newstar2024 reverse (部分)
Newstar 2024 --Reverse
base64
无壳
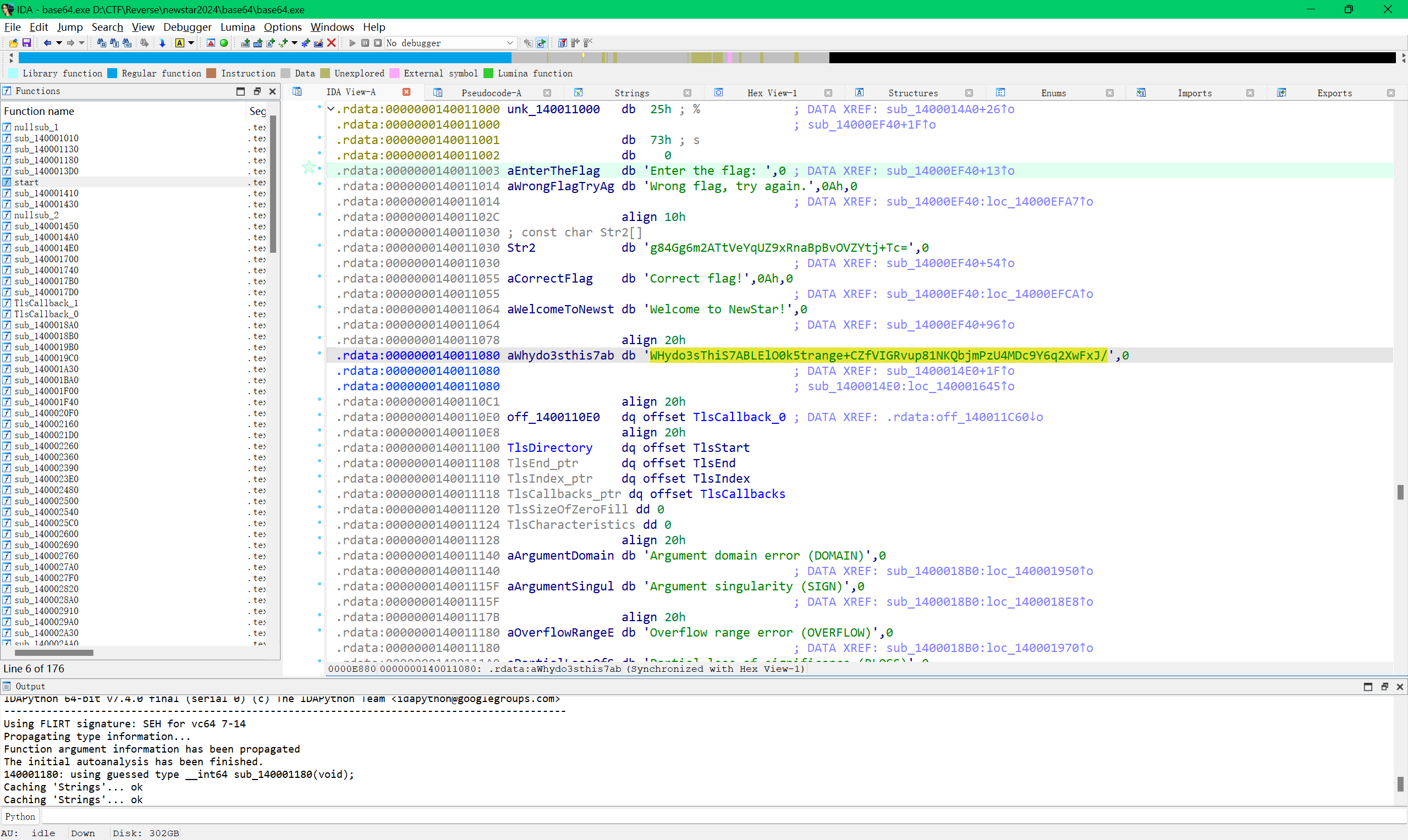
shift f12查找字符串
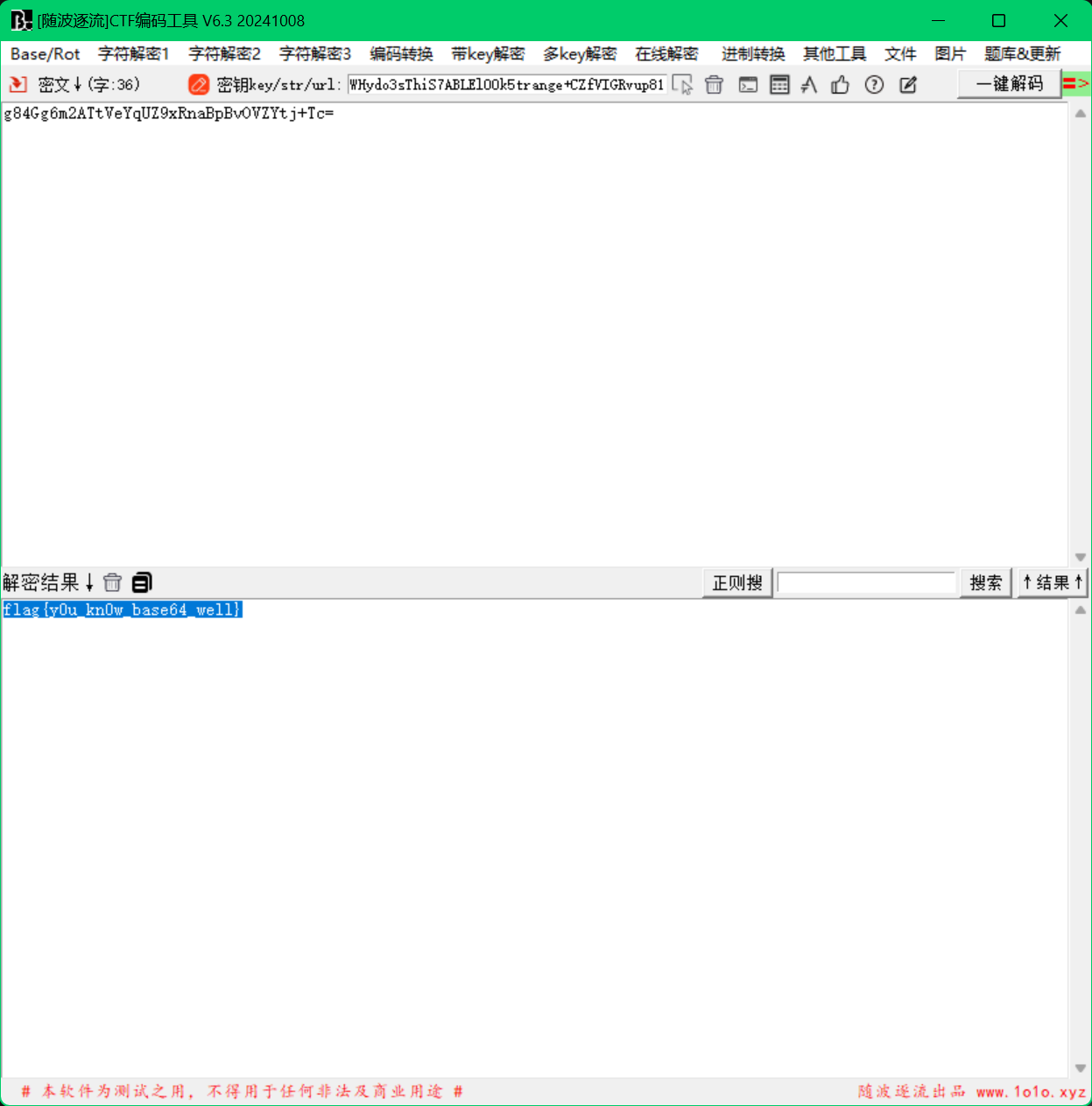
换表的base64加密
