极客大挑战2024题解(Reverse)(部分)
2024极客大挑战
Hello_re
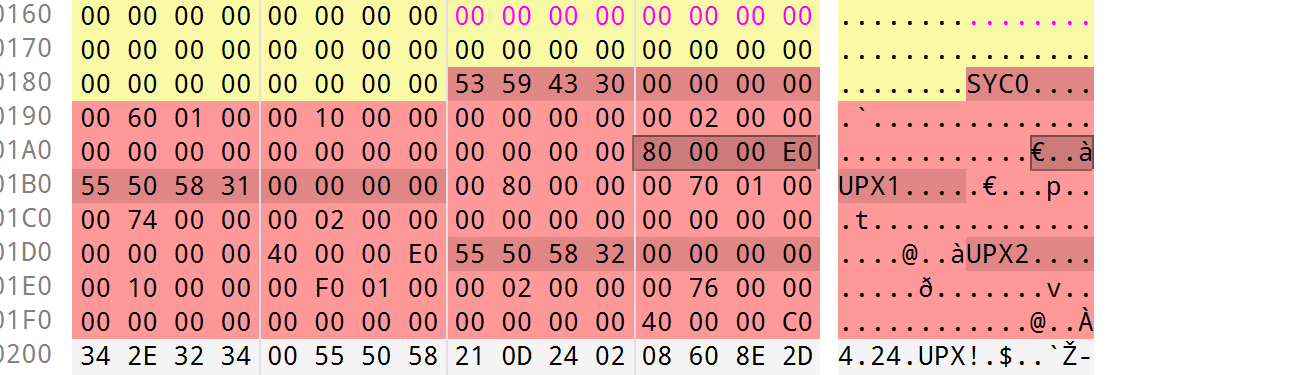
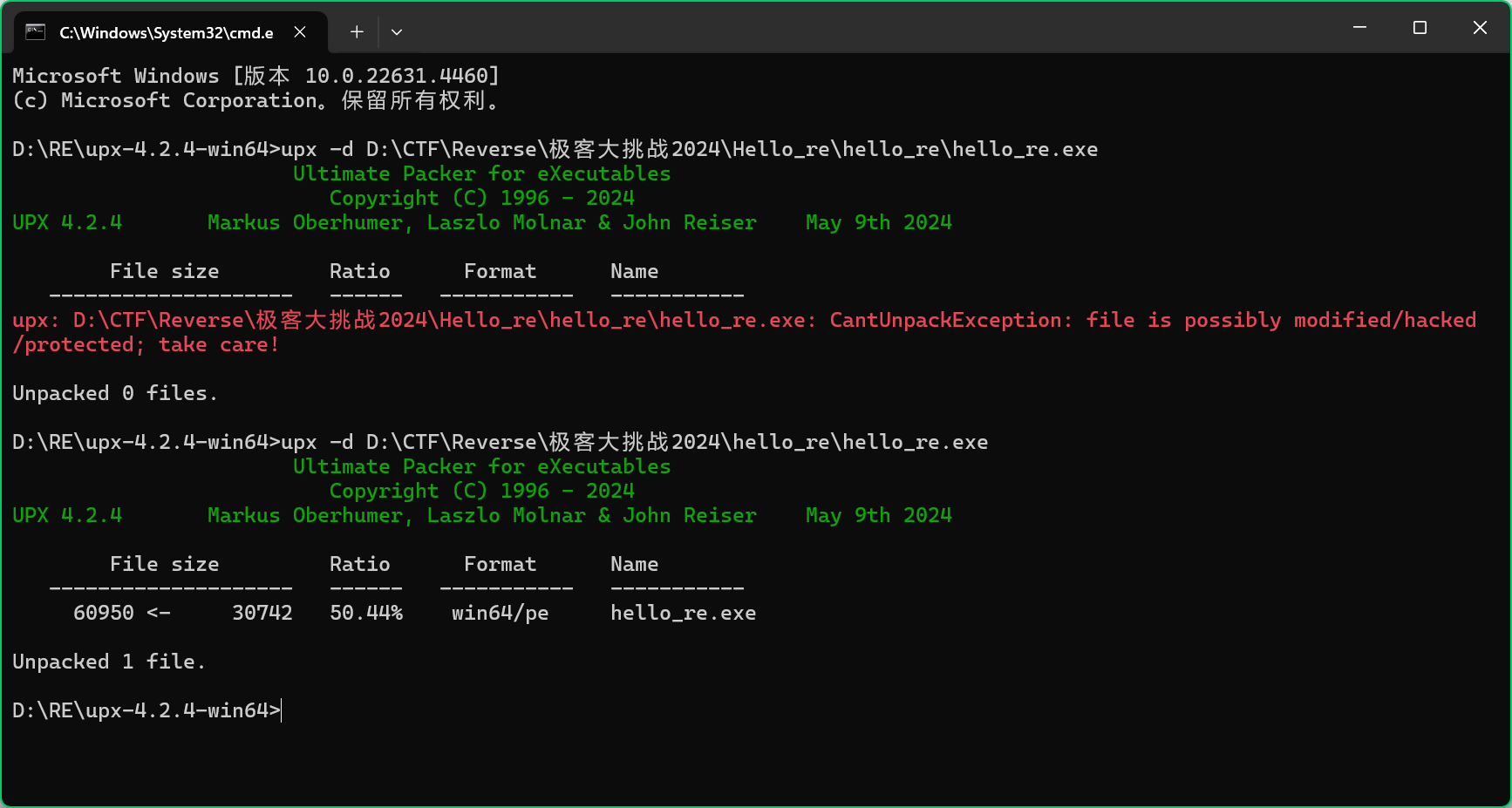
脱壳
die打开发现有upx壳
一键不能去除,用010打开发现魔改了,将SYC0改为UPX0即可
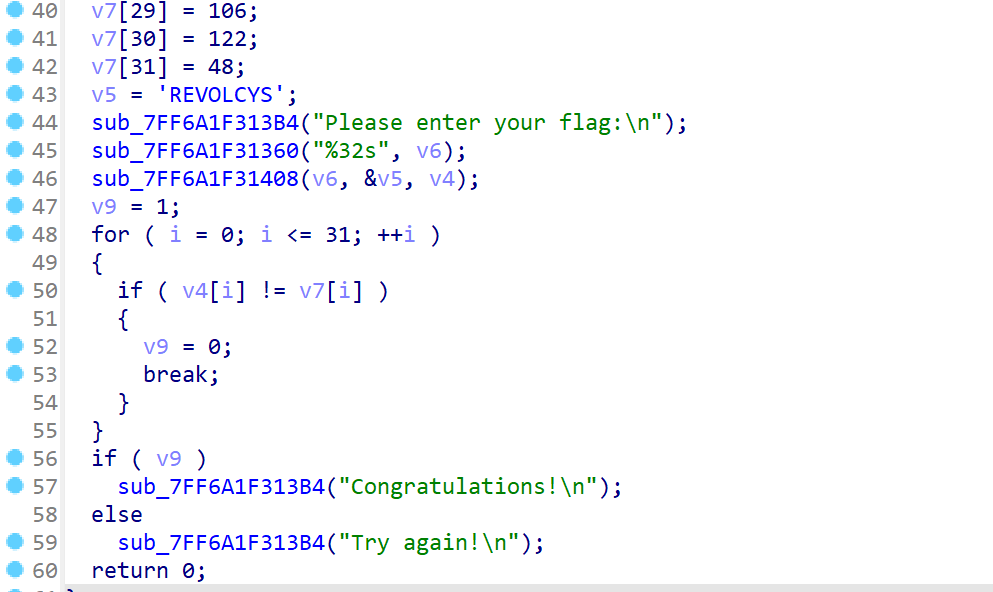
是个很简单的加密
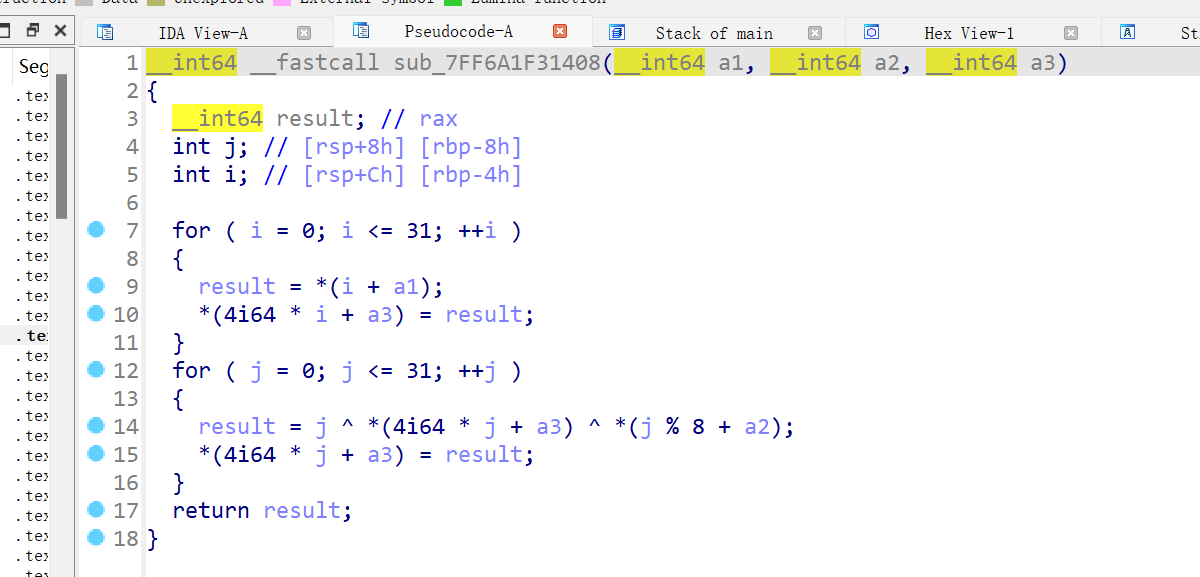
编写解密脚本
key = [0x53, 0x59, 0x43, 0x4C, 0x4F, 0x56, 0x45, 0x52]
enc = [0, 1, 2, 52, 3, 96, 47, 28, 107, 15, 9, 24, 45, 62, 60, 2, 17, 123, 39, 58, 41, 48, 96, 26, 8, 52, 63, 100, 33, 106, 122, 48]
for i in range(32):
enc[i] ^= i ^ key[i % 8]
print(chr(enc[i]), end='')
#SYC{H3lI0_@_new_R3vers3_Ctf3r!!}
先来一道签到题
.file "chal_custom.c"
.text
.section .rodata
.LC0:
.string "%s"
.LC1:
.string "maybe try again!"
.LC2:
.string "good job!"
