APP逆向实战 : 淘最热点
5.淘最热点(com.maihan.tredian)
HTTP canary抓包分析
POST /api/v1/auth/login/sms HTTP/1.1
Content-Type: application/json
Connection: close
Charset: UTF-8
User-Agent: Dalvik/2.1.0 (Linux; U; Android 10; Pixel XL Build/QP1A.191005.007.A3)
Host: api.taozuiredian.com
Accept-Encoding: gzip
Content-Length: 654
{"app_ver":"100","sign":"fba554eb67979499bd32021348b2d51f73214782","nonce":"6uhdp11727146769351","tzrd":"BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t\/KDL9RCbvH\/vr0qdSE1IMBjy6D\/SQoXbTBgojGsCYv2+yA2ocToOyRo6AzjqzrJwksJtIEBj3Mo9DFvL2KF2qtNQhMDk8bwF1gRho7ABBPfZHgcI2ipsidU6to0\/zSCf6XKggA9XOrS9hgc3qZrUOuuvs6VkaxuHKrGYJhvMgMPgFjl1Lj3jd1\/+M7Nej0CmFY3mVFAZhowYwXBuce5N47Ru5IBz7rR+maDhSibKNWb\/5\/8lielUEuBJUgIYW0H8tXIlpg\/eYX7Nx4mABcuvmYJuIEAjswQSPuRPvttSR4pgf9WyEoq+ysVTEbAP3zLMtpuzV6OmRn9CznkwE7AZpRiIV8L60\/MX3UeHYQcFCFYAgV7DeLJsWPZ1Oour34LHqaNF7wffGMkABdDeEAO1iA8pJTz5juRzOHGjonbZM1B9CscmlxNmLvk4fQX7Y6\/FnoDj2KptzeO596nCAeBW5","timestamp":"1727146769"}
POST请求,这里面包含了请求的相关信息
Content-Type: application/json
表示请求体的格式是JSON,这意味着请求发送的数据将是JSON格式的字符串。
Connection: close
指示服务器在完成请求后关闭连接,不保持长连接。
Charset: UTF-8
指定字符编码为UTF-8,确保请求体中的数据被正确解析。
User-Agent: Dalvik/2.1.0 (Linux; U; Android 10; Pixel XL Build/QP1A.191005.007.A3)
表示发起请求的客户端信息,这里是一个Android应用,使用的是Dalvik虚拟机(Android的Java运行环境)。
Host: api.taozuiredian.com
请求的主机名,指明请求的目标服务器。
Accept-Encoding: gzip
客户端支持的内容编码,这里表示可以接收gzip压缩的响应。
Content-Length: 654
请求体的字节长度,这里表示请求体的内容长度为654字节。
我们再来看看这里的JSON
"app_ver":"100","sign":"fba554eb67979499bd32021348b2d51f73214782","nonce":"6uhdp11727146769351"
这里包含了APP的版本号,以及sign,nonce的值
自吐算法去hook相关算法
这里我们使用的是算法自吐,去HOOK加密算法的相关加密函数得到相关的信息
[Pixel XL::淘最热点]-> Cipher.init('int', 'java.security.Key', 'java.security.spec.AlgorithmParameterSpec') is called!
AES/CBC/PKCS5Padding init Key Utf8: PeMBjWOVbrMgElXO
AES/CBC/PKCS5Padding init Key Hex: 50654d426a574f5662724d67456c584f
AES/CBC/PKCS5Padding init Key Base64: UGVNQmpXT1Zick1nRWxYTw==
AES/CBC/PKCS5Padding init iv Utf8: VTToNCiifIJ9c2co
AES/CBC/PKCS5Padding init iv Hex: 5654546f4e43696966494a396332636f
AES/CBC/PKCS5Padding init iv Base64: VlRUb05DaWlmSUo5YzJjbw==
=======================================================
Cipher.doFinal('[B') is called!
java.lang.Throwable
at javax.crypto.Cipher.doFinal(Native Method)
at com.maihan.tredian.util.AesUtil.b(AesUtil.java:5)
at com.maihan.tredian.net.MhRequestUtil.a(MhRequestUtil.java:19)
at com.maihan.tredian.net.MhRequestUtil.b(MhRequestUtil.java:1)
at com.maihan.tredian.net.MhNetworkUtil$2.run(MhNetworkUtil.java:36)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:462)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1167)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:641)
at java.lang.Thread.run(Thread.java:919)
AES/CBC/PKCS5Padding doFinal data Utf8: {"imei2":"null","device_name":"google Pixel XL","code":"1234","imei1":"null","phone":"15349673565","getui_push_id":"5ed9164a9b30d0862f4971832f1aeeec","device_udid":"52d2d4dcb8989f701e65ce8e634bfa83","device_id":"52477ecf24d7d5f2bb316dd075e1c35","channel":"official","system":"1","from":"app","mac":"40:4E:36:24:41:C1","os_ver_code":"29","android_id":"027228ebf6d6c3d6"}
AES/CBC/PKCS5Padding doFinal data Hex: 7b22696d656932223a226e756c6c222c226465766963655f6e616d65223a22676f6f676c6520506978656c20584c222c22636f6465223a2231323334222c22696d656931223a226e756c6c222c2270686f6e65223a223135333439363733353635222c2267657475695f707573685f6964223a223565643931363461396233306430383632663439373138333266316165656563222c226465766963655f75646964223a223532643264346463623839383966373031653635636538653633346266613833222c226465766963655f6964223a2235323437376563663234643764356632626233313664643037356531633335222c226368616e6e656c223a226f6666696369616c222c2273797374656d223a2231222c2266726f6d223a22617070222c226d6163223a2234303a34453a33363a32343a34313a4331222c226f735f7665725f636f6465223a223239222c22616e64726f69645f6964223a2230323732323865626636643663336436227d
