | [root@ldap-server1 CA]# pwd/etc/pki/CA[root@ldap-server1 CA]# cp /root/server.csr .[root@ldap-server1 CA]# openssl ca -in server.csr -out server.crt -days 3650Using configuration from /etc/pki/tls/openssl.cnfCheck that the request matches the signatureSignature okCertificate Details: Serial Number: 1 (0x1) Validity Not Before: Mar 23 14:54:33 2022 GMT Not After : Mar 20 14:54:33 2032 GMT Subject: countryName = CN stateOrProvinceName = ShangHai localityName = ShangHai organizationName = dewu organizationalUnitName = Tech commonName = ldap-server1.example.com X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: E1:32:96:1F:9F:3B:0A:53:53:6E:46:7B:C4:43:01:D4:5D:4C:70:BE X509v3 Authority Key Identifier: keyid:74:93:DF:5C:C3:A6:49:B2:CB:2A:AA:05:9C:FE:27:3F:69:C2:B9:89Certificate is to be certified until Mar 20 14:54:33 2032 GMT (3650 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base Updated |
可能遇见的问题:
1 2 | The stateOrProvinceName field needed to be the same in theCA certificate (ShangHai) and the request (ShangHai) |
原因
1 2 | 1.CA默认使用policy_match策略,要求请求证书和CA证书 countryName stateOrProvinceName organizationName三个字段保持一致,如果不一致会报错2.当上面三个字段保持一致时,请求证书和CA证书编码不一致时也会报错,CA编码为utf8only |
解决方法
1 2 3 4 | [root@ldap-server1 CA]# cp /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl.cnf-bak[root@ldap-server1 CA]# vim /etc/pki/tls/openssl.cnf #将策略修改为policy_anything 81 #policy = policy_match 82 policy = policy_anything |
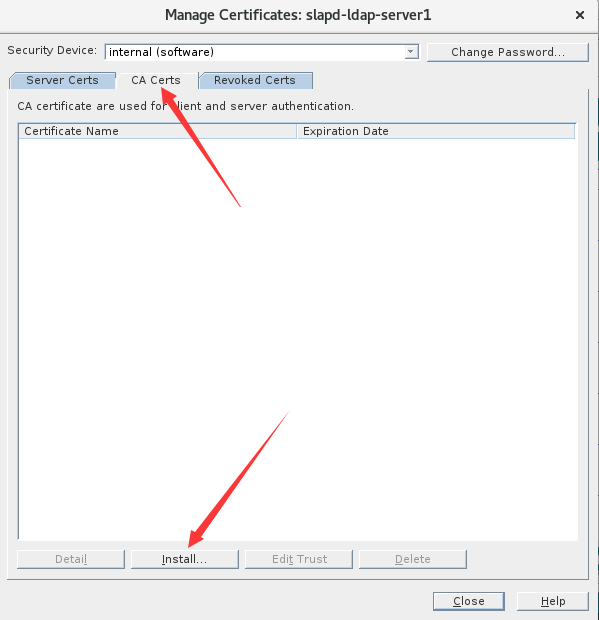
四、导入服务端及CA证书
1.导入服务端证书
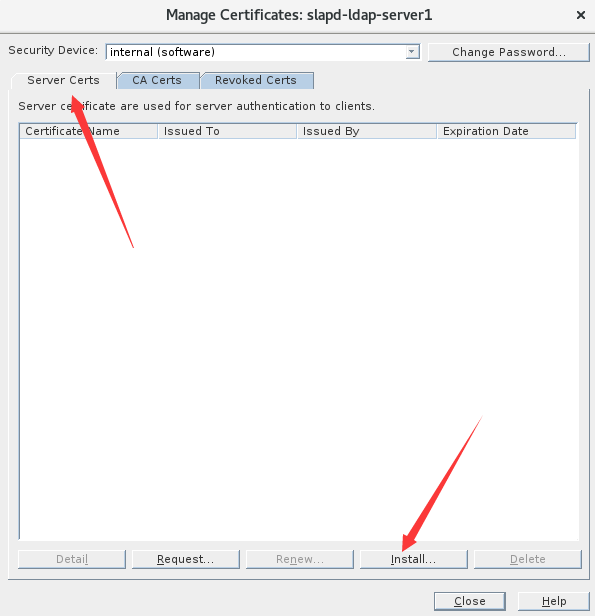
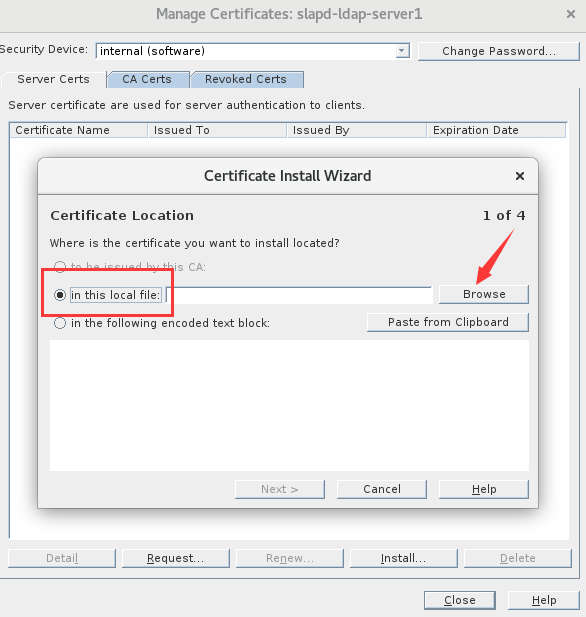
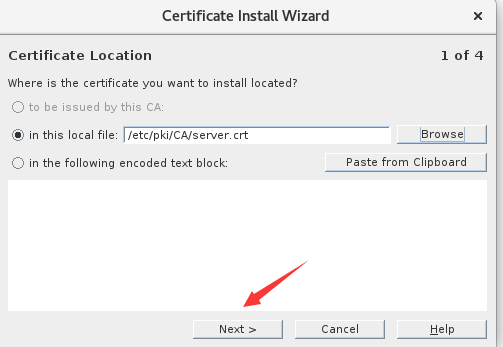
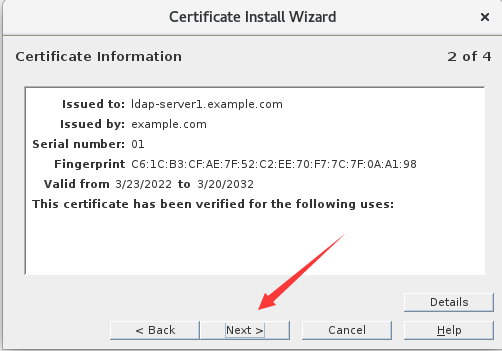
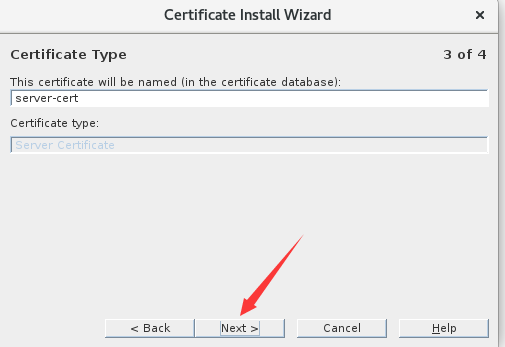
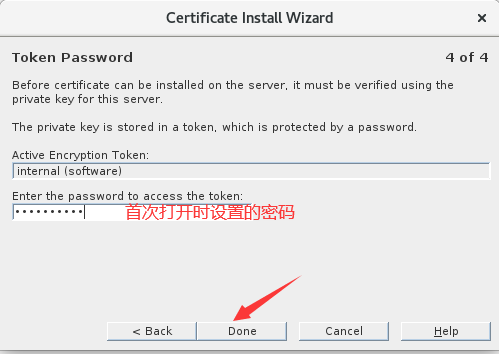
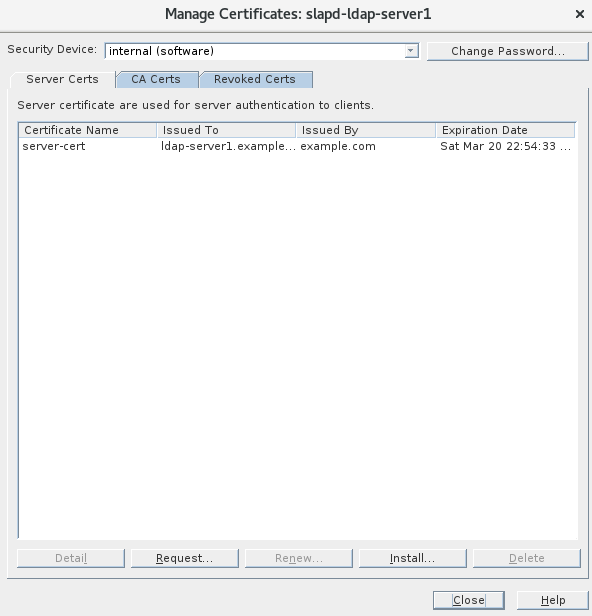