.data
target_data:
.string "TTDv^jrZu`Gg6tXfi+pZojpZSjXmbqbmt.&x"
.text
.globl main
.type main, @function
main:
endbr64
pushq %rbp
movq %rsp, %rbp
subq $96, %rsp //初始化栈帧
movq %fs:40, %rax
movq %rax, -8(%rbp)
xorl %eax, %eax
leaq -80(%rbp), %rax
movq %rax, %rsi
leaq .LC0(%rip), %rax
movq %rax, %rdi
movl $0, %eax
call __isoc99_scanf@PLT //获取用户输入
movl $0, -84(%rbp)
leaq -80(%rbp), %rdi
jmp .L2
.L3:
movl -84(%rbp), %eax //获取i
movl %eax, %ecx
shl %ecx //将i左移一位,也就是乘2
movzbl (%rdi,%rcx), %eax
xorb $7, %al //获取当前值,异或7
movb %al, (%rdi,%rcx)
movzbl 1(%rdi,%rcx), %eax //将i加1
subb $5, %al //将当前索引值减 5
movb %al, 1(%rdi,%rcx)
addl $1, -84(%rbp)
.L2:
movl -84(%rbp), %eax
imull $2, %eax
cmpl $36, %eax
jl .L3
leaq target_data(%rip), %rsi
leaq -80(%rbp), %rdi
call strcmp@PLT
testl %eax, %eax
jne .L4
leaq .LC2(%rip), %rax //比较
jmp .L5
.L4:
leaq .LC1(%rip), %rax
.L5:
movq %rax, %rdi
call puts@PLT
movl $0, %eax
movq -8(%rbp), %rdx
subq %fs:40, %rdx
je .L6
call __stack_chk_fail@PLT
.L6:
leave
ret
.size main, .-main
.ident "GCC: (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0"
.section .note.GNU-stack,"",@progbits
.section .note.gnu.property,"a"
.align 8
.long 1f - 0f
.long 4f - 1f
.long 5
0:
.string "GNU"
1:
.align 8
.long 0xc0000002
.long 3f - 2f
2:
.long 0x3
3:
.align 8
4:
解密脚本
enc = [84, 84, 68, 118, 94, 106, 114, 90, 117, 96, 71, 103, 54, 116, 88, 102, 105, 43, 112, 90, 111, 106, 112, 90, 83, 106, 88, 109, 98, 113, 98, 109, 116, 46, 38, 120]
for i in range(len(enc)):
if i % 2 == 0:
print(chr(enc[i] ^ 7), end='')
else:
print(chr(enc[i] + 5), end='')
#SYC{You_re@l1y_kn0w_how_To_revers3!}
也许你也听jay
enc = [0x96, 0xa1, 0xa0, 0x9b, 0x9b, 0x5f, 0x49, 0x46, 0x85, 0x82, 0x53, 0x95, 0x7d, 0x36, 0x8d, 0x74, 0x82, 0x88, 0x46, 0x7a, 0x81, 0x65, 0x80, 0x6c, 0x78, 0x2f, 0x6b, 0x6a, 0x27, 0x50, 0x61, 0x38, 0x3f, 0x37, 0x33, 0xf1, 0x27, 0x32, 0x34, 0x1f, 0x39, 0x23, 0xde, 0x1c, 0x17, 0xd4]
key1 = [0x5D, 0x5C, 0x5B, 0x5A, 0x59, 0x58, 0x57, 0x56, 0x55, 0x54, 0x53, 0x52, 0x51, 0x50, 0x4F, 0x4E, 0x4D, 0x4C, 0x4B, 0x4A, 0x49, 0x48, 0x47, 0x46, 0x45, 0x44, 0x43, 0x42, 0x41, 0x40, 0x3F, 0x3E, 0x3D, 0x3C, 0x3B, 0x3A, 0x39, 0x38, 0x37, 0x36, 0x35, 0x34, 0x33, 0x32, 0x31, 0x30, 0x2F, 0x2E, 0x2D, 0x2C, 0x2B, 0x2A, 0x29, 0x28, 0x27, 0x26, 0x25, 0x24, 0x23, 0x22, 0x21, 0x20, 0x1F, 0x1E, 0x1D, 0x1C, 0x1B, 0x1A, 0x19, 0x18, 0x17, 0x16, 0x15, 0x14, 0x13, 0x12, 0x11, 0x10, 0x0F, 0x0E, 0x0D, 0x0C, 0x0B, 0x0A, 0x09, 0x08, 0x07, 0x06, 0x05, 0x04, 0x03, 0x02, 0x01]
key2 = [0x65, 0x64, 0x63, 0x62, 0x61, 0x60, 0x5F, 0x5E, 0x5D, 0x5C, 0x5B, 0x5A, 0x59, 0x58, 0x57, 0x56, 0x55, 0x54, 0x53, 0x52, 0x51, 0x50, 0x4F, 0x4E, 0x4D, 0x4C, 0x4B, 0x4A, 0x49, 0x48, 0x47, 0x46, 0x45, 0x44, 0x43, 0x42, 0x41, 0x40, 0x3F, 0x3E, 0x3D, 0x3C, 0x3B, 0x3A, 0x39, 0x38, 0x37, 0x36, 0x35, 0x34, 0x33, 0x00, 0x31, 0x30, 0x2F]
key3 = [ 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, 0x07, 0x08, 0x09, 0x0A, 0x0B, 0x0C, 0x0D, 0x0E, 0x0F, 0x10, 0x11, 0x12, 0x13, 0x14, 0x15, 0x16, 0x17, 0x18, 0x19, 0x1A, 0x1B, 0x1C, 0x1D, 0x1E, 0x1F, 0x20, 0x21, 0x22, 0x23, 0x24, 0x25, 0x26, 0x27, 0x28, 0x29, 0x2A, 0x2B, 0x2C, 0x2D, 0x2E, 0x2F, 0x30, 0x31, 0x32, 0x33, 0x34, 0x35, 0x36, 0x37, 0x38, 0x39, 0x3A, 0x3B, 0x3C, 0x3D, 0x3E, 0x3F, 0x40, 0x41, 0x42, 0x43, 0x44, 0x45, 0x46, 0x47, 0x48, 0x49, 0x4A, 0x4B, 0x4C, 0x4D, 0x4E, 0x4F, 0x50, 0x51, 0x52, 0x53, 0x54, 0x55, 0x56, 0x57, 0x58, 0x59, 0x5A, 0x5B, 0x5C, 0x5D, 0x5E, 0x5F, 0x60, 0x61, 0x62, 0x63, 0x64, 0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6B, 0x6C, 0x6D, 0x6E, 0x6F, 0x70, 0x71, 0x72, 0x73, 0x74, 0x75, 0x76, 0x77, 0x78, 0x79, 0x7A, 0x7B, 0x7C, 0x7D, 0x7E, 0x7F, 0x80, 0x81, 0x82, 0x83, 0x84, 0x85, 0x86, 0x87, 0x88, 0x89, 0x8A, 0x8B, 0x8C, 0x8D]
strlen = 46
for i in range(strlen):
key2[i] ^= key1[i + 1]
for i in range(strlen):
key2[i] -= key3[i]
for i in range(strlen):
enc[i] -= key1[i]
for i in range(strlen):
key3[i] ^= key2[51]
enc[i] += key3[47 + i]
for i in range(strlen):
enc[i] ^= key3[i]
print((chr(enc[i] & 0xff)), end='')
#https://am1re-sudo.github.io/Coisni.github.io/
点开的的网页,发现了密文和密钥和加密方式
密文:Q7u+cyiOQtKHRMqZNzPpApgmTL4j+TE=
key :lovebeforeBC
加密方式 : rc4
from base64 import *
def KSA(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def PRGA(S):
i, j = 0, 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
yield K
def RC4Decrypt(key, text):
S = KSA(key)
keystream = PRGA(S)
res = []
for char in text:
res.append(char ^ next(keystream))
return bytes(res)
key = b'lovebeforeBC'
plaintext = b'Q7u+cyiOQtKHRMqZNzPpApgmTL4j+TE='
Rc4encrypt = RC4Decrypt(key, b64decode(plaintext))
print(Rc4encrypt.decode())
#SYC{ILIKELISTENJAYSONG}
让我康康你的调试
无壳,打开程序的加密处
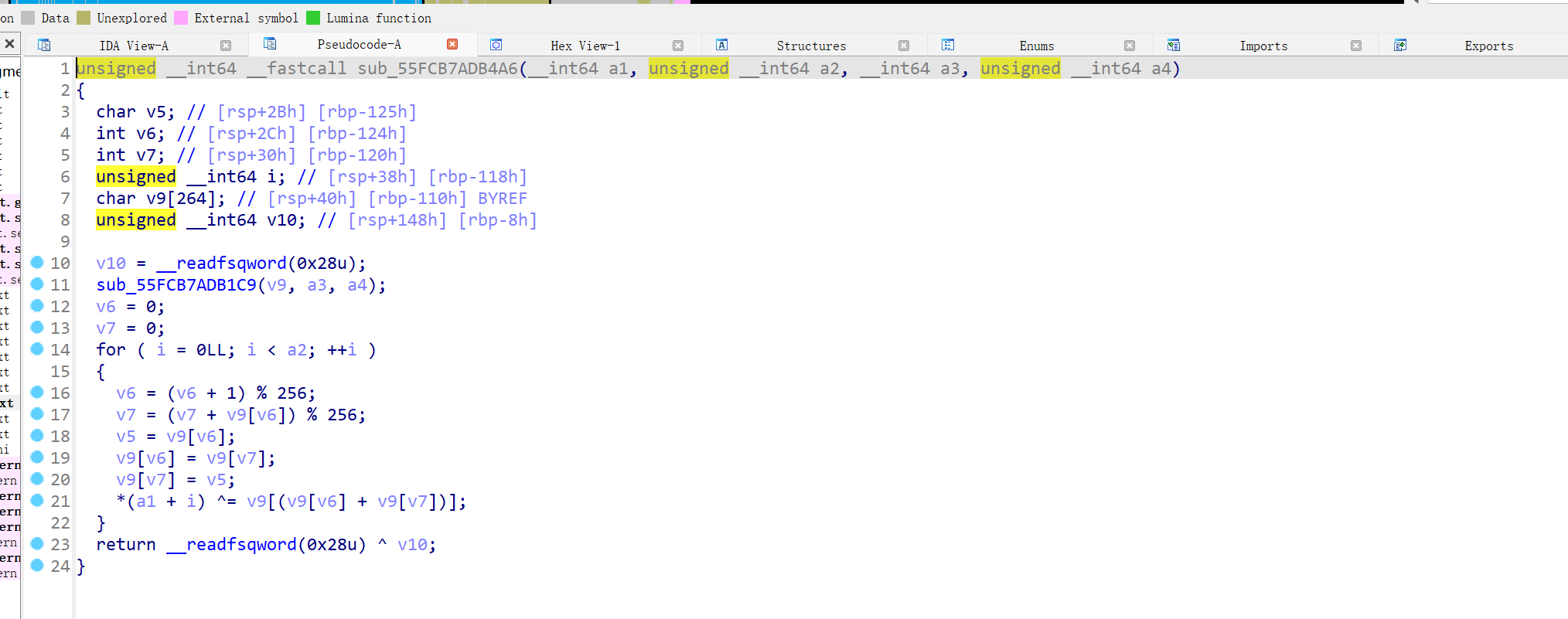
一眼是rc4加密,是对称加密,可以用动调解
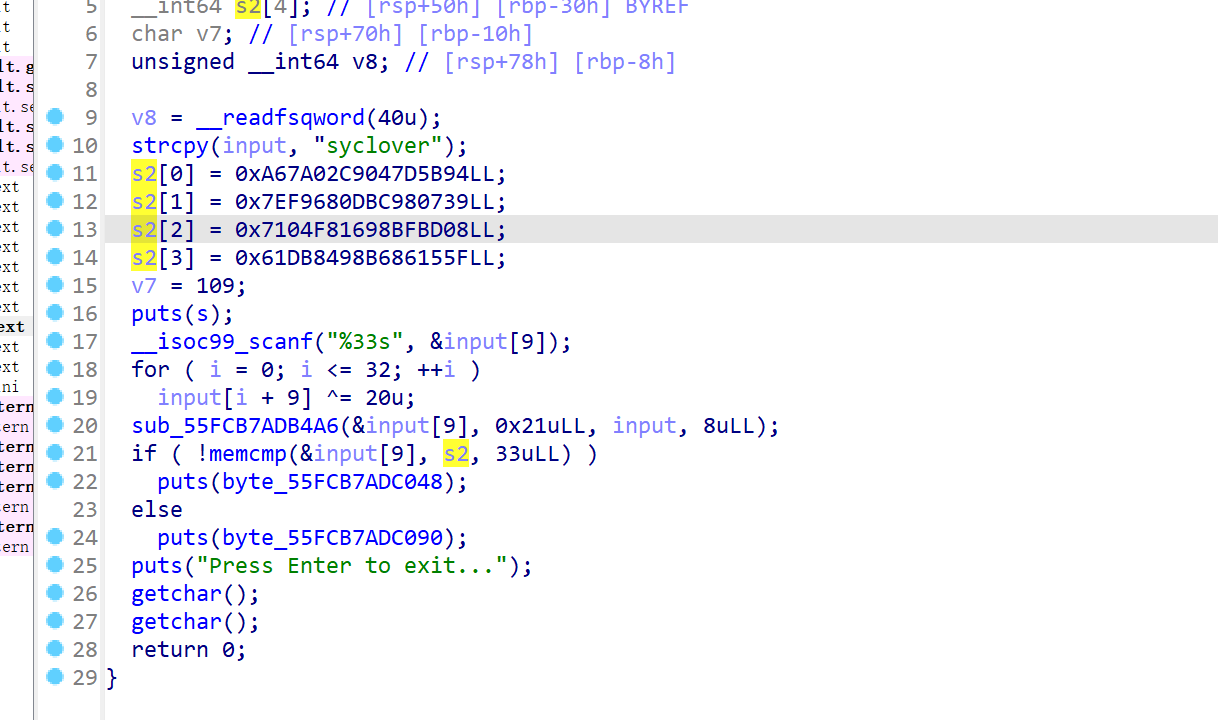
cmp函数使用了s2的值,也就是密文
用struct库将密文弄下来(v7也是密文的一部分,是溢出的)
enc = [0x94, 0x5B, 0x7D, 0x04, 0xC9, 0x02, 0x7A, 0xA6, 0x39, 0x07, 0x98, 0xBC, 0x0D, 0x68, 0xF9, 0x7E, 0x08, 0xBD, 0xBF, 0x98, 0x16, 0xF8, 0x04, 0x71, 0x5F, 0x15, 0x86, 0xB6, 0x98, 0x84, 0xDB, 0x61, 0x6D ]
动调放进去就行
先放等长的1进去
用lazyida插件改内存
下断点F9执行完加密函数
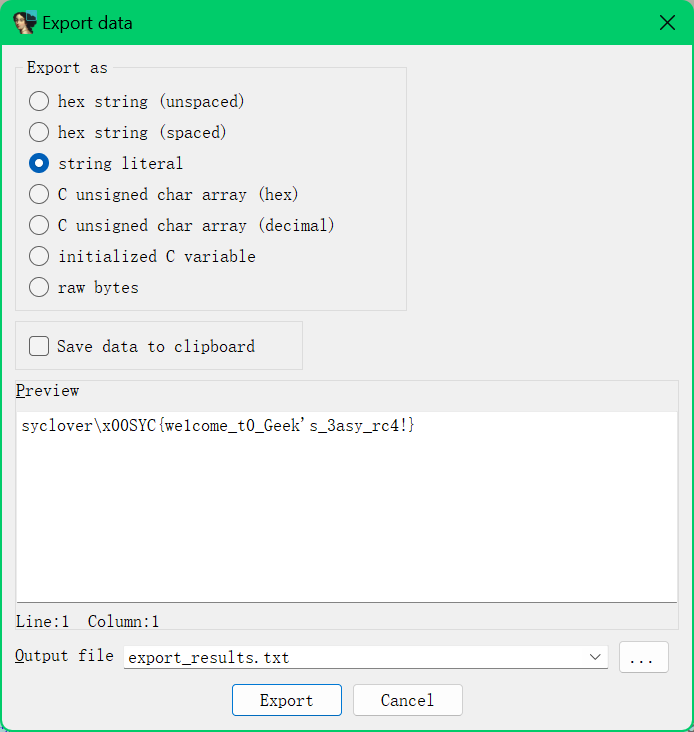
SYC{we1come_t0_Geek's_3asy_rc4!}
我勒个z3啊
先解出里面的方程
from z3 import *
enc = [0x19B, 0x113, 0x189, 0x1C9, 0x250, 0x536, 0x4DE, 0x1BC, 0x41B, 0x724, 0x6D0, 0x4A1, 0x645, 0x475, 0x4CA, 0x68C, 0x3E5,
0x1C7, 0x33D, 0x5B7, 0x28D, 0x244, 0x30E, 0x291, 0x271, 0x301, 0x45F, 0x46F, 0x517, 0x41E, 0x426, 0x4B5]
s = Solver()
x = [Int(f"x{i}") for i in range(0, 32)]
for i in range(0, len(enc), 4):
s.add(x[i] + 8 * x[i + 1] + 6 * x[i + 2] + x[i + 3] == enc[i])
s.add(x[i + 1] + 8 * x[i + 2] + 6 * x[i + 3] + x[i] == enc[i + 1])
s.add(x[i + 2] + 8 * x[i + 3] + 6 * x[i] + x[i + 1] == enc[i + 2])
s.add(x[i + 3] + 8 * x[i] + 6 * x[i + 1] + x[i + 2] == enc[i + 3])
s.check() == sat
result = s.model()
array = []
for i in range(len(enc)):
array.append(result[Int(f'x{i}')].as_long())
print(array)
#array = [23, 40, 7, 26, 29, 3, 69, 125, 111, 9, 125, 118, 99, 126, 74, 54, 112, 89, 28, 5, 25, 63, 9, 70, 111, 26, 43, 48, 58, 102, 60, 69]
再逆第二个异或
key = 'Geek___Challenge'
enc = [23, 40, 7, 26, 29, 3, 69, 125, 111, 9, 125, 118, 99, 126, 74, 54, 112, 89, 28, 5, 25, 63, 9, 70, 111, 26, 43, 48, 58, 102, 60, 69]
for i in range(len(enc)-1, -1, -1):
enc[i] ^= ord(key[(47 - i) % 16]) ^ i
enc[i] ^= enc[(len(enc) + i - 1) % len(enc)]
print(enc)
再经过一次位置替换
enc = 'SYC{ow!WY0!_ru_43_9od_A0r3t_}$!!'
