NFS搭建共享-ssh免密连接
综合架构学习笔记-4-NFS
1.NFS是什么?
存储,部署这个软件可以实现 客户机可以访问远程服务器共享资源
2.优点 缺点
优点:免费 配置方便 满足做架构方案
缺点:使用明文传输 不安全
3.nfs使用场景
1.做负载均衡会用到
2.数据备份
实战部分
4.生产部署实战---重点
存储:10.0.1.134
web服务器:10.0.1.100
开始部署:
NFS存储服务器端
1.
yum install -y nfs-utils
[root@master ~]# yum -y install nfs-utils
Loaded plugins: fastestmirror
base | 3.6 kB 00:00:00
extras | 2.9 kB 00:00:00
updates | 2.9 kB 00:00:00
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
Resolving Dependencies
--> Running transaction check
---> Package nfs-utils.x86_64 1:1.3.0-0.68.el7.2 will be installed
--> Processing Dependency: gssproxy >= 0.7.0-3 for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: rpcbind for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: quota for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libnfsidmap for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libevent for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: keyutils for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libnfsidmap.so.0()(64bit) for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libevent-2.0.so.5()(64bit) for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Running transaction check
---> Package gssproxy.x86_64 0:0.7.0-30.el7_9 will be installed
--> Processing Dependency: libini_config >= 1.3.1-31 for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: krb5-libs >= 1.15 for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libverto-module-base for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libref_array.so.1(REF_ARRAY_0.1.1)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3(INI_CONFIG_1.2.0)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3(INI_CONFIG_1.1.0)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libref_array.so.1()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libcollection.so.2()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libbasicobjects.so.0()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
---> Package keyutils.x86_64 0:1.5.8-3.el7 will be installed
---> Package libevent.x86_64 0:2.0.21-4.el7 will be installed
---> Package libnfsidmap.x86_64 0:0.25-19.el7 will be installed
---> Package quota.x86_64 1:4.01-19.el7 will be installed
--> Processing Dependency: quota-nls = 1:4.01-19.el7 for package: 1:quota-4.01-19.el7.x86_64
--> Processing Dependency: tcp_wrappers for package: 1:quota-4.01-19.el7.x86_64
---> Package rpcbind.x86_64 0:0.2.0-49.el7 will be installed
--> Running transaction check
---> Package krb5-libs.x86_64 0:1.12.2-14.el7 will be updated
---> Package krb5-libs.x86_64 0:1.15.1-55.el7_9 will be an update
---> Package libbasicobjects.x86_64 0:0.1.1-32.el7 will be installed
---> Package libcollection.x86_64 0:0.7.0-32.el7 will be installed
---> Package libini_config.x86_64 0:1.3.1-32.el7 will be installed
--> Processing Dependency: libpath_utils.so.1(PATH_UTILS_0.2.1)(64bit) for package: libini_config-1.3.1-32.el7.x86_64
--> Processing Dependency: libpath_utils.so.1()(64bit) for package: libini_config-1.3.1-32.el7.x86_64
---> Package libref_array.x86_64 0:0.1.5-32.el7 will be installed
---> Package libverto-libevent.x86_64 0:0.2.5-4.el7 will be installed
---> Package quota-nls.noarch 1:4.01-19.el7 will be installed
---> Package tcp_wrappers.x86_64 0:7.6-77.el7 will be installed
--> Running transaction check
---> Package libpath_utils.x86_64 0:0.2.1-32.el7 will be installed
--> Processing Conflict: gssproxy-0.7.0-30.el7_9.x86_64 conflicts selinux-policy < 3.13.1-166.el7.noarch
--> Restarting Dependency Resolution with new changes.
--> Running transaction check
---> Package selinux-policy.noarch 0:3.13.1-23.el7 will be updated
--> Processing Dependency: selinux-policy = 3.13.1-23.el7 for package: selinux-policy-targeted-3.13.1-23.el7.noarch
--> Processing Dependency: selinux-policy = 3.13.1-23.el7 for package: selinux-policy-targeted-3.13.1-23.el7.noarch
---> Package selinux-policy.noarch 0:3.13.1-268.el7_9.2 will be an update
--> Processing Dependency: policycoreutils >= 2.5-24 for package: selinux-policy-3.13.1-268.el7_9.2.noarch
--> Processing Dependency: libsemanage >= 2.5-13 for package: selinux-policy-3.13.1-268.el7_9.2.noarch
--> Running transaction check
---> Package libsemanage.x86_64 0:2.1.10-16.el7 will be updated
---> Package libsemanage.x86_64 0:2.5-14.el7 will be an update
--> Processing Dependency: libsepol >= 2.5-10 for package: libsemanage-2.5-14.el7.x86_64
--> Processing Dependency: libselinux >= 2.5-14 for package: libsemanage-2.5-14.el7.x86_64
--> Processing Dependency: libsepol.so.1(LIBSEPOL_1.1)(64bit) for package: libsemanage-2.5-14.el7.x86_64
--> Processing Dependency: libsepol.so.1(LIBSEPOL_1.0)(64bit) for package: libsemanage-2.5-14.el7.x86_64
---> Package policycoreutils.x86_64 0:2.2.5-15.el7 will be updated
---> Package policycoreutils.x86_64 0:2.5-34.el7 will be an update
--> Processing Dependency: libselinux-utils >= 2.5-14 for package: policycoreutils-2.5-34.el7.x86_64
---> Package selinux-policy-targeted.noarch 0:3.13.1-23.el7 will be updated
---> Package selinux-policy-targeted.noarch 0:3.13.1-268.el7_9.2 will be an update
--> Running transaction check
---> Package libselinux.x86_64 0:2.2.2-6.el7 will be updated
--> Processing Dependency: libselinux = 2.2.2-6.el7 for package: libselinux-python-2.2.2-6.el7.x86_64
---> Package libselinux.x86_64 0:2.5-15.el7 will be an update
---> Package libselinux-utils.x86_64 0:2.2.2-6.el7 will be updated
---> Package libselinux-utils.x86_64 0:2.5-15.el7 will be an update
---> Package libsepol.x86_64 0:2.1.9-3.el7 will be updated
---> Package libsepol.x86_64 0:2.5-10.el7 will be an update
--> Running transaction check
---> Package libselinux-python.x86_64 0:2.2.2-6.el7 will be updated
---> Package libselinux-python.x86_64 0:2.5-15.el7 will be an update
--> Finished Dependency Resolution
Dependencies Resolved
===========================================================================================================
Package Arch Version Repository Size
===========================================================================================================
Installing:
nfs-utils x86_64 1:1.3.0-0.68.el7.2 updates 413 k
Updating:
selinux-policy noarch 3.13.1-268.el7_9.2 updates 498 k
Installing for dependencies:
gssproxy x86_64 0.7.0-30.el7_9 updates 111 k
keyutils x86_64 1.5.8-3.el7 base 54 k
libbasicobjects x86_64 0.1.1-32.el7 base 26 k
libcollection x86_64 0.7.0-32.el7 base 42 k
libevent x86_64 2.0.21-4.el7 base 214 k
