ciscn初赛 2024
ezCsky
先根据提示到github下载M-Core插件放到ida的proxy文件夹,然后选择MCORE形式打开
流程
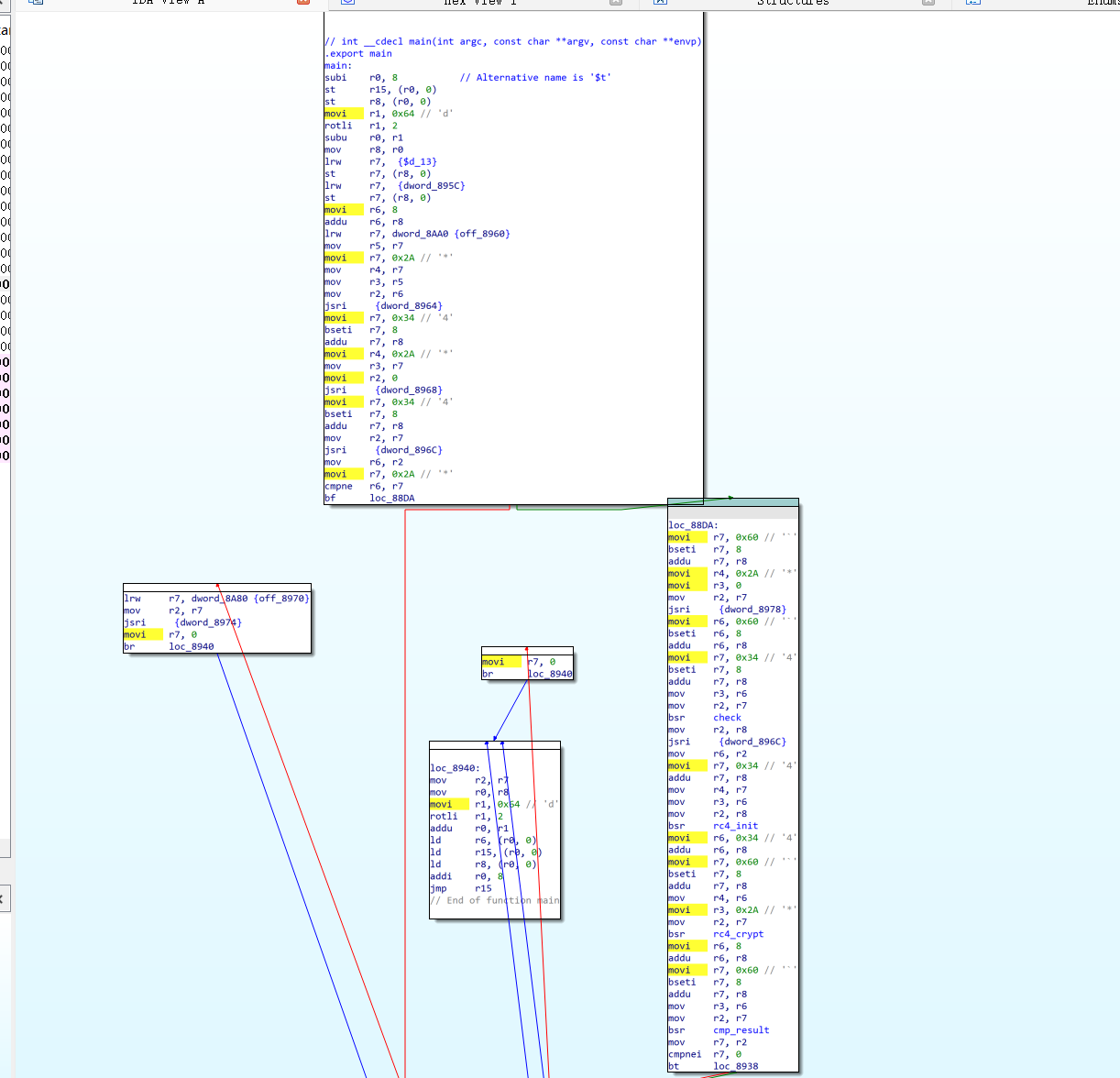
首先进行一次长度检查,然后通过check函数,rc4_init初始化s盒,rc4_crypt进行rc4加密
这里有个xor函数,我不知道咋跳到这里的,然后猜测是按自己向后异或
lrw r7, byte_8AA0 {off_8960}
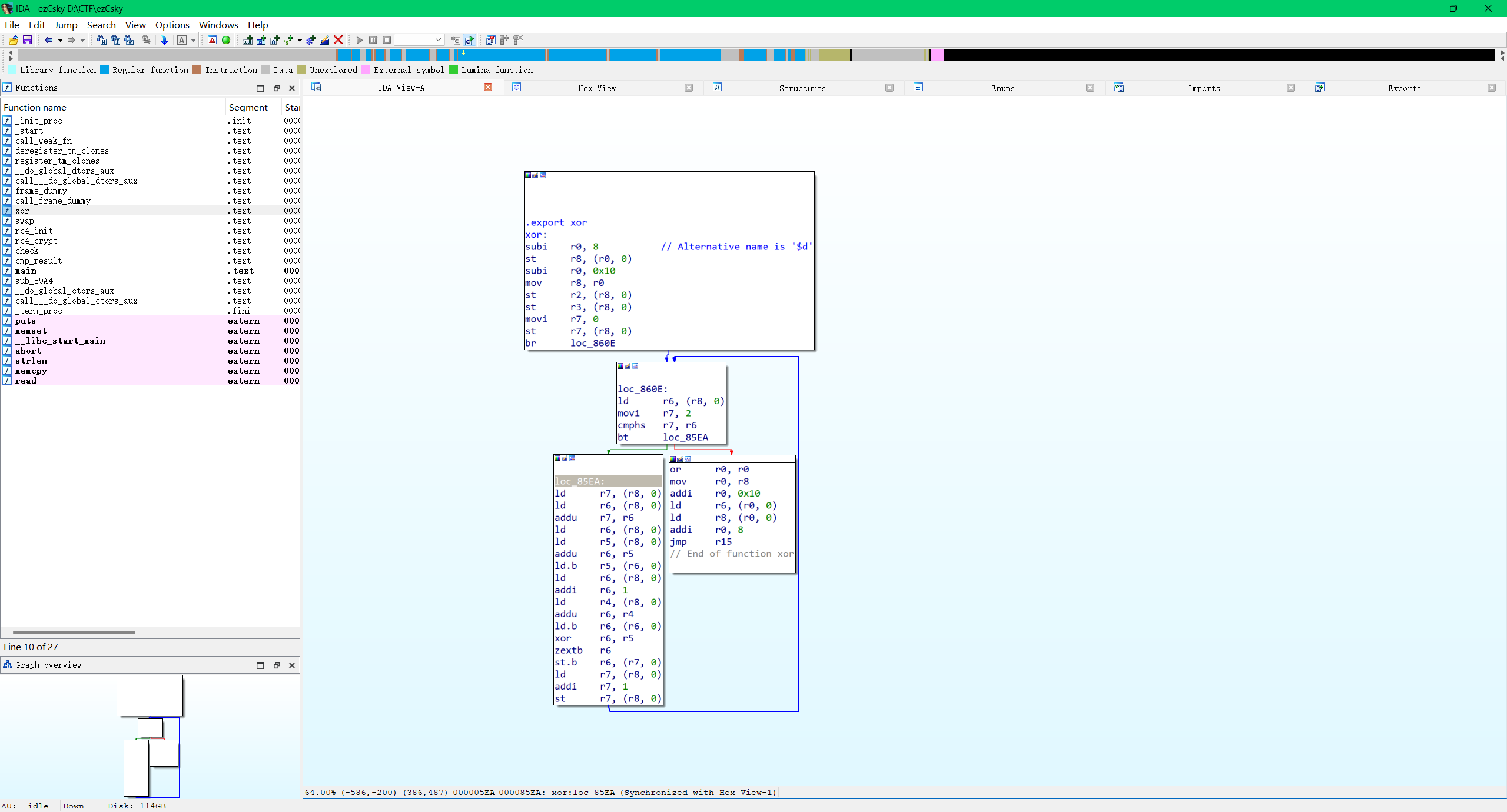
这里就是加密部分
lrw r7, {$d_13} // "testkey"
这是key
解密脚本:
def KSA(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def PRGA(S):
i, j = 0, 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
yield K
def RC4Decrypt(key, text):
S = KSA(key)
keystream = PRGA(S)
res = []
for char in text:
res.append(char ^ next(keystream))
return bytes(res)
#示例
key = b'testkey'
plaintext = [0x96, 0x8F, 0xB8, 0x08, 0x5D, 0xA7, 0x68, 0x44, 0xF2, 0x64,
0x92, 0x64, 0x42, 0x7A, 0x78, 0xE6, 0xEA, 0xC2, 0x78, 0xB8,
0x63, 0x9E, 0x5B, 0x3D, 0xD9, 0x28, 0x3F, 0xC8, 0x73, 0x06,
0xEE, 0x6B, 0x8D, 0x0C, 0x4B, 0xA3, 0x23, 0xAE, 0xCA, 0x40,
0xED, 0xD1]
