H&NCTF
总排名:67
不用看,没写几题
总结:比赛真的不错,还有游戏可以玩,mc好玩,hnwanna玩得血压高
misc
签到、问卷、签退
111
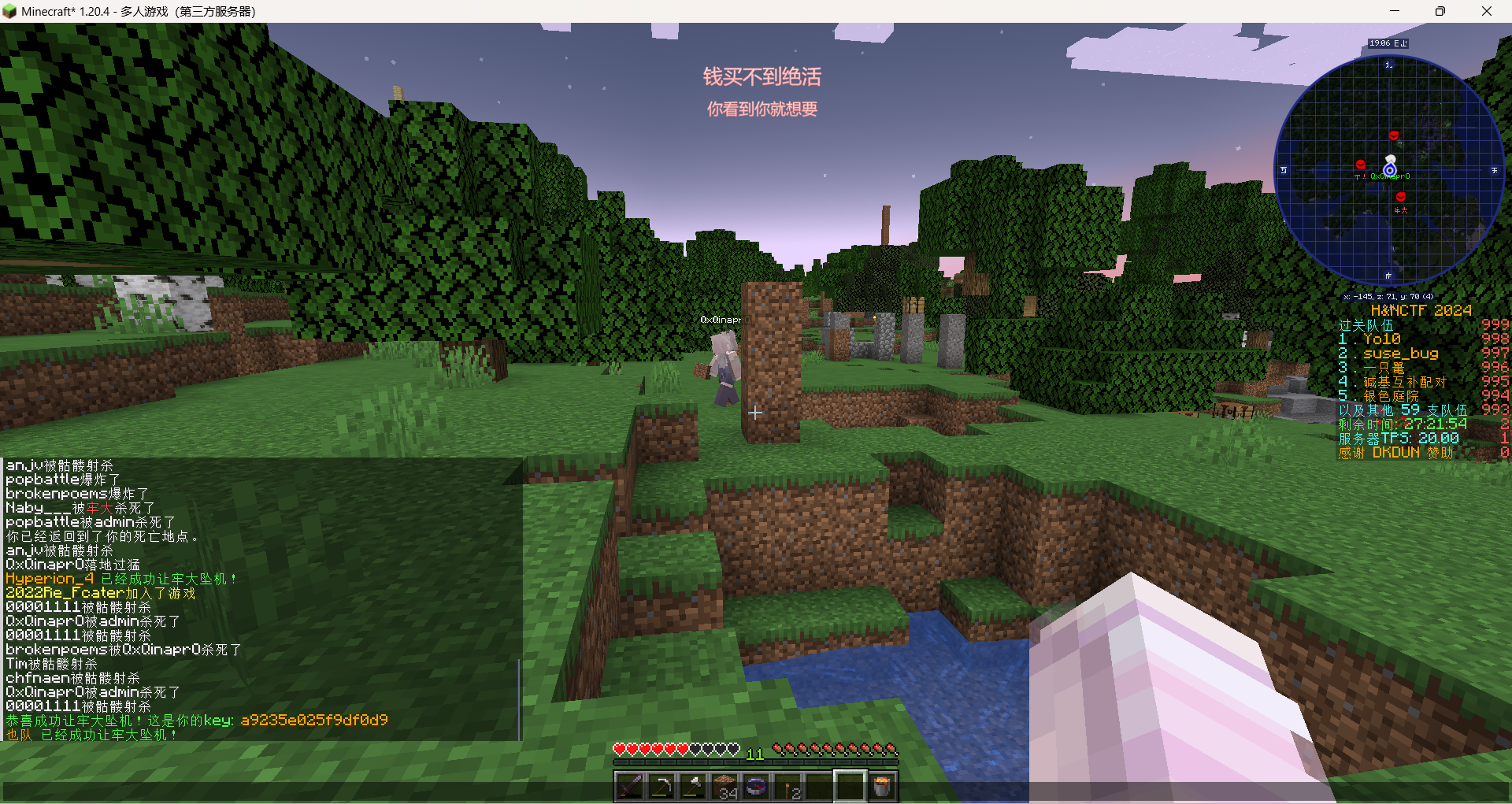
mc题
好玩
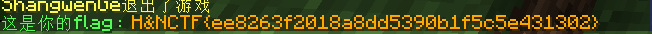
crypto
babyAES
有点偏杂项
源码:
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
from secret import flag
import time
import random
flag = pad(flag,16)
assert b"H&NCTF" in flag
seed = int(time.time())
random.seed(seed)
key = random.randbytes(16)
iv = random.randbytes(16)
aes = AES.new(key,AES.MODE_CBC,iv)
cipher = aes.encrypt(flag)
print(f"cipher = {cipher}")
"""
cipher = b'\x96H_hz\xe7)\x0c\x15\x91c\x9bt\xa4\xe5\xacwch\x92e\xd1\x0c\x9f\x8fH\x05\x9f\x1d\x92\x81\xcc\xe0\x98\x8b\xda\x89\xcf\x92\x01a\xe1B\xfb\x97\xdc\x0cG'
"""
分析:
正常的aes加密,没法破解
但是使用了时间作为随机数种子,并且给出了flag头 H&NCTF
尝试用时间爆破