Simple_encryption
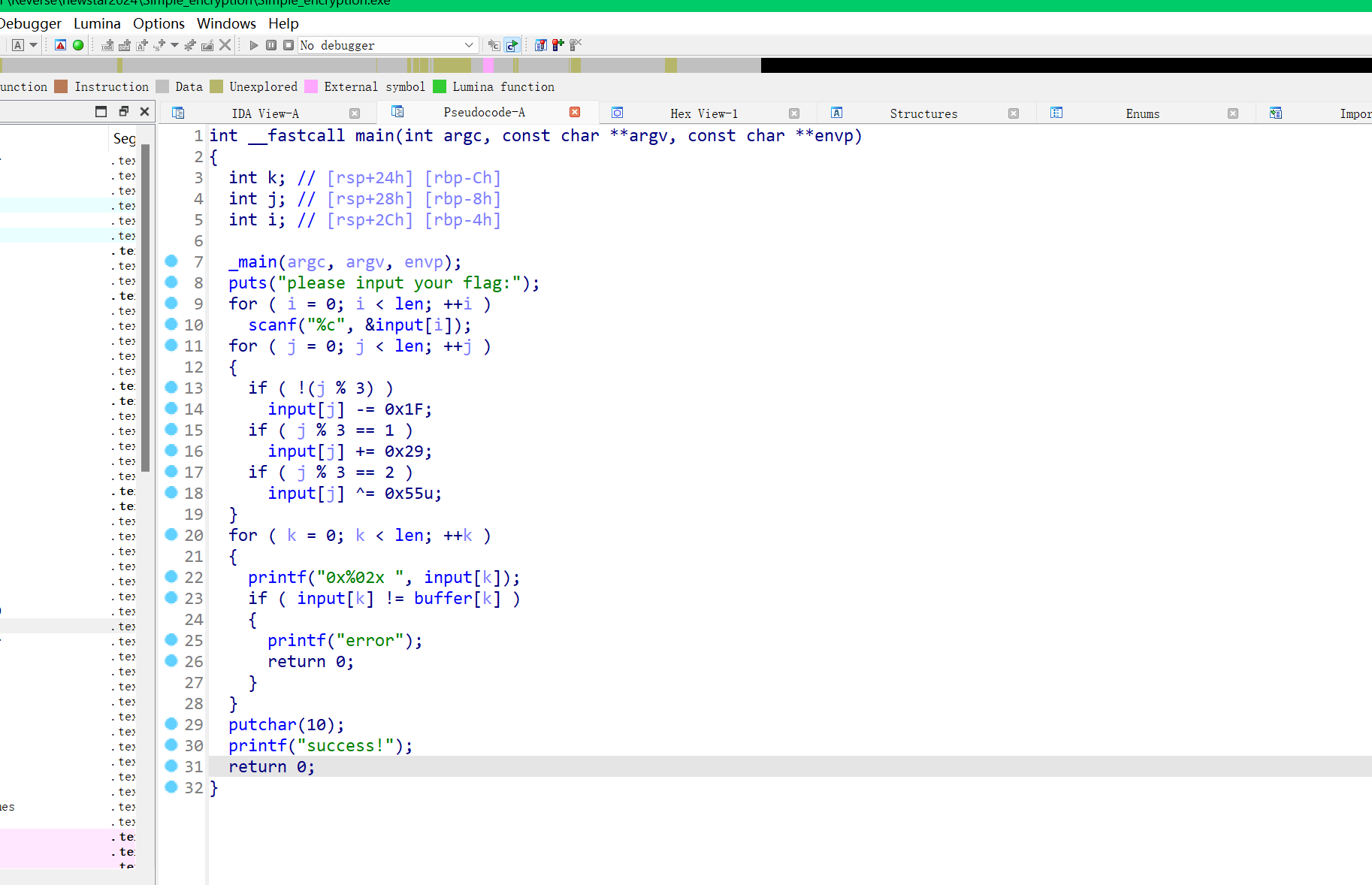
打开主函数
直接查看buffer,逆向破解
enc = [0x47, 0x95, 0x34, 0x48, 0xA4, 0x1C, 0x35, 0x88, 0x64, 0x16,
0x88, 0x07, 0x14, 0x6A, 0x39, 0x12, 0xA2, 0x0A, 0x37, 0x5C,
