USG6525E防火墙更换记录
公司原使用的防为墙为USG2210, 接了一条100M联通的企业光纤为公司内部300台左右电脑提供上网服务.最早这个型号最早是华为和赛门铁克合作研发的.
公司上线这个设备是2010年8月26日后来我又在2013年做了双机热备,防火墙和核心交换都做了备份,当时公司业务量还是很大的,也是病毒泛滥的年代.、灰鸽子、文件夹.EXE 等. ,时隔多年,我又将防火墙更换为最新版本的设备USG6525E. 更换的过程中遇到了各种配置问题,主要是由于新版本的防火墙较之前有很大变化,最终由华为的工程师协助还是调试完成了.在此感谢! 大家在遇到问题时可以拨打4008229999会有工程师协助,中间联系这么多工程师发还有妹子协助解决,当然还有一些需要查文档的新手.尽量还是多给他们一些机会来学习.写这篇文章的目的是为了记录,因为调试过程中间耗费许多时间.
原设备:

新设备:

USG6525E前面板是镂空设计:网络端口2×10GE(SFP+)+8×GE Combo+2×GE WAN纠错 控制端口1×USB2.0+1×USB3.0, 足以满足中小企业需求.
USG2210防火墙原始配置如下:
acl number 2999
rule 0 permit sysname USG2210 web-manager enable port 10086 info-center timestamp debugging date firewall packet-filter default permit interzone local trust direction inbound firewall packet-filter default permit interzone local trust direction outbound firewall packet-filter default permit interzone local untrust direction inbound firewall packet-filter default permit interzone local untrust direction outbound firewall packet-filter default permit interzone local dmz direction inbound firewall packet-filter default permit interzone local dmz direction outbound firewall packet-filter default permit interzone local vzone direction inbound firewall packet-filter default permit interzone local vzone direction outbound firewall packet-filter default permit interzone trust untrust direction inbound firewall packet-filter default permit interzone trust untrust direction outbound firewall packet-filter default permit interzone trust dmz direction inbound firewall packet-filter default permit interzone trust dmz direction outbound firewall packet-filter default permit interzone trust vzone direction inbound firewall packet-filter default permit interzone trust vzone direction outbound firewall packet-filter default permit interzone dmz untrust direction inbound firewall packet-filter default permit interzone dmz untrust direction outbound firewall packet-filter default permit interzone untrust vzone direction inbound firewall packet-filter default permit interzone untrust vzone direction outbound firewall packet-filter default permit interzone dmz vzone direction inbound firewall packet-filter default permit interzone dmz vzone direction outbound firewall defend ip-spoofing enable firewall defend land enable firewall defend smurf enable firewall defend fraggle enable firewall defend winnuke enable firewall defend icmp-redirect enable firewall defend icmp-unreachable enable firewall defend source-route enable firewall defend route-record enable firewall defend tracert enable firewall defend time-stamp enable firewall defend ping-of-death enable firewall defend teardrop enable firewall defend tcp-flag enable firewall defend ip-fragment enable firewall defend large-icmp enable firewall defend ip-sweep enable firewall defend port-scan enable firewall defend syn-flood enable firewall defend udp-flood enable firewall defend icmp-flood enable firewall defend get-flood enable firewall defend dns-flood enable firewall defend tcp-illegal-session enable firewall defend arp-flood enable firewall defend arp-spoofing enable firewall statistic system enable interface GigabitEthernet0/0/0 ip address x.x.x.x 255.255.255.0interface GigabitEthernet0/0/1 ip address 10.0.0.1 255.255.255.0interface NULL0 firewall zone local set priority 100 firewall zone trust set priority 85 add interface GigabitEthernet0/0/1 firewall zone untrust set priority 5 add interface GigabitEthernet0/0/0 firewall zone dmz set priority 50 firewall zone vzone set priority 0 firewall interzone trust untrust packet-filter 2999 outbound nat outbound 2999 address-group 1 aaa local-user adminadmin password cipher Y:O.H18#&N2SFAN&3^SD#^<L1!! local-user adminadmin service-type web telnet local-user adminadmin level 3 local-user finson password cipher EO"Q61=BK%G=834JL]>45<433!!! local-user finson service-type web telnet local-user finson level 3 authentication-scheme default authorization-scheme default accounting-scheme default domain default right-manager server-group slb ip route-static 0.0.0.0 0.0.0.0 200.280.130.31 ip route-static 192.168.0.0 255.255.0.0 10.0.0.2 user-interface con 0 user-interface vty 0 4 authentication-mode aaa protocol inbound telnet
随着光纤入户,居民上网速度大提示. 现在家用宽带都已提升至千兆,原有的百兆光纤明显不能满足企业需要. 现有的网络已经是多线接入. 1条企光纤+2条千兆ADSL..根据现在办公需求继续使用华为设备作为企业出口路由.