Rc4decrypt = RC4Decrypt(key, plaintext)
Rc4decrypt = list(Rc4decrypt)
for i in range(len(Rc4decrypt) - 2, -1, -1):
Rc4decrypt[i] = Rc4decrypt[i] ^ Rc4decrypt[i+1]
print(chr(Rc4decrypt[i]), end='')
dump
直接丢输入看回显
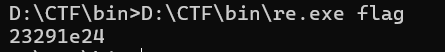
和flag的输出一样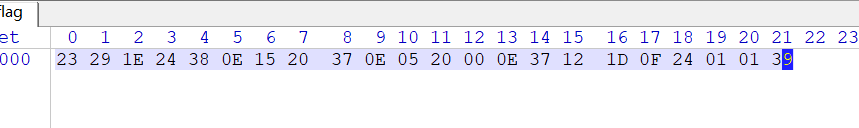
import string
print(string.ascii_letters + string.digits + '={}')
table = '1e1f202122232425262728292a2b2c2d2e2f303132333435363702030405060708090a0b0c0d0e0f101112131415161718191a1b001c1d00000000000000013839'
key = []
for i in range(0, len(table), 2):
key.append(int("0x" + table[i:i + 2], 16))
print(key)
enc = [0x23, 0x29, 0x1E, 0x24, 0x38, 0x0E, 0x15, 0x20, 0x37, 0x0E, 0x05, 0x20, 0x00, 0x0E, 0x37, 0x12, 0x1D, 0x0F, 0x24, 0x01, 0x01, 0x39]
value = list(string.ascii_letters + string.digits + '={}')
print(value)
dic = dict(zip(key, value))
for i in enc:
print(dic[i], end='')
#flag{MTczMDc9MzQ2Ng==}
标准base
flag{17307466}