libini_config x86_64 1.3.1-32.el7 base 64 k
libnfsidmap x86_64 0.25-19.el7 base 50 k
libpath_utils x86_64 0.2.1-32.el7 base 28 k
libref_array x86_64 0.1.5-32.el7 base 27 k
libverto-libevent x86_64 0.2.5-4.el7 base 8.9 k
quota x86_64 1:4.01-19.el7 base 179 k
quota-nls noarch 1:4.01-19.el7 base 90 k
rpcbind x86_64 0.2.0-49.el7 base 60 k
tcp_wrappers x86_64 7.6-77.el7 base 78 k
Updating for dependencies:
krb5-libs x86_64 1.15.1-55.el7_9 updates 810 k
libselinux x86_64 2.5-15.el7 base 162 k
libselinux-python x86_64 2.5-15.el7 base 236 k
libselinux-utils x86_64 2.5-15.el7 base 151 k
libsemanage x86_64 2.5-14.el7 base 151 k
libsepol x86_64 2.5-10.el7 base 297 k
policycoreutils x86_64 2.5-34.el7 base 917 k
selinux-policy-targeted noarch 3.13.1-268.el7_9.2 updates 7.0 M
Transaction Summary
===========================================================================================================
Install 1 Package (+14 Dependent packages)
Upgrade 1 Package (+ 8 Dependent packages)
Total size: 12 M
Total download size: 1.4 M
Downloading packages:
(1/15): libbasicobjects-0.1.1-32.el7.x86_64.rpm | 26 kB 00:00:02
(2/15): keyutils-1.5.8-3.el7.x86_64.rpm | 54 kB 00:00:02
(3/15): libcollection-0.7.0-32.el7.x86_64.rpm | 42 kB 00:00:00
(4/15): gssproxy-0.7.0-30.el7_9.x86_64.rpm | 111 kB 00:00:02
(5/15): libini_config-1.3.1-32.el7.x86_64.rpm | 64 kB 00:00:00
(6/15): libnfsidmap-0.25-19.el7.x86_64.rpm | 50 kB 00:00:00
(7/15): libpath_utils-0.2.1-32.el7.x86_64.rpm | 28 kB 00:00:00
(8/15): libevent-2.0.21-4.el7.x86_64.rpm | 214 kB 00:00:00
(9/15): libverto-libevent-0.2.5-4.el7.x86_64.rpm | 8.9 kB 00:00:00
(10/15): libref_array-0.1.5-32.el7.x86_64.rpm | 27 kB 00:00:00
(11/15): quota-nls-4.01-19.el7.noarch.rpm | 90 kB 00:00:00
(12/15): quota-4.01-19.el7.x86_64.rpm | 179 kB 00:00:00
(13/15): rpcbind-0.2.0-49.el7.x86_64.rpm | 60 kB 00:00:00
(14/15): tcp_wrappers-7.6-77.el7.x86_64.rpm | 78 kB 00:00:00
(15/15): nfs-utils-1.3.0-0.68.el7.2.x86_64.rpm | 413 kB 00:00:03
-----------------------------------------------------------------------------------------------------------
Total 238 kB/s | 1.4 MB 00:00:06
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Updating : libsepol-2.5-10.el7.x86_64 1/33
Updating : libselinux-2.5-15.el7.x86_64 2/33
Updating : krb5-libs-1.15.1-55.el7_9.x86_64 3/33
Updating : libsemanage-2.5-14.el7.x86_64 4/33
Installing : libref_array-0.1.5-32.el7.x86_64 5/33
Installing : libcollection-0.7.0-32.el7.x86_64 6/33
Installing : libevent-2.0.21-4.el7.x86_64 7/33
Installing : rpcbind-0.2.0-49.el7.x86_64 8/33
Installing : libbasicobjects-0.1.1-32.el7.x86_64 9/33
Installing : libverto-libevent-0.2.5-4.el7.x86_64 10/33
Updating : libselinux-utils-2.5-15.el7.x86_64 11/33
Updating : policycoreutils-2.5-34.el7.x86_64 12/33
Updating : selinux-policy-3.13.1-268.el7_9.2.noarch 13/33
Installing : 1:quota-nls-4.01-19.el7.noarch 14/33
Installing : tcp_wrappers-7.6-77.el7.x86_64 15/33
Installing : 1:quota-4.01-19.el7.x86_64 16/33
Installing : keyutils-1.5.8-3.el7.x86_64 17/33
Installing : libnfsidmap-0.25-19.el7.x86_64 18/33
Installing : libpath_utils-0.2.1-32.el7.x86_64 19/33
Installing : libini_config-1.3.1-32.el7.x86_64 20/33
Installing : gssproxy-0.7.0-30.el7_9.x86_64 21/33
Installing : 1:nfs-utils-1.3.0-0.68.el7.2.x86_64 22/33
Updating : selinux-policy-targeted-3.13.1-268.el7_9.2.noarch 23/33
Updating : libselinux-python-2.5-15.el7.x86_64 24/33
Cleanup : selinux-policy-targeted-3.13.1-23.el7.noarch 25/33
Cleanup : selinux-policy-3.13.1-23.el7.noarch 26/33
Cleanup : policycoreutils-2.2.5-15.el7.x86_64 27/33
Cleanup : libsemanage-2.1.10-16.el7.x86_64 28/33
Cleanup : libselinux-utils-2.2.2-6.el7.x86_64 29/33
Cleanup : libselinux-python-2.2.2-6.el7.x86_64 30/33
Cleanup : krb5-libs-1.12.2-14.el7.x86_64 31/33
Cleanup : libselinux-2.2.2-6.el7.x86_64 32/33
Cleanup : libsepol-2.1.9-3.el7.x86_64 33/33
Verifying : gssproxy-0.7.0-30.el7_9.x86_64 1/33
Verifying : libselinux-2.5-15.el7.x86_64 2/33
Verifying : libbasicobjects-0.1.1-32.el7.x86_64 3/33
Verifying : selinux-policy-targeted-3.13.1-268.el7_9.2.noarch 4/33
Verifying : rpcbind-0.2.0-49.el7.x86_64 5/33
Verifying : 1:nfs-utils-1.3.0-0.68.el7.2.x86_64 6/33
Verifying : policycoreutils-2.5-34.el7.x86_64 7/33
Verifying : libsepol-2.5-10.el7.x86_64 8/33
Verifying : libselinux-utils-2.5-15.el7.x86_64 9/33
Verifying : libini_config-1.3.1-32.el7.x86_64 10/33
Verifying : krb5-libs-1.15.1-55.el7_9.x86_64 11/33
Verifying : libevent-2.0.21-4.el7.x86_64 12/33
Verifying : libselinux-python-2.5-15.el7.x86_64 13/33
Verifying : libsemanage-2.5-14.el7.x86_64 14/33
Verifying : libverto-libevent-0.2.5-4.el7.x86_64 15/33
Verifying : libcollection-0.7.0-32.el7.x86_64 16/33
Verifying : libref_array-0.1.5-32.el7.x86_64 17/33
Verifying : selinux-policy-3.13.1-268.el7_9.2.noarch 18/33
Verifying : libpath_utils-0.2.1-32.el7.x86_64 19/33
Verifying : 1:quota-4.01-19.el7.x86_64 20/33
Verifying : libnfsidmap-0.25-19.el7.x86_64 21/33
Verifying : keyutils-1.5.8-3.el7.x86_64 22/33
Verifying : tcp_wrappers-7.6-77.el7.x86_64 23/33
Verifying : 1:quota-nls-4.01-19.el7.noarch 24/33
Verifying : selinux-policy-targeted-3.13.1-23.el7.noarch 25/33
Verifying : policycoreutils-2.2.5-15.el7.x86_64 26/33
Verifying : selinux-policy-3.13.1-23.el7.noarch 27/33
Verifying : libselinux-utils-2.2.2-6.el7.x86_64 28/33
Verifying : libselinux-python-2.2.2-6.el7.x86_64 29/33
Verifying : libsemanage-2.1.10-16.el7.x86_64 30/33
Verifying : libsepol-2.1.9-3.el7.x86_64 31/33
Verifying : krb5-libs-1.12.2-14.el7.x86_64 32/33
Verifying : libselinux-2.2.2-6.el7.x86_64 33/33
Installed:
nfs-utils.x86_64 1:1.3.0-0.68.el7.2
Dependency Installed:
gssproxy.x86_64 0:0.7.0-30.el7_9 keyutils.x86_64 0:1.5.8-3.el7
libbasicobjects.x86_64 0:0.1.1-32.el7 libcollection.x86_64 0:0.7.0-32.el7
libevent.x86_64 0:2.0.21-4.el7 libini_config.x86_64 0:1.3.1-32.el7
libnfsidmap.x86_64 0:0.25-19.el7 libpath_utils.x86_64 0:0.2.1-32.el7
libref_array.x86_64 0:0.1.5-32.el7 libverto-libevent.x86_64 0:0.2.5-4.el7
quota.x86_64 1:4.01-19.el7 quota-nls.noarch 1:4.01-19.el7
rpcbind.x86_64 0:0.2.0-49.el7 tcp_wrappers.x86_64 0:7.6-77.el7
Updated:
selinux-policy.noarch 0:3.13.1-268.el7_9.2
Dependency Updated:
krb5-libs.x86_64 0:1.15.1-55.el7_9 libselinux.x86_64 0:2.5-15.el7
libselinux-python.x86_64 0:2.5-15.el7 libselinux-utils.x86_64 0:2.5-15.el7
libsemanage.x86_64 0:2.5-14.el7 libsepol.x86_64 0:2.5-10.el7
policycoreutils.x86_64 0:2.5-34.el7 selinux-policy-targeted.noarch 0:3.13.1-268.el7_9.2
Complete!