新设备支持100个SSL VPN可满足企业上网办公需求. 接口速度达20万兆.
废话不多上新防火墙配置,由于涉及公司重要信息,IP作的隐藏.
!Software Version V600R007C20SPC300
!Last configuration was saved at 2022-08-29 13:44:15 UTC
sysname USG6500E
l2tp domain suffix-separator @
authentication-profile name portal_authen_default
undo factory-configuration prohibit
undo telnet server enable
undo telnet ipv6 server enable
clock timezone UTC add 00:00:00
firewall packet-filter basic-protocol enable
update schedule location-sdb weekly Sun 01:57
#
firewall defend port-scan enable
firewall defend ip-sweep enable
firewall defend teardrop enable
firewall defend time-stamp enable
firewall defend route-record enable
firewall defend source-route enable
firewall defend ip-fragment enable
firewall defend tcp-flag enable
firewall defend winnuke enable
firewall defend fraggle enable
firewall defend tracert enable
firewall defend icmp-unreachable enable
firewall defend icmp-redirect enable
firewall defend large-icmp enable
firewall defend ping-of-death enable
firewall defend smurf enable
firewall defend land enable
firewall defend action discard
#
undo log type traffic enable
log type syslog enable
log type policy enable
#
undo dataflow enable
#
undo sa force-detection enable
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.2
password-policy
level high
#
firewall ipv6 statistics system enable
#
firewall ids authentication type aes256
#
firewall tcp-mss 1200
#
web-manager security version tlsv1.2
web-manager enable
web-manager security enable
web-manager max-user-number 1
undo web-manager config-guide enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
dns resolve
dns server 114.114.114.114
dns server 8.8.8.8
dns server unnumbered interface Dialer0
dns server unnumbered interface GigabitEthernet0/0/0
dns server unnumbered interface GigabitEthernet0/0/1
dns proxy enable
#
dhcp enable
#
update schedule ips-sdb daily 07:29
update schedule av-sdb daily 07:29
update schedule sa-sdb daily 07:29
update schedule ip-reputation daily 07:29
update schedule cnc daily 07:29
update schedule file-reputation daily 07:29
update schedule ext-url-sdb daily 07:29
#
disk-usage alarm threshold 95
#
ip vpn-instance default
ipv4-family
#
ip-link check enable
ip-link name CNC037106524649
destination 114.114.114.114 interface Dialer1 mode icmp
ip-link name TEL1
destination 114.114.114.114 interface Dialer0 mode icmp
ip address-set VLAN8 type object
description 所有服务器
address 0 192.168.8.0 mask 24
address 1 192.168.2.8 mask 32
address 2 192.168.0.0 mask 16
#
ip address-set 开发组IP type object
address 0 192.168.5.190 mask 32
address 1 range 192.168.3.10 192.168.3.21
#
ip address-set 公网IP type object
address 0 range X.X.X.X X.X.X.X
#
ip address-set VLAN-ALL type object
address 0 192.168.0.0 mask 16
#
ip service-set 2222 type object 513
service 0 protocol tcp source-port 2222 destination-port 2222
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
web-auth-server default
port 50100
#
portal-access-profile name default
#
ip pool L2TP
section 0 10.0.1.2 10.0.1.254
dns-list 114.114.114.114
#
aaa
authentication-scheme admin_ad
authentication-scheme admin_ad_local
authentication-scheme admin_hwtacacs