AES/CBC/PKCS5Padding doFinal data Base64: eyJpbWVpMiI6Im51bGwiLCJkZXZpY2VfbmFtZSI6Imdvb2dsZSBQaXhlbCBYTCIsImNvZGUiOiIxMjM0IiwiaW1laTEiOiJudWxsIiwicGhvbmUiOiIxNTM0OTY3MzU2NSIsImdldHVpX3B1c2hfaWQiOiI1ZWQ5MTY0YTliMzBkMDg2MmY0OTcxODMyZjFhZWVlYyIsImRldmljZV91ZGlkIjoiNTJkMmQ0ZGNiODk4OWY3MDFlNjVjZThlNjM0YmZhODMiLCJkZXZpY2VfaWQiOiI1MjQ3N2VjZjI0ZDdkNWYyYmIzMTZkZDA3NWUxYzM1IiwiY2hhbm5lbCI6Im9mZmljaWFsIiwic3lzdGVtIjoiMSIsImZyb20iOiJhcHAiLCJtYWMiOiI0MDo0RTozNjoyNDo0MTpDMSIsIm9zX3Zlcl9jb2RlIjoiMjkiLCJhbmRyb2lkX2lkIjoiMDI3MjI4ZWJmNmQ2YzNkNiJ9
AES/CBC/PKCS5Padding doFinal result Hex: 070cd7cd2185ca23ecb4c215bb34d96fb2f34d9cdb5d124e173a5b42221a4fbb7f2832fd4426ef1ffbebd2a75213520c063cba0ff490a176d3060a231ac098bf6fb2036a1c4e83b2468e80ce3ab3ac9c24b09b481018f7328f4316f2f6285daab4d42130393c6f0175811868ec00413df64781c2368a9b22754eada34ff34827fa5ca82003d5cead2f6181cdea66b50ebaebece9591ac6e1caac660986f32030f8058e5d4b8f78ddd7ff8cecd7a3d02985637995140661a306305c1b9c7b9378ed1bb9201cfbad1fa668385289b28d59bff9ffc9627a5504b81254808616d07f2d5c894378400ed6203ca494f3e63b91cce1c68e89db64cd41f42b1c9a5c4d98bbe4e1f417ed8ebf167a038f62a9b7378ee7dea70807815b9
AES/CBC/PKCS5Padding doFinal result Base64: BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMBjy6D/SQoXbTBgojGsCYv2+yA2ocToOyRo6AzjqzrJwksJtIEBj3Mo9DFvL2KF2qtNQhMDk8bwF1gRho7ABBPfZHgcI2ipsidU6to0/zSCf6XKggA9XOrS9hgc3qZrUOuuvs6VkaxuHKrGYJhvMgMPgFjl1Lj3jd1/+M7Nej0CmFY3mVFAZhowYwXBuce5N47Ru5IBz7rR+maDhSibKNWb/5/8lielUEuBJUgIYW0H8tXIlpg/eYX7Nx4mABcuvmYJuIEAjswQSPuRPvttSR4pgf9WyEoq+ysVTEbAP3zLMtpuzV6OmRn9CznkwE7AZpRiIV8L60/MX3UeHYQcFCFYAgV7DeLJsWPZ1Oour34LHqaNF7wffGMkABdDeEAO1iA8pJTz5juRzOHGjonbZM1B9CscmlxNmLvk4fQX7Y6/FnoDj2KptzeO596nCAeBW5
=======================================================
我们可以看到HOOK到了Cipher的init方法,更好的是我们发现AES/CBC/PKCS5Padding doFinal result的结果是抓包的tzrd。
tzrd
"tzrd":"BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t\/KDL9RCbvH\/vr0qdSE1IMBjy6D\/SQoXbTBgojGsCYv2+yA2ocToOyRo6AzjqzrJwksJtIEBj3Mo9DFvL2KF2qtNQhMDk8bwF1gRho7ABBPfZHgcI2ipsidU6to0\/zSCf6XKggA9XOrS9hgc3qZrUOuuvs6VkaxuHKrGYJhvMgMPgFjl1Lj3jd1\/+M7Nej0CmFY3mVFAZhowYwXBuce5N47Ru5IBz7rR+maDhSibKNWb\/5\/8lielUEuBJUgIYW0H8tXIlpg\/eYX7Nx4mABcuvmYJuIEAjswQSPuRPvttSR4pgf9WyEoq+ysVTEbAP3zLMtpuzV6OmRn9CznkwE7AZpRiIV8L60\/MX3UeHYQcFCFYAgV7DeLJsWPZ1Oour34LHqaNF7wffGMkABdDeEAO1iA8pJTz5juRzOHGjonbZM1B9CscmlxNmLvk4fQX7Y6\/F
这里有相关的IV和key以及明文代码
AES/CBC/PKCS5Padding init Key Utf8: PeMBjWOVbrMgElXO
AES/CBC/PKCS5Padding init Key Hex: 50654d426a574f5662724d67456c584f
AES/CBC/PKCS5Padding init Key Base64: UGVNQmpXT1Zick1nRWxYTw==
AES/CBC/PKCS5Padding init iv Utf8: VTToNCiifIJ9c2co
AES/CBC/PKCS5Padding init iv Hex: 5654546f4e43696966494a396332636f
AES/CBC/PKCS5Padding init iv Base64: VlRUb05DaWlmSUo5YzJjbw==
{"imei2":"null","device_name":"google Pixel XL","code":"1234","imei1":"null","phone":"15349673565","getui_push_id":"5ed9164a9b30d0862f4971832f1aeeec","device_udid":"52d2d4dcb8989f701e65ce8e634bfa83","device_id":"52477ecf24d7d5f2bb316dd075e1c35","channel":"official","system":"1","from":"app","mac":"40:4E:36:24:41:C1","os_ver_code":"29","android_id":"027228ebf6d6c3d6"}
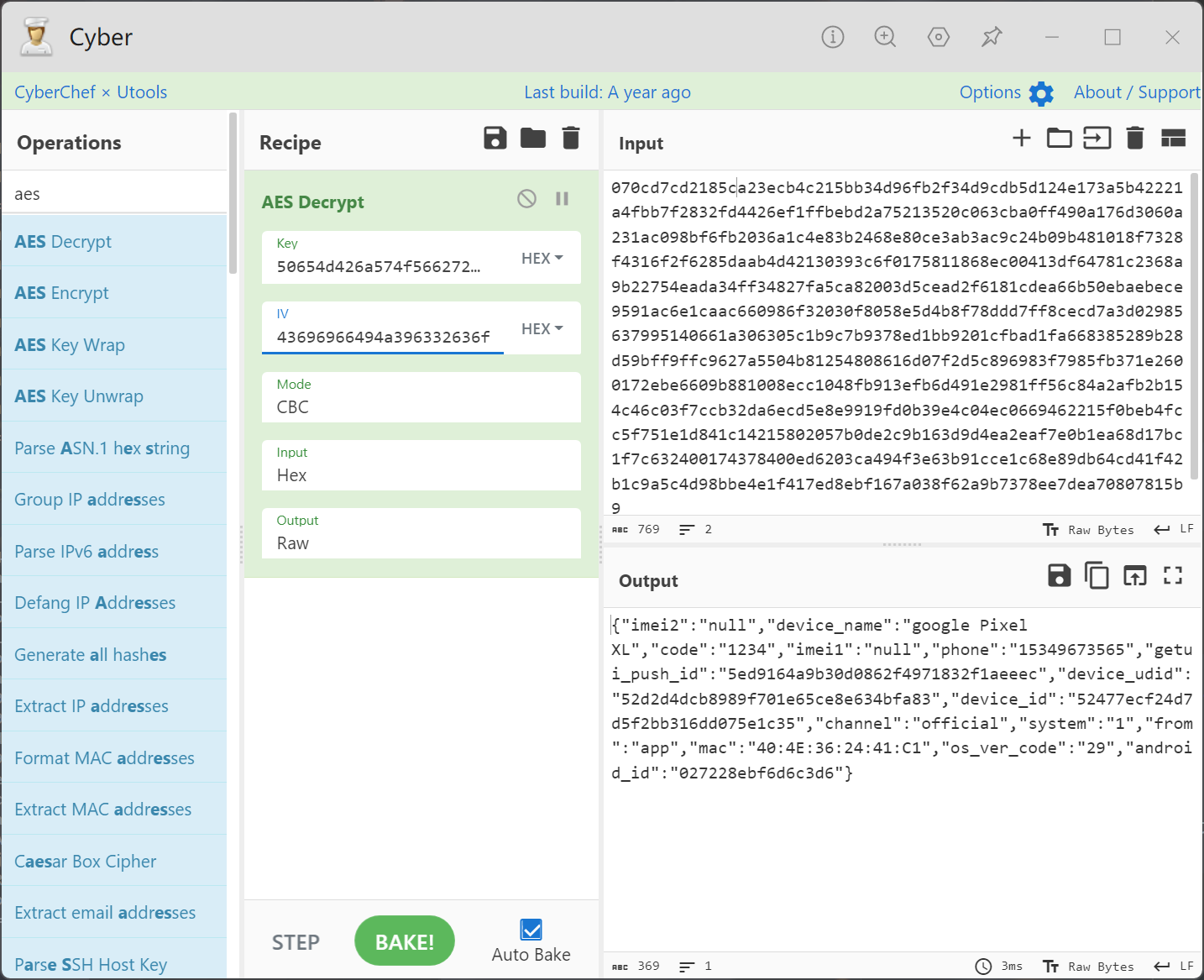
这里就可以直接解出tzrd了,这里的tzrd全部都是固定的,可以直接伪造的值(这里要使用HEX进行解密,base64中的 ‘/’ 字符会多出 ‘\’ )
关键代码函数定位
Cipher.doFinal('[B') is called!
