Sniffer-Agent抓mysql简单使用
gihutb:
https://github.com/zr-hebo/sniffer-agent
环境:mysql5.7
客户端:mysql8.0
1、使用:
[root@mysql ~]# ./sniffer-agent --log_level=info --port=3357 --interface=eth0
2、查看结果内容
ERRO[0157] parse auth info failed <-- malform packet error {"sip":"172.16.1.10","sport":3357,"cpr":1,"bt":1639656947883,"cip":"172.16.1.2","cport":3357,"user":"root","db":"","sql":"show databases","cms":0} {"sip":"172.16.1.10","sport":3357,"cpr":1,"bt":1639656975058,"cip":"172.16.1.2","cport":3357,"user":"root","db":"","sql":"ceshiT DATABASE()","cms":0} {"sip":"172.16.1.10","sport":3357,"cpr":1,"bt":1639656975058,"cip":"172.16.1.2","cport":3357,"user":"root","db":"","sql":"use ceshi","cms":0} {"sip":"172.16.1.10","sport":3357,"cpr":1,"bt":1639656975059,"cip":"172.16.1.2","cport":3357,"user":"root","db":"ceshi","sql":"show databases","cms":0} {"sip":"172.16.1.10","sport":3357,"cpr":1,"bt":1639656975060,"cip":"172.16.1.2","cport":3357,"user":"root","db":"ceshi","sql":"show tables","cms":0}
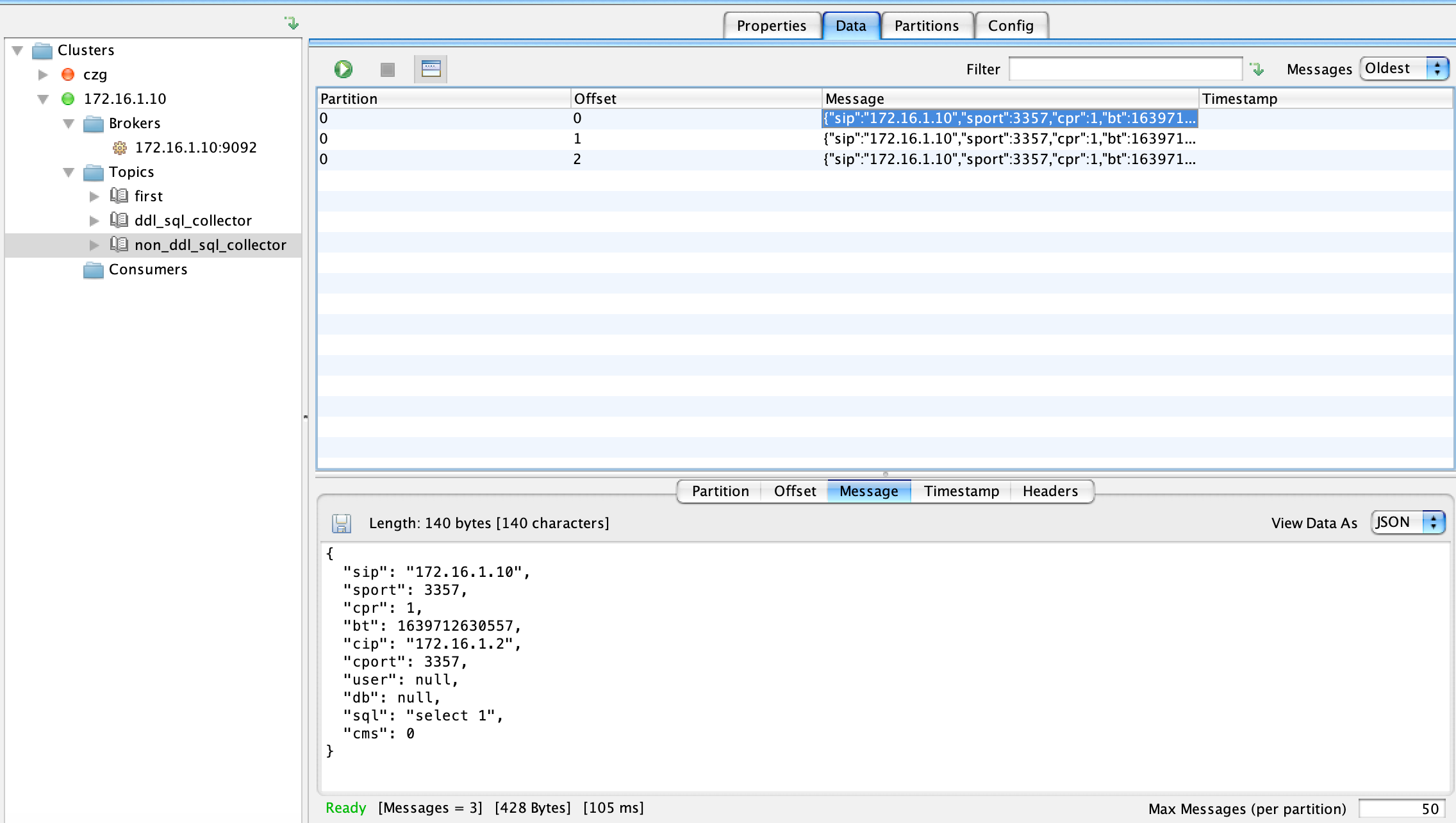
【其中cip代表客户端ip,cport代表客户端port(客户端ip:port组成session标识),sip代表server ip,sport代表server port,user代表查询用户,db代表当前连接的库名,sql代表查询语句,cpr代表抓包率,bt代表查询开始时间戳,cms代表查询消耗的时间,单位是毫秒】
第一行是Mysql8.0登录 mysql5.7抓到的结果,是ERROR,还是兼容mysql8.0不好,下边是抓到的正常请求SQL,结果比较简单,结果中不包括事务ID之类的,也无法分析长事务之类的情况。
这些结果还能推送到kafka中,通过gohangout 消费kafka数据库到clickhouse中,不过这部分还没有做实验。
3、推送到kafka
[root@mysql ~]# ./sniffer-agent --export_type=kafka --kafka-server=172.16.1.10:9092 --kafka-group-id=sniffer --kafka-async-topic=non_ddl_sql_collector --kafka-sync-topic=ddl_sql_collector --log_level=info --port=3357 --interface=eth0
kafka消息示例: