Requirement
The Test have eight flag, Can you finding all?
Begin
first
aHR0cHM6Ly9DaGluYUNOQ3lTZWM6Y3liZXJjeWJlckBjdXJpb3NpdHkudmxhYjAxLmRlLw==
to Base64
second
https://ChinaCNCySec:cybercyber@curiosity.vlab01.de/
to HTML

third
https://curiosity.vlab01.de/level00/

guess https://curiosity.vlab01.de/level00/ to https://curiosity.vlab01.de/level01/
fourthly
https://curiosity.vlab01.de/level01/

How meaning is the code? Q29udGludWUgdG8gbGV2ZWwwMl9h

Q29udGludWUgdG8gbGV2ZWwwMl9h to deMD5 , deciphering = Continue to level02_a
fifthly
https://curiosity.vlab01.de/level02_a/
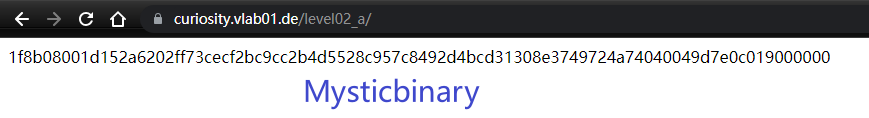
1f8b08001d152a6202ff73cecf2bc9cc2b4d5528c957c8492d4bcd31308e3749724a74040049d7e0c019000000,
HaHa..., One more do it again deciphering , but I good at deciphering.
Look forward to 1f8b0800,It is feature ,So these is Steganography.
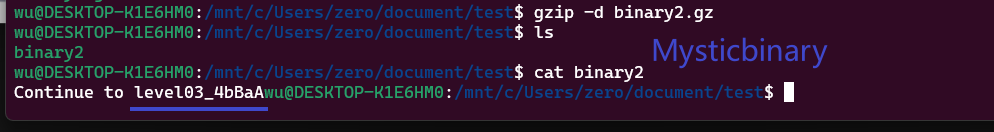
Continue to level03_4bBaA
fixth
https://curiosity.vlab01.de/level03_4bBaA/
( ̄y▽ ̄)╭ Ohohoho..... , Do you want me to do brute force cracking?
Let's go.
So,Tough bit bit .
Request:
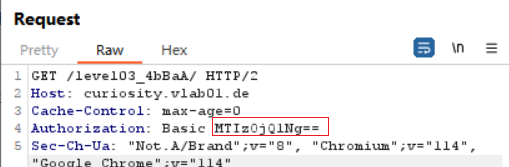
Authorization: Basic MTIzOjQ1Ng==
Authorization: Basic 123:456
reference:https://blog.csdn.net/qq_44881113/article/details/121036945
I try top500 password of dictionary, and gain no any respones.
Oh! New hope!
https://curiosity.vlab01.de/level03_4bBaA/
to https://curiosity.vlab01.de/level03_4BBAA/
to https://curiosity.vlab01.de/level03_4bBaA/
to https://curiosity.vlab01.de/level03_4bBaA/login.php
critical:
Authorization: Basic Q2hpbmFDTkN5U2VjOmN5YmVyY3liZXI=

POST /level03_4bBaA/login.php HTTP/1.1
Host: curiosity.vlab01.de
Connection: close
Content-Length: 49
Pragma: no-cache
Cache-Control: no-cache
Authorization: Basic Q2hpbmFDTkN5U2VjOmN5YmVyY3liZXI=
sec-ch-ua: "Not.A/Brand";v="8", "Chromium";v="114", "Google Chrome";v="114"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
Origin: https://curiosity.vlab01.de
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://curiosity.vlab01.de/level03_4bBaA/
Accept-Encoding: gzip, deflate
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8,en-US;q=0.7
Cookie: PHPSESSID=53828ff221ce7ec9b605a1ca427ee681
user=user01&password=password&submit=%E6%8F%90%E4%BA%A4
Nice, get administrator

continue...
administrator
user=administrator&password=123456.&submit=%E6%8F%90%E4%BA%A4

Oh [○・`Д´・ ○] , Damn it! it's stuck. I hate getting stuck!
End
After arriving on the level03_4bBaA, I have tried many account passwords, but I haven't gained much. I have already spent a lot of time, and I think it's time to say goodbye. The game is over!