java.lang.Throwable
at javax.crypto.Cipher.doFinal(Native Method)
at com.maihan.tredian.util.AesUtil.b(AesUtil.java:5)
at com.maihan.tredian.net.MhRequestUtil.a(MhRequestUtil.java:19)
at com.maihan.tredian.net.MhRequestUtil.b(MhRequestUtil.java:1)
at com.maihan.tredian.net.MhNetworkUtil$2.run(MhNetworkUtil.java:36)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:462)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1167)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:641)
at java.lang.Thread.run(Thread.java:919)
我们既然得到了相应的堆栈信息,那我们就去看看相关函数的加密过程到这个函数的位置去com.maihan.tredian.net.MhRequestUtil
可以看到的很多关于我们初始化数据的地方,我们先来看java层中那些抓包得到的数据是怎么进行得到和获取的
public static void a(Context context, MsMultiPartFormData msMultiPartFormData) {
HashMap hashMap = new HashMap();
String a2 = a();
String valueOf = String.valueOf(System.currentTimeMillis() / 1000);
String valueOf2 = String.valueOf(Util.j(context));
hashMap.put("nonce", a2);
hashMap.put(CampaignEx.f3, valueOf);
hashMap.put("app_ver", valueOf2);
String a3 = a((Map<String, String>) hashMap, false, false);
msMultiPartFormData.a("nonce", a2);
msMultiPartFormData.a(CampaignEx.f3, valueOf);
msMultiPartFormData.a("app_ver", valueOf2);
msMultiPartFormData.a("sign", TreUtil.sign(a3));
hashMap.put("sign", TreUtil.sign(a3));
}
app_ver:这里是直接去调用的包管理器去寻找对应app的版本号的
public static int j(Context context) {
try {
return context.getPackageManager().getPackageInfo(context.getPackageName(), 0).versionCode;
} catch (Exception e2) {
e2.printStackTrace();
return 0;
}
}
nonce:字符串中去抽取六个字符+时间戳
private static String a() {
Random random = new Random();
StringBuffer stringBuffer = new StringBuffer();
for (int i = 0; i < 6; i++) {
stringBuffer.append("abcdefghijklmnopqrstuvwxyz0123456789".charAt(random.nextInt(36)));
}
return stringBuffer.toString() + System.currentTimeMillis();
}
sign:
HashMap hashMap = new HashMap();
String a3 = a((Map<String, String>) hashMap, false, false)
msMultiPartFormData.a("sign", TreUtil.sign(a3));
hashMap.put("sign", TreUtil.sign(a3));
这里是sign的获取的结果,我们先不去看a3是怎么获取的,我们直接去看sign函数是怎么实现
package com.maihan.tredian.util;
/* loaded from: classes2.dex */
public class TreUtil {
static {
try {
System.loadLibrary("tre");
} catch (Throwable th) {
th.printStackTrace();
}
}
public static native byte[] iv();
public static native byte[] key();
public static native String sign(String str);
}
发现是SO层进行的加密过程,我们先在java层进行HOOK,看看这个函数进行了so层之后的加密得到的值是什么
var TreUtil = Java.use("com.maihan.tredian.util.TreUtil");
TreUtil.sign.implementation = function(args){
console.log("TreUtil.sign:");
console.log(args)
var result =this.sign(args);
console.log("result: " + result);
return result;
}
结果:
[Pixel XL::淘最热点]-> TreUtil.sign:
app_ver=100&nonce=5gabrw1727152834366×tamp=1727152834&tzrd=BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMBjy6D/SQoXbTBgojGsCYv2+yA2ocToOyRo6AzjqzrJzi8nK5xkh2tw1mUSWdOSQGvsW4bPX/DgVIpBGDygHZSkttyMfR5b6dlomTRR245vk9RMo5FdYSp+4I7TEmJbBKEOOZg5hZyT4eqeLuaB33zJXFGxngvmHd+3zemLFnjxAkDumF+qFGJi7+OgJ8dm3ZRdxaydE6nZXrTGa/gQINX72Fca7NVNDPqFx9MisTkzy5+gfxc2dECDO7yXHbYgLITCdHDNlewcYhk8RiH/QeRB2lodnaRhJUv5N/TRuh+Dle3EM7JTazu9UGlvsSlKcBkc48bCrgGfqLUyWPpCJzqR7lAp0sbzLJGXx33iBlGnQ4xlMRiuX40Lb1Odcn6cURJZulhT/NPMyilX9jZJs0CC66v9C/TDkpWDXd1ZFhuJtrJfDEHGgqqFCUWsuUyEzj
result: e60377bdebeb5762d33ba23d99e0d9b919f962b8
我们发现这里HOOK了之后,其实也就是我们抓包的结果,得到的40个十六进制,二十个字节的数据(有点像SHA1)
SO层HOOK
直接去ida分析,定位导出函数,到sign函数内部去(可以分析看到是SHA1的加密)
那么我们就定义一个结构体,并且将参数一修改为JNIEnv类型
struct Context
{
uint32_t Intermediate_Hash[5];
int Computed;
int Corrupted;
uint32_t Length_Low;
uint32_t Length_High;
};