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ldap
authentication-scheme admin_ldap_local
authentication-scheme admin_local
authentication-scheme admin_radius
authentication-scheme admin_radius_local
authentication-scheme default
authorization-scheme default
accounting-scheme default
service-scheme l2tpSScheme_1660200618239
ip-pool L2TP
domain default
service-type ssl-vpn
internet-access mode password
reference user current-domain
domain jishu
description 技术组
service-type ssl-vpn
internet-access mode password
reference user current-domain
manager-user Admin
password cipher
level 15
authentication-scheme admin_local
manager-user niewei
password cipher
service-type web terminal telnet ssh
level 15
authentication-scheme admin_local
lock-authentication timeout 1
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user Admin role system-admin
bind manager-user nieweidong role system-admin
#
interface Dialer0
link-protocol ppp
ppp chap user 637127543
ppp chap password cipher %$%$UOS"7jI!jF[A+pRO86ZVvSt1%$%$
ppp pap local-user 637127429153 password cipher %$%$_C\+S4.$Q*im${RGfV'.PJiD%$%$
ppp ipcp dns admit-any
ip address ppp-negotiate
dialer user 637127429153
dialer bundle 1
service-manage ping permit
bandwidth ingress 300000
bandwidth egress 60000
redirect-reverse
#
interface Dialer1
link-protocol ppp
ppp chap user 03710459
ppp chap password cipher %$%$l:~IRzmyy0Vygz.K5)w9(fCR%$%$
ppp pap local-user 037106524649 password cipher %$%$-}}DFidwz']gLV8*_aK(ZHDq%$%$
ppp ipcp dns admit-any
ip address ppp-negotiate
undo service-manage enable
bandwidth ingress 1000000
bandwidth egress 1000000
redirect-reverse
#
interface MEth0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
#
l2tp-group default-lns
tunnel password cipher %$%$Er,cOh761EEKV,>Ba]r/+)rx%$%$
allow l2tp virtual-template 0
#
interface Virtual-Template0
ppp authentication-mode chap
remote service-scheme l2tpSScheme_1660200618239
ip address 10.0.1.1 255.255.255.0
alias L2TP_LNS_0
undo service-manage enable
#
interface GigabitEthernet0/0/0
undo shutdown
alias 联通0371064549
gateway 172.16.1.1 route disable
service-manage https permit
service-manage ssh permit
service-manage telnet permit
bandwidth ingress 1000000 threshold 90
bandwidth egress 1000000 threshold 90
ip address dhcp-alloc
#
interface GigabitEthernet0/0/1
undo shutdown
alias 联通0371054545
gateway 192.168.1.1 route disable
service-manage https permit
service-manage ssh permit
service-manage telnet permit
bandwidth ingress 1000000 threshold 90
bandwidth egress 1000000 threshold 90
ip address dhcp-alloc
#
interface GigabitEthernet0/0/2
pppoe-client dial-bundle-number 1 ipv4
undo shutdown
alias 中国电信
service-manage ping permit
#
interface GigabitEthernet0/0/3
shutdown
#
interface GigabitEthernet0/0/4
shutdown
#
interface GigabitEthernet0/0/5
shutdown
#
interface GigabitEthernet0/0/6
shutdown
#
interface GigabitEthernet0/0/7
undo shutdown
ip address 10.0.7.1 255.255.255.0
alias WIFI-LAN
service-manage https permit
service-manage ping permit
service-manage ssh permit
bandwidth ingress 1000000
bandwidth egress 1000000
dhcp server mask 255.255.255.0
