利用内存锁定技术防止CE修改
利用内存锁定技术防止CE修改
通过这种在R3环利用的技术,我们可以来达到保护内存的目的,像VirtualProtect等函数来修改页属性根本无法修改。
而CE修改器推测应该使用VirtualProtect来修改页属性,从而可以修改内存。
当然,这种技术在R0层面是可以修改的(当然修改起来也有一定难度)
原理这里先说明自己还不太清除,但弄清楚之后会补上的。
先展示源代码,后展示效果
1 // 内存锁定.cpp : Defines the entry point for the console application. 2 // 3 4 #include "stdafx.h" 5 #include <stdio.h> 6 #include <Windows.h> 7 #include <stdlib.h> 8 9 #define InitializeObjectAttributes( p, n, a, r, s ) { \ 10 (p)->Length = sizeof( OBJECT_ATTRIBUTES ); \ 11 (p)->RootDirectory = r; \ 12 (p)->Attributes = a; \ 13 (p)->ObjectName = n; \ 14 (p)->SecurityDescriptor = s; \ 15 (p)->SecurityQualityOfService = NULL; \ 16 } 17 typedef struct _UNICODE_STRING { 18 USHORT Length; 19 USHORT MaximumLength; 20 PWSTR Buffer; 21 } UNICODE_STRING, *PUNICODE_STRING; 22 23 typedef struct _OBJECT_ATTRIBUTES { 24 ULONG Length; 25 HANDLE RootDirectory; 26 PUNICODE_STRING ObjectName; 27 ULONG Attributes; 28 PVOID SecurityDescriptor; 29 PVOID SecurityQualityOfService; 30 } OBJECT_ATTRIBUTES, *POBJECT_ATTRIBUTES; 31 32 typedef DWORD (WINAPI*ZwCreateSectionProc)( 33 PHANDLE SectionHandle, 34 ACCESS_MASK DesiredAccess, 35 POBJECT_ATTRIBUTES ObjectAttributes, 36 PLARGE_INTEGER MaximumSize, 37 ULONG SectionPageProtection, 38 ULONG AllocationAttributes, 39 HANDLE FileHandle 40 ); 41 42 typedef enum _SECTION_INHERIT { 43 ViewShare = 1, 44 ViewUnmap = 2 45 } SECTION_INHERIT; 46 47 typedef DWORD (WINAPI *ZwMapViewOfSectionProc)( 48 HANDLE SectionHandle, 49 HANDLE ProcessHandle, 50 PVOID *BaseAddress, 51 ULONG_PTR ZeroBits, 52 SIZE_T CommitSize, 53 PLARGE_INTEGER SectionOffset, 54 PSIZE_T ViewSize, 55 SECTION_INHERIT InheritDisposition, 56 ULONG AllocationType, 57 ULONG Win32Protect 58 ); 59 int main() 60 { 61 HMODULE h = LoadLibraryA("ntdll.dll"); 62 ZwCreateSectionProc ZwCreateSection = (ZwCreateSectionProc)GetProcAddress(h, "NtCreateSection"); 63 ZwMapViewOfSectionProc ZwMapViewOfSection = (ZwMapViewOfSectionProc)GetProcAddress(h, "ZwMapViewOfSection"); 64 HANDLE SectionHandle; 65 LARGE_INTEGER MaximumSize = { 0 }; 66 MaximumSize.QuadPart = 0x10000; 67 OBJECT_ATTRIBUTES obj = { 0 }; 68 InitializeObjectAttributes(&obj, NULL, 0x40, 0, 0); 69 DWORD error = ZwCreateSection(&SectionHandle, SECTION_ALL_ACCESS, NULL, &MaximumSize, PAGE_EXECUTE_READ, SEC_COMMIT, NULL); 70 PVOID BaseAddress = NULL; 71 SIZE_T ViewSize = 0; 72 error = ZwMapViewOfSection(SectionHandle, GetCurrentProcess(), &BaseAddress, 0, 73 0x10000, NULL, &ViewSize, (SECTION_INHERIT)1, 0, PAGE_EXECUTE_READ); 74 printf("%x,%x\r\n", BaseAddress, SectionHandle); 75 DWORD p = 0; 76 error = VirtualProtect(BaseAddress, 0x10000, PAGE_EXECUTE_READWRITE, &p); 77 system("pause"); 78 return 0; 80 }
1. 代码运行结果:
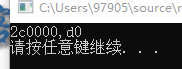
2. 使用CE来修改
1)用CE附加。
2)查看内存。
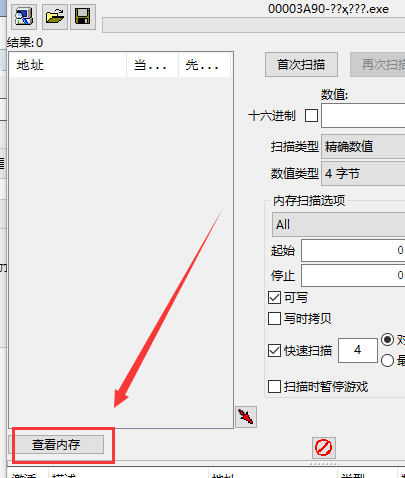
3)点击“视图 -> 内存区域”。
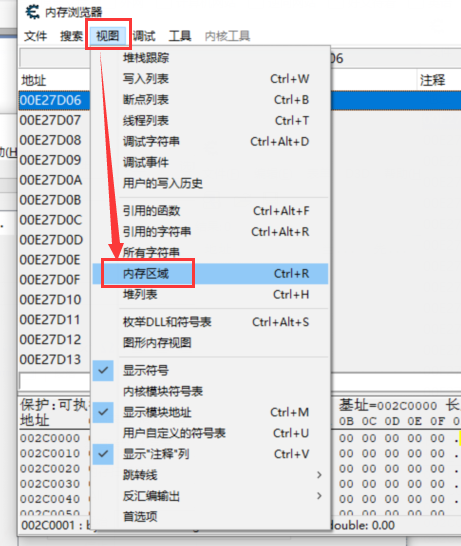
4)选中目标区域内存,左键修改,则明显无法修改。
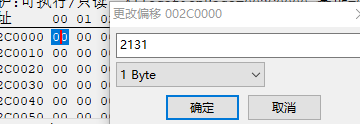
3. 同时根据内存属性可以看到,其使用 VirtualProtect 将内存页属性置为 PAGE_EXECUTE_READWRITE, 明显无效。
1)代码修改的
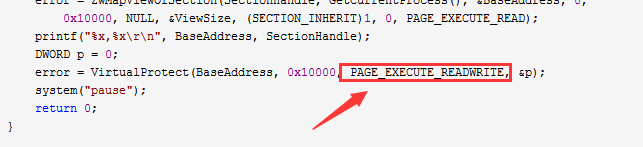
2)内存显示的
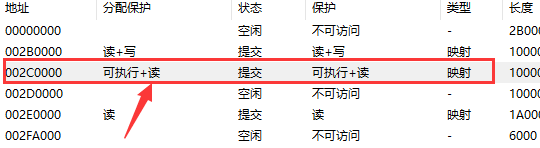
4. 后记:其实这种技术在R0层是可以修改的,之后我们会详细介绍。