flag = ''
for i in range(8):
tmp1 = enc[4 * i:4 * i + 4]
for j in range(i):
tmp2 = ''
tmp2 += tmp1[3] + tmp1[0:3]
tmp1 = tmp2
flag += tmp1
print(flag)
#SYC{Wow!!_Y0u_4r3_9o0d_At_r3$!!}
ezzzz
XTEA加密
from ctypes import *
from Crypto.Util import *
key = [71, 69, 69, 75]
enc = [0xb286f1f1, 0x82c7965a, 0xb3ac6e6, 0x5c1bb670, 0x48f86bed, 0x6b0d7089, 0x5c1b3809, 0xfa242fcb, 0x799ec7b1,
0x9c2d826d, 0x765fc5dc, 0x750e780f, 0xafc4650d, 0xa98490b8, 0x82c378e9, 0x10d88d7a, 0xf38df291, 0xcaba4da8,
0x755fd7b4, 0xe5f89af1, 0xfc800fb9, 0xc3a510fc, 0xfb7906d2, 0xc834c72b, 0x921cb3cc, 0xd32ac51a, 0xb722f9e7,
0x23d9242e, 0xf5e94cfb, 0xe5a94835, 0x5ac2eb71, 0x2e8638df, 0x86910510, 0x46097532, 0x4cd5d43d, 0x36bc5a90,
0x12536dc2, 0xc042cdd2, 0xe5992d77, 0x66c4d40c, 0xd678315c, 0x71fe7f3a, 0xc051a2ad, 0x5a8d5670, 0x92c29857,
0xfcf7c01e, 0x41d8e93a, 0x29766084, 0x2d6aca30, 0xd251efcc, 0x5408a8a1, 0x2df8b091, 0x47a36c68, 0xf2dc574,
0x9f44260f, 0x2c368dc2, 0x1b31f386, 0xb14fdc8a, 0x347e49a4, 0x5d91f0e0]
# enc = [0xf1f186b2, 0x5a96c782, 0xe6c63a0b, 0x70b61b5c, 0xed6bf848, 0x89700d6b, 0x09381b5c, 0xcb2f24fa, 0xb1c79e79,
# 0x6d822d9c, 0xdcc55f76, 0x0f780e75, 0x0d65c4af, 0xb89084a9, 0xe978c382, 0x7a8dd810, 0x91f28df3, 0xa84dbaca,
# 0xb4d75f75, 0xf19af8e5, 0xb90f80fc, 0xfc10a5c3, 0xd20679fb, 0x2bc734c8, 0xccb31c92, 0x1ac52ad3, 0xe7f922b7,
# 0x2e24d923, 0xfb4ce9f5, 0x3548a9e5, 0x71ebc25a, 0xdf38862e, 0x10059186, 0x32750946, 0x3dd4d54c, 0x905abc36,
# 0xc26d5312, 0xd2cd42c0, 0x772d99e5, 0x0cd4c466, 0x5c3178d6, 0x3a7ffe71, 0xada251c0, 0x70568d5a, 0x5798c292,
# 0x1ec0f7fc, 0x3ae9d841, 0x84607629, 0x30ca6a2d, 0xccef51d2, 0xa1a80854, 0x91b0f82d, 0x686ca347, 0x74c52d0f,
# 0x0f26449f, 0xc28d362c, 0x86f3311b, 0x8adc4fb1, 0xa4497e34, 0xe0f0915d]
for i in range(0, len(enc), 2):
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i+1])
delta = 1640531527
r = 32
sum = c_uint32(r * -delta)
for j in range(r):
v1.value -= (key[(sum.value >> 11) & 3] + sum.value) ^ (v0.value + ((v0.value >> 5) ^ (v0.value << 4))) ^ (sum.value + j)
sum.value += 1640531527
