CTFshow——funnyrsa3
题目如下:
题目分析:
发现常规rsa不存在的dp。查找资料知道 dp ≡ d mod (p - 1)。意识到dp是解题关键,可能dp和n存在某种关系可以解出p或者去,跟之前有一题有点类似,求p和q之间存在的线性关系那题。Rsa之给定n很大求解问题 - nLesxw - 博客园 (cnblogs.com)
存在关系的推导:
dp ≡ d % (p - 1) 可以写成d ≡ dp % (p - 1) 所以存在一个k1 使得 k1 * ( p - 1) + dp = d
因为 ed ≡ 1 mod phi(n) 也可以变换 ed = k2 * phi(n) + 1
所以e * d = e * (k1 * ( p - 1) + dp) ,易得:
k2 * phi(n) + 1 = e * (k1 * ( p - 1) + dp)
又因为 phi(n) = (p - 1) * (q - 1),所以可以得到:
k2 * [(p - 1) * (q - 1)] + 1 = e * (k1 * ( p - 1) + dp)
展开得到:
k2 * (p-1)*(q-1) + 1 = e * k1 * (p-1) + e * dp
整理得到:
e * dp = (p-1) * (k2*(q-1) - e * k1) + 1
设 x = k2 * (q-1) - k1 * e,可以得到:
e * dp = (p - 1) * x + 1
根据dp ≡ d % (p - 1) 我们可以得到 dp < p-1
根据e * dp = (p - 1) * x + 1 估算我们可以得到 x < e
因为e * dp > 0且不等于1,所以x > 1
所以在e * dp = (p - 1) * x + 1 式子中我们知道了e,dp 和x的范围[1,e],,通过爆破x即的p
脚本编写:
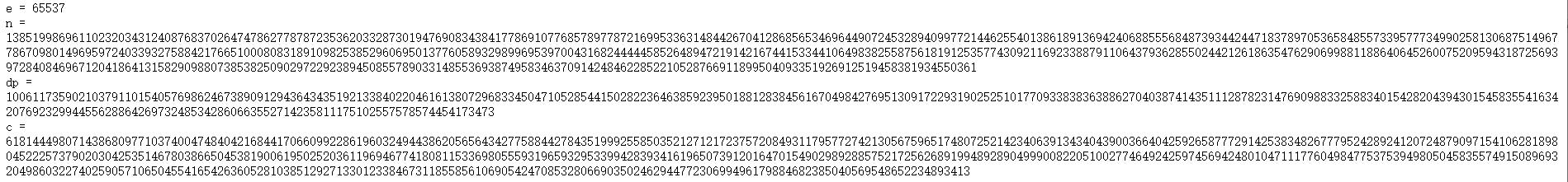
from Cryptodome.Util.number import * import gmpy2 e = 65537 n = 13851998696110232034312408768370264747862778787235362033287301947690834384177869107768578977872169953363148442670412868565346964490724532894099772144625540138618913694240688555684873934424471837897053658485573395777349902581306875149677867098014969597240339327588421766510008083189109825385296069501377605893298996953970043168244444585264894721914216744153344106498382558756181912535774309211692338879110643793628550244212618635476290699881188640645260075209594318725693972840846967120418641315829098807385382509029722923894508557890331485536938749583463709142484622852210528766911899504093351926912519458381934550361 dp = 100611735902103791101540576986246738909129436434351921338402204616138072968334504710528544150282236463859239501881283845616704984276951309172293190252510177093383836388627040387414351112878231476909883325883401542820439430154583554163420769232994455628864269732485342860663552714235811175102557578574454173473 c = 6181444980714386809771037400474840421684417066099228619603249443862056564342775884427843519992558503521271217237572084931179577274213056759651748072521423406391343404390036640425926587772914253834826777952428924120724879097154106281898045222573790203042535146780386650453819006195025203611969467741808115336980555931965932953399428393416196507391201647015490298928857521725626891994892890499900822051002774649242597456942480104711177604984775375394980504583557491508969320498603227402590571065045541654263605281038512927133012338467311855856106905424708532806690350246294477230699496179884682385040569548652234893413 a = e * dp for i in range(1, e): p = (a + i - 1) // i if a == (p - 1) * i + 1: q = n // p phi = (p - 1) * (q - 1) d = gmpy2.invert(e, phi) m = pow(c, d, n) print(long_to_bytes(m))
爆破得到flag
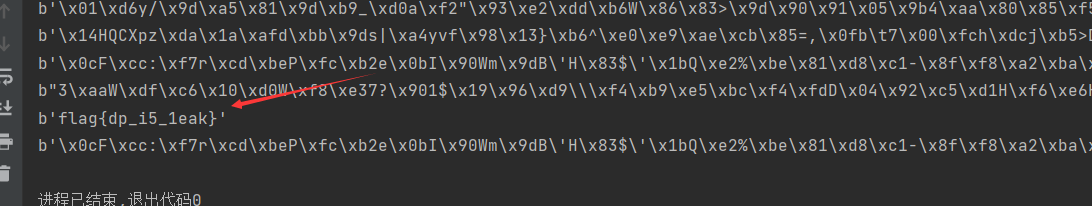
这里代码写的不够好,你也可以加上一些限制条件,直接得到flag。
总结:
dp问题的rsa要找出关系e * dp = (p - 1) * x + 1 [1<x<e]爆破x即得解




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理