dhcp server ip-range 10.0.7.6 10.0.7.254
dhcp select interface
dhcp server gateway-list 10.0.7.1
dhcp server dns-list 114.114.114.114 8.8.8.8
#
interface WAN0/0/0
undo shutdown
ip address X.X.X.X 255.255.255.0
ip address X.X.X.X 255.255.255.0 sub
ip address X.X.X.41 255.255.255.0 sub
ip address X.X.X.44 255.255.255.0 sub
alias 企业光纤
gateway X.X.X.33
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage telnet permit
bandwidth ingress 50000 threshold 75
bandwidth egress 100000 threshold 75
redirect-reverse next-hop X.X.X.31
#
interface WAN0/0/1
undo shutdown
ip address 10.0.0.1 255.255.255.0
alias LAN
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage telnet permit
bandwidth ingress 1000000
bandwidth egress 100000
#
interface XGigabitEthernet0/0/0
undo shutdown
#
interface XGigabitEthernet0/0/1
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/7
add interface MEth0/0/0
add interface Virtual-Template0
add interface WAN0/0/1
#
firewall zone untrust
set priority 5
add interface Dialer0
add interface Dialer1
add interface GigabitEthernet0/0/0
add interface GigabitEthernet0/0/1
add interface GigabitEthernet0/0/2
add interface Virtual-if0
add interface WAN0/0/0
#
firewall zone dmz
set priority 50
#
api
security version tlsv1.2
#
undo icmp name timestamp-request receive
undo icmp name timestamp-reply receive
undo icmp type 17 code 0 receive
undo icmp type 18 code 0 receive
#
ip route-static 0.0.0.0 0.0.0.0 WAN0/0/0 X.X.X.3
ip route-static 0.0.0.0 0.0.0.0 Dialer0
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0/0
ip route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0/1
ip route-static 192.168.0.0 255.255.255.0 10.0.0.2
ip route-static 192.168.2.0 255.255.255.0 10.0.0.2
ip route-static 192.168.3.0 255.255.255.0 10.0.0.2
ip route-static 192.168.4.0 255.255.255.0 10.0.0.2
ip route-static 192.168.5.0 255.255.255.0 10.0.0.2
ip route-static 192.168.6.0 255.255.255.0 10.0.0.2
ip route-static 192.168.7.0 255.255.255.0 10.0.0.2
ip route-static 192.168.8.0 255.255.255.0 10.0.0.2
ip route-static 192.168.9.0 255.255.255.0 10.0.0.2
ip route-static 192.168.10.0 255.255.255.0 10.0.0.2
#
undo ssh server compatible-ssh1x enable
ssh user nieweidong
ssh user nieweidong authentication-type password
ssh user nieweidong service-type all
ssh user nieweidong sftp-directory hda1:
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256
ssh server key-exchange dh_group16_sha512 dh_group15_sha512 dh_group14_sha256 dh_group_exchange_sha256
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256
ssh client key-exchange dh_group16_sha512 dh_group15_sha512 dh_group14_sha256 dh_group_exchange_sha256
ssh server dh-exchange min-len 3072
ssh server publickey ecc
#
firewall detect ftp
#
bandwidth-limit destination-ip type udp max-speed 50
bandwidth-limit destination-ip type icmp max-speed 2000
anti-ddos syn-flood source-detect
anti-ddos dns-request-flood source-detect mode basic
anti-ddos dns-reply-flood source-detect
anti-ddos sip-flood source-detect
anti-ddos udp-flood dynamic-fingerprint-learn
anti-ddos udp-frag-flood dynamic-fingerprint-learn
anti-ddos https-flood source-detect
anti-ddos http-flood source-detect mode basic