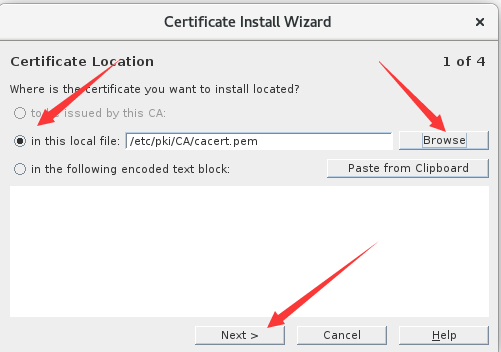
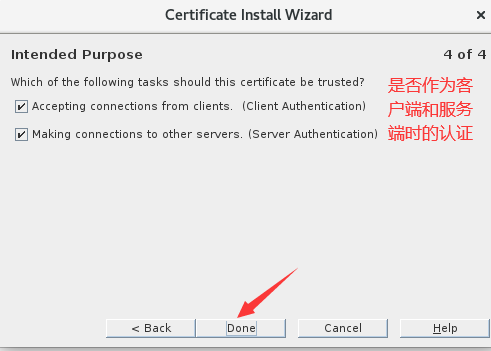
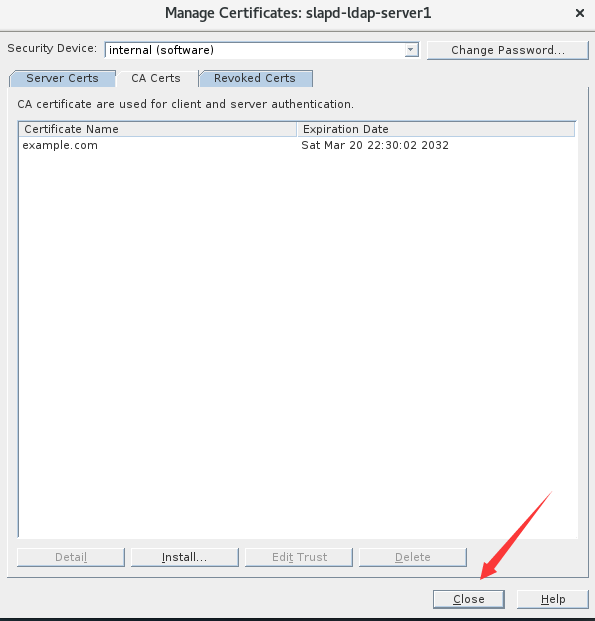
2.导入CA证书
五、启用TLS
控制台启用
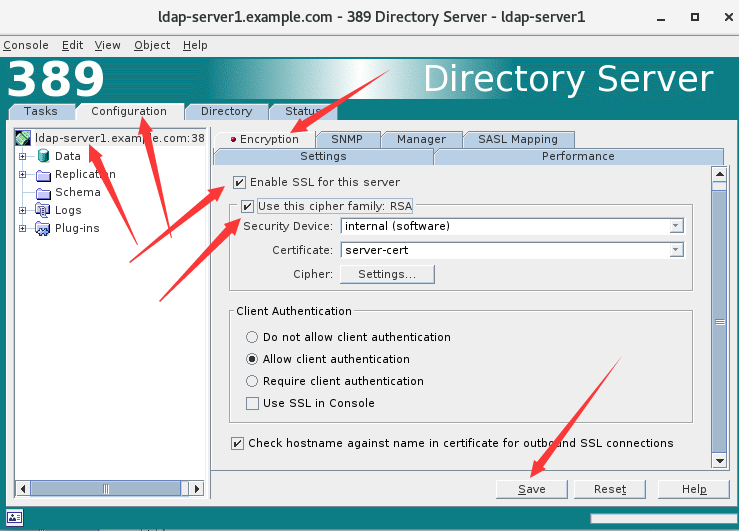
提示需要重启服务
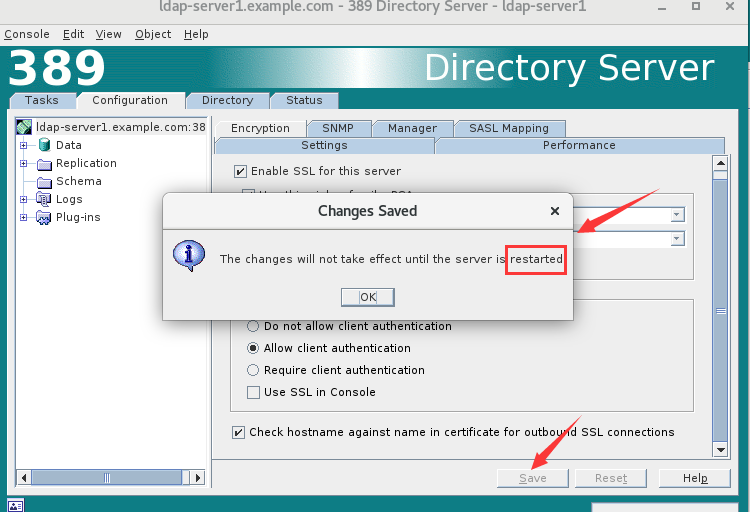
重启服务
1 2 | [root@ldap-server1 CA]# systemctl restart dirsrv.target Enter PIN for Internal (Software) Token: ********** #注意,启用TLS后每次重启都需要输入证书管理时设置的密码 |
六、验证
1 2 3 4 5 6 7 | [root@ldap-server1 CA]# ldapsearch -ZZ -x #-Z是使用TLS请求,-ZZ是强制使用TLSldap_start_tls: Connect error (-11) additional info: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed (self signed certificate in certificate chain)[root@ldap-server1 CA]# vim /etc/openldap/ldap.conf #配置客户端使用证书TLS_CACERT /etc/openldap/certs/cacert.pem[root@ldap-server1 CA]# cp /etc/pki/CA/cacert.pem /etc/openldap/certs/ #拷贝CA证书到指定位置[root@ldap-server1 CA]# ldapsearch -ZZ -x |
七、其他