mkdir /data 创建共享目录
vim /etc/exports
把下面这条复制进去,ip段不要搞错了
/data 10.0.1.0/24(rw,sync,no_root_squash,no_all_squash)
/data 共享目录
10.0.1.0/24 授权ip
rw 允许读写
sync 同步内存和硬盘
no_root_squash 客户机root身份访问本地权限 不加这个没有写入权限
no_all_squash 所有用户不能用匿名访问
命令详解 该命令是在NFS(Network File System,网络文件系统)服务器配置中的一条规则,用于定义对特定网络地址的共享目录访问权限。具体解释如下:
- `/data`:这是NFS服务器上要共享出去的目录路径。
- `10.0.1.0/24`:这是一个CIDR表示法的IP地址范围,指允许从10.0.1.0到10.0.1.255这个子网段内的所有主机可以访问此共享目录。
- `(rw)`:表明客户端对该共享目录具有读写权限,即可以读取和修改共享目录中的文件。
- `(sync)`:同步模式,要求数据在写入共享目录时必须先写入硬盘,然后再返回确认信息给客户端。这样虽然会降低性能但提供了最大程度的数据一致性保障。
- `(no_root_squash)`:不进行root用户映射,意味着来自客户端的root用户请求将被直接以服务器上的root用户权限处理。如果不设置此选项,通常会将远程root用户的权限映射为一个非特权用户。
- `(no_all_squash)`:不进行普通用户映射,意味着来自客户端的所有用户都将保持其原有的用户ID和组ID进行操作。如果设置了`all_squash`,则无论客户端使用何种用户身份连接,都会被映射为匿名用户或用户组。
综上所述,这条命令配置了NFS服务器将/data目录共享给10.0.1.0/24子网段内的所有主机,并且这些主机可以以原始用户身份读写该共享目录,同时保证数据操作的同步性且不对root用户的权限进行限制。
systemctl restart rpcbind
systemctl restart nfs
或者
systemctl start rpcbind
systemctl start nfs
systemctl enable rpcbind
systemctl enable nfs
2、检查 NFS 服务器端是否有目录共享
服务器端ip 10.0.1.134
showmount -e 10.0.0.134
[root@master data]# showmount -e 10.0.1.134
Export list for 10.0.1.134:
/data 10.0.1.0/24
客户端执行
1、安装nfs,不需要启动服务
yum install -y nfs-utils
[root@node ~]# yum -y install nfs-utils
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
base | 3.6 kB 00:00:00
epel | 4.7 kB 00:00:00
extras | 2.9 kB 00:00:00
updates | 2.9 kB 00:00:00
(1/2): epel/x86_64/updateinfo | 1.0 MB 00:00:03
(2/2): epel/x86_64/primary_db | 7.0 MB 00:00:17
Resolving Dependencies
--> Running transaction check
---> Package nfs-utils.x86_64 1:1.3.0-0.68.el7.2 will be installed
--> Processing Dependency: libtirpc >= 0.2.4-0.7 for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: gssproxy >= 0.7.0-3 for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: rpcbind for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: quota for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libnfsidmap for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libevent for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: keyutils for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libtirpc.so.1()(64bit) for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libnfsidmap.so.0()(64bit) for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Processing Dependency: libevent-2.0.so.5()(64bit) for package: 1:nfs-utils-1.3.0-0.68.el7.2.x86_64
--> Running transaction check
---> Package gssproxy.x86_64 0:0.7.0-30.el7_9 will be installed
--> Processing Dependency: libini_config >= 1.3.1-31 for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libverto-module-base for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libref_array.so.1(REF_ARRAY_0.1.1)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3(INI_CONFIG_1.2.0)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3(INI_CONFIG_1.1.0)(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libref_array.so.1()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libini_config.so.3()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libcollection.so.2()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
--> Processing Dependency: libbasicobjects.so.0()(64bit) for package: gssproxy-0.7.0-30.el7_9.x86_64
---> Package keyutils.x86_64 0:1.5.8-3.el7 will be installed
---> Package libevent.x86_64 0:2.0.21-4.el7 will be installed
---> Package libnfsidmap.x86_64 0:0.25-19.el7 will be installed
---> Package libtirpc.x86_64 0:0.2.4-0.16.el7 will be installed
---> Package quota.x86_64 1:4.01-19.el7 will be installed
--> Processing Dependency: quota-nls = 1:4.01-19.el7 for package: 1:quota-4.01-19.el7.x86_64
--> Processing Dependency: tcp_wrappers for package: 1:quota-4.01-19.el7.x86_64
---> Package rpcbind.x86_64 0:0.2.0-49.el7 will be installed
--> Running transaction check
---> Package libbasicobjects.x86_64 0:0.1.1-32.el7 will be installed
---> Package libcollection.x86_64 0:0.7.0-32.el7 will be installed
---> Package libini_config.x86_64 0:1.3.1-32.el7 will be installed
--> Processing Dependency: libpath_utils.so.1(PATH_UTILS_0.2.1)(64bit) for package: libini_config-1.3.1-32.el7.x86_64
--> Processing Dependency: libpath_utils.so.1()(64bit) for package: libini_config-1.3.1-32.el7.x86_64
---> Package libref_array.x86_64 0:0.1.5-32.el7 will be installed
---> Package libverto-libevent.x86_64 0:0.2.5-4.el7 will be installed
---> Package quota-nls.noarch 1:4.01-19.el7 will be installed
---> Package tcp_wrappers.x86_64 0:7.6-77.el7 will be installed
--> Running transaction check
---> Package libpath_utils.x86_64 0:0.2.1-32.el7 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
===========================================================================================================
Package Arch Version Repository Size
===========================================================================================================
Installing:
nfs-utils x86_64 1:1.3.0-0.68.el7.2 updates 413 k
Installing for dependencies:
gssproxy x86_64 0.7.0-30.el7_9 updates 111 k
keyutils x86_64 1.5.8-3.el7 base 54 k
libbasicobjects x86_64 0.1.1-32.el7 base 26 k
libcollection x86_64 0.7.0-32.el7 base 42 k
libevent x86_64 2.0.21-4.el7 base 214 k
libini_config x86_64 1.3.1-32.el7 base 64 k
libnfsidmap x86_64 0.25-19.el7 base 50 k
libpath_utils x86_64 0.2.1-32.el7 base 28 k
libref_array x86_64 0.1.5-32.el7 base 27 k
libtirpc x86_64 0.2.4-0.16.el7 base 89 k
libverto-libevent x86_64 0.2.5-4.el7 base 8.9 k
quota x86_64 1:4.01-19.el7 base 179 k
quota-nls noarch 1:4.01-19.el7 base 90 k
rpcbind x86_64 0.2.0-49.el7 base 60 k
tcp_wrappers x86_64 7.6-77.el7 base 78 k
Transaction Summary
===========================================================================================================
Install 1 Package (+15 Dependent packages)
Total download size: 1.5 M
Installed size: 4.3 M
Downloading packages:
(1/16): libbasicobjects-0.1.1-32.el7.x86_64.rpm | 26 kB 00:00:00
(2/16): keyutils-1.5.8-3.el7.x86_64.rpm | 54 kB 00:00:00
(3/16): libcollection-0.7.0-32.el7.x86_64.rpm | 42 kB 00:00:00
(4/16): libini_config-1.3.1-32.el7.x86_64.rpm | 64 kB 00:00:00
(5/16): libnfsidmap-0.25-19.el7.x86_64.rpm | 50 kB 00:00:00
(6/16): libpath_utils-0.2.1-32.el7.x86_64.rpm | 28 kB 00:00:00
(7/16): libevent-2.0.21-4.el7.x86_64.rpm | 214 kB 00:00:00
(8/16): libref_array-0.1.5-32.el7.x86_64.rpm | 27 kB 00:00:00
(9/16): libverto-libevent-0.2.5-4.el7.x86_64.rpm | 8.9 kB 00:00:00
(10/16): libtirpc-0.2.4-0.16.el7.x86_64.rpm | 89 kB 00:00:00
(11/16): quota-nls-4.01-19.el7.noarch.rpm | 90 kB 00:00:00
(12/16): gssproxy-0.7.0-30.el7_9.x86_64.rpm | 111 kB 00:00:01
(13/16): rpcbind-0.2.0-49.el7.x86_64.rpm | 60 kB 00:00:00
(14/16): quota-4.01-19.el7.x86_64.rpm | 179 kB 00:00:00
(15/16): tcp_wrappers-7.6-77.el7.x86_64.rpm | 78 kB 00:00:00
(16/16): nfs-utils-1.3.0-0.68.el7.2.x86_64.rpm | 413 kB 00:00:01
-----------------------------------------------------------------------------------------------------------
Total 549 kB/s | 1.5 MB 00:00:02
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : libbasicobjects-0.1.1-32.el7.x86_64 1/16
Installing : libref_array-0.1.5-32.el7.x86_64 2/16
Installing : libcollection-0.7.0-32.el7.x86_64 3/16
Installing : libevent-2.0.21-4.el7.x86_64 4/16
Installing : libtirpc-0.2.4-0.16.el7.x86_64 5/16
Installing : rpcbind-0.2.0-49.el7.x86_64 6/16
Installing : libverto-libevent-0.2.5-4.el7.x86_64 7/16
Installing : 1:quota-nls-4.01-19.el7.noarch 8/16
Installing : tcp_wrappers-7.6-77.el7.x86_64 9/16
Installing : 1:quota-4.01-19.el7.x86_64 10/16
Installing : keyutils-1.5.8-3.el7.x86_64 11/16
Installing : libnfsidmap-0.25-19.el7.x86_64 12/16
Installing : libpath_utils-0.2.1-32.el7.x86_64 13/16
Installing : libini_config-1.3.1-32.el7.x86_64 14/16
Installing : gssproxy-0.7.0-30.el7_9.x86_64 15/16
Installing : 1:nfs-utils-1.3.0-0.68.el7.2.x86_64 16/16
Verifying : libtirpc-0.2.4-0.16.el7.x86_64 1/16
Verifying : gssproxy-0.7.0-30.el7_9.x86_64 2/16
Verifying : 1:quota-4.01-19.el7.x86_64 3/16
Verifying : libpath_utils-0.2.1-32.el7.x86_64 4/16
Verifying : libnfsidmap-0.25-19.el7.x86_64 5/16
Verifying : libevent-2.0.21-4.el7.x86_64 6/16
Verifying : keyutils-1.5.8-3.el7.x86_64 7/16
Verifying : libverto-libevent-0.2.5-4.el7.x86_64 8/16
Verifying : tcp_wrappers-7.6-77.el7.x86_64 9/16
Verifying : libcollection-0.7.0-32.el7.x86_64 10/16
Verifying : 1:quota-nls-4.01-19.el7.noarch 11/16
Verifying : libref_array-0.1.5-32.el7.x86_64 12/16
Verifying : libbasicobjects-0.1.1-32.el7.x86_64 13/16
Verifying : 1:nfs-utils-1.3.0-0.68.el7.2.x86_64 14/16
Verifying : libini_config-1.3.1-32.el7.x86_64 15/16
Verifying : rpcbind-0.2.0-49.el7.x86_64 16/16
Installed:
nfs-utils.x86_64 1:1.3.0-0.68.el7.2
Dependency Installed:
gssproxy.x86_64 0:0.7.0-30.el7_9 keyutils.x86_64 0:1.5.8-3.el7
libbasicobjects.x86_64 0:0.1.1-32.el7 libcollection.x86_64 0:0.7.0-32.el7
libevent.x86_64 0:2.0.21-4.el7 libini_config.x86_64 0:1.3.1-32.el7
libnfsidmap.x86_64 0:0.25-19.el7 libpath_utils.x86_64 0:0.2.1-32.el7
libref_array.x86_64 0:0.1.5-32.el7 libtirpc.x86_64 0:0.2.4-0.16.el7
libverto-libevent.x86_64 0:0.2.5-4.el7 quota.x86_64 1:4.01-19.el7
quota-nls.noarch 1:4.01-19.el7 rpcbind.x86_64 0:0.2.0-49.el7
tcp_wrappers.x86_64 0:7.6-77.el7
Complete!