strcpy(context_104, "b2qKgtaW4,9z9D`Fmst?K5JZbLYOY]NP6ssGf2U~;zk9oCNgoytV!}wW7ia+`w9g");
v5 = (*(a1->reserved0 + 169))(a1, a3, &v22);
v6 = 0;
if ( v5 )
{
v21 = &_stack_chk_guard;
v7 = v5;
v19[0] = a3;
v8 = strlen(context_104);
v19[1] = v19;
v9 = v19 - ((strlen(v7) + v8 + 8) & 0xFFFFFFF8);
strcpy(v9, v7);
strcat(v9, context_104);
reserved0 = a1->reserved0;
v20 = a1;
reserved0[170](a1, v19[0], v7);
v11 = strlen(v9);
v12 = &v19[-2 * v11];
j_base64_encode_new(v9, v12, v11);
context.Intermediate_Hash[0] = 1732584193;
context.Intermediate_Hash[1] = -271733879;
context.Intermediate_Hash[2] = -1732584194;
context.Intermediate_Hash[3] = 271733878;
context.Intermediate_Hash[4] = -1009589776;
memset(&context.Computed, 0, 10);
context_96 = 0;
context_100 = 0;
memset(v25, 0, sizeof(v25));
v13 = strlen(v12);
v14 = j_SHA1Input(&context, v12, v13);
if ( v14 )
fprintf((&_sF + 168), "SHA1Input Error %d.\n", v14);
v15 = j_SHA1Result(&context, v26);
if ( v15 )
{
fprintf((&_sF + 168), "SHA1Result Error %d, could not compute message digest.\n", v15);
}
else
{
for ( i = 0; i != 20; ++i )
{
v17 = v26[i];
v23[0] = 0;
v23[1] = 0;
v24 = 0;
sprintf(v23, "%02x", v17);
strncat(v25, v23, 5u);
}
}
return (*(v20->reserved0 + 167))(v20, v25);
}
return v6;
}
我们从后往前去分析,返回的是v25,v25——>v23——>v17——>v26——>j_SHA1Result(&context, v26)
直接去定位j_SHA1Result(&context, v26)函数,传了context和v26,大概率这里是填充和加密之类的了
HOOK一下看看,这里为了使得麻烦,我们先去固定一个输入,然后自己调用Sign函数去,这样得到的结果也会固定
function call_java(){
Java.perform(function () {
var TreUtil = Java.use("com.maihan.tredian.util.TreUtil");
TreUtil.sign("app_ver=100&nonce=x8h25v1727078972259×tamp=1727078972&tzrd=BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMFZi/KoHkWSyO25GgaqxcKD8WLqwgUTo6hN3SLvTt//nD3EW3mKUpbFSalBc2JiXIap+q/ATioQZez9p53lttTCDp3KZjHL0IWk7CQZ7SzQzWtB4E+GtHUAphh30R0/WLv+PVlaJc6Hrwy7zZPjelzYni6+j+VAyNME+E4ymRzuSM56yVoIlb3nPcSFgqiZ237z2uJhSbIioXh3ZFwA7cbG0KYlqZT808PKIDDM70BWX9DptsqDNH58XvNsYipugw9PcknZjWRp3QOrV06E4qyzI4YDd+lEqUpPjNst5uDrLM9GWm8TjK2n5EFkhMbL4Aihl82kQpfb+a9i/WIZy7FJnkj1gcCZsvfj4qH0qT47gbZBlVSFtF+W7ZKFS/32TWyGnLxcS7ts67M/d0HtGsi7YiBH4q5E0+ESEDfBhtlERydiQgb45xbDje49aB6Ma/result: 7a10f0f6e26b0d6b50f31ff955bcb2a6622afe88")
});//这个结果是之前得到的
Java.perform(function() {
function print_args(args) {
if (args.isNull()) {
return "null";
}
if (args instanceof NativePointer) {
var module = Process.findRangeByAddress(args);
if (module != null) {
return hexdump(args) + "\n";
}
}
return ptr(args)+"\n";
}
function hook_native_add(funPtr, paramNum) {
var Module1 = Process.findModuleByAddress(funPtr);
if (Module1 === null) {
console.log("Module not found for function pointer");
return;
}
Interceptor.attach(funPtr, {
onEnter: function(args) {
this.logs = [];
this.param = [];
for (let i = 0; i < paramNum; i++) {
this.param.push(args[i]);
}
this.logs.push("call " + Module1.name + "!" + ptr(funPtr).sub(Module1.base) + "\n");
for (let i = 0; i < paramNum; i++) {
this.logs.push("this.args" + i + " onEnter: " + print_args(this.param[i]) + "\n");
}
},
onLeave: function(retval) {
for (let i = 0; i < paramNum; i++) {
this.logs.push("this.args" + i + " onLeave: " + print_args(this.param[i]) + "\n");
}
this.logs.push("retval onLeave: " + retval + "\n");
console.log(this.logs.join("\n"));
this.logs = [];
}
});
}
var moduleBase = Module.findBaseAddress("libtre.so");
if (moduleBase !== null) {
var baseaddr = moduleBase.add(0x014C8+1);
hook_native_add(baseaddr, 2);
}
else {
console.log("Module not found: libencryptlib.so");
}
这里得到的结果:
this.args0 onEnter: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c2231878 75 b7 38 c0 44 22 ee 0d 09 89 8a 27 60 6f f9 81 u.8.D".....'`o..