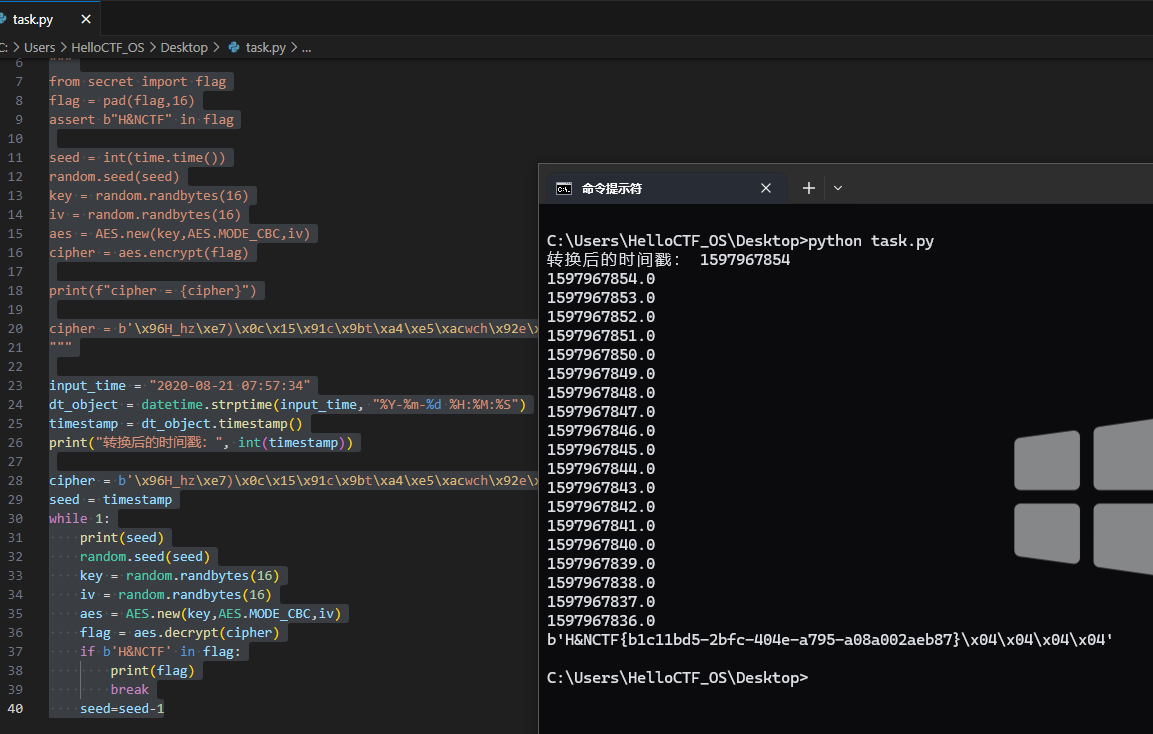
分析压缩包内脚本时间为2020-08-21 07:57:34
问题:
random.randbytes好像是python3.9以上版本才支持,我本机是python3.7,所以在ctfos里搞了个python3.11再来实现爆破
安装Crypto库
python3报错:ModuleNotFoundError: No module named ‘Crypto‘-CSDN博客
exp:
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
import time
import random
from datetime import datetime
"""
from secret import flag
flag = pad(flag,16)
assert b"H&NCTF" in flag
seed = int(time.time())
random.seed(seed)
key = random.randbytes(16)
iv = random.randbytes(16)
aes = AES.new(key,AES.MODE_CBC,iv)
cipher = aes.encrypt(flag)
print(f"cipher = {cipher}")
cipher = b'\x96H_hz\xe7)\x0c\x15\x91c\x9bt\xa4\xe5\xacwch\x92e\xd1\x0c\x9f\x8fH\x05\x9f\x1d\x92\x81\xcc\xe0\x98\x8b\xda\x89\xcf\x92\x01a\xe1B\xfb\x97\xdc\x0cG'
