“科来杯”第九届山东省大学生网络安全技能大赛决赛部分wp
1.损坏的流量包
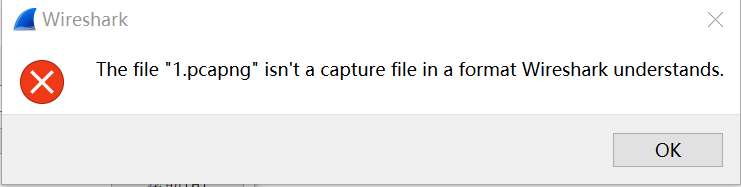
wireshark打不开,丢进winhex里,找关键字flag
哎,没找到。
那就仔细看看,在最后发现一串类似base64的密文
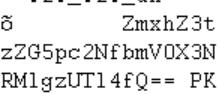
base64解密
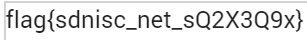
得到flag
2.签到题
一个游戏,

查看源码,发现有一个提示
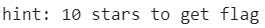
10课星星获得flag,玩十关再查看源码得到flag
听说可以改代码,但我太菜了,我是打到第十关得到的flag,后期会尽量学会然后更新的!
3.ctf的起源
base64隐写,之前前面有详细总结过,这里就不多说了
脚本跑出flag
import base64 b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' with open('flag.txt', 'rb') as f: bin_str = '' for line in f.readlines(): stegb64 = str(line, "utf-8").strip("\n") rowb64 = str(base64.b64encode(base64.b64decode(stegb64)), "utf-8").strip("\n") offset = abs(b64chars.index(stegb64.replace('=','')[-1])-b64chars.index(rowb64.replace('=','')[-1])) equalnum = stegb64.count('=') #no equalnum no offset if equalnum: bin_str += bin(offset)[2:].zfill(equalnum * 2) print (''.join([chr(int(bin_str[i:i + 8], 2)) for i in range(0, len(bin_str), 8)]))
#flag{944776b2c95a350bb27d7038d42b273a}
4.简单的rsa
rsa共模攻击
直接上脚本
# -*- coding: utf-8 -*- """ Created on Tue Nov 3 20:11:03 2020 @author: zhao """ import libnum from gmpy2 import invert # 欧几里得算法 def egcd(a, b): if a == 0: return (b, 0, 1) else: g, y, x = egcd(b % a, a) return (g, x - (b // a) * y, y) def main(): n = 20429315528655111523073560675648813309162375303954090348572329091957960032412518712093691044501240262294304779722690063594446637140928522882936561204180425968593685714138402078212148627806816974924904301217144262198933589412344408694401386330925556100970326676200349102533012051159456051076045413561059070291766268594455676378031127514060030926838750670330939410961355756909171469945402924037610757364146531235448523106870829710488056210511070536574177473906753241807683881800419949735443822439277498329376433536971257102334607742626401589209417830185425783917209141580607207923687068496513264733739213966151881471319 c1 = 12051796366524088489284445109295502686341498426965277230069915294159131976231473789977279364263965099422235647723775278060569378071469131866368399394772898224166518089593340803913798327451963589996734323497943301819051718709807518655868569656941242449109980876397661605271517459716669684900920279597477446629607627693769738733623143693170696779851882404994923673483971528314806130892416509854017091137325195201225617407959645788145876202882024723106204183257094755002924708009138560347432552090905489132135154932987521239299578509008290614398700799670928805692609756924823628055245227290288940649158862576448537833423 c2 = 16648382384980770705624348910895797622774711113202207693584907182552301186239613809347201161450012615995859738410661452438496756353485538305614949211776668793864984429696790944750894691957799234264508530084026894611228513698963347402329109838109621609770406925700520983387811451074838470370044678634099202003480925903267508744006195455234025325060817223813858985074720872124168142943926467694676717713503559007112874381750005406371400109962943508349497151148446064846096531445037416174913915923050332242843403926133165817310272633884358263778516770288515592959832151762499526363131801945163501999337808208074381212795 e1 = 4106294671 e2 = 4103337937 s = egcd(e1, e2) s1 = s[1] s2 = s[2] # 求模反元素 if s1<0: s1 = - s1 c1 = invert(c1, n) elif s2<0: s2 = - s2 c2 = invert(c2, n) m = pow(c1,s1,n)*pow(c2,s2,n) % n m=int(m) print (libnum.n2s(m)) if __name__ == '__main__': main()
得到flag
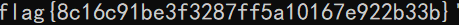
第一次参加这种比赛,见识了大佬们的风采,老萌新瑟瑟发抖,努力不做老萌新!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号