c2231888 33 a0 90 95 c0 1a 00 00 00 00 00 00 18 00 62 33 3.............b3
c2231898 6c 30 56 69 46 39 64 31 63 33 61 57 45 72 59 48 l0ViF9d1c3aWErYH
c22318a8 63 35 5a 77 3d 3d 64 44 39 4c 4e 55 70 61 59 6b c5Zw==dD9LNUpaYk
c22318b8 78 5a 54 31 6c 64 54 6c 41 32 63 33 4e 48 5a 6a xZT1ldTlA2c3NHZj
c22318c8 4a 56 66 6a 74 36 61 7a 6c 76 51 30 35 6e 00 00 JVfjt6azlvQ05n..
c22318d8 00 00 00 00 00 00 00 00 62 32 71 4b 67 74 61 57 ........b2qKgtaW
c22318e8 34 2c 39 7a 39 44 60 46 6d 73 74 3f 4b 35 4a 5a 4,9z9D`Fmst?K5JZ
c22318f8 62 4c 59 4f 59 5d 4e 50 36 73 73 47 66 32 55 7e bLYOY]NP6ssGf2U~
c2231908 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 21 7d 77 57 ;zk9oCNgoytV!}wW
c2231918 37 69 61 2b 60 77 39 67 00 00 5c 00 00 00 43 00 7ia+`w9g..\...C.
c2231928 84 1e 86 cd 00 00 00 00 00 60 30 c3 58 1a 23 c2 .........`0.X.#.
c2231938 dc 19 23 c2 cc c8 07 e4 02 00 00 00 00 60 30 c3 ..#..........`0.
c2231948 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 64 36 23 c2 .u...(......d6#.
c2231958 02 00 00 00 c0 f2 12 17 40 fa 04 13 01 00 00 00 ........@.......
c2231968 01 00 00 80 08 a8 16 e4 20 4a dc c0 00 00 00 00 ........ J......
this.args1 onEnter: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c2231864 08 00 00 00 a8 18 23 c2 a7 31 18 b0 b0 18 23 c2 ......#..1....#.
c2231874 a7 31 18 b0 75 b7 38 c0 44 22 ee 0d 09 89 8a 27 .1..u.8.D".....'
c2231884 60 6f f9 81 33 a0 90 95 c0 1a 00 00 00 00 00 00 `o..3...........
c2231894 18 00 62 33 6c 30 56 69 46 39 64 31 63 33 61 57 ..b3l0ViF9d1c3aW
c22318a4 45 72 59 48 63 35 5a 77 3d 3d 64 44 39 4c 4e 55 ErYHc5Zw==dD9LNU
c22318b4 70 61 59 6b 78 5a 54 31 6c 64 54 6c 41 32 63 33 paYkxZT1ldTlA2c3
c22318c4 4e 48 5a 6a 4a 56 66 6a 74 36 61 7a 6c 76 51 30 NHZjJVfjt6azlvQ0
c22318d4 35 6e 00 00 00 00 00 00 00 00 00 00 62 32 71 4b 5n..........b2qK
c22318e4 67 74 61 57 34 2c 39 7a 39 44 60 46 6d 73 74 3f gtaW4,9z9D`Fmst?
c22318f4 4b 35 4a 5a 62 4c 59 4f 59 5d 4e 50 36 73 73 47 K5JZbLYOY]NP6ssG
c2231904 66 32 55 7e 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 f2U~;zk9oCNgoytV
c2231914 21 7d 77 57 37 69 61 2b 60 77 39 67 00 00 5c 00 !}wW7ia+`w9g..\.
c2231924 00 00 43 00 84 1e 86 cd 00 00 00 00 00 60 30 c3 ..C..........`0.
c2231934 58 1a 23 c2 dc 19 23 c2 cc c8 07 e4 02 00 00 00 X.#...#.........
c2231944 00 60 30 c3 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 .`0..u...(......
c2231954 64 36 23 c2 02 00 00 00 c0 f2 12 17 40 fa 04 13 d6#.........@...
this.args0 onLeave: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c2231878 41 fd e4 31 80 61 64 e0 71 5b fe 35 fb af db 65 A..1.ad.q[.5...e
c2231888 27 86 25 2f 00 00 00 00 00 00 00 00 00 00 00 00 '.%/............
c2231898 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318a8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318b8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318c8 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318d8 01 00 00 00 00 00 00 00 62 32 71 4b 67 74 61 57 ........b2qKgtaW
c22318e8 34 2c 39 7a 39 44 60 46 6d 73 74 3f 4b 35 4a 5a 4,9z9D`Fmst?K5JZ
c22318f8 62 4c 59 4f 59 5d 4e 50 36 73 73 47 66 32 55 7e bLYOY]NP6ssGf2U~
c2231908 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 21 7d 77 57 ;zk9oCNgoytV!}wW
c2231918 37 69 61 2b 60 77 39 67 00 00 5c 00 00 00 43 00 7ia+`w9g..\...C.