v0.value -= (key[sum.value & 3] + sum.value) ^ (v1.value + ((v1.value >> 5) ^ (v1.value << 4))) ^ (sum.value + j)
enc[i] = v0.value
enc[i+1] = v1.value
for i in range(len(enc)):
print(hex(enc[i])[2:], end='')
# print(number.long_to_bytes(enc[i]).decode()[::-1], end='')
CPP_flower
DH爱喝茶
去花
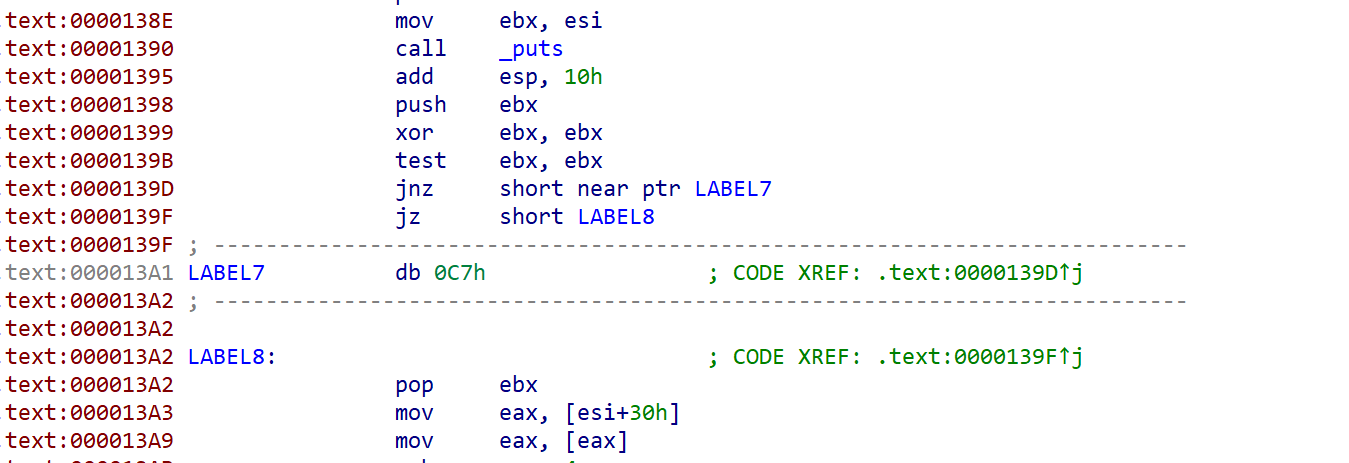
删掉jnz和0c7h
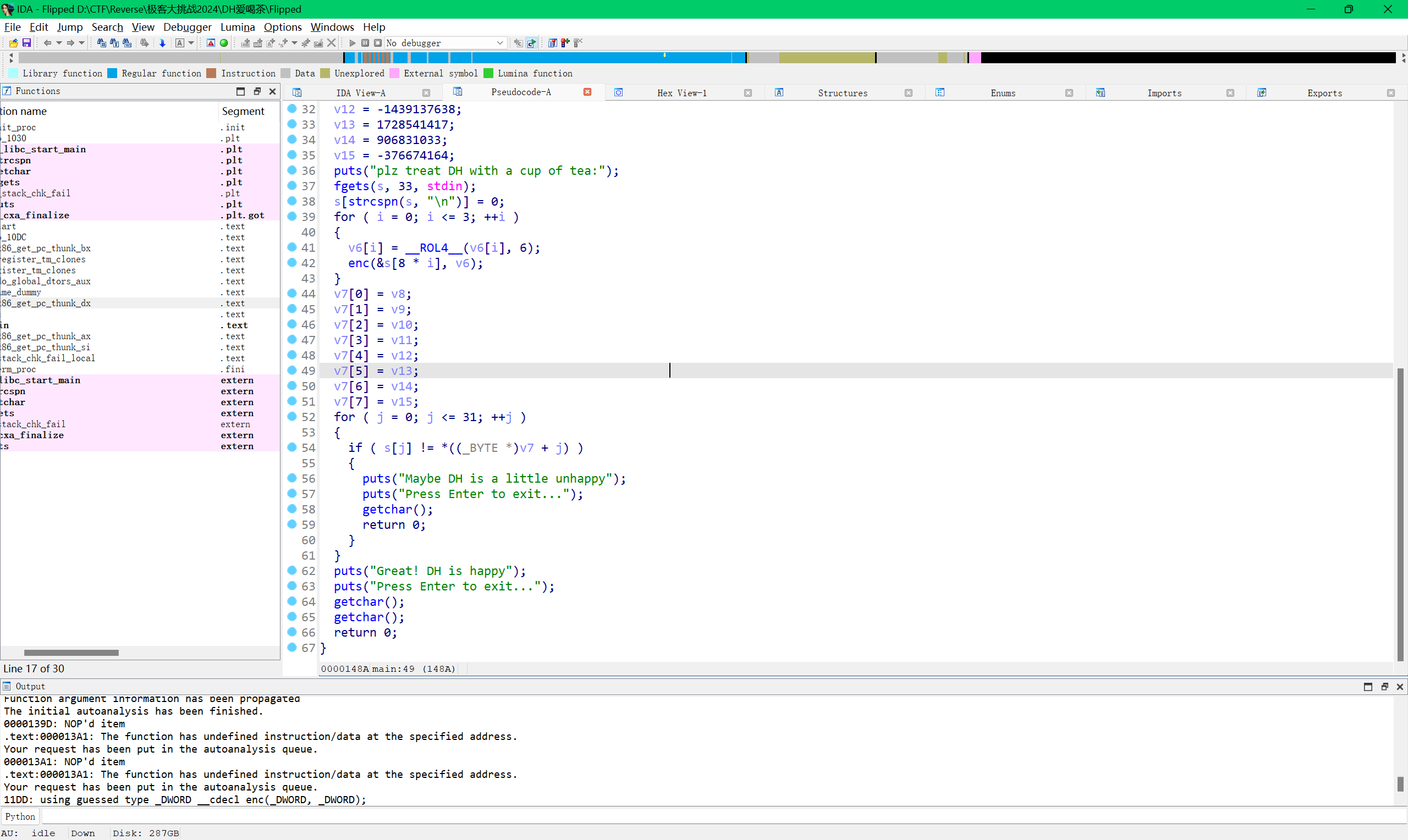
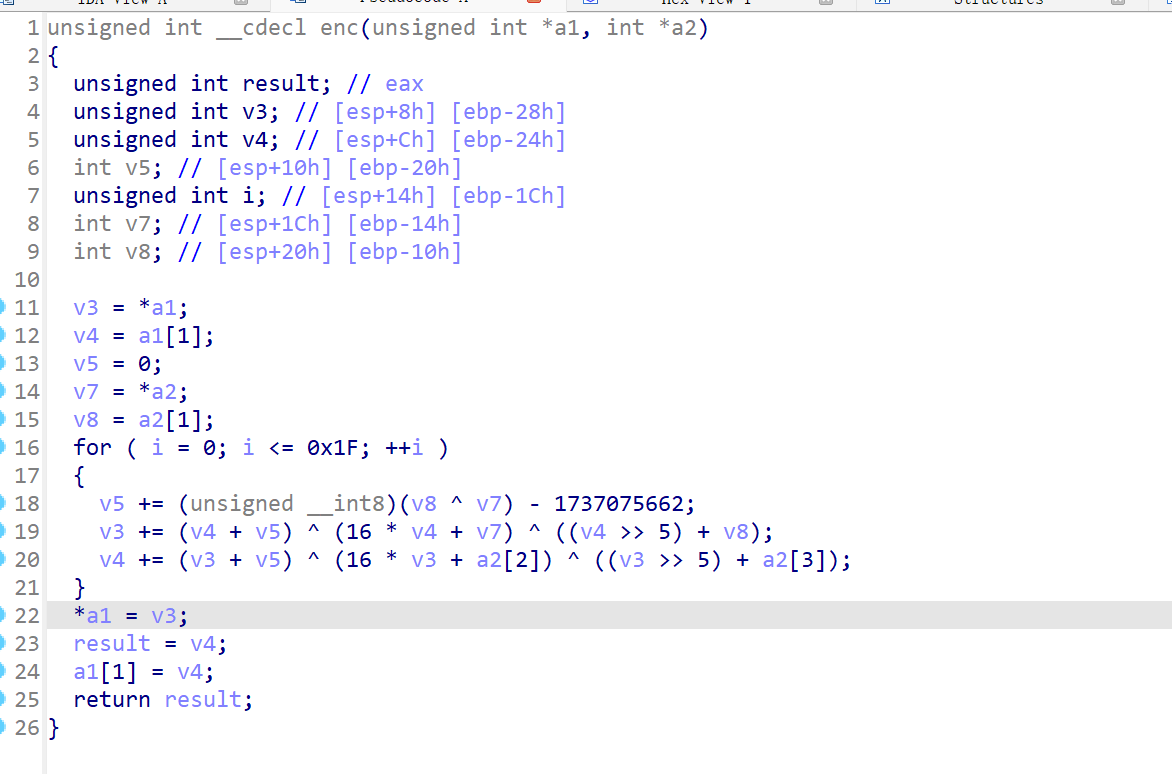
更换了加密过程,delta,key轮换的tea加密
python脚本(注意 v5 += (unsigned __int8)(v8 ^ v7) - 1737075662;的数据类型)
from ctypes import *
from Crypto.Util import *
key = [0x56789ABC, 0x6789ABCD, 0x789ABCDE, 0x89ABCDEF]
tmp = [0x9E26AF15, 0xE26AF359, 0x26AF379E, 0x6AF37BE2]
enc = [0x1F85A965, 0xEEC063EC, 0x5BF1D0B6, 0xF2FDE7B0, 0xAA38809A, 0x670772E9, 0x360D24B9, 0xE98C688C]
for i in range(0, len(enc), 2):
key[i // 2] = tmp[i // 2]
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i + 1])
sum = c_int32((((key[0] ^ key[1]) & 0xff) - 0x6789ABCE) * 32)
r = 32
for j in range(r):
v1.value -= (sum.value + v0.value) ^ (key[2] + 16 * v0.value) ^ (key[3] + (v0.value >> 5))
v0.value -= (sum.value + v1.value) ^ (key[0] + 16 * v1.value) ^ (key[1] + (v1.value >> 5))
sum.value -= ((key[0] ^ key[1]) & 0xff) - 0x6789ABCE
enc[i] = (v0.value)
enc[i + 1] = (v1.value)
print(number.long_to_bytes(enc[i]).decode()[::-1], end="")
print(number.long_to_bytes(enc[i+1]).decode()[::-1], end="")
#SYC{DH_likes_flower_and_tea!!!!}
好像是python?
enc = [255, 220, 26, 251, 14, 41, 6, 247, 60, 29, 228, 17, 21, 7, 35, 38, 26, 48]
key = 'SYC'
flag = []
for i in range(len(enc)):
flag.append(chr(((enc[i]) - (~ord(key[i % 3]) + 1) ^ i)&0xff))
result = ''
R = 14
for i in flag:
if 'A' <= i <= 'Z':
result += (chr(((ord(i) - ord('A') - R) % 26) + ord('A')))
elif 'a' <= i <= 'z':
result += (chr(((ord(i) - ord('a') - R) % 26) + ord('a')))
elif '0' <= i <= '9':
result += (chr(((ord(i) - ord('0') - R) % 10) + ord('0')))
else:
result += (i)
print(result)
#D0_You_Iik3_python
奇怪的RC4
拆包(注意要用python3.8版本)
把里面的rc4.pyc和easy_xor_and_rc4.pyc反编译了
是两个异或加一个魔改了最后异或部分的rc4
解密
enc = [158, 31, 205, 434, 354, 15, 383, 298, 304, 351, 465, 312, 261, 442,