3、使用 mount 挂载A服务器端的目录/data到客户端B的目录/html/www下
[root@node ~]# mkdir /html/www
[root@node ~]# mount -t nfs 10.0.1.134:/data /html/www
命令注解
mount -t nfs 10.0.1.134:/data /html/www
- `mount`:这是一个Linux命令,用于挂载文件系统。
- `-t nfs`:指定文件系统类型为NFS,即将要挂载的是一个网络文件系统。
- `10.0.1.134:/data`:这里指定了 NFS 服务器的 IP 地址及其提供的共享目录。其中,`10.0.1.134` 是 NFS 服务器的 IP 地址,`/data` 是在该服务器上已经通过NFS服务共享出来的目录。
- `/html/www`:这是本地计算机上的挂载点,即你希望把远程NFS服务器的 `/data` 目录挂载到本地计算机的 `/html/www` 这个位置。之后,你在本地访问 `/html/www` 就相当于访问 NFS 服务器上的 `/data` 目录。
总结起来,这条命令的作用是将IP地址为10.0.1.134的NFS服务器上共享的/data目录挂载到本地Linux系统的/html/www目录下,使得本地能够访问并操作远程服务器的/data目录内容。
查看是否挂载成功
df -h
[root@node ~]# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 474M 0 474M 0% /dev
tmpfs 487M 0 487M 0% /dev/shm
tmpfs 487M 7.7M 479M 2% /run
tmpfs 487M 0 487M 0% /sys/fs/cgroup
/dev/mapper/centos-root 50G 1.8G 49G 4% /
/dev/sda1 497M 155M 343M 32% /boot
/dev/mapper/centos-home 148G 33M 148G 1% /home
tmpfs 98M 0 98M 0% /run/user/0
10.0.1.134:/data 47G 33M 47G 1% /html/www
在客户端创建20个文件,再去查看服务端的/data 目录
[root@node www]# touch {1..20}.txt
[root@node www]# ls
10.txt 12.txt 14.txt 16.txt 18.txt 1.txt 2.txt 4.txt 6.txt 8.txt
11.txt 13.txt 15.txt 17.txt 19.txt 20.txt 3.txt 5.txt 7.txt 9.txt
服务端/data 目录
[root@master data]# ls
10.txt 12.txt 14.txt 16.txt 18.txt 1.txt 2.txt 4.txt 6.txt 8.txt
11.txt 13.txt 15.txt 17.txt 19.txt 20.txt 3.txt 5.txt 7.txt 9.txt
总结:你在客户端、/html/www 创建文件就等于在nfs服务端创建文件 因为我们的这个目录已经通过nfs挂载到nfs服务器端的/data 。
nas存储
如果提示这个报错:
clnt_create: RPC: Port mapper failure - Unable to receive: errno 113 (No route to host)
原因
1.防火墙问题
2.ip错误
systemctl stop firewalld 关的是nfs服务器的防火墙 因为我们访问的是他的共享目录,当然如果你不放心,都关也可以
5.使用秘钥连接服务器-实现免密登录服务器
第一种方案-----a服务器登录b服务器 使用秘钥连接
生成ssh秘钥
[root@master ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
5f:a7:40:f2:d4:84:23:b8:0d:c7:1d:2a:b8:e2:db:d4 root@master
The key's randomart image is:
+--[ RSA 2048]----+
| o ..o. |
| .o +.+o |
| . .=o.o.. |
| ....= |
| . . S o . . |
| . . . . o o |
| . . E . . |
| + |
| . . |
+-----------------+
[root@master ~]# cd .ssh
[root@master .ssh]# ls
id_rsa id_rsa.pub
您执行的命令是 `ssh-keygen`,这是一个在Linux系统中生成SSH密钥对的命令,主要用于无密码登录或者其他需要SSH认证的场景。下面是命令执行过程的详细说明:
1. `ssh-keygen`:启动密钥生成程序,它默认生成RSA类型的密钥对,长度为2048位。
2. "Enter file in which to save the key (/root/.ssh/id_rsa): " 提示您输入保存私钥的位置,默认情况下私钥保存在 `/root/.ssh/id_rsa` 文件中。如果您在这里按回车接受默认值,则私钥将保存在这个位置。
3. "Enter passphrase (empty for no passphrase): " 和 "Enter same passphrase again: " 让您输入一个密钥口令(passphrase)。这个口令用于加密私钥文件,保护私钥的安全。如果您不想为私钥设置口令(即无密码登录),可以留空直接回车。
4. "Your identification has been saved in /root/.ssh/id_rsa." 表示您的私钥已成功保存在指定位置。
5. "Your public key has been saved in /root/.ssh/id_rsa.pub." 表示对应的公钥已保存在 `/root/.ssh/id_rsa.pub` 文件中。公钥通常用于复制到其他服务器的 `authorized_keys` 文件中,以便实现基于密钥的身份验证和无密码登录。
6. "The key fingerprint is:..." 和下面的一行显示了生成的密钥指纹(fingerprint),这是一种唯一标识密钥的方式,可用于验证密钥的真实性和完整性。
7. "The key's randomart image is:" 后面展示了一种图形化的密钥表示方式,称为“随机艺术图像”(randomart),这种可视化可以帮助用户更容易地识别和记忆密钥,而不仅仅是查看一串难以记忆的字符。
a机器:10.0.1.134
b机器:10.0.1.100
a服务器登录b服务器 使用秘钥连接
a机器执行这条命令
执行:ssh-keygen -t rsa
[root@master .ssh]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
/root/.ssh/id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
ba:0b:dc:35:70:7e:59:e1:e1:22:3f:8e:bc:9f:a2:1d root@master
The key's randomart image is:
+--[ RSA 2048]----+
| o |
| o o |
| . o . + |
| + o + |
| S = |
| . . + = . |
| o o E . |
| . o.o . |
| +oooo |
+-----------------+
[root@master .ssh]# ls
authorized_keys id_rsa id_rsa.pub known_hosts
这时.ssh目录下会生成私钥和公钥的键值对id_rsa,id_rsa.pub
把a机器的秘钥文件复制b机器
[root@master .ssh]# scp /root/.ssh/id_rsa.pub root@10.0.1.100:/root/.ssh/authorized_keys
root@10.0.1.100's password:
id_rsa.pub 100% 393 0.4KB/s 00:00
在b机器上把过来的秘钥文件给与权限
[root@b ~]# chmod 600 /root/.ssh/authorized_keys
测试:在a机器上远程登录b机器
[root@a ~]# ssh -l root 10.0.1.100
或者也可以用 ssh 10.0.1.100
[root@master .ssh]# ssh 10.0.1.100
Last login: Mon Mar 18 16:52:11 2024 from 10.0.1.1
[root@node ~]# ls
anaconda-ks.cfg ifcfg-eno16777736 it01 sh www_2024-03-17.tar.gz
[root@master .ssh]# ssh 10.0.1.100 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:ed:03:07 brd ff:ff:ff:ff:ff:ff
inet 10.0.1.100/24 brd 10.0.1.255 scope global noprefixroute eno16777736
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feed:307/64 scope link noprefixroute
valid_lft forever preferred_lft forever
可以看到已经登录成功
缺点:a可以远程登录b服务器,但b机器不可以登录a服务器
[root@node .ssh]# ssh 10.0.1.134
The authenticity of host '10.0.1.134 (10.0.1.134)' can't be established.