c2231928 84 1e 86 cd 00 00 00 00 00 60 30 c3 58 1a 23 c2 .........`0.X.#.
c2231938 dc 19 23 c2 cc c8 07 e4 02 00 00 00 00 60 30 c3 ..#..........`0.
c2231948 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 64 36 23 c2 .u...(......d6#.
c2231958 02 00 00 00 c0 f2 12 17 40 fa 04 13 01 00 00 00 ........@.......
c2231968 01 00 00 80 08 a8 16 e4 20 4a dc c0 00 00 00 00 ........ J......
this.args1 onLeave: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c2231864 31 e4 fd 41 e0 64 61 80 35 fe 5b 71 65 db af fb 1..A.da.5.[qe...
c2231874 2f 25 86 27 41 fd e4 31 80 61 64 e0 71 5b fe 35 /%.'A..1.ad.q[.5
c2231884 fb af db 65 27 86 25 2f 00 00 00 00 00 00 00 00 ...e'.%/........
c2231894 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318a4 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318b4 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318c4 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c22318d4 00 00 00 00 01 00 00 00 00 00 00 00 62 32 71 4b ............b2qK
c22318e4 67 74 61 57 34 2c 39 7a 39 44 60 46 6d 73 74 3f gtaW4,9z9D`Fmst?
c22318f4 4b 35 4a 5a 62 4c 59 4f 59 5d 4e 50 36 73 73 47 K5JZbLYOY]NP6ssG
c2231904 66 32 55 7e 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 f2U~;zk9oCNgoytV
c2231914 21 7d 77 57 37 69 61 2b 60 77 39 67 00 00 5c 00 !}wW7ia+`w9g..\.
c2231924 00 00 43 00 84 1e 86 cd 00 00 00 00 00 60 30 c3 ..C..........`0.
c2231934 58 1a 23 c2 dc 19 23 c2 cc c8 07 e4 02 00 00 00 X.#...#.........
c2231944 00 60 30 c3 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 .`0..u...(......
c2231954 64 36 23 c2 02 00 00 00 c0 f2 12 17 40 fa 04 13 d6#.........@...
retval onLeave: 0x0
result: 31e4fd41e064618035fe5b7165dbaffb2f258627
可以看到的是我们这里最后就是得到了SHA1的结果的,那我们之前的arg1的数据是我们要输入的数据吗?不确实啊
再往后HOOK去 v14 = j_SHA1Input(&context, v12, v12_len);
var moduleBase = Module.findBaseAddress("libtre.so");
if (moduleBase !== null) {
var baseaddr = moduleBase.add(0x014C8+1);//32位程序要++1
var Input = moduleBase.add(0x015BE+1);
Interceptor.attach(Input,{
onEnter:function(args){
console.log("Input.onEnter:");
console.log(args[1].readCString());
},
onLeave:function(result){
}
}),
hook_native_add(baseaddr, 2);
} else {
console.log("Module not found: libencryptlib.so");
}
这里注意一下,为什么要console.log(args[1].readCString()),是因为我们得到的数据是一个很大的数据,不能直接输出,或者我们也可以使用hexdump(),但是这里的hexdump要修改一下格式
console.log(hexdump(args[1], {
offset: 0,
length: args[2].toInt32(),
header: true,
ansi: true
}));
[Pixel XL::淘最热点]-> call_java()
TreUtil.sign:
app_ver=100&nonce=x8h25v1727078972259×tamp=1727078972&tzrd=BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMFZi/KoHkWSyO25GgaqxcKD8WLqwgUTo6hN3SLvTt//nD3EW3mKUpbFSalBc2JiXIap+q/ATioQZez9p53lttTCDp3KZjHL0IWk7CQZ7SzQzWtB4E+GtHUAphh30R0/WLv+PVlaJc6Hrwy7zZPjelzYni6+j+VAyNME+E4ymRzuSM56yVoIlb3nPcSFgqiZ237z2uJhSbIioXh3ZFwA7cbG0KYlqZT808PKIDDM70BWX9DptsqDNH58XvNsYipugw9PcknZjWRp3QOrV06E4qyzI4YDd+lEqUpPjNst5uDrLM9GWm8TjK2n5EFkhMbL4Aihl82kQpfb+a9i/WIZy7FJnkj1gcCZsvfj4qH0qT47gbZBlVSFtF+W7ZKFS/32TWyGnLxcS7ts67M/d0HtGsi7YiBH4q5E0+ESEDfBhtlERydiQgb45xbDje49aB6Ma/result: 7a10f0f6e26b0d6b50f31ff955bcb2a6622afe88
Input.onEnter:
YXBwX3Zlcj0xMDAmbm9uY2U9eDhoMjV2MTcyNzA3ODk3MjI1OSZ0aW1lc3RhbXA9MTcyNzA3ODk3MiZ0enJkPUJ3elh6U0dGeWlQc3RNSVZ1elRaYjdMelRaemJYUkpPRnpwYlFpSWFUN3QvS0RMOVJDYnZIL3ZyMHFkU0UxSU1GWmkvS29Ia1dTeU8yNUdnYXF4Y0tEOFdMcXdnVVRvNmhOM1NMdlR0Ly9uRDNFVzNtS1VwYkZTYWxCYzJKaVhJYXArcS9BVGlvUVplejlwNTNsdHRUQ0RwM0taakhMMElXazdDUVo3U3pReld0QjRFK0d0SFVBcGhoMzBSMC9XTHYrUFZsYUpjNkhyd3k3elpQamVselluaTYraitWQXlOTUUrRTR5bVJ6dVNNNTZ5Vm9JbGIzblBjU0ZncWlaMjM3ejJ1SmhTYklpb1hoM1pGd0E3Y2JHMEtZbHFaVDgwOFBLSURETTcwQldYOURwdHNxRE5INThYdk5zWWlwdWd3OVBja25aaldScDNRT3JWMDZFNHF5ekk0WURkK2xFcVVwUGpOc3Q1dURyTE05R1dtOFRqSzJuNUVGa2hNYkw0QWlobDgya1FwZmIrYTlpL1dJWnk3Rkpua2oxZ2NDWnN2Zmo0cUgwcVQ0N2diWkJsVlNGdEYrVzdaS0ZTLzMyVFd5R25MeGNTN3RzNjdNL2QwSHRHc2k3WWlCSDRxNUUwK0VTRURmQmh0bEVSeWRpUWdiNDV4YkRqZTQ5YUI2TWEvcmVzdWx0OiA3YTEwZjBmNmUyNmIwZDZiNTBmMzFmZjk1NWJjYjJhNjYyMmFmZTg4YjJxS2d0YVc0LDl6OURgRm1zdD9LNUpaYkxZT1ldTlA2c3NHZjJVfjt6azlvQ05nb3l0ViF9d1c3aWErYHc5Zw==
call libtre.so!0x14c9
this.args0 onEnter: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c0ff9c38 53 f3 be e0 1d b4 b2 e2 46 99 ec 81 46 97 dc 8a S.......F...F...