397, 474, 310, 397, 31, 21, 78, 67, 47, 133, 168, 48, 153, 99, 103,
204, 137, 29, 22, 13, 228, 3, 136, 141, 248, 124, 26, 26, 65, 200,
7]
for i in range(len(enc)-2, -1, -1):
enc[i+1] = enc[i] ^ enc[i+1]
for i in range(len(enc)):
enc[i] ^= i
def KSA(key):
j = 0
S = list(range(256))
key_length = len(key)
for i in range(256):
j = (j + S[i] + key[i % key_length]) % 256
S[i], S[j] = S[j], S[i]
else:
return S
def PRGA(S):
i = 0
j = 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
k = (S[i] + S[j]) % 256
yield k
def rc4(plaintext, key):
key = [ord(i) for i in key]
S = KSA(key)
xor_value = PRGA(S)
for i in range(len(plaintext)):
plaintext[i] ^= int(next(xor_value)) + 6
for i in range(len(plaintext)):
plaintext[i] -= i
return plaintext
plaintxt = enc
key = 'SYCFOREVER'
result = rc4(plaintxt, key)
for i in result:
print(chr(i), end='')
#SYC{Bel1eve_thAt_you_a3e_Unique_@nd_tHe_beSt}
玩就行了
先用ce修改器达到目标
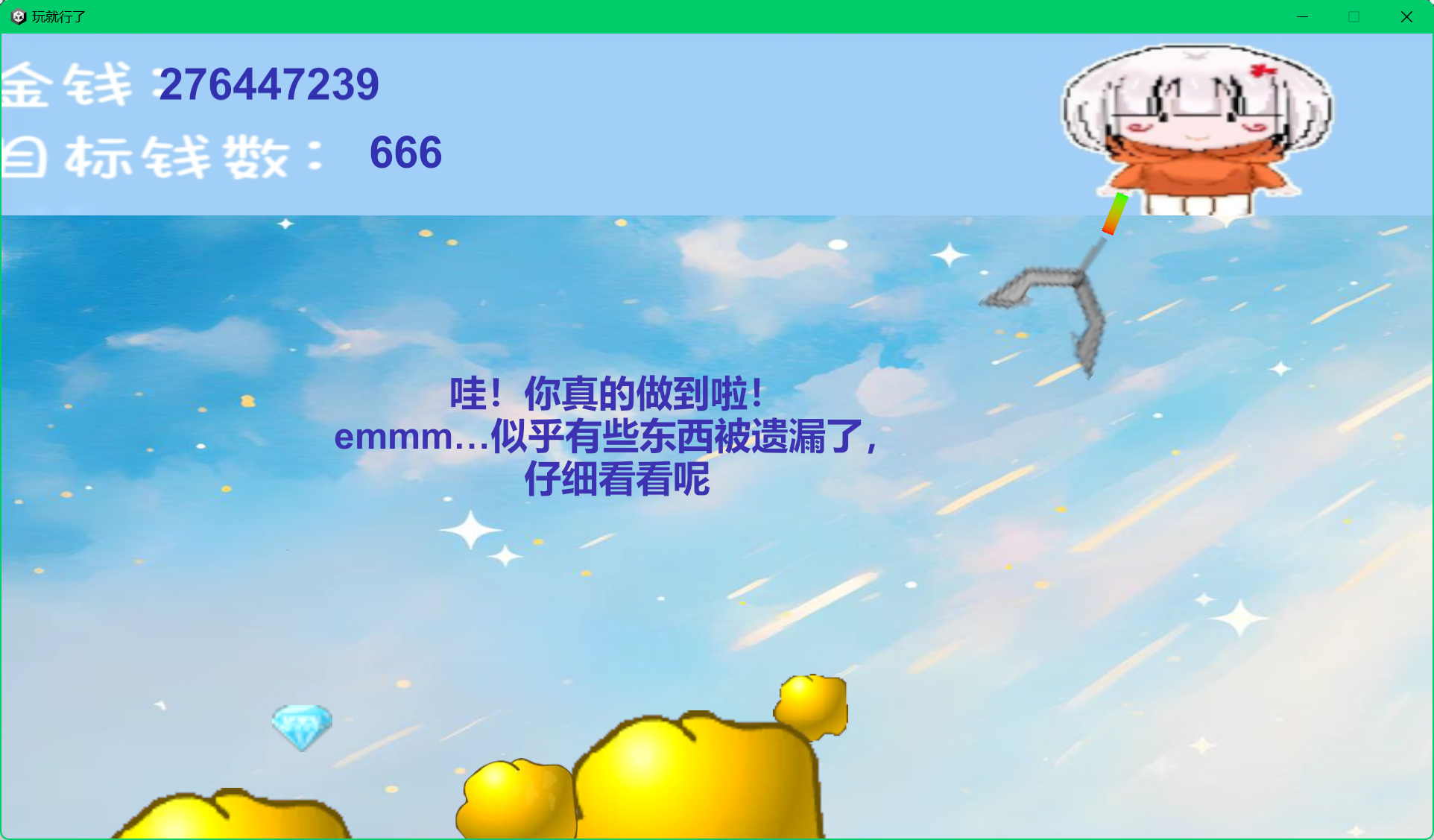
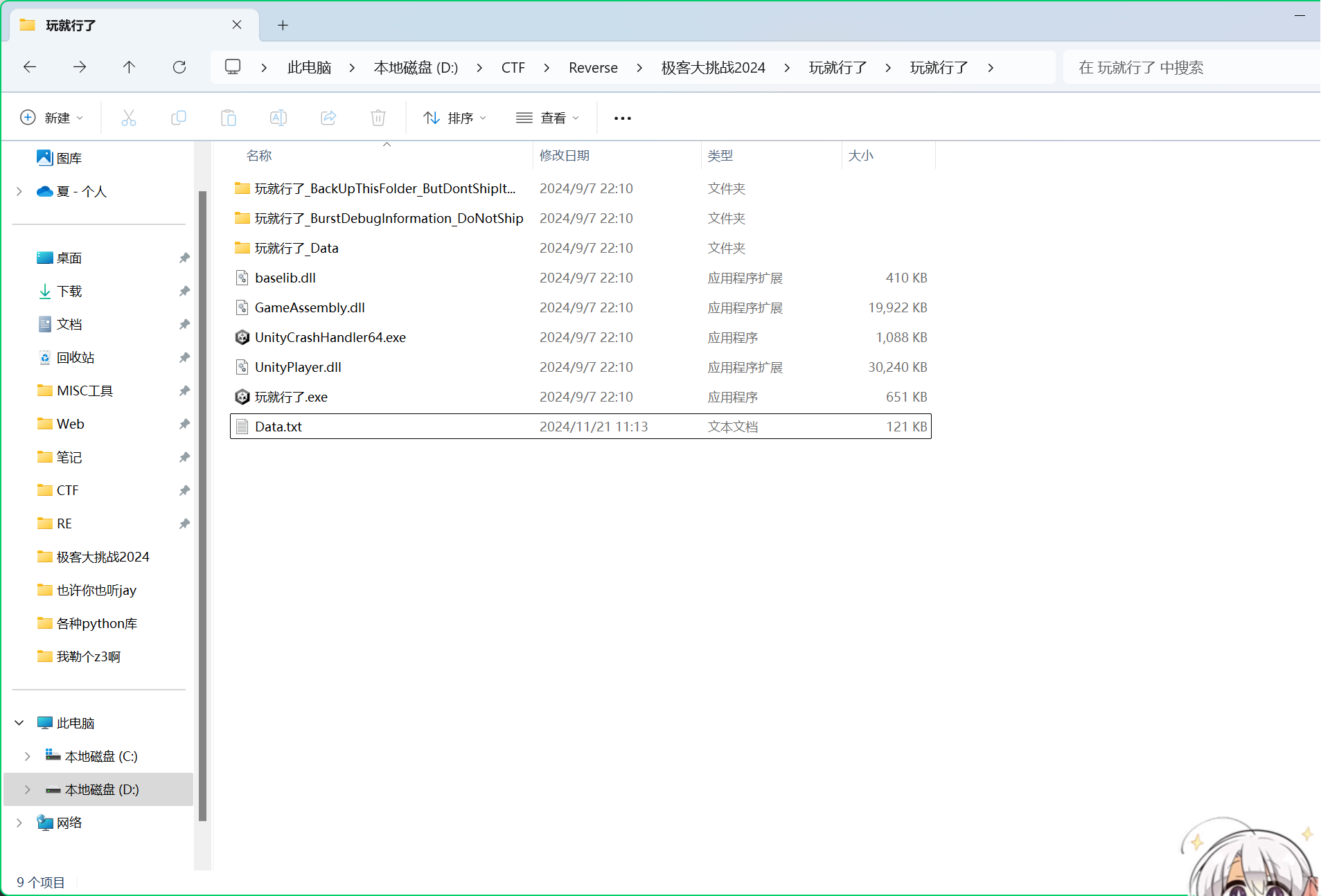
文件生成了一个data.txt
打开即可看到pe文件头
用hex文件保存
ida打开
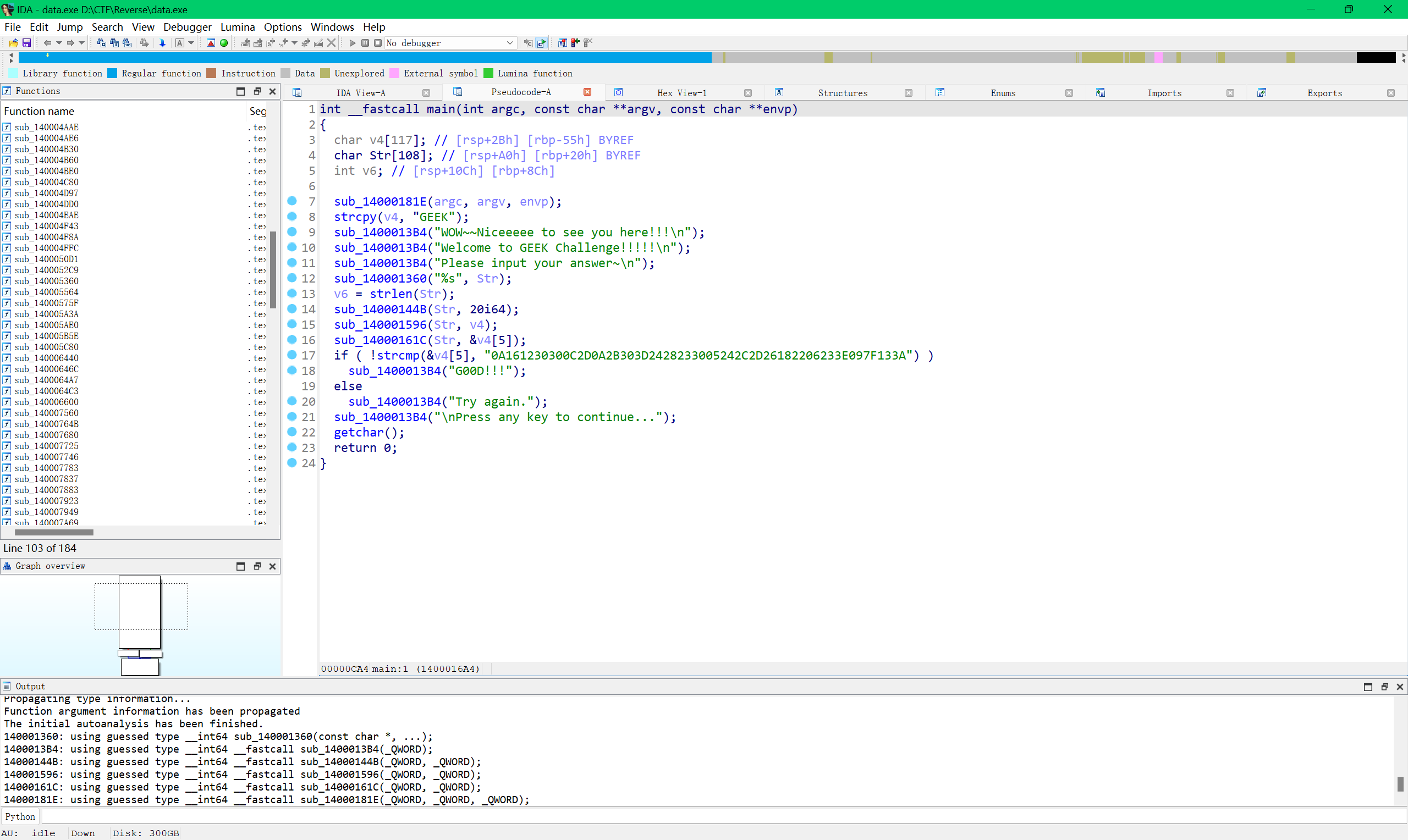
很简单的异或+凯撒
key = 'GEEK'
enc = '0A161230300C2D0A2B303D2428233005242C2D26182206233E097F133A'
tmp = list(bytes.fromhex(enc))
flag = ''
for i in range(len(tmp)):
flag += chr(tmp[i] ^ ord(key[i % len(key)]))
result = ''
R = 20
for i in flag:
if 'A' <= i <= 'Z':
result += (chr(((ord(i) - ord('A') - R) % 26) + ord('A')))
elif 'a' <= i <= 'z':
result += (chr(((ord(i) - ord('a') - R) % 26) + ord('a')))
elif '0' <= i <= '9':
result += (chr(((ord(i) - ord('0') - R) % 10) + ord('0')))
else:
result += (i)
print(result)
#SYC{cOnGraduulaTions_mIneR:D}
长颈鹿喜欢吃彩虹
先用b810去平坦化
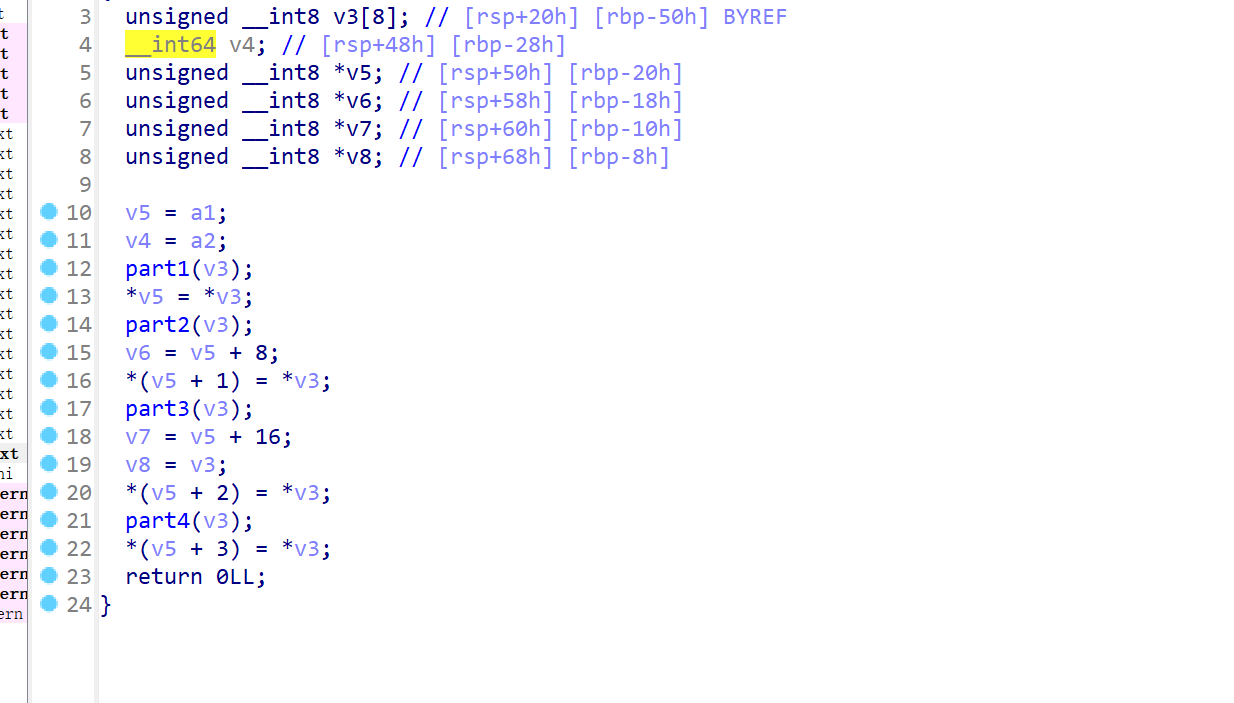
这里是密文,小端序弄出来
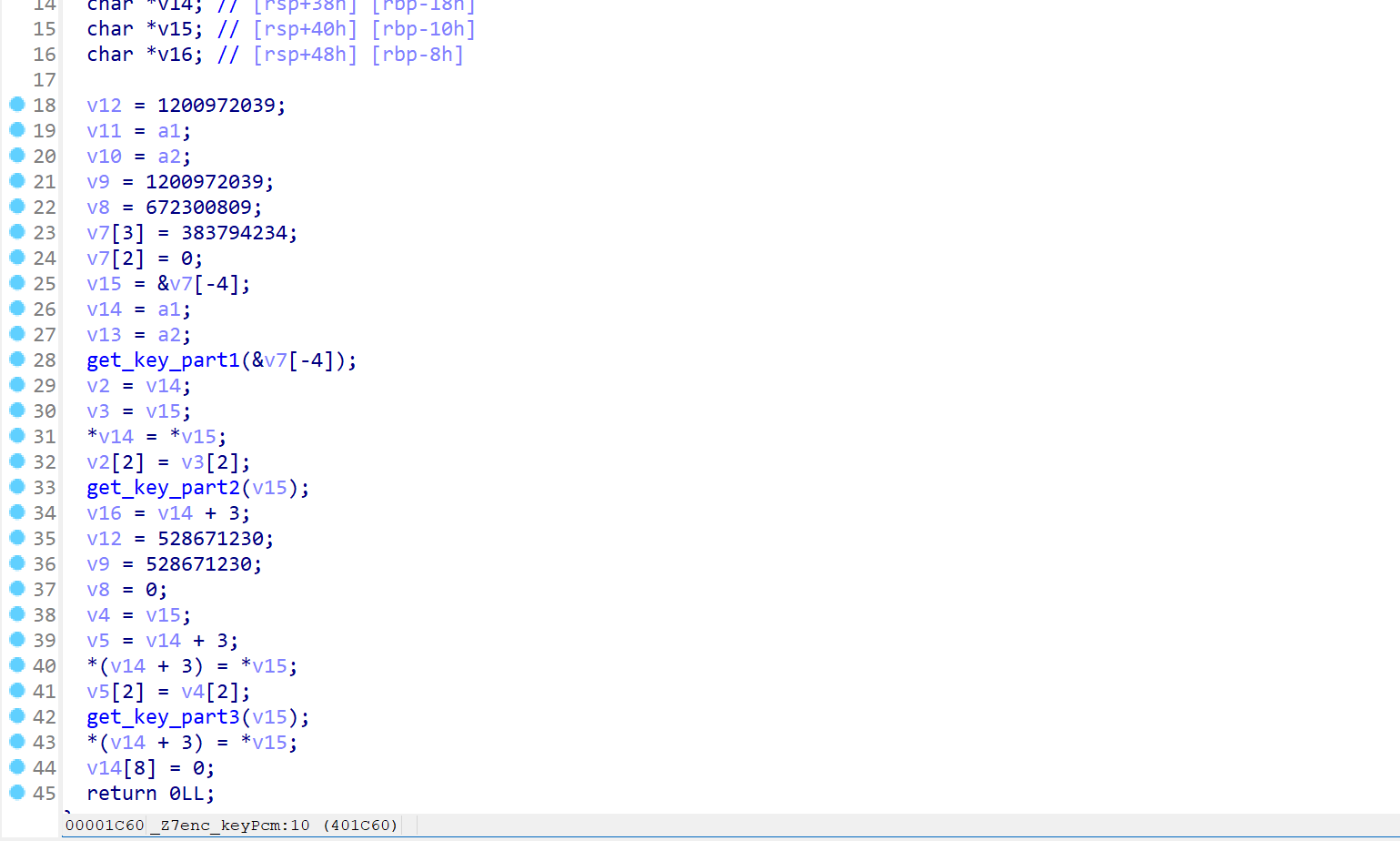
这里是key,动调弄出来(只有8位)
encrypt函数关键加密处
直接猜的
enc = [29, 54, 115, 22, 73, 45, 26, 29, 41, 6, 66, 44, 118, 7, 16, 14, 126, 57, 85, 50, 117, 3, 27, 29, 25, 95, 82, 35, 1, 3, 29, 63]
key = [0x42, 0x4f, 0x62, 0x30, 0x6d, 0x30, 0x6f, 0x4e]
result = []
for i in range(len(enc)):
print(chr((enc[i] ^ key[::-1][i % len(key)]) & 0xff), end='')
#SYC{yOU_girAFe_L0Ve_EaT_W0bN1aR}
AES!