1.如果我们在控制台添加了server证书,忘记添加CA证书,并且启用了TSL,那么服务就无法启动了,这时候就需要修改配置文件
配置文件:
1 2 | [root@ldap-server1 ~]# grep -n "nsslapd-security" /etc/dirsrv/slapd-server1/dse.ldif51:nsslapd-security: on #将on修改为off重启服务即可 |
2.解决添加TLS后每次重启都输入密码的问题
1 2 | [root@ldap-server1 ~]# echo 'Internal (Software) Token:admin12345' > /etc/dirsrv/slapd-server1/pin.txt[root@ldap-server1 ~]# chmod 600 /etc/dirsrv/slapd-server1/pin.txt |
3.控制台导入证书有一定几率会失败,这是就要使用certutil工具命令行导入了
1 2 | [root@ldap-server1 ~]# certutil -d /etc/dirsrv/slapd-ldap-server1/ -A -i ca.crt -n CA_CERT -t CT,CT,CT #-d 数据目录 -A 追加 -i指定证书 -n给证书设置一个名称 -t 固定写法[root@ldap-server1 ~]# certutil -d /etc/dirsrv/slapd-ldap-server1/ -A -i ldap-server1.example.com.crt -n SERVE_CERT -t u,u,u |
"一劳永逸" 的话,有是有的,而 "一劳永逸" 的事却极少






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· AI 智能体引爆开源社区「GitHub 热点速览」
· Manus的开源复刻OpenManus初探
· 写一个简单的SQL生成工具
2019-03-23 Python课程第一天作业