anti-ddos first-packet-check syn
#
v-gateway public ssl version tlsv12
v-gateway public ssl public-key algorithm rsa
v-gateway public ssl ciphersuit custom aes256-sha aes128-sha
v-gateway ssl-renegotiation-attack defend enable
v-gateway ssl_vpn interface WAN0/0/0 port 2222 private
v-gateway ssl_vpn authentication-domain default
v-gateway ssl_vpn alias SSL_VPN
#
v-gateway ssl_vpn_js interface WAN0/0/0 port 5555 private
v-gateway ssl_vpn_js authentication-domain jishu
v-gateway ssl_vpn_js alias ssl_vpn_js
#
#
nat server 2 protocol tcp global X.X.X.X 30000 inside 192.168.8.19 30000 no-reverse
#
user-interface con 0
authentication-mode password
set authentication password cipher $1c$-4::1\|c5C$hf$"/8AsfPBhXM/p!5V>GKh{~[B*Z=X$,UL@+e/T$
user-interface vty 0 4
authentication-mode aaa
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
nat address-group address1 0
mode pat
route enable
section 0 X.X.X.X X.X.X.X
#
nat address-group 44 1
mode pat
section 0 X.X.X.44 X.X.X.44
#
interface-group 0 name adsl
add interface Dialer1
add interface GigabitEthernet0/0/1
add interface Dialer0
#
multi-interface
mode proportion-of-bandwidth
session persistence enable
session persistence mode source-ip destination-ip
add interface GigabitEthernet0/0/0
add interface GigabitEthernet0/0/1
add interface WAN0/0/0
#
#****BEGIN***ssl_vpn**1****#
v-gateway ssl_vpn
basic
dns-server 114.114.114.114 8.8.8.8
ssl version tlsv12
ssl timeout 5
ssl lifecycle 1440
ssl public-key algorithm rsa
ssl ciphersuit custom aes256-sha aes128-sha
service
network-extension enable
network-extension keep-alive enable
network-extension keep-alive interval 120
network-extension netpool 172.16.20.1 172.16.20.50 255.255.255.0
netpool 172.16.20.1 default
network-extension mode manual
security
policy-default-action permit vt-src-ip
certification cert-anonymous cert-field user-filter subject cn group-filter subject cn
certification cert-anonymous filter-policy permit-all
certification cert-challenge cert-field user-filter subject cn
certification user-cert-filter key-usage any
undo public-user enable
hostchecker
cachecleaner
vpndb
group /default
group /default/call
role
role default
role default condition all
role default network-extension enable
#****END****#
#****BEGIN***ssl_vpn_js**1****#
v-gateway ssl_vpn_js
basic
dns-server 114.114.114.114
ssl version tlsv12
ssl timeout 5
ssl lifecycle 1440
ssl public-key algorithm rsa
ssl ciphersuit custom aes256-sha aes128-sha
service
network-extension enable
network-extension keep-alive enable
network-extension keep-alive interval 120
network-extension netpool 172.16.20.60 172.16.20.70 255.255.255.0
netpool 172.16.20.60 default
network-extension mode manual
network-extension manual-route 10.0.0.0 255.255.255.0
network-extension manual-route 192.168.8.0 255.255.255.0
security
policy-default-action permit vt-src-ip
certification cert-anonymous cert-field user-filter subject cn group-filter subject cn
certification cert-anonymous filter-policy permit-all
certification cert-challenge cert-field user-filter subject cn
certification user-cert-filter key-usage any
undo public-user enable
hostchecker
cachecleaner
vpndb
group /default
group /jishu
group /jishu/kaifa
role
role default
role default condition all
role default network-extension enable
#****END****#
#
right-manager server-group
#
IoT
#
network-scan
network-scan timeout per-asset 300
network-scan timeout entire-scan 23
conflict-resolve override
#
ztna
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
user-manage server-sync tsm
#
security-policy
default action permit
rule name sslvpn_ul
source-zone untrust
destination-zone local
service 2222
service 5555
service udp
action permit
rule name untrust>trust
source-zone untrust
destination-zone trust
action permit
rule name 工作时间禁止
disable
source-zone trust
destination-zone untrust
application label P2P-Based
time-range worktime
action deny
rule name trust>untrust
source-zone trust
destination-zone untrust
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
rule name nopbr
source-zone trust
source-address address-set VLAN8
destination-address address-set VLAN8
action no-pbr
rule name 服务器网络策略
description 服务器走企业光纤
ingress-interface WAN0/0/1
source-address address-set 服务器网段VLAN8
source-address address-set 开发组IP
action pbr egress-interface WAN0/0/0 next-hop X.X.X.33
rule name WIFI带宽占用策略
description WIFI高带宽占用走ADSL线路
disable
ingress-interface GigabitEthernet0/0/7
application label Bandwidth-Consuming
application label Data-Loss
application label Productivity-Loss
action pbr egress-interface multi-interface
mode proportion-of-bandwidth
session persistence enable
session persistence mode source-ip destination-ip
add interface-group adsl
rule name LAN带宽占用策略
description LAN高带宽占用走ADSL线路
disable
ingress-interface WAN0/0/1
application label Bandwidth-Consuming
action pbr egress-interface multi-interface
mode proportion-of-bandwidth
session persistence enable
session persistence mode source-ip destination-ip
add interface-group adsl
rule name 32
disable
source-zone trust
source-address 192.168.3.100 mask 255.255.255.255
action pbr egress-interface WAN0/0/0 next-hop X.X.X.33
#
nat-policy
rule name 指定NAT地址出口
description 用于开发测试
source-zone trust
destination-zone trust
source-address 192.168.3.10 mask 255.255.255.255
destination-address 192.168.8.215 mask 255.255.255.255
action source-nat address-group 44
rule name 域内策略
description 勿删除
source-zone trust
destination-zone trust
source-address address-set VLAN8
destination-address address-set VLAN8
action source-nat address-group address1
rule name 上网策略
description 勿删除
source-zone trust
egress-interface GigabitEthernet0/0/0
egress-interface GigabitEthernet0/0/1
egress-interface WAN0/0/0
action source-nat easy-ip
#
proxy-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
dns server bind interface GigabitEthernet0/0/7 preferred 114.114.114.114 alternate 8.8.8.8
dns server bind interface WAN0/0/0 preferred 114.114.114.114 alternate 8.8.8.8
mode based-on-multi-interface
#
rightm-policy
#
decryption-policy
#
flow-probe-policy
#
mac-access-profile name mac_access_profile
#
return
重点重点:
问题1: 域内策略开放, trust > trunst 之前必须开放,不开放会出现不能正常访问服务器.(WEB服务器中部分内嵌入的是公网地址).
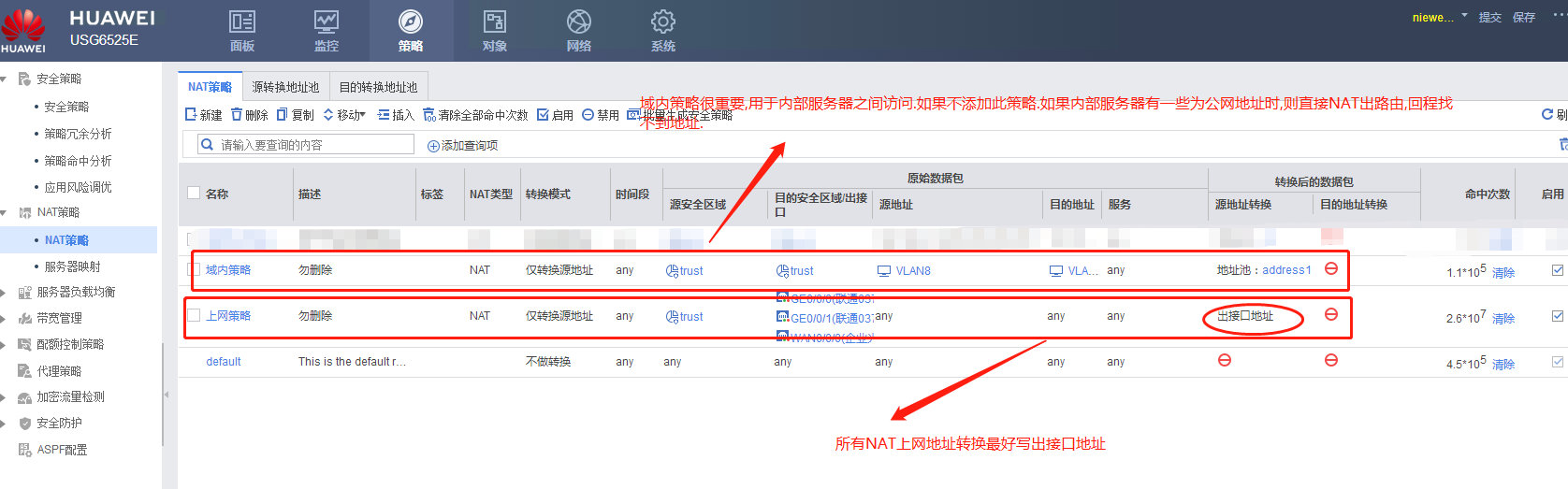
上网NAT地址转换最好写为出接口的地址.