程序开了地址随机分配(ASLR)
先用CFF关闭其中的DLL可移动选项(因为我要动调分析,所以关了比较好)
流程
先把秘钥给处理了一下
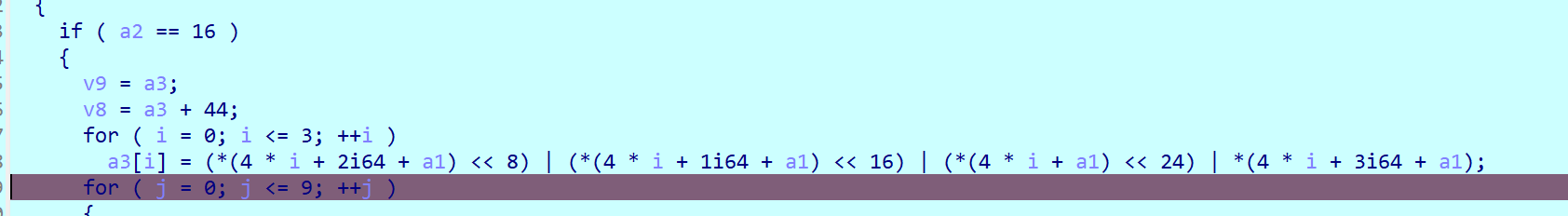
处理后的秘钥: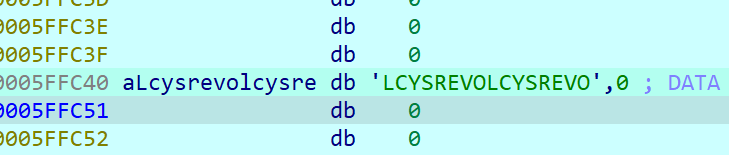
密钥扩展储存区(00000000005FFC50)
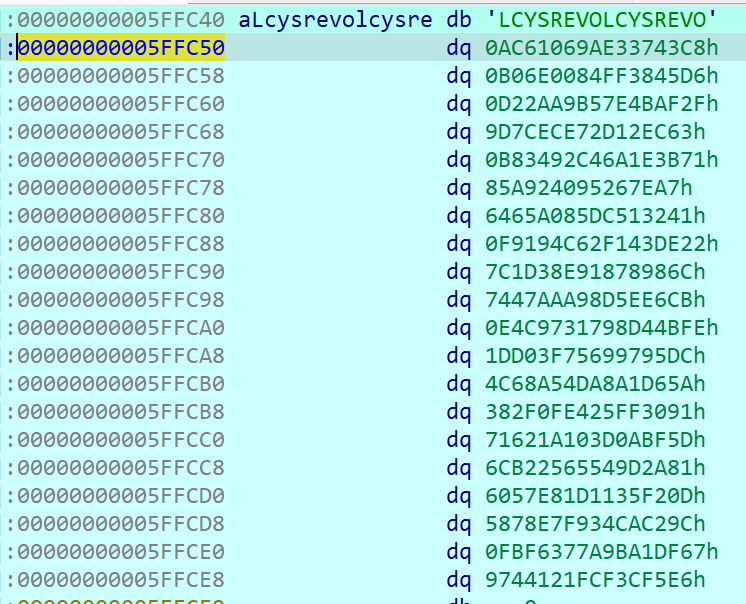
这里再将秘钥[::-1]
替换了s_box
更新:
只更换了s盒
class AES:
MIX_C = [[0x2, 0x3, 0x1, 0x1], [0x1, 0x2, 0x3, 0x1], [0x1, 0x1, 0x2, 0x3], [0x3, 0x1, 0x1, 0x2]]
I_MIXC = [[0xe, 0xb, 0xd, 0x9], [0x9, 0xe, 0xb, 0xd], [0xd, 0x9, 0xe, 0xb], [0xb, 0xd, 0x9, 0xe]]
RCon = [0x01000000, 0x02000000, 0x04000000, 0x08000000, 0x10000000, 0x20000000, 0x40000000, 0x80000000, 0x1B000000, 0x36000000]
S_BOX = [[124, 202, 123, 119, 242, 107, 111, 197, 48, 1, 103, 43, 254, 215, 71, 171],
[118, 99, 130, 201, 125, 250, 89, 240, 173, 212, 162, 175, 156, 164, 114, 192],
[183, 253, 147, 38, 54, 63, 247, 204, 52, 165, 229, 241, 113, 216, 49, 21],
[4, 199, 35, 195, 24, 150, 5, 154, 7, 18, 128, 226, 235, 39, 178, 117],
[9, 131, 44, 26, 27, 110, 90, 160, 82, 59, 214, 179, 41, 227, 47, 132],
[83, 209, 0, 237, 32, 252, 177, 91, 106, 203, 190, 57, 74, 76, 88, 207],
[208, 239, 170, 251, 67, 77, 51, 133, 69, 249, 2, 127, 80, 60, 159, 168],
[81, 163, 64, 143, 146, 157, 56, 245, 188, 182, 218, 33, 16, 255, 243, 210],
[151, 205, 12, 19, 236, 95, 68, 23, 196, 167, 126, 61, 100, 93, 25, 115],
[96, 129, 79, 220, 34, 42, 144, 136, 70, 238, 184, 20, 222, 94, 11, 219],
[224, 50, 58, 10, 73, 6, 36, 92, 194, 211, 172, 98, 145, 149, 228, 121],
[231, 200, 55, 109, 141, 213, 78, 169, 108, 86, 244, 234, 101, 122, 174, 8],
[186, 120, 37, 46, 28, 166, 180, 198, 232, 221, 116, 31, 75, 189, 139, 138],
[112, 62, 181, 102, 72, 3, 246, 14, 97, 53, 87, 185, 134, 193, 29, 158],
[225, 248, 152, 17, 105, 217, 142, 148, 155, 30, 233, 206, 85, 40, 223, 140],
[161, 137, 13, 191, 230, 66, 104, 65, 153, 45, 15, 176, 84, 187, 22, 135]]
I_SBOX = [[82, 9, 106, 213, 48, 54, 165, 56, 191, 64, 163, 158, 130, 242, 215, 250],
[124, 227, 57, 131, 155, 47, 254, 135, 52, 142, 67, 68, 196, 222, 233, 203],
[84, 123, 148, 50, 166, 194, 35, 61, 237, 76, 149, 11, 66, 249, 195, 78],
[8, 46, 161, 102, 40, 217, 36, 178, 118, 91, 162, 73, 109, 139, 209, 37],
[114, 247, 245, 100, 134, 104, 152, 14, 212, 164, 92, 204, 93, 101, 182, 146],
[108, 112, 72, 80, 252, 236, 185, 218, 94, 22, 70, 87, 167, 141, 157, 133],
[144, 216, 171, 17, 140, 188, 211, 10, 246, 228, 88, 5, 184, 179, 69, 6],
[208, 44, 30, 143, 202, 63, 16, 3, 193, 175, 189, 2, 0, 20, 138, 107],
[58, 145, 18, 65, 79, 103, 220, 255, 151, 241, 207, 206, 239, 180, 230, 115],
[150, 172, 116, 34, 231, 173, 53, 128, 226, 248, 55, 232, 28, 117, 223, 110],
[71, 240, 26, 113, 29, 41, 197, 137, 111, 183, 98, 15, 170, 24, 190, 27],
[251, 86, 62, 75, 198, 210, 121, 32, 154, 219, 192, 253, 120, 205, 90, 243],
[31, 221, 168, 51, 136, 7, 199, 49, 177, 19, 1, 89, 39, 129, 235, 95],
[96, 81, 127, 169, 25, 181, 74, 13, 45, 229, 122, 159, 147, 201, 156, 238],
[160, 224, 59, 77, 174, 42, 244, 176, 200, 234, 187, 60, 132, 83, 153, 97],
[23, 43, 4, 126, 186, 119, 214, 38, 225, 105, 21, 99, 85, 33, 12, 125]]
def SubBytes(self, State):
# 字节替换
return [self.S_BOX[i][j] for i, j in
[(_ >> 4, _ & 0xF) for _ in State]]
def SubBytes_Inv(self, State):
# 字节逆替换
return [self.I_SBOX[i][j] for i, j in
[(_ >> 4, _ & 0xF) for _ in State]]
def ShiftRows(self, S):
# 行移位
return [S[0], S[5], S[10], S[15],
S[4], S[9], S[14], S[3],
S[8], S[13], S[2], S[7],
S[12], S[1], S[6], S[11]]
def ShiftRows_Inv(self, S):
# 逆行移位
return [S[0], S[13], S[10], S[7],
S[4], S[1], S[14], S[11],
S[8], S[5], S[2], S[15],
S[12], S[9], S[6], S[3]]
def MixColumns(self, State):
# 列混合
return self.Matrix_Mul(self.MIX_C, State)
def MixColumns_Inv(self, State):
# 逆列混合
return self.Matrix_Mul(self.I_MIXC, State)
def RotWord(self, _4byte_block):
# 用于生成轮密钥的字移位
return ((_4byte_block & 0xffffff) << 8) + (_4byte_block >> 24)
def SubWord(self, _4byte_block):
# 用于生成密钥的字节替换
result = 0
for position in range(4):
i = _4byte_block >> position * 8 + 4 & 0xf
j = _4byte_block >> position * 8 & 0xf
result ^= self.S_BOX[i][j] << position * 8
return result
def mod(self, poly, mod=0b100011011):
# poly模多项式mod
while poly.bit_length() > 8:
poly ^= mod << poly.bit_length() - 9
return poly
def mul(self, poly1, poly2):
# 多项式相乘
result = 0
for index in range(poly2.bit_length()):
if poly2 & 1 << index:
result ^= poly1 << index
return result
def Matrix_Mul(self, M1, M2): # M1 = MIX_C M2 = State
# 用于列混合的矩阵相乘
M = [0] * 16
for row in range(4):
for col in range(4):
for Round in range(4):
M[row + col * 4] ^= self.mul(M1[row][Round], M2[Round + col * 4])
M[row + col * 4] = self.mod(M[row + col * 4])
return M
def round_key_generator(self, _16bytes_key):
# 轮密钥产生
w = [_16bytes_key >> 96,
_16bytes_key >> 64 & 0xFFFFFFFF,
_16bytes_key >> 32 & 0xFFFFFFFF,
_16bytes_key & 0xFFFFFFFF] + [0] * 40
for i in range(4, 44):
temp = w[i - 1]
if not i % 4:
temp = self.SubWord(self.RotWord(temp)) ^ self.RCon[i // 4 - 1]
w[i] = w[i - 4] ^ temp
return [self.num_2_16bytes(
sum([w[4 * i] << 96, w[4 * i + 1] << 64,
w[4 * i + 2] << 32, w[4 * i + 3]])
) for i in range(11)]
def AddRoundKey(self, State, RoundKeys, index):
# 异或轮密钥
return self._16bytes_xor(State, RoundKeys[index])
def _16bytes_xor(self, _16bytes_1, _16bytes_2):
return [_16bytes_1[i] ^ _16bytes_2[i] for i in range(16)]
def _16bytes2num(cls, _16bytes):
# 16字节转数字
return int.from_bytes(_16bytes, byteorder='big')
def num_2_16bytes(cls, num):
# 数字转16字节
return num.to_bytes(16, byteorder='big')
def aes_encrypt(self, plaintext_list, RoundKeys):
State = plaintext_list
State = self.AddRoundKey(State, RoundKeys, 0)
for Round in range(1, 10):
State = self.SubBytes(State)
State = self.ShiftRows(State)
State = self.MixColumns(State)
State = self.AddRoundKey(State, RoundKeys, Round)
State = self.SubBytes(State)
State = self.ShiftRows(State)
State = self.AddRoundKey(State, RoundKeys, 10)
return State
def aes_decrypt(self, ciphertext_list, RoundKeys):
State = ciphertext_list
State = self.AddRoundKey(State, RoundKeys, 10)
for Round in range(1, 10):
State = self.ShiftRows_Inv(State)
State = self.SubBytes_Inv(State)
State = self.AddRoundKey(State, RoundKeys, 10 - Round)
State = self.MixColumns_Inv(State)
State = self.ShiftRows_Inv(State)
State = self.SubBytes_Inv(State)
State = self.AddRoundKey(State, RoundKeys, 0)