ECDSA key fingerprint is SHA256:WNHlA4APdESQiNa1jvJ1HHo3Ey6XJh5vjRepHX8k36o.
ECDSA key fingerprint is MD5:b0:c9:fe:89:6e:49:75:58:87:2b:c5:5e:78:fd:82:1a.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.1.134' (ECDSA) to the list of known hosts.
root@10.0.1.134's password:
Last login: Mon Mar 18 15:38:35 2024 from 10.0.1.1
**************
** 生产服务器,请慎重操作并慎用rm命令! **
**************
sh: /root/sh/1.sh: No such file or directory
虽然登录上了,但是是输入密码登录上的,所以我们要的是不输入密码登录上,很明显,他的缺点。
第二种方案---a和b互相免密连接
a和b互相免密连接
ssh-keygen
cd /root/.ssh
mv id_rsa.pub authorized_keys
scp -r /root/.ssh 192.168.100.11:/root
a机器操作
a机器ip:10.0.1.134
生成秘钥文件
[root@master .ssh]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
5b:ce:1a:f1:9d:08:b3:d0:e6:2d:1a:5c:b5:2a:31:e8 root@master
The key's randomart image is:
+--[ RSA 2048]----+
| |
| |
| . |
| . . . . |
| . + S o |
| . . B & o . |
| E + B * o |
| + + |
| . . |
+-----------------+
查看是否生成秘钥文件了
[root@master .ssh]# ls
id_rsa id_rsa.pub
把当前目录下的 id_rsa.pub 公钥文件移动到名为 authorized_keys 的文件中
[root@master .ssh]# mv id_rsa.pub authorized_keys
查看是否移动成功
[root@master .ssh]# ls
authorized_keys id_rsa
给予一下权限
[root@master .ssh]# chmod 600 authorized_keys
本地机器上的 /root/.ssh 目录及其所有内容将会被完整地复制到远程主机 10.0.1.100 上的 /root/.ssh 目录中。如果远程目录不存在,scp 命令会创建它
[root@master .ssh]# scp -r /root/.ssh 10.0.1.100:/root
The authenticity of host '10.0.1.100 (10.0.1.100)' can't be established.
ECDSA key fingerprint is ae:9d:91:23:b2:20:e5:5d:df:d9:8a:b3:34:64:68:16.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.1.100' (ECDSA) to the list of known hosts.
root@10.0.1.100's password:
id_rsa 100% 1675 1.6KB/s 00:00
authorized_keys 100% 393 0.4KB/s 00:00
known_hosts 100% 172 0.2KB/s 00:00
测试a机器登录b机器
[root@master .ssh]# ssh 10.0.1.100 ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:ed:03:07 brd ff:ff:ff:ff:ff:ff
inet 10.0.1.100/24 brd 10.0.1.255 scope global noprefixroute eno16777736
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feed:307/64 scope link noprefixroute
valid_lft forever preferred_lft forever
b机器
b机器ip:10.0.1.100
查看远程复制过来的秘钥公钥文件
[root@node .ssh]# ls
authorized_keys id_rsa known_hosts
测试有没有b机器登录a机器
[root@node .ssh]# ssh 10.0.1.134 ip a
The authenticity of host '10.0.1.134 (10.0.1.134)' can't be established.
ECDSA key fingerprint is SHA256:WNHlA4APdESQiNa1jvJ1HHo3Ey6XJh5vjRepHX8k36o.
ECDSA key fingerprint is MD5:b0:c9:fe:89:6e:49:75:58:87:2b:c5:5e:78:fd:82:1a.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.1.134' (ECDSA) to the list of known hosts.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno16777736: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:4c:25:86 brd ff:ff:ff:ff:ff:ff
inet 10.0.1.134/24 brd 10.0.1.255 scope global dynamic eno16777736
valid_lft 1512sec preferred_lft 1512sec
inet6 fe80::20c:29ff:fe4c:2586/64 scope link
valid_lft forever preferred_lft forever
[root@node .ssh]# ssh 10.0.1.134
Last login: Mon Mar 18 18:40:29 2024 from 10.0.1.100
**************
** 生产服务器,请慎重操作并慎用rm命令! **
**************
sh: /root/sh/1.sh: No such file or directory
总结: 就是把a机器生成的秘钥公钥文件同时也复制给了b机器 这样就可双方以免密登录了
第三种方案-----windows 服务器 产生秘钥 使用xhsell 使用公钥远程连接服务器
windows 服务器 产生秘钥 使用xhsell 使用公钥远程连接服务器
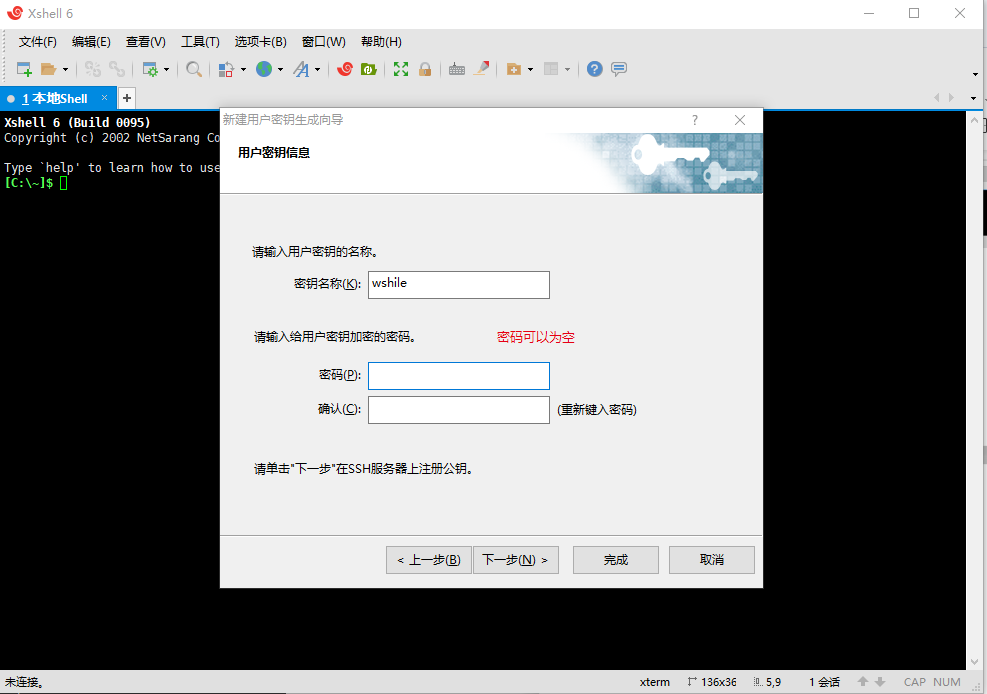
1 使用xshell 生成公钥
生成公钥文件要保存到本地后面要用到
2 公钥复制到linux 服务器上 authorized_keys
如果想只用秘钥登录 可以关闭系统的ssh密码连接
3 vi /etc/ssh/sshd_config
PasswordAuthentication yes 改成no 就可以实现关闭密码登录 使用秘钥远程登录服务器
需求1:实现root用户秘钥登录
需求2:实现普通用户wang秘钥登录
需求3:实现只用秘钥登录,关闭远程连接
具体实操
注意:这个上传的公钥可以用一个,也不用多创建的
需求1:实现root用户秘钥登录
1.先用xshell生成秘钥公钥文件
不明白的可以看下面图示,照着生成就可以了,保存到本地。
我的root秘钥文件生成的是这个秘钥,文件名为roottest.pub 这个秘钥文件我设置l密码是123 ,当然也可以不设置
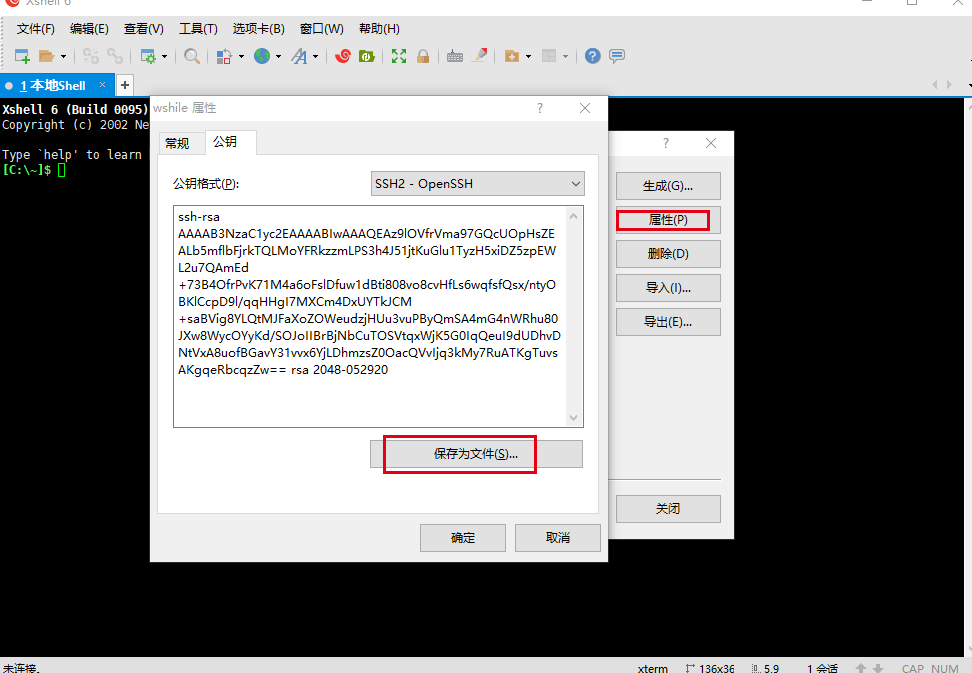
