etcd搭建过程记录
安装介质准备
etcd 安装介质
wget https://github.com/etcd-io/etcd/releases/download/v3.3.10/etcd-v3.3.10-linux-amd64.tar.gz
cfssl证书制作工具 :访问时加HTTPSwget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
服务器
|
主机名 |
IP |
|
k8s-master1 |
192.168.193.63 |
|
k8s-node1 |
192.168.193.65 |
|
k8s-node2 |
192.168.193.66 |
目录初始化
mkdir -p /k8s/etcd/{bin,cfg,ssl}
mkdir -p /data/etcd
到介质目录下 执行
chmod +x cfssl_linux-amd64 cfssljson_linux-amd64 cfssl-certinfo_linux-amd64 mv cfssl_linux-amd64 /usr/local/bin/cfssl mv cfssljson_linux-amd64 /usr/local/bin/cfssljson mv cfssl-certinfo_linux-amd64 /usr/bin/cfssl-certinfo
证书生成配置
生成etcd ca配置 ssl 为证书目录
cd /k8s/etcd/ssl/
cat << EOF | tee ca-config.json { "signing": { "default": { "expiry": "87600h" }, "profiles": { "etcd": { "expiry": "87600h", "usages": [ "signing", "key encipherment", "server auth", "client auth" ] } } } } EOF
生成etcd ca-csr配置
cat << EOF | tee ca-csr.json { "CN": "etcd CA", "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ] } EOF
生成etcd server-csr配置
cat << EOF | tee server-csr.json { "CN": "etcd", "hosts": [ "192.168.193.63", "192.168.193.65", "192.168.193.66" ], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ] } EOF
开始制作etcd相关证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca
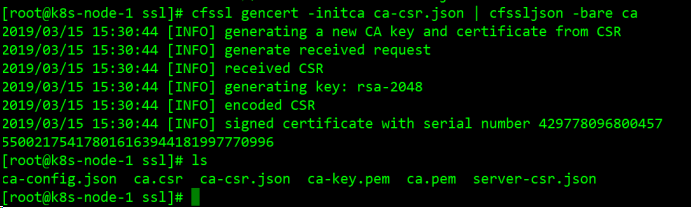
说明:生成 "ca-csr.json ca-key.pem ca.pem" 三个文件
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=etcd server-csr.json | cfssljson -bare server
生成 "server-csr.json server-key.pem server.pem" 三个文件
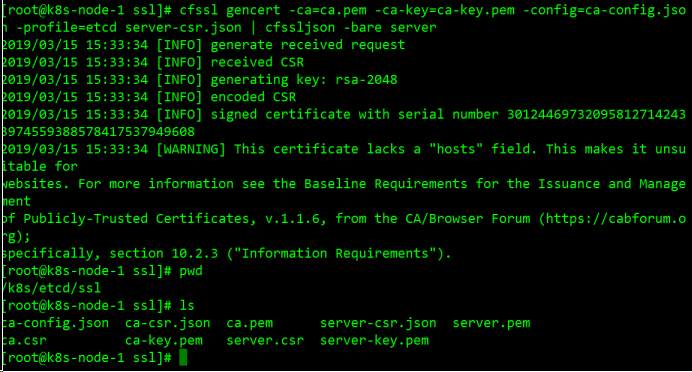
将192.168.193.63上生成的证书密钥拷贝到对应目录
scp /k8s/etcd/ssl/*.pem root@192.168.193.65:/k8s/etcd/ssl/
scp /k8s/etcd/ssl/*.pem root@192.168.193.66:/k8s/etcd/ssl/
etcd安装
在介质目录下
tar -xvf etcd-v3.3.10-linux-amd64.tar.gz cd etcd-v3.3.10-linux-amd64/ cp etcd etcdctl /k8s/etcd/bin/
vim /k8s/etcd/cfg/etcd.conf #这里注意一下 每个服务器的标红处需要填写本服务Ip
#[Member] ETCD_NAME="etcd01" #其他的 分别为 etcd02 etcd03 与标绿 处对应 ETCD_DATA_DIR="/data/etcd" ETCD_LISTEN_PEER_URLS="https://192.168.193.63:2380" ETCD_LISTEN_CLIENT_URLS="https://192.168.193.63:2379,https://127.0.0.1:2379" #[Clustering] ETCD_INITIAL_ADVERTISE_PEER_URLS="https://192.168.193.63:2380" ETCD_ADVERTISE_CLIENT_URLS="https://192.168.193.63:2379,https://127.0.0.1:2379" ETCD_INITIAL_CLUSTER="etcd01=https://192.168.193.63:2380,etcd02=https://192.168.193.65:2380,etcd03=https://192.168.193.66:2380" ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster" ETCD_INITIAL_CLUSTER_STATE="new" #[Security] ETCD_CERT_FILE="/k8s/etcd/ssl/server.pem" ETCD_KEY_FILE="/k8s/etcd/ssl/server-key.pem" ETCD_TRUSTED_CA_FILE="/k8s/etcd/ssl/ca.pem" ETCD_CLIENT_CERT_AUTH="true" ETCD_PEER_CERT_FILE="/k8s/etcd/ssl/server.pem" ETCD_PEER_KEY_FILE="/k8s/etcd/ssl/server-key.pem" ETCD_PEER_TRUSTED_CA_FILE="/k8s/etcd/ssl/ca.pem" ETCD_PEER_CLIENT_CERT_AUTH="true"
[Unit] Description=Etcd Server After=network.target After=network-online.target Wants=network-online.target [Service] Type=notify WorkingDirectory=/data/etcd/ EnvironmentFile=-/k8s/etcd/cfg/etcd.conf # set GOMAXPROCS to number of processors ExecStart=/bin/bash -c "GOMAXPROCS=$(nproc) /k8s/etcd/bin/etcd --name=\"${ETCD_NAME}\" --data-dir=\"${ETCD_DATA_DIR}\" --listen-client-urls=\"${ETCD_LISTEN_CLIENT_URLS}\" --listen-peer-urls=\"${ETCD_LISTEN_PEER_URLS}\" --advertise-client-urls=\"${ETCD_ADVERTISE_CLIENT_URLS}\" --initial-cluster-token=\"${ETCD_INITIAL_CLUSTER_TOKEN}\" --initial-cluster=\"${ETCD_INITIAL_CLUSTER}\" --initial-cluster-state=\"${ETCD_INITIAL_CLUSTER_STATE}\" --cert-file=\"${ETCD_CERT_FILE}\" --key-file=\"${ETCD_KEY_FILE}\" --trusted-ca-file=\"${ETCD_TRUSTED_CA_FILE}\" --client-cert-auth=\"${ETCD_CLIENT_CERT_AUTH}\" --peer-cert-file=\"${ETCD_PEER_CERT_FILE}\" --peer-key-file=\"${ETCD_PEER_KEY_FILE}\" --peer-trusted-ca-file=\"${ETCD_PEER_TRUSTED_CA_FILE}\" --peer-client-cert-auth=\"${ETCD_PEER_CLIENT_CERT_AUTH}\"" Restart=on-failure LimitNOFILE=65536 [Install] WantedBy=multi-user.target
vim /usr/lib/systemd/system/etcd.service
启动服务
#集群所有节点都配置好配置文件,同时启动。
systemctl daemon-reload && systemctl enable etcd && systemctl start etcd
/k8s/etcd/bin/etcdctl --ca-file=/k8s/etcd/ssl/ca.pem --cert-file=/k8s/etcd/ssl/server.pem --key-file=/k8s/etcd/ssl/server-key.pem --endpoints="https://192.168.193.63:2379,https://192.168.193.65:2379,https://192.168.193.66:2379" cluster-health
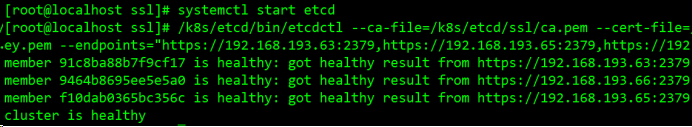
日志 查看方式 journalctl -b -u etcd
可能出现的问题一般是端口占用 防火墙端口未开 以及 每个服务器上编辑配置文件时 Ip没有对应好本服务器