"""
input_time = "2020-08-21 07:57:34"
dt_object = datetime.strptime(input_time, "%Y-%m-%d %H:%M:%S")
timestamp = dt_object.timestamp()
print("转换后的时间戳:", int(timestamp))
cipher = b'\x96H_hz\xe7)\x0c\x15\x91c\x9bt\xa4\xe5\xacwch\x92e\xd1\x0c\x9f\x8fH\x05\x9f\x1d\x92\x81\xcc\xe0\x98\x8b\xda\x89\xcf\x92\x01a\xe1B\xfb\x97\xdc\x0cG'
seed = timestamp
while 1:
print(seed)
random.seed(seed)
key = random.randbytes(16)
iv = random.randbytes(16)
aes = AES.new(key,AES.MODE_CBC,iv)
flag = aes.decrypt(cipher)
if b'H&NCTF' in flag:
print(flag)
break
seed=seed-1
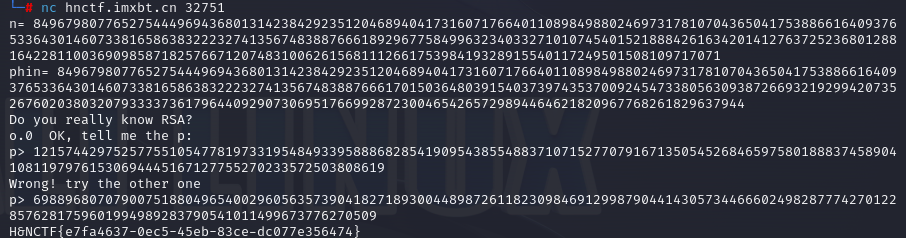
#H&NCTF{b1c11bd5-2bfc-404e-a795-a08a002aeb87}
babyPQ
nc 拿到n和phin
找板子题
#sagemath
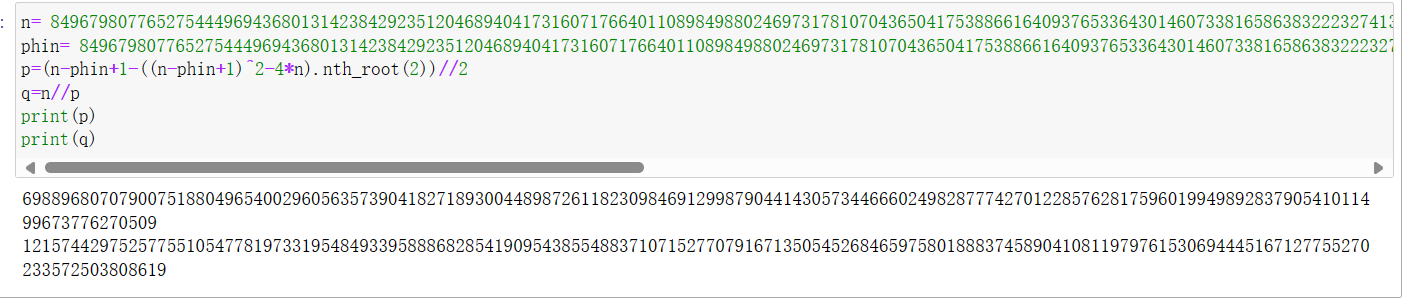