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAoAGzrTb+WEihp+bOwXhv3Oy809zS4BFcZ3Zo+U6RafFm4pyWj/HkvRF2qY1iXcT0Nz8doAwTXpnCh75VsRGUV4EU6OTuFWTkiVzluTAaT9xHWkseiUHiLebxI9drssAks8p5Q+wXGdG7QuX65wokGQ1pCuSU0VcVngGB00AJpA10Wuq3y76/tlOSrzkfELVFZHRS5Gwhqhnt/Zq4J0+7kXZEzeBzHeK2EXxBxDmV7iqYXjJNiZ2+4XuVhHJWzHbSNIUjsHElKl4tBMdjQmLD1iZqvtLhT1JXC6YEy6LvzS5IEpvRrLvzZUg9SeH+GjGiR1uiFO8RLzaSJJAbUbit1w==
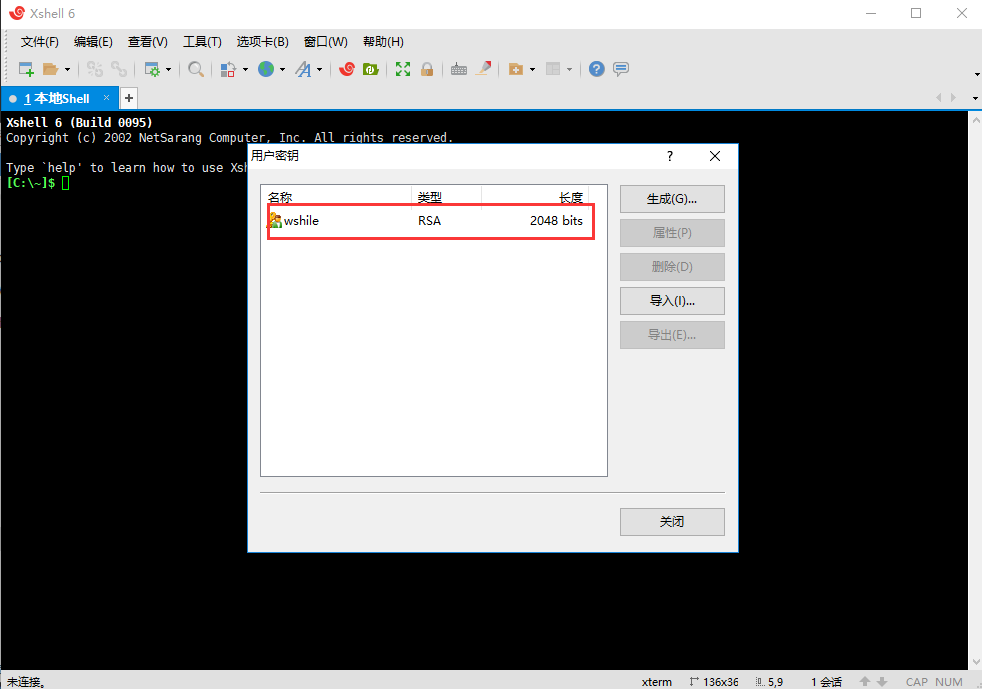
进入到这个文件夹,用rz命令把公钥文件上传,没有这个命令,可以安装一下 yum -y install lrzsz
[root@centos8 ~]# cd .ssh
[root@centos8 .ssh]# ls
authorized_keys id_rsa id_rsa.pub test.pub
[root@centos8 .ssh]# rz
[root@centos8 .ssh]# ls
authorized_keys id_rsa id_rsa.pub roottest.pub test.pub
把这个秘钥文件给追加到这个authorized_keys文件里,如果你没有这个文件夹,你也可以生成这个文件夹 touch authorized_keys
[root@centos8 .ssh]# cat roottest.pub >> authorized_keys
当然你也可以用vim authorized_keys 直接把秘钥追加到后面也可以
测试
用xshell实现root秘钥登录,测试测试成功
[C:\~]$
Connecting to 10.0.1.130:22...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Mon Mar 18 12:55:27 2024 from 10.0.1.1
[root@centos8 ~]#
需求2:实现普通用户wang秘钥登录
1.先用xshell生成秘钥公钥文件
不明白的可以看下面图示,照着生成就可以了,保存到本地。
我的root秘钥文件生成的是这个秘钥,文件名为wang.pub 这个秘钥文件我设置l密码是123 ,当然也可以不设置
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAv9OQi/IWwCzN5ghmk9LgwNPIrR94jctuqM3Tj9+qTt5FekIuUp5vdfbG0rexrzndIVfYPQX8QjrWdSWu8dyZfKIDNWQUeRe5bbeR0fpPof2NySBo/oO2eBm8Krd9R+cIZRly2ClHAJRl3FiBDcqxUPhG7xE8hA5DoRiIQTb4T+cuRxGmdJJRh7zlsW+Mw04Hw+NKcFV7elncWaXU7tcZ2m+3sG/AJo7Zc/2PLUFirPX142A33bxo/HrDFTZ0sdnGAvxMT1HZNltphnEOe5JwsG0q8/IxT+ji4DeCRdr9se1hdObuZVBlOOFRihzldvYm7kY6/d1bxz2n+TQF2xBcBQ==
先创建wang这个普通用户和密码
ps:密码你也可以不创建,不过一般生产环境中建议还是用密码的
这里密码就设置123
[root@centos8 ~]# useradd wang
[root@centos8 ~]# cd .ssh/
[root@centos8 .ssh]# ls
authorized_keys id_rsa id_rsa.pub wang.pub roottest.pub test.pub
把之前的root秘钥给复制过去,当然你也可以用新的
只不要这里还要上传,我就不传了
[root@centos8 .ssh]# cp roottest.pub /home/wang/
查看wang用户是否把秘钥复制过去了
[root@centos8 .ssh]# cd /home/
[root@centos8 home]# cd wang/
[root@centos8 wang]# ls
roottest.pub
[root@centos8 wang]# ls -a
. .. .bash_logout .bash_profile .bashrc .mozilla roottest.pub
创建.ssh 文件夹
[root@centos8 wang]# mkdir .ssh
进去到.ssh目录下
[root@centos8 wang]# cd .ssh/
没有这个authorized_keys文件,我们需要手动创建的
[root@centos8 .ssh]# touch authorized_keys
[root@centos8 .ssh]# ls
authorized_keys
把原来root账户里的root公钥文件给追加到wang用户里面的 authorized_keys 里
[root@centos8 .ssh]# cat /root/.ssh/roottest.pub >> /home/wang/.ssh/authorized_keys
测试
Xshell 7 (Build 0049)
Copyright (c) 2020 NetSarang Computer, Inc. All rights reserved.
Type `help' to learn how to use Xshell prompt.
[C:\~]$
Connecting to 10.0.1.130:22...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
Activate the web console with: systemctl enable --now cockpit.socket
/usr/bin/xauth: file /home/wang/.Xauthority does not exist
[wang@centos8 ~]$
需求3:实现只用秘钥登录,关闭远程连接
vi /etc/ssh/sshd_config
PasswordAuthentication yes 改成no 就可以实现关闭密码登录 使用秘钥远程登录服务器
[root@centos8 ~]# vi /etc/ssh/sshd_config
PasswordAuthentication yes 改成no
[root@centos8 ~]# cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/local/bin:/usr/bin:/usr/local/sbin:/usr/sbin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
# Ciphers and keying
#RekeyLimit default none
# This system is following system-wide crypto policy. The changes to
# crypto properties (Ciphers, MACs, ...) will not have any effect here.
# They will be overridden by command-line options passed to the server
# on command line.
# Please, check manual pages for update-crypto-policies(8) and sshd_config(5).
# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#PubkeyAuthentication yes
# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedPrincipalsFile none
#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication no
#PermitEmptyPasswords no
PasswordAuthentication yes
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Fedora and may cause several