return State
if __name__ == '__main__':
aes = AES()
key = 0x5359434C4F5645525359434C4F564552
RoundKeys = aes.round_key_generator(key)
# # 加密
# plaintext = 0x00112233445566778899aabbccddeeff
# # 0x00112233445566778899aabbccddeeff -> b'\x00\x11"3DUfw\x88\x99\xaa\xbb\xcc\xdd\xee\xff'
# plaintext = aes.num_2_16bytes(plaintext)
# ciphertext = aes.aes_encrypt(plaintext, RoundKeys)
# print('ciphertext = ' + hex(aes._16bytes2num(ciphertext)))
# 解密
for i in [0x99E8B801C882519312EE8964E7EF638D, 0x51DF5D7839AA3962A0B4503047302106]:
ciphertext = i
ciphertext = aes.num_2_16bytes(ciphertext)
plaintext = aes.aes_decrypt(ciphertext, RoundKeys)
print((bytes(plaintext).decode()), end='')
#SYC{B3l1eue_Th@t_y0u__l3aRn_Aes}
blasting_master
主加密程序
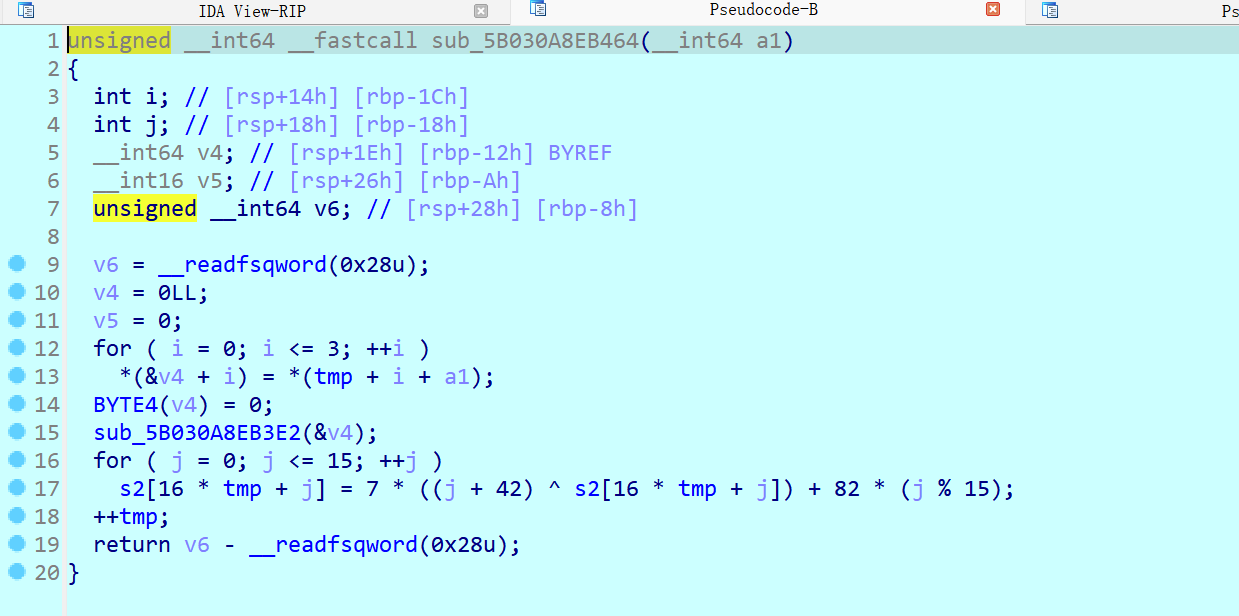
将输入md5加密后进行位运算,然后存到s2中
编写爆破脚本
from Crypto.Util.number import *
from hashlib import *
from string import *
enc = [0xB2, 0x50, 0xA0, 0xBC, 0x3A, 0x7F, 0x54, 0x6D, 0x96, 0x07,
0x0F, 0x71, 0x9A, 0x72, 0xEB, 0xA5, 0xA0, 0xB5, 0x71, 0xA4,
0x6A, 0xB8, 0xBA, 0xFA, 0xE4, 0x31, 0xC3, 0x71, 0x54, 0x29,
0xA7, 0x59, 0x20, 0x2B, 0x13, 0x21, 0xBD, 0x67, 0x5F, 0x8D,
0x65, 0x3A, 0x02, 0x27, 0x08, 0x4F, 0x92, 0x9C, 0xB5, 0x7C,
0xDF, 0x69, 0x34, 0xB8, 0x82, 0x2D, 0xF6, 0xCA, 0x7A, 0x65,
0x98, 0x63, 0xDC, 0x51, 0x2A, 0x34, 0x97, 0x4F, 0xF8, 0xBC,
0x23, 0x1F, 0x38, 0xA8, 0xA6, 0x2F, 0xA9, 0x0D, 0x64, 0x4C,
0xAC, 0x2F, 0xF9, 0xF5, 0x2D, 0xB1, 0x91, 0xA8, 0xD5, 0x76,
0xD9, 0x2D, 0xC6, 0xAC, 0x2E, 0x69, 0x32, 0xD5, 0x64, 0x1D,
0xC1, 0x3C, 0xEC, 0xF5, 0x2C, 0x90, 0xED, 0xF4, 0x17, 0x8B,
0x55, 0x4C, 0xE4, 0x6C, 0x3B, 0xB3, 0xDA, 0x29, 0xC0, 0x7B,
0x39, 0xDF, 0x92, 0x73, 0xFC, 0xC9, 0xC2, 0xA8, 0x68, 0x11,
0x22, 0x2B, 0x64, 0x3F, 0x12, 0x9B, 0x95, 0x73, 0x2A, 0x05,
0xD3, 0x3F, 0x2E, 0x33, 0xF1, 0x85, 0xED, 0x07, 0x7B, 0x86,
0x8F, 0x62, 0x2D, 0x79, 0x03, 0xAC, 0x80, 0xCE, 0xF5, 0xB2,
0xA0, 0x0C, 0xF7, 0xE1, 0xC5, 0x0E, 0x63, 0x27, 0xD1, 0x65,
0x23, 0xEA, 0x5A, 0x1C, 0x02, 0x0B, 0x32, 0xBA, 0x1F, 0xE5,
0xC7, 0x22, 0xA5, 0x66, 0x77, 0xEA, 0x5B, 0xE4, 0x64, 0xAB,
0x8B, 0x60, 0xB6, 0xDF, 0x00, 0xDC, 0xF7, 0x6D, 0x93, 0xEC,
0x2F, 0x2F, 0x68, 0x07, 0x50, 0xE0, 0xD1, 0x1A, 0x3F, 0xC6,
0x4E, 0x2E, 0xC6, 0xBB, 0xAE, 0x08, 0x40, 0xD8, 0x5B, 0x11,
0xB5, 0xDC, 0x15, 0x35, 0x7F, 0x63, 0x49, 0x3E, 0x5B, 0x9C,
0x0D, 0xFC, 0x0D, 0xB6, 0x80, 0xB7, 0x2B, 0x00, 0xEF, 0x3C,
0x0C, 0x2F, 0xEB, 0x86, 0x44, 0x57, 0x74, 0x9E, 0x5F, 0x1F,
0x8B, 0xA1, 0xC9, 0x01, 0xF1, 0xD8, 0xF4, 0x92, 0x82, 0x95,
0x6F, 0x85, 0xD2, 0x15, 0x22, 0x1F, 0xF0, 0x9F, 0xD1, 0xAB,
0x51, 0x39, 0x9A, 0xB6, 0xC4, 0xDA, 0xFB, 0x38, 0x8D, 0xE6,
0x8C, 0x57, 0x19, 0x5E, 0x94, 0xDA, 0x57, 0xCC, 0xF0, 0xB9,
0x0A, 0x4A, 0x17, 0x82, 0xFC, 0xC5, 0x4F, 0x4B, 0x5A, 0xA5,
0xF4, 0xE5, 0x3E, 0xFA, 0x3A, 0x0A, 0xF4, 0xB4, 0x8E, 0x7F,
0x25, 0x84, 0x75, 0x90, 0xCD, 0x35, 0x87, 0xEB, 0xC3, 0xCE,
0x81, 0x2B, 0x86, 0xC9, 0x16, 0x7E, 0x85, 0x68, 0x2D, 0xF1,
0xDB, 0x8E, 0x74, 0x15, 0xCF, 0x95, 0x51, 0x07, 0x88, 0x5E,
0x1B, 0xE9, 0x37, 0xC9, 0x5B, 0xBA, 0x61, 0xEB, 0x9F, 0x7B,
0xE4, 0x89, 0x10, 0xF0, 0x6E, 0xCD, 0x75, 0x71, 0xAD, 0x09,
0x74, 0x58, 0x49, 0xA3, 0xF5, 0x33, 0x83, 0x75, 0x22, 0x95,
0x1B, 0xE3, 0x3C, 0x48, 0x05, 0x5C, 0xAD, 0xA8, 0x6B, 0xFD,
0x41, 0xEB, 0xAF, 0xC6, 0x02, 0x28, 0xC6, 0x5E, 0xCF, 0x36,
0xAE, 0x50, 0xCE, 0x93, 0xF2, 0x70, 0x88, 0x9D, 0x3F, 0x4A,
0x9F, 0x86, 0xE7, 0x67, 0x64, 0xB0, 0x02, 0x96, 0x0C, 0xAB,
0x9F, 0xEB, 0x4B, 0x03, 0x44, 0x92, 0xDE, 0x6C, 0xF4, 0xCE,
0x32, 0x4F, 0x4F, 0x38, 0xE2, 0x52, 0x59, 0xCA, 0x95, 0x4A,
0x11, 0xD8, 0x30, 0xA2, 0x7B, 0xD5, 0x3A, 0xE6, 0x11, 0xDA,
0x3A, 0x4A, 0x33, 0x61, 0x39, 0x65, 0x26, 0xD2, 0x78, 0xBC,
0xED, 0xBD, 0xA5, 0x8B, 0x2B, 0x87, 0x4C, 0x95, 0x47, 0x25,
0x02, 0xBA, 0x83, 0x3D, 0xDC, 0xE4, 0x6A, 0xAD, 0x67, 0xDD,
0x22, 0xB1, 0xBD, 0x2B, 0x7C, 0x53, 0x11, 0x3C, 0xD9, 0x23,
0x06, 0x3D, 0x20, 0xBA, 0x28, 0xC8, 0x2D, 0x89, 0x51, 0x57,
0x63, 0x82, 0xA0, 0xC8, 0xA8, 0xDE, 0x29, 0x61, 0xC1, 0x53,
0x51, 0xB0, 0xBC, 0x37, 0x04, 0xEE, 0xC9, 0x35, 0x8A, 0xA8,
0xA2, 0x66, 0xBA, 0x6F, 0x24, 0xB6, 0x3F, 0x62, 0x41, 0x6D,
0x10, 0x46, 0xCB, 0x06, 0x12, 0x39, 0xD9, 0x0E, 0xF9, 0xDC,
0x19, 0xA7, 0x65, 0xB8, 0xC0, 0x40, 0xBE, 0xF6, 0x99, 0x9A,
0xAF, 0x02, 0x16, 0x37, 0x4D, 0xA5, 0x75, 0x4C, 0x42, 0x4B,
0x1A, 0xF0, 0x52, 0xDA, 0x38, 0xF3, 0x6B, 0xA9, 0x1A, 0xDC,
0xFA, 0x80, 0xB0, 0x60, 0xB1, 0xFD, 0x73, 0x7B, 0x78, 0xD9,
0x62, 0x83, 0x26, 0xBF, 0x16, 0x33, 0x71, 0x79, 0x6F, 0x11,
0x2F, 0xE9, 0xA7, 0xBB, 0x46, 0x46, 0xD6, 0x8F, 0xF6, 0x21,
0x7E, 0xFC, 0x68, 0x12, 0x86, 0x6B, 0xFC, 0x51, 0xC9, 0x70,
0x7A, 0x74, 0xBC, 0x8F, 0x6E, 0x0B, 0x86, 0x42, 0x6F, 0x5C,
0xFD, 0xF7, 0x4E, 0x27, 0x71, 0xFE, 0x37, 0xE6, 0xC8, 0x62,
0x47, 0xFC, 0xD5, 0x6C, 0xBA, 0x5C, 0xD9, 0x29, 0x5A, 0x73,
0xAE, 0xC3, 0x8F, 0xF0, 0x46, 0x95, 0x32, 0x42, 0x2D, 0xD0]
hash = []
flag = ''
for i in range(len(enc) // 16):
for j in range(16):
enc[16 * i + j] = (((enc[16 * i + j] - 82 * (j % 15)) * inverse(7, 256)) ^ (j + 42)) & 0xff
for i in range(0, len(enc), 16):
hash.append(bytes(enc[i:i+16]).hex())
for n in range(0, len(hash), 4): #我也不知道为什么,试出来的
tmp2 = hash[n]
for one in printable:
for two in printable:
for three in printable:
for four in printable:
tmp = one + two + three + four
if md5(tmp.encode()).hexdigest() == tmp2:
flag += tmp
print(flag)
break
else:
continue
break
else:
continue
break
else:
continue
break
#SYC{W0w!y0u_@re_th3_BeSt_blasting_Exp3rt
ez_hook
把反调试处退出程序跳转判断的jz改jnz
然后输入一个字符串后patch就行(这是个大部分是异或的加密),但中间有个什么字符串换位我没看懂,直接丢个有规律的字符串进去然后把换位规律打印出来就行
解密脚本:
enc = '}h_wnoYko_1th_0kuyCSOs@w_{'
flag = ''
origin_str = 'abcdefghijklmnopqrstuvwxyz'
replace_str = 'zvrnjfbywusqomkigecaxtplhd'
idx = []
for i in origin_str:
idx.append(replace_str.index(i)) #以上操作全是用来看是怎么移位的
for i in idx:
flag += enc[i]
print(flag)
#SYC{you_kn0w_wh@t_1s_hoOk}
致我的星星
给地图打通路
let data = [
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#'
];
let coordinates = [
[1, 11], [1, 12], [1, 13], [1, 14],
[2, 1], [2, 4], [2, 11], [2, 12], [2, 14],
[3, 4], [3, 14],
[5, 7], [5, 8], [5, 12], [5, 14], [5, 15], [5, 18],
[6, 1], [6, 2], [6, 4], [6, 5], [6, 7], [6, 8], [6, 11], [6, 15],
[7, 1], [7, 5], [7, 11], [7, 12], [7, 13], [7, 14], [7, 15], [7, 16],
[8, 1], [8, 12], [8, 13], [8, 15], [8, 18],
[9, 3], [9, 4], [9, 6], [9, 7], [9, 8]
];
let cols = 20;