n= 84967980776527544496943680131423842923512046894041731607176640110898498802469731781070436504175388661640937653364301460733816586383222327413567483887666189296775849963234033271010745401521888426163420141276372523680128816422811003690985871825766712074831006261568111266175398419328915540117249501508109717071
phin= 84967980776527544496943680131423842923512046894041731607176640110898498802469731781070436504175388661640937653364301460733816586383222327413567483887666170150364803915403739743537009245473380563093872669321929942073526760203803207933337361796440929073069517669928723004654265729894464621820967768261829637944
p=(n-phin+1-((n-phin+1)^2-4*n).nth_root(2))//2
q=n//p
print(p)
print(q)
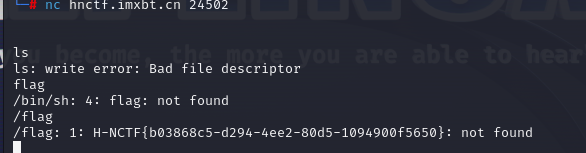
pwn
close
看不懂
就一直尝试连接然后输入命令就出来了(摊手
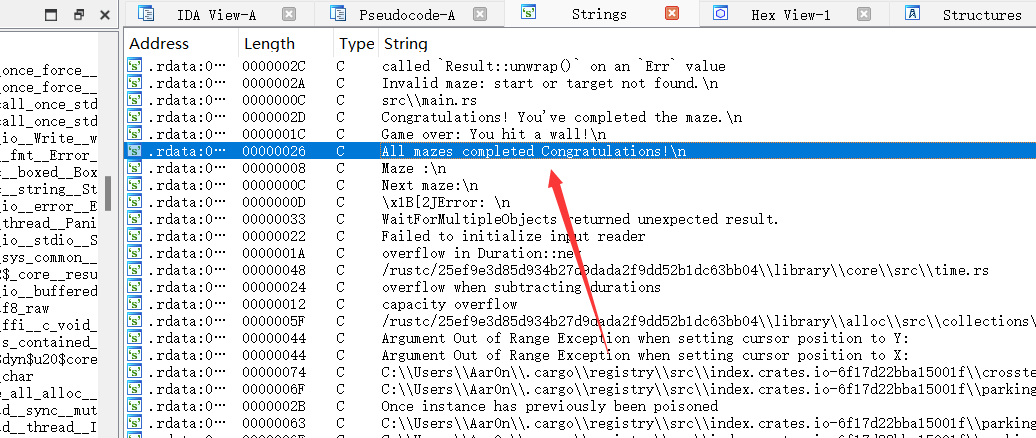
reverse
childmaze
我愿其为找一找
全程x
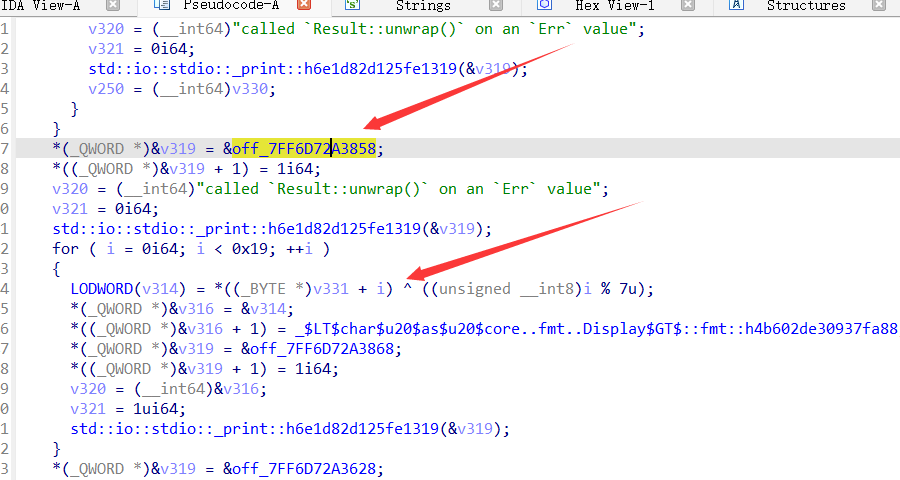
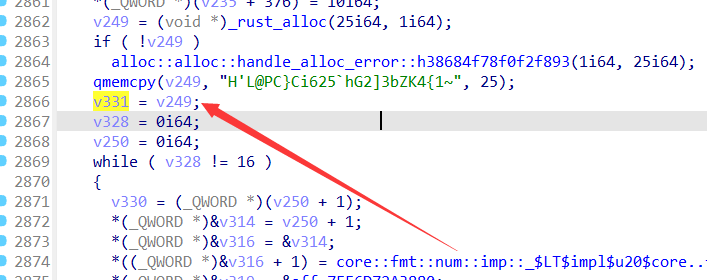
a="H'L@PC}Ci625`hG2]3bZK4{1~"
b=[]
for i in a:
b.append(ord(i))
for i in range(len(b)):
b[i]=(b[i])^(i%7)
print(chr(b[i]),end="")
#H&NCTF{Ch411enG3_0f_M4z3}
I_LOVE_SWDD
不会逆向
先看F12
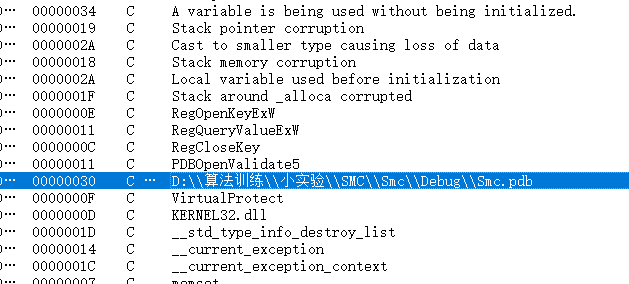
看到个这个
百度一下
知道smc是对局部代码进行加密,静态调试不行,所以只能动调
分析到这里,看汇编有点复杂
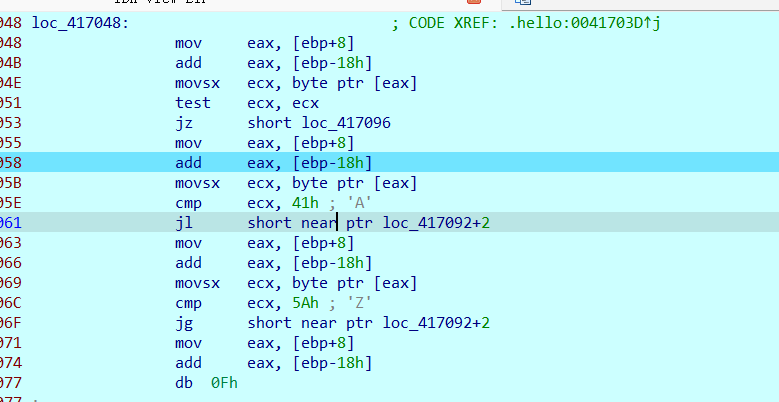
交给Copilot
初步分析是判断是否在A-Z范围内
往下翻发现关键,有跟一个字符串进行判断,而且除符号外字符都在A-Z
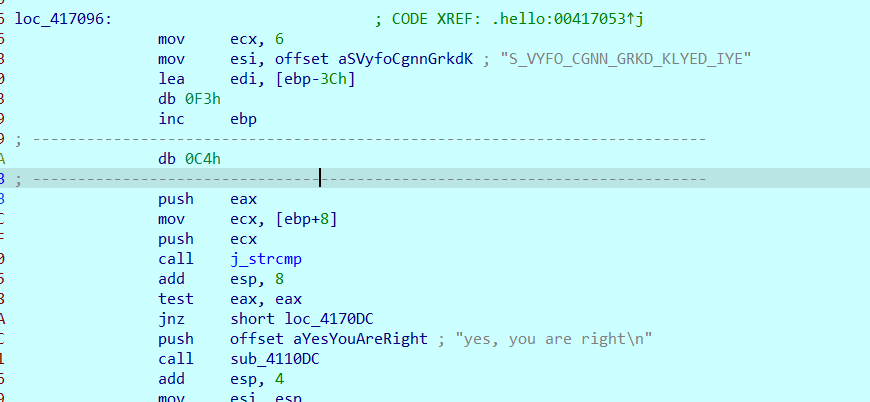
因为解题人数较多,而且汇编貌似挺短的,猜测为简单的加解密,猜测凯撒(总之就是试出来的
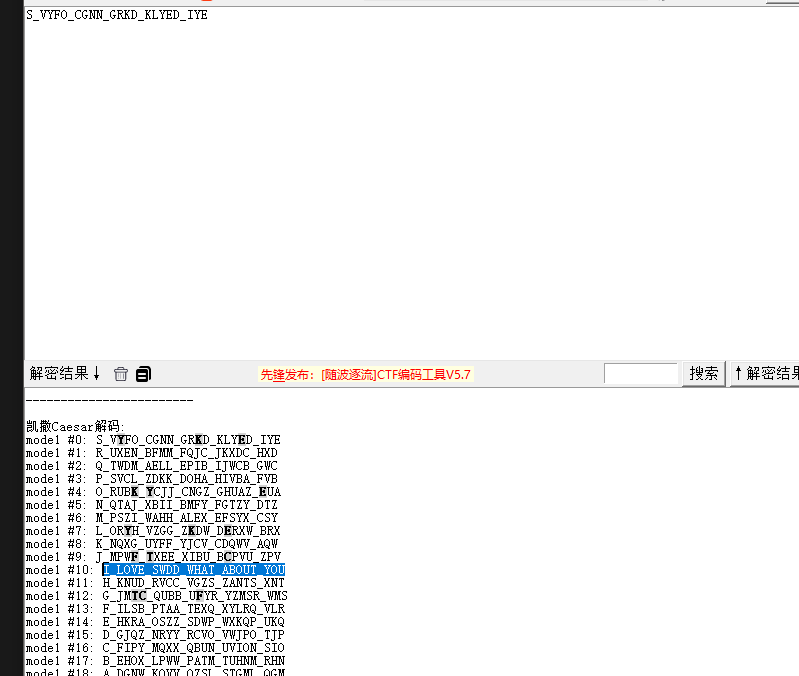
最后加上H&NCTF{}
H&NCTF
算是猜出来的
最喜欢的逆向题
确实最喜欢
找一找,F12



 浙公网安备 33010602011771号
浙公网安备 33010602011771号