# problems.
UsePAM yes
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
# It is recommended to use pam_motd in /etc/pam.d/sshd instead of PrintMotd,
# as it is more configurable and versatile than the built-in version.
PrintMotd no
#PrintLastLog yes
#TCPKeepAlive yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#UseDNS no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none
# no default banner path
#Banner none
# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@centos8 ~]# systemctl restart sshd
测试成功
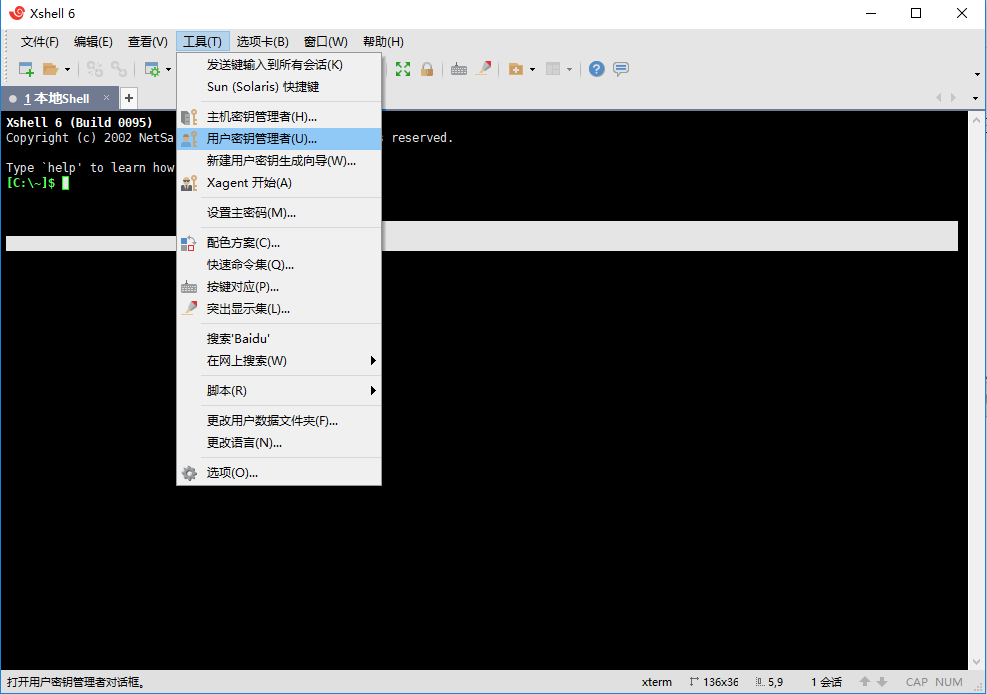
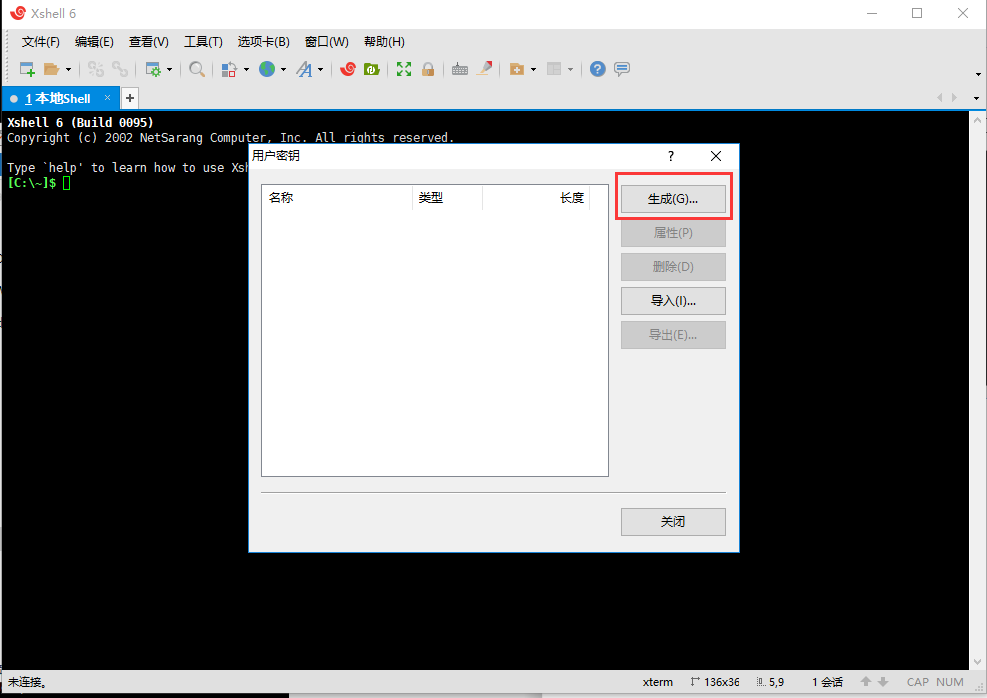
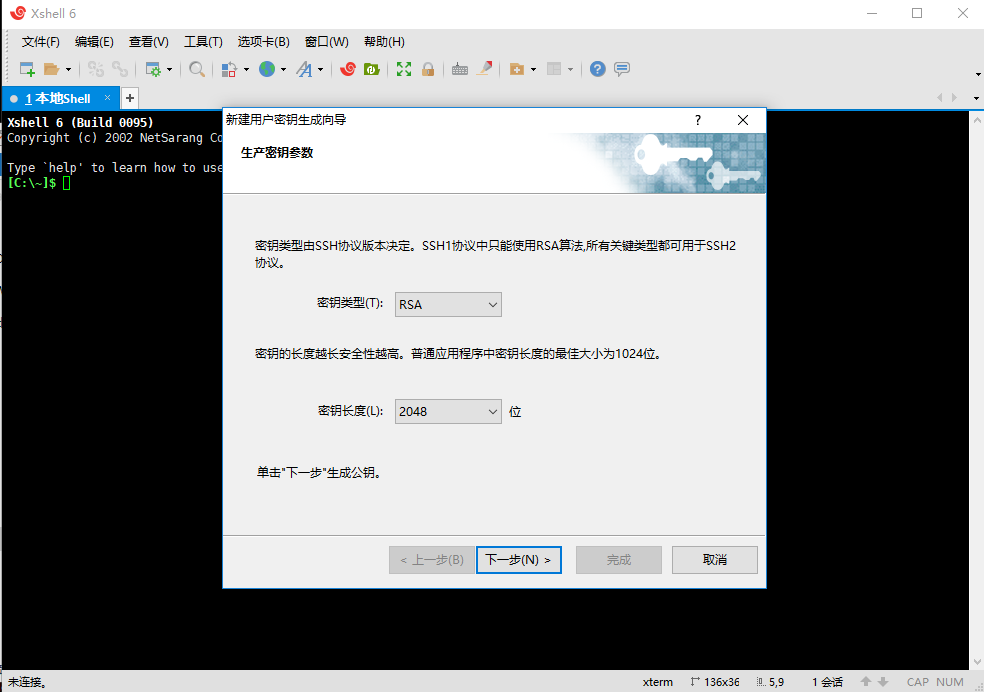
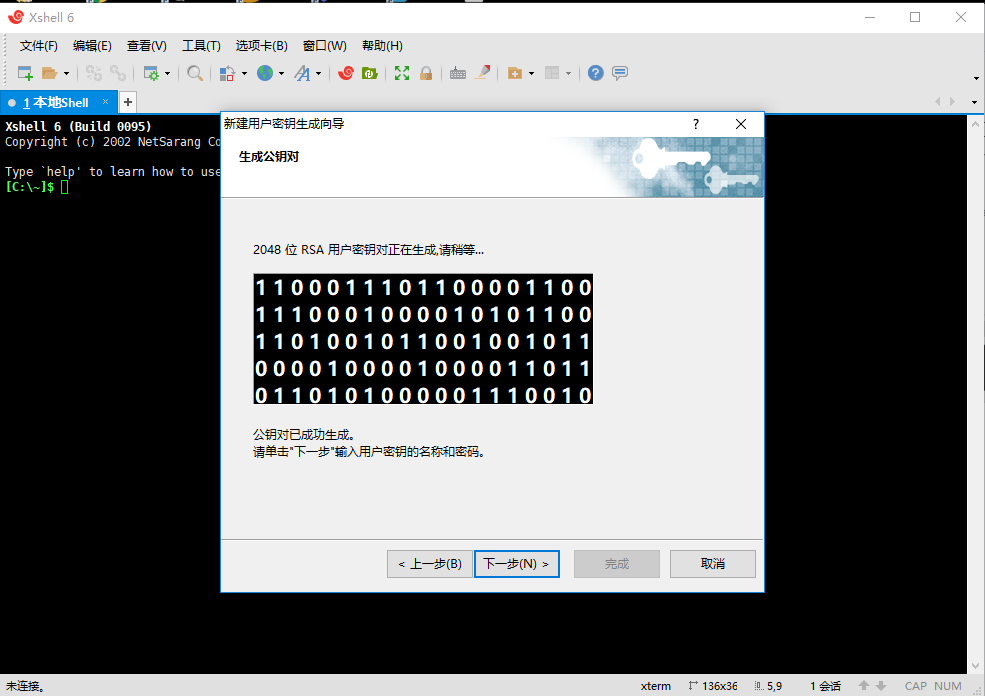
xshell--图示操作步骤
1Xshell生成秘钥免密登录
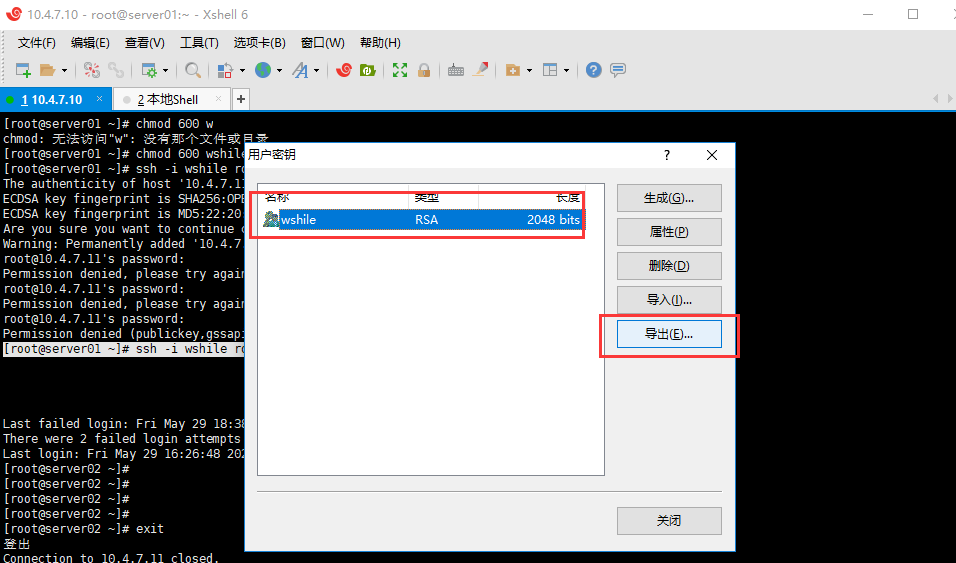
导出生成的公钥
故障案例--秘钥
如果遇到无法实现秘钥连接服务器怎么办?