let rows = 10;
coordinates.forEach(([row, col]) => {
const index = row * cols + col;
if (index >= 0 && index < data.length) {
data[index] = '*';
}
});
python实现
data = [
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#',
'#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#', '#'
]
coordinates = [
[1, 11], [1, 12], [1, 13], [1, 14],
[2, 1], [2, 4], [2, 11], [2, 12], [2, 14],
[3, 4], [3, 14],
[5, 7], [5, 8], [5, 12], [5, 14], [5, 15], [5, 18],
[6, 1], [6, 2], [6, 4], [6, 5], [6, 7], [6, 8], [6, 11], [6, 15],
[7, 1], [7, 5], [7, 11], [7, 12], [7, 13], [7, 14], [7, 15], [7, 16],
[8, 1], [8, 12], [8, 13], [8, 15], [8, 18],
[9, 3], [9, 4], [9, 6], [9, 7], [9, 8]
]
cols = 20 #列
rows = 10 #行
for row, col in coordinates:
index = row * cols + col
if 0 <= index < len(data):
data[index] = '*'
设置起点和终点(有两处)
let a1, a2,a3, a4, a5, a6, a7, a8;
43654*a1 - 57003*a2 -3158*a3 + 30120*a4 -58621*a5 -41947*a6 +122237*a7 +129534*a8 == 2594143;
-48022*a1 + 18308*a2 + 52478*a3 + 69397*a4 +49696*a5 + 12288*a6 -40437*a7 -23154*a8 == 651137;
124109*a1 +58952*a2 + 16645*a3 -17531*a4 + 53139*a5 +49937*a6 + 3282*a7 +7656*a8 == 2071815;
108286*a1 + 118886*a2 +116876*a3 +2281*a4 -64590*a5 -3021*a6 + 13386*a7 -56070*a8 == 703;
105983*a1 + 8794*a2 + 31851*a3 -35052*a4 -7880*a5 + 2183*a6 + 47575*a7 +107236*a8 == 2511919;
-38005*a1 -6833*a2 +107897*a3 +119771*a4 +124322*a5 + 13335*a6+ 121590*a7 -17434*a8 == 4816084;
60696*a1 +95253*a2 +101581*a3 + 93822*a4 +112989*a5 +65643*a6 +45639*a7 + 26705*a8 == 5330538;
49019*a1 +72343*a2 -21814*a3 +85020*a4 -62332*a5 +99828*a6 + 587*a7 -65119*a8 == 505173;
python解出
from z3 import *
a1, a2, a3, a4, a5, a6, a7, a8 = Ints('a1 a2 a3 a4 a5 a6 a7 a8')
s = Solver()
s.add(43654*a1 - 57003*a2 -3158*a3 + 30120*a4 -58621*a5 -41947*a6 +122237*a7 +129534*a8 == 2594143)
s.add(-48022*a1 + 18308*a2 + 52478*a3 + 69397*a4 +49696*a5 + 12288*a6 -40437*a7 -23154*a8 == 651137)
s.add(124109*a1 +58952*a2 + 16645*a3 -17531*a4 + 53139*a5 +49937*a6 + 3282*a7 +7656*a8 == 2071815)
s.add(108286*a1 + 118886*a2 +116876*a3 +2281*a4 -64590*a5 -3021*a6 + 13386*a7 -56070*a8 == 703)
s.add(105983*a1 + 8794*a2 + 31851*a3 -35052*a4 -7880*a5 + 2183*a6 + 47575*a7 +107236*a8 == 2511919)
s.add(-38005*a1 -6833*a2 +107897*a3 +119771*a4 +124322*a5 + 13335*a6+ 121590*a7 -17434*a8 == 4816084)
s.add(60696*a1 +95253*a2 +101581*a3 + 93822*a4 +112989*a5 +65643*a6 +45639*a7 + 26705*a8 == 5330538)
s.add(49019*a1 +72343*a2 -21814*a3 +85020*a4 -62332*a5 +99828*a6 + 587*a7 -65119*a8 == 505173)
if s.check() == sat:
print(s.model())
# [a3 = 6,
# a4 = 8,
# a5 = 13,
# a1 = 3,
# a8 = 15,
# a2 = 4,
# a6 = 13,
# a7 = 15]
剩下的部分就是走迷宫了
注意迷宫走了两次(分为上下两个部分),用chance控制
bfs脚本
from collections import deque
maze = [['#', '#', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '*', '*', '*', '*', '#', '#', '#', '#', '#'],
['#', '*', '#', '#', '*', '#', '#', '#', '#', '#'],
['#', '*', 'S', '#', '*', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '*', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', 'Y', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '#', '#', '#', '#', '#', '#', '*', '*', '#'],
['#', '#', '*', '#', '*', '*', '#', '#', '*', '#'],
['#', '*', '*', '#', '*', '*', '#', '*', '*', '#'],
['#', '*', '#', '#', '#', '*', '#', '#', '#', '#'],
['#', '*', '#', '#', '#', '*', '#', '#', '#', '#'],
['#', '*', '*', '*', '*', '*', '*', '#', '#', '#'],
['#', '*', '#', '#', '#', '#', '#', '#', '#', '#'],
['#', '#', '*', '*', '#', '*', '#', '#', '*', '#'],]
directions = {
'T' : (-1, 0),
"S" : (0, -1),
"R" : (1, 0),
"A" : (0, 1)
}
def bfs(maze):
start = None
end = None
# 找到起点(3)和终点(2)
for i in range(len(maze)):
for j in range(len(maze[0])):
if maze[i][j] == 'S':
start = (i, j)
elif maze[i][j] == 'Y':
end = (i, j)
path_list = deque([(start, [])]) #用来储存坐标和路径
visited = set() #保存访问过的坐标
visited.add(start)
while path_list:
(x, y), path = path_list.popleft()
if (x, y) == end:
return path
for direction, (dx, dy) in directions.items():
nx, ny = x + dx, y + dy #下一个坐标
if 0 <= nx < len(maze) and 0 <= ny < len(maze[0]) and (nx, ny) not in visited and maze[nx][ny] != '#':
visited.add((nx, ny))
path_list.append(((nx, ny), path + [direction]))
return "no way"
path = bfs(maze)
print(''.join(path))
第一次 AAATTTTS
第二次 STTAAARRRR
SYC{AAATTTTSSTTAAARRRR}
LinkedListModular
你干嘛~~
贝斯!贝斯!
一个base58,一个base85
先用时间戳当随机数种子换了base58表
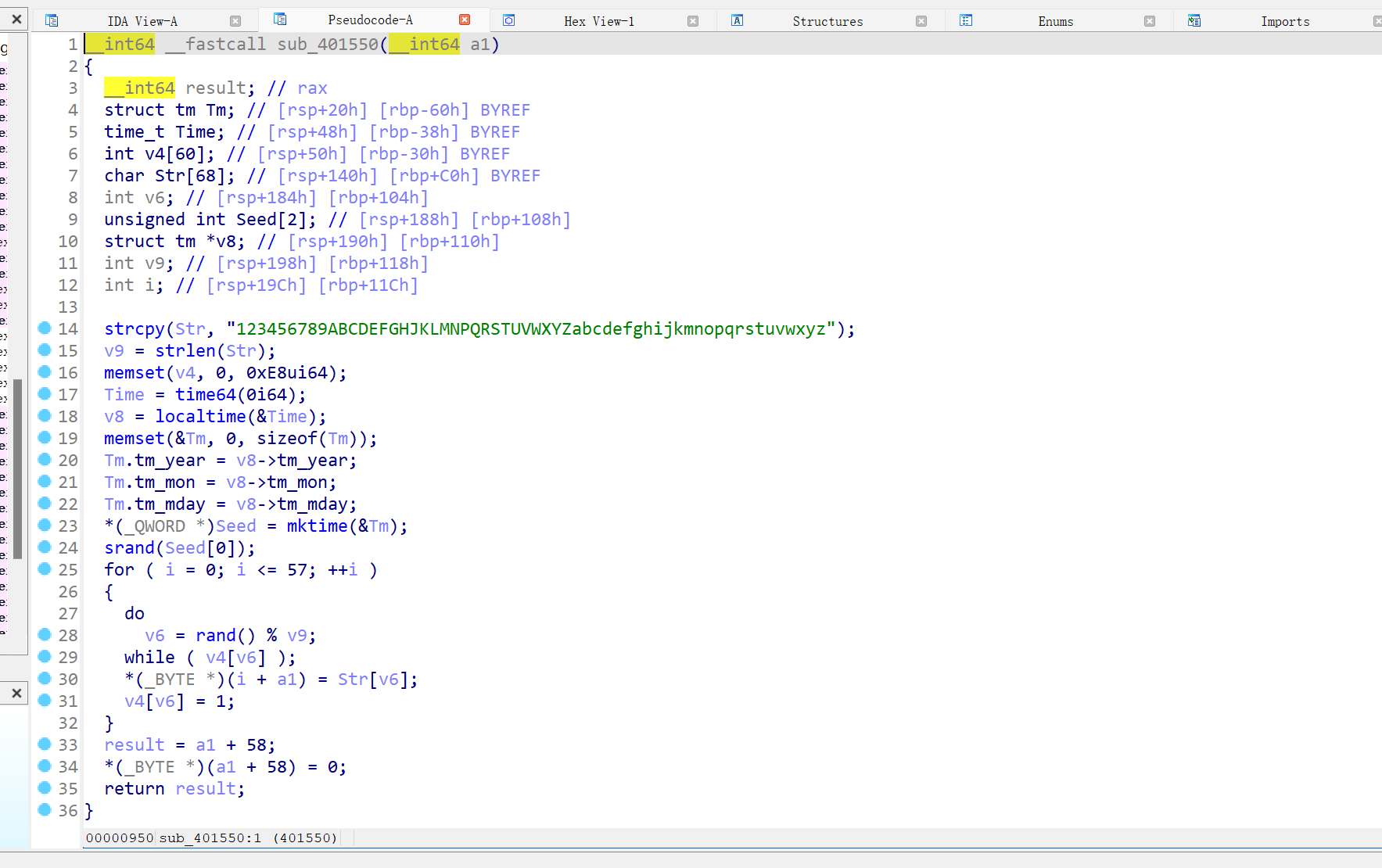
再进行了base58加密,然后用rc4的伪随机数生成换了base85的表(这个表的值可以动调得出来)
Base85_table:eM+wr=x8aYZ/[zU$yRB&kbO;%p0P5f*7d(n]1Eug4ojc62AC,v39!h-^qQ.G?s)i:DFlS<>#@HINJTmtKLVWX
b85解码:
table = "eM+wr=x8aYZ/[zU$yRB&kbO;%p0P5f*7d(n]1Eug4ojc62AC,v39!h-^qQ.G?s)i:DFlS<>#@HINJTmtKLVWX"
def base85_decode(data):
decoded_data = b""
padding = 0
remainder = len(data) % 5
# 添加填充字符
if remainder != 0:
padding = 5 - remainder
data += table[0] * padding
# 将每5个字符解码为4个字节
for i in range(0, len(data), 5):
value = 0
for j in range(5):
value = value * 85 + table.index(data[i + j])
decoded_value = value.to_bytes(4, byteorder='big')
decoded_data += decoded_value
# 移除填充字节
if remainder != 0:
decoded_data = decoded_data[:-padding]
return decoded_data
encoded_data = 'RjB6Myu#,>Bgoq&u.H(nBgdIaOKJbgEYj1GR4S.w'
decoded_data = base85_decode(encoded_data)
print("解码后:", decoded_data.decode())
#6pmB34FC9sbYxcKP9rjGGiyRsx1s6c72
从一月一号(1704038400)开始爆破表,一直爆到十一月中旬(1731600000),每天间隔86400秒,将结果输入output.txt
#include <iostream>
#include <cstdlib>
#include <string>
#include <fstream>
using namespace std;
int main() {
int v6, i, k;
string str = "123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz";
size_t str_len = str.length();
ofstream outfile("../output.txt");
for (k = 1704038400; k <= 1731600000; k += 86400) {
srand(k);
char table[68] = {0};
int v4[60] = {0};
for (i = 0; i <= 57; ++i) {
do
v6 = rand() % str_len;
while (v4[v6]);
table[i] = str[v6];
v4[v6] = 1;
}
outfile << k << ", " << table << "\n";
}
outfile.close();
return 0;
}
爆破
import base58
f = open(r'D:\c_code\output.txt').readlines()
for line in f:
now = line.strip().split(', ')
time = int(now[0])
table = now[1]
m = base58.b58decode(b'6pmB34FC9sbYxcKP9rjGGiyRsx1s6c72', alphabet=table.encode())
if b'SYC{' in m or b'flag{' in m:
print(time, table, m)
看了GeekChallenge2024 第十五届极客大挑战 | Lazzaro此处wp才做出来了,最开始根本没想到用时间戳爆破