c0ff9c48 eb f2 06 c7 c0 1c 00 00 00 00 00 00 18 00 62 33 ..............b3
c0ff9c58 6c 30 56 69 46 39 64 31 63 33 61 57 45 72 59 48 l0ViF9d1c3aWErYH
c0ff9c68 63 35 5a 77 3d 3d 64 44 39 4c 4e 55 70 61 59 6b c5Zw==dD9LNUpaYk
c0ff9c78 78 5a 54 31 6c 64 54 6c 41 32 63 33 4e 48 5a 6a xZT1ldTlA2c3NHZj
c0ff9c88 4a 56 66 6a 74 36 61 7a 6c 76 51 30 35 6e 00 00 JVfjt6azlvQ05n..
c0ff9c98 00 00 00 00 00 00 00 00 62 32 71 4b 67 74 61 57 ........b2qKgtaW
c0ff9ca8 34 2c 39 7a 39 44 60 46 6d 73 74 3f 4b 35 4a 5a 4,9z9D`Fmst?K5JZ
c0ff9cb8 62 4c 59 4f 59 5d 4e 50 36 73 73 47 66 32 55 7e bLYOY]NP6ssGf2U~
c0ff9cc8 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 21 7d 77 57 ;zk9oCNgoytV!}wW
c0ff9cd8 37 69 61 2b 60 77 39 67 00 00 5c 00 00 00 43 00 7ia+`w9g..\...C.
c0ff9ce8 84 1e 86 cd 00 00 00 00 00 c4 50 dd 18 9e ff c0 ..........P.....
c0ff9cf8 9c 9d ff c0 cc c8 07 e4 02 00 00 00 00 c4 50 dd ..............P.
c0ff9d08 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 24 ba ff c0 .u...(......$...
c0ff9d18 02 00 00 00 c0 f2 12 17 78 b8 38 13 01 00 00 00 ........x.8.....
c0ff9d28 01 00 00 80 e8 a1 0c e4 00 71 d8 c0 00 00 00 00 .........q......
this.args1 onEnter: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c0ff9c24 08 00 00 00 68 9c ff c0 a7 d1 1a b0 70 9c ff c0 ....h.......p...
c0ff9c34 a7 d1 1a b0 53 f3 be e0 1d b4 b2 e2 46 99 ec 81 ....S.......F...
c0ff9c44 46 97 dc 8a eb f2 06 c7 c0 1c 00 00 00 00 00 00 F...............
c0ff9c54 18 00 62 33 6c 30 56 69 46 39 64 31 63 33 61 57 ..b3l0ViF9d1c3aW
c0ff9c64 45 72 59 48 63 35 5a 77 3d 3d 64 44 39 4c 4e 55 ErYHc5Zw==dD9LNU
c0ff9c74 70 61 59 6b 78 5a 54 31 6c 64 54 6c 41 32 63 33 paYkxZT1ldTlA2c3
c0ff9c84 4e 48 5a 6a 4a 56 66 6a 74 36 61 7a 6c 76 51 30 NHZjJVfjt6azlvQ0
c0ff9c94 35 6e 00 00 00 00 00 00 00 00 00 00 62 32 71 4b 5n..........b2qK
c0ff9ca4 67 74 61 57 34 2c 39 7a 39 44 60 46 6d 73 74 3f gtaW4,9z9D`Fmst?
c0ff9cb4 4b 35 4a 5a 62 4c 59 4f 59 5d 4e 50 36 73 73 47 K5JZbLYOY]NP6ssG
c0ff9cc4 66 32 55 7e 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 f2U~;zk9oCNgoytV
c0ff9cd4 21 7d 77 57 37 69 61 2b 60 77 39 67 00 00 5c 00 !}wW7ia+`w9g..\.
c0ff9ce4 00 00 43 00 84 1e 86 cd 00 00 00 00 00 c4 50 dd ..C...........P.
c0ff9cf4 18 9e ff c0 9c 9d ff c0 cc c8 07 e4 02 00 00 00 ................
c0ff9d04 00 c4 50 dd ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 ..P..u...(......
c0ff9d14 24 ba ff c0 02 00 00 00 c0 f2 12 17 78 b8 38 13 $...........x.8.
this.args0 onLeave: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c0ff9c38 f4 35 0d 6d 3f 6b 6d e0 98 8f 9e 97 56 17 fb e6 .5.m?km.....V...
c0ff9c48 ae ba 88 61 00 00 00 00 00 00 00 00 00 00 00 00 ...a............
c0ff9c58 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c68 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c78 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c88 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c98 01 00 00 00 00 00 00 00 62 32 71 4b 67 74 61 57 ........b2qKgtaW
c0ff9ca8 34 2c 39 7a 39 44 60 46 6d 73 74 3f 4b 35 4a 5a 4,9z9D`Fmst?K5JZ
c0ff9cb8 62 4c 59 4f 59 5d 4e 50 36 73 73 47 66 32 55 7e bLYOY]NP6ssGf2U~
c0ff9cc8 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 21 7d 77 57 ;zk9oCNgoytV!}wW
c0ff9cd8 37 69 61 2b 60 77 39 67 00 00 5c 00 00 00 43 00 7ia+`w9g..\...C.