如果在配置密钥连接服务器时遇到问题,无法通过SSH密钥成功连接服务器,可以从以下几个方面进行排查和解决:
1. **检查密钥文件**:
- 确保私钥文件(例如 `id_rsa`)存在并且路径正确。
- 检查私钥文件的权限,确保只有用户自己有读取权限,例如:`chmod 400 ~/.ssh/id_rsa`。
- 确认公钥(例如 `id_rsa.pub`)已正确地复制到了服务器的 `~/.ssh/authorized_keys` 文件中。
2. **密钥格式与编码**:
- 确保密钥文件采用OpenSSH支持的格式,一般应该是PEM格式。
- 检查密钥文件是否有乱码或损坏,如有需要,重新生成密钥对。
3. **权限和账号问题**:
- 确保在服务器端,密钥关联的用户账号具有足够的权限登录。
- 在阿里云等云服务商平台,还要检查该密钥是否绑定到了正确的ECS实例或RAM用户。
4. **网络连接**:
- 检查网络连接是否畅通,防火墙或安全组规则是否允许SSH端口(默认为22)的入站流量。
- 使用ping命令测试网络连通性,或者尝试telnet到SSH端口看是否可以连接。
5. **SSH客户端配置**:
- 确保在SSH客户端中正确指定了密钥文件,例如使用 `-i` 参数指定私钥文件路径。
- 确认SSH客户端配置文件(如 `~/.ssh/config`)中关于服务器的配置无误。
6. **服务器配置**:
- 检查服务器的SSH服务配置(如 `/etc/ssh/sshd_config`),确保AllowUsers或AllowGroups中有相应的用户,并且PubkeyAuthentication被设置为yes。
- 重启SSH服务以确保配置生效:`systemctl restart sshd` 或 `service sshd restart`。
7. **秘钥过期或无效**:
- 检查阿里云或其他云服务商控制台,确认密钥是否仍在有效期内,过期的秘钥需要重新生成并更新。
8. **服务器状态**:
- 确认服务器是否正常运行,没有因维护或故障而不可达。
通过逐项排查和修复上述可能出现的问题,通常可以解决无法通过秘钥连接服务器的问题。如果问题依然存在,可以查看服务器日志(如 `/var/log/auth.log` 或 `/var/log/secure`)以获取更详细的错误信息。对于阿里云等云服务商,还可以联系他们的技术支持寻求帮助。
NFS故障报错
如果提示这个报错:
clnt_create: RPC: Port mapper failure - Unable to receive: errno 113 (No route to host)
原因
1.防火墙问题
2.ip错误
systemctl stop firewalld 关的是nfs服务器的防火墙 因为我们访问的是他的共享目录,当然如果你不放心,都关也可以
重点回顾
部署nfs服务器
开始部署:
yum install -y nfs-utils
mkdir /data
vim /etc/exports
/data 10.0.0.0/24(rw,async,no_root_squash,no_all_squash)
systemctl restart rpcbind
systemctl restart nfs
systemctl enable rpcbind
systemctl enable nfs
检查 NFS 服务器端是否有目录共享
showmount -e 10.0.0.20
/data 共享目录
10.0.0.0/24 授权ip网段
(rw,sync,no_root_squash,no_all_squash)
rw:读写
sync:同步写入内存和硬盘
no_root_squash:root身份访问
no_all_squash:所有用户不能转换匿名用户
客户机执行
1、安装nfs,不需要启动服务
yum install -y nfs-utils
2、检查 NFS 服务器端是否有目录共享
showmount -e 10.0.0.20
3、使用 mount 挂载A服务器端的目录/data到客户端B的目录/html/www下
[root@localhost ~]# mkdir /html/www
[root@localhost ~]# mount -t nfs 10.0.0.20:/data /html/www
df -h
nas存储
报错:
clnt_create: RPC: Port mapper failure - Unable to receive: errno 113 (No route to host)
systemctl stop firewalld
ssh秘钥连接服务器
a服务器登录b服务器 使用秘钥连接
执行:ssh-keygen -t rsa
这时.ssh目录下会生成私钥和公钥的键值对id_rsa,id_rsa.pub
[root@a ~]# scp /root/.ssh/id_rsa.pub root@192.168.1.101:/root/.ssh/authorized_keys
[root@b ~]# chmod 600 /root/.ssh/authorized_keys
[root@a ~]# ssh -l root 192.168.1.101
第二种方案:
a和b互相免密连接
ssh-keygen
cd /root/.ssh
mv id_rsa.pub authorized_keys
scp -r /root/.ssh 192.168.100.11:/root
第三种方案:windows 服务器 产生秘钥 使用xhsell 使用公钥远程连接服务器
1 使用xshell 生成公钥
2 公钥复制到linux 服务器上 authorized_keys
3 vi /etc/ssh/sshd_config
PasswordAuthentication yes 改成no 就可以实现关闭密码登录 使用秘钥远程登录服务器
新命令讲解-scp
scp命令用于在Linux下进行远程拷贝文件的命令,和它类似的命令有cp,不过cp只是在本机进行拷贝不能跨服务器,而且scp传输是加密的。可能会稍微影响一下速度。当你服务器硬盘变为只读read only system时,用scp可以帮你把文件移出来。另外,scp还非常不占资源,不会提高多少系统负荷,在这一点上,rsync就远远不及它了。虽然 rsync比scp会快一点,但当小文件众多的情况下,rsync会导致硬盘I/O非常高,而scp基本不影响系统正常使用。
语法
scp(选项)(参数)
选项
-1:使用ssh协议版本1;
-2:使用ssh协议版本2;
-4:使用ipv4;
-6:使用ipv6;
-B:以批处理模式运行;
-C:使用压缩;
-F:指定ssh配置文件;
-l:指定宽带限制;
-o:指定使用的ssh选项;
-P:指定远程主机的端口号;
-p:保留文件的最后修改时间,最后访问时间和权限模式;
-q:不显示复制进度;
-r:以递归方式复制。
参数
源文件:指定要复制的源文件。
目标文件:目标文件。格式为user@host:filename(文件名为目标文件的名称)。
实例
从远程复制到本地的scp命令与上面的命令雷同,只要将从本地复制到远程的命令后面2个参数互换顺序就行了。
从远处复制文件到本地目录
scp root@10.10.10.10:/opt/soft/nginx-0.5.38.tar.gz /opt/soft/
从10.10.10.10机器上的/opt/soft/的目录中下载nginx-0.5.38.tar.gz 文件到本地/opt/soft/目录中。
从远处复制到本地
scp -r root@10.10.10.10:/opt/soft/mongodb /opt/soft/
从10.10.10.10机器上的/opt/soft/中下载mongodb目录到本地的/opt/soft/目录来。
上传本地文件到远程机器指定目录
scp /opt/soft/nginx-0.5.38.tar.gz root@10.10.10.10:/opt/soft/scptest
复制本地/opt/soft/目录下的文件nginx-0.5.38.tar.gz到远程机器10.10.10.10的opt/soft/scptest目录。
上传本地目录到远程机器指定目录
scp -r /opt/soft/mongodb root@10.10.10.10:/opt/soft/scptest
上传本地目录/opt/soft/mongodb到远程机器10.10.10.10上/opt/soft/scptest的目录中去。