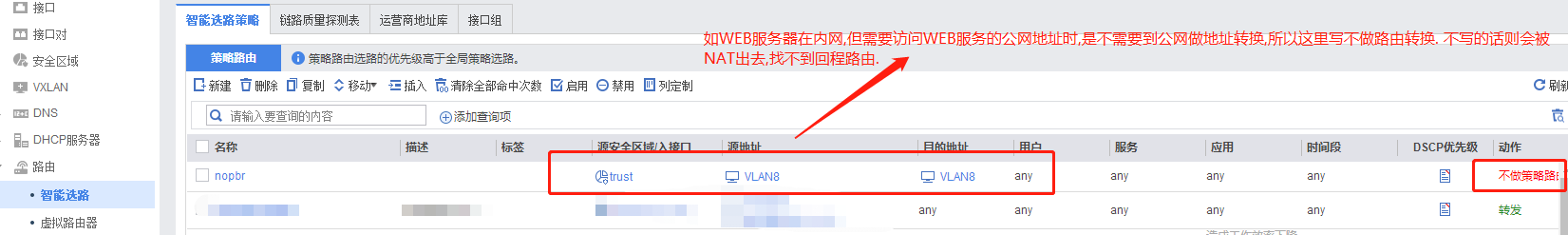
以上这几个地方是需注意的.
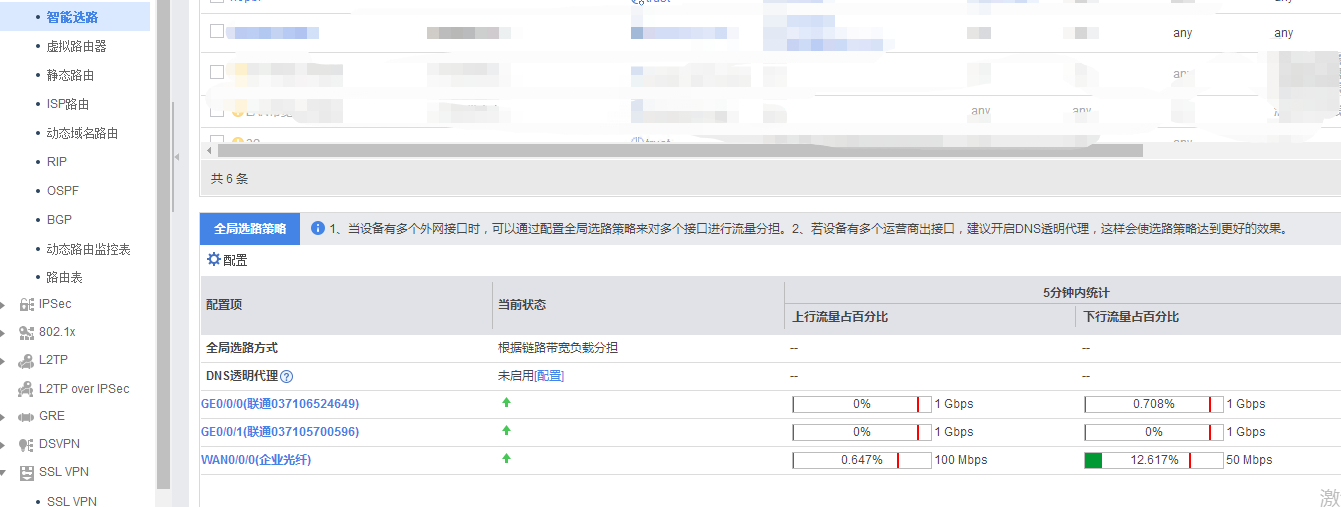
另外: 多条上网线路需开启全局上网策略.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号