学习shamir秘密分享
介绍#
1979年Shamir在下文提出基于拉格朗日插值多项式的
方案#
- 秘密分享
假设有一个秘密
- 秘密重构
当有不少于
也可以看作是:
实验#
import random
from decimal import Decimal
FIELD_SIZE = 10**5 # GF域大小
def reconstruct_secret(shares):
"""
Combines individual shares (points on graph)
using Lagranges interpolation.
`shares` is a list of points (x, y) belonging to a
polynomial with a constant of our key.
"""
sums = 0
for j, share_j in enumerate(shares):
xj, yj = share_j
prod = Decimal(1)
for i, share_i in enumerate(shares):
xi, _ = share_i
if i != j:
prod *= Decimal(Decimal(xi)/(xi-xj))
prod *= yj
sums += Decimal(prod)
return int(round(Decimal(sums), 0))
def polynom(x, coefficients):
"""
This generates a single point on the graph of given polynomial
in `x`. The polynomial is given by the list of `coefficients`.
"""
point = 0
# Loop through reversed list, so that indices from enumerate match the
# actual coefficient indices
for coefficient_index, coefficient_value in enumerate(coefficients[::-1]):
point += x ** coefficient_index * coefficient_value
return point
def coeff(t, secret):
"""
Randomly generate a list of coefficients for a polynomial with
degree of `t` - 1, whose constant is `secret`.
For example with a 3rd degree coefficient like this:
3x^3 + 4x^2 + 18x + 554
554 is the secret, and the polynomial degree + 1 is
how many points are needed to recover this secret.
(in this case it's 4 points).
"""
coeff = [random.randrange(0, FIELD_SIZE) for _ in range(t - 1)]
coeff.append(secret)
return coeff
def generate_shares(n, m, secret):
"""
Split given `secret` into `n` shares with minimum threshold
of `m` shares to recover this `secret`, using SSS algorithm.
"""
coefficients = coeff(m, secret)
shares = []
for i in range(1, n+1):
x = random.randrange(1, FIELD_SIZE)
shares.append((x, polynom(x, coefficients)))
return shares
# Driver code
if __name__ == '__main__':
# (3,5) sharing scheme
t, n = 3, 5
secret = 1234
print(f'Original Secret: {secret}')
# Phase I: Generation of shares
shares = generate_shares(n, t, secret)
print(f'Shares: {", ".join(str(share) for share in shares)}')
# Phase II: Secret Reconstruction
# Picking t shares randomly for
# reconstruction
pool = random.sample(shares, t)
print(f'Combining shares: {", ".join(str(share) for share in pool)}')
print(f'Reconstructed secret: {reconstruct_secret(pool)}')
## 输出
Original Secret: 1234
Shares: (85479, 169064248999330), (64655, 96725154480594), (47701, 52649409201294), (99941, 231110282437614), (93923, 204115595277642)
Combining shares: (47701, 52649409201294), (64655, 96725154480594), (99941, 231110282437614)
Reconstructed secret: 1234
总结#
秘密共享方案广泛应用于要求信任是分布式而不是集中式的密码系统中。使用秘密共享的真实场景的突出例子包括:
- 基于阈值的比特币签名
- 安全多方计算
- 具有多方计算的私有机器学习
- 密码管理
作者:Hang Shao
出处:https://www.cnblogs.com/pam-sh/p/17750476.html
版权:本作品采用「知识共享」许可协议进行许可。
声明:欢迎交流! 原文链接 ,如有问题,可邮件(mir_soh@163.com)咨询.


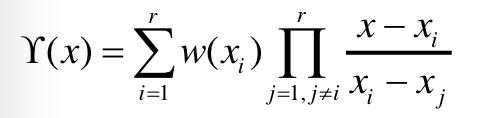


 PamShao
PamShao

【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· .NET10 - 预览版1新功能体验(一)