c0ff9ce8 84 1e 86 cd 00 00 00 00 00 c4 50 dd 18 9e ff c0 ..........P.....
c0ff9cf8 9c 9d ff c0 cc c8 07 e4 02 00 00 00 00 c4 50 dd ..............P.
c0ff9d08 ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 24 ba ff c0 .u...(......$...
c0ff9d18 02 00 00 00 c0 f2 12 17 78 b8 38 13 01 00 00 00 ........x.8.....
c0ff9d28 01 00 00 80 e8 a1 0c e4 00 71 d8 c0 00 00 00 00 .........q......
this.args1 onLeave: 0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
c0ff9c24 6d 0d 35 f4 e0 6d 6b 3f 97 9e 8f 98 e6 fb 17 56 m.5..mk?.......V
c0ff9c34 61 88 ba ae f4 35 0d 6d 3f 6b 6d e0 98 8f 9e 97 a....5.m?km.....
c0ff9c44 56 17 fb e6 ae ba 88 61 00 00 00 00 00 00 00 00 V......a........
c0ff9c54 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c64 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c74 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c84 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
c0ff9c94 00 00 00 00 01 00 00 00 00 00 00 00 62 32 71 4b ............b2qK
c0ff9ca4 67 74 61 57 34 2c 39 7a 39 44 60 46 6d 73 74 3f gtaW4,9z9D`Fmst?
c0ff9cb4 4b 35 4a 5a 62 4c 59 4f 59 5d 4e 50 36 73 73 47 K5JZbLYOY]NP6ssG
c0ff9cc4 66 32 55 7e 3b 7a 6b 39 6f 43 4e 67 6f 79 74 56 f2U~;zk9oCNgoytV
c0ff9cd4 21 7d 77 57 37 69 61 2b 60 77 39 67 00 00 5c 00 !}wW7ia+`w9g..\.
c0ff9ce4 00 00 43 00 84 1e 86 cd 00 00 00 00 00 c4 50 dd ..C...........P.
c0ff9cf4 18 9e ff c0 9c 9d ff c0 cc c8 07 e4 02 00 00 00 ................
c0ff9d04 00 c4 50 dd ae 75 8f c5 1b 28 a5 c4 cc c8 07 e4 ..P..u...(......
c0ff9d14 24 ba ff c0 02 00 00 00 c0 f2 12 17 78 b8 38 13 $...........x.8.
retval onLeave: 0x0
result: 6d0d35f4e06d6b3f979e8f98e6fb17566188baae
得到的一大串的字符串,太像base64了,base64解码一下
app_ver=100&nonce=x8h25v1727078972259×tamp=1727078972&tzrd=BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMFZi/KoHkWSyO25GgaqxcKD8WLqwgUTo6hN3SLvTt//nD3EW3mKUpbFSalBc2JiXIap+q/ATioQZez9p53lttTCDp3KZjHL0IWk7CQZ7SzQzWtB4E+GtHUAphh30R0/WLv+PVlaJc6Hrwy7zZPjelzYni6+j+VAyNME+E4ymRzuSM56yVoIlb3nPcSFgqiZ237z2uJhSbIioXh3ZFwA7cbG0KYlqZT808PKIDDM70BWX9DptsqDNH58XvNsYipugw9PcknZjWRp3QOrV06E4qyzI4YDd+lEqUpPjNst5uDrLM9GWm8TjK2n5EFkhMbL4Aihl82kQpfb+a9i/WIZy7FJnkj1gcCZsvfj4qH0qT47gbZBlVSFtF+W7ZKFS/32TWyGnLxcS7ts67M/d0HtGsi7YiBH4q5E0+ESEDfBhtlERydiQgb45xbDje49aB6Ma/b2qKgtaW4,9z9D`FmstK5JZbLYOY]NP6ssGf2U~;zk9oCNgoytV!}wW7ia+`w9g
这里不就是我们抓包的东西吗?
TreUtil.sign:
app_ver=100&nonce=x8h25v1727078972259×tamp=1727078972&tzrd=BwzXzSGFyiPstMIVuzTZb7LzTZzbXRJOFzpbQiIaT7t/KDL9RCbvH/vr0qdSE1IMFZi/KoHkWSyO25GgaqxcKD8WLqwgUTo6hN3SLvTt//nD3EW3mKUpbFSalBc2JiXIap+q/ATioQZez9p53lttTCDp3KZjHL0IWk7CQZ7SzQzWtB4E+GtHUAphh30R0/WLv+PVlaJc6Hrwy7zZPjelzYni6+j+VAyNME+E4ymRzuSM56yVoIlb3nPcSFgqiZ237z2uJhSbIioXh3ZFwA7cbG0KYlqZT808PKIDDM70BWX9DptsqDNH58XvNsYipugw9PcknZjWRp3QOrV06E4qyzI4YDd+lEqUpPjNst5uDrLM9GWm8TjK2n5EFkhMbL4Aihl82kQpfb+a9i/WIZy7FJnkj1gcCZsvfj4qH0qT47gbZBlVSFtF+W7ZKFS/32TWyGnLxcS7ts67M/d0HtGsi7YiBH4q5E0+ESEDfBhtlERydiQgb45xbDje49aB6Ma/
但是多了b2qKgtaW4,9z9DFmstK5JZbLYOY]NP6ssGf2U~;zk9oCNgoytV!}wW7ia+w9g
原因:
strcpy(context_104, "b2qKgtaW4,9z9D`Fmst?K5JZbLYOY]NP6ssGf2U~;zk9oCNgoytV!}wW7ia+`w9g");
v5 = (*(a1->reserved0 + 169))(a1, a3, &v22);
v6 = 0;
if ( v5 )
{
v21 = &_stack_chk_guard;
v7 = v5;
v19[0] = a3;
v8 = strlen(context_104);
v19[1] = v19;
v9 = v19 - ((strlen(v7) + v8 + 8) & 0xFFFFFFF8);
strcpy(v9, v7);
strcat(v9, context_104);
总结
抓包的所有东西都能伪造了,其次就是填上"b2qKgtaW4,9z9DFmst?K5JZbLYOY]NP6ssGf2U~;zk9oCNgoytV!}wW7ia+w9g"的结果SHA1,得到的结果就是sign。




