用tcpdump 分析如何建立与关闭tcp连接
according to preview article 【并发服务器系列】3 epoll模型
I use tcpdump to analyze how tcp build up a connection, send a message ,and close the connection. (code are available in the preview article.)
client(172.18.70.159) use a random port 49538 to connection server(172.18.70.149:54321)
now I print out the client's captured:
1 sudo tcpdump port 54321
3 listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
4
5
6 19:29:52.674854 IP bogon.49538 > bogon.54321: Flags [S], seq 2303324334, win 5840, options [mss 1460,sackOK,TS val 6717463 ecr 0,nop,wscale 5], length 0
7 19:29:52.675309 IP bogon.54321 > bogon.49538: Flags [S.], seq 2402310477, ack 2303324335, win 5792, options [mss 1460,sackOK,TS val 3494999994 ecr 6717463,nop,wscale 6], length 0
8 19:29:52.675351 IP bogon.49538 > bogon.54321: Flags [.], ack 1, win 183, options [nop,nop,TS val 6717464 ecr 3494999994], length 0
9
19:29:52.676059 IP bogon.49538 > bogon.54321: Flags [P.], seq 1:34, ack 1, win 183, options [nop,nop,TS val 6717464 ecr 3494999994], length 33
10 19:29:52.676489 IP bogon.54321 > bogon.49538: Flags [.], ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 0
11 19:29:52.676517 IP bogon.54321 > bogon.49538: Flags [P.], seq 1:30, ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 29
12 19:29:52.676526 IP bogon.49538 > bogon.54321: Flags [.], ack 30, win 183, options [nop,nop,TS val 6717464 ecr 3494999995], length 0
13 19:29:52.676591 IP bogon.54321 > bogon.49538: Flags [F.], seq 30, ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 0
14 19:29:52.677302 IP bogon.49538 > bogon.54321: Flags [F.], seq 34, ack 31, win 183, options [nop,nop,TS val 6717464 ecr 3494999995], length 0
15 19:29:52.677641 IP bogon.54321 > bogon.49538: Flags [.], ack 35, win 91, options [nop,nop,TS val 3494999996 ecr 6717464], length 0
line 6,7,8(first 3 lines) is how the connection build (called three handshakes).
line 9,10,11 (middle 3 lines ) is how message send.
line 12,13,14,15 (last 4 lines) is how conncetion close.(called four handshakes)
here is server's capture:
2 19:30:49.882771 IP bogon.54321 > bogon.49538: Flags [S.], seq 2402310477, ack 2303324335, win 5792, options [mss 1460,sackOK,TS val 3494999994 ecr 6717463,nop,wscale 6], length 0
3 19:30:49.883168 IP bogon.49538 > bogon.54321: Flags [.], ack 1, win 183, options [nop,nop,TS val 6717464 ecr 3494999994], length 0
4
5
6 19:30:49.883888 IP bogon.49538 > bogon.54321: Flags [P.], seq 1:34, ack 1, win 183, options [nop,nop,TS val 6717464 ecr 3494999994], length 33
7 19:30:49.883917 IP bogon.54321 > bogon.49538: Flags [.], ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 0
8 19:30:49.883986 IP bogon.54321 > bogon.49538: Flags [P.], seq 1:30, ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 29
9
10
11 19:30:49.884028 IP bogon.54321 > bogon.49538: Flags [F.], seq 30, ack 34, win 91, options [nop,nop,TS val 3494999995 ecr 6717464], length 0
12 19:30:49.884355 IP bogon.49538 > bogon.54321: Flags [.], ack 30, win 183, options [nop,nop,TS val 6717464 ecr 3494999995], length 0
13 19:30:49.885115 IP bogon.49538 > bogon.54321: Flags [F.], seq 34, ack 31, win 183, options [nop,nop,TS val 6717464 ecr 3494999995], length 0
14 19:30:49.885139 IP bogon.54321 > bogon.49538: Flags [.], ack 35, win 91, options [nop,nop,TS val 3494999996 ecr 6717464], length 0
what does S . P F mean ?
S SYN ---- sys number
F FIN ---- finished sending message
P PSH --- send message to app
R RST --- connection RST
. --- all above set 0
analyse:
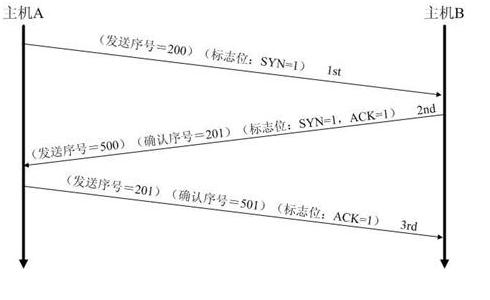
three handshakes to build up a connection
- client(172.18.70.159) send a SYN to server(172.18.70.149)'s port(54321)
- server send another SYN to client , in the same time use ack+1 to confirm the client's SYN
- client confirm back server SYN with ack+1
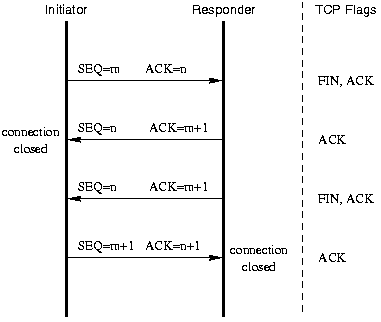
four handshakes to close a connection
- server send to client a FIN
- client confirm back server SYN with ack+1
- client send to server a FIN
- server confirm back client SYN with ack+1
from line 11 we can see server send the FIN to client (code:close(events[n].data.fd); //chat_server.cpp)
chat client start 172.18.70.149
write finished msg: hello, this is client
iwrite = 33
----> receive msg_content: Hi this is server
ireadback = 29
message send and receive:
- length 33 was sent by client ( a message struct with content: hello, this is client) --- first of middle 3 lines
- a confim in the middle
- length 29 was received from server to ( a message struct with content: Hi thi is server) --- last of middle 3 lines
[dengwei@localhost ~]$ uname -a
EOF