0x07, 0x5A, 0x56, 0x60, 0x12, 0x76, 0x25, 0x12, 0x8E, 0x28]
for i in range(len(enc)):
if i % 3 == 1:
enc[i] -= 0x29
elif i % 3 == 2:
enc[i] ^= 0x55
else:
enc[i] += 0x1f
print(chr((enc[i]) & 0xff), end='')
ezAndroidStudy
很好的萌新题,可以看官解
begin
跟着题解走
ezencode
用jadx打开软件
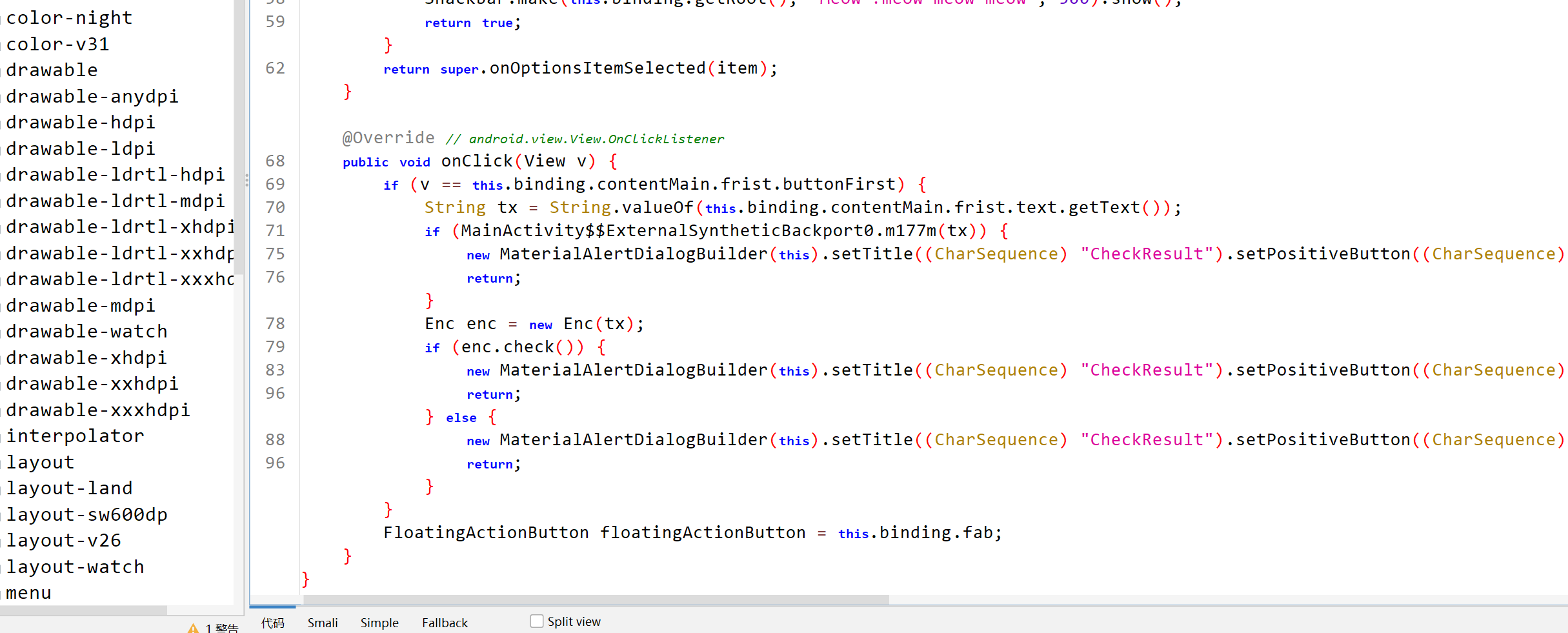
找到mainactivity加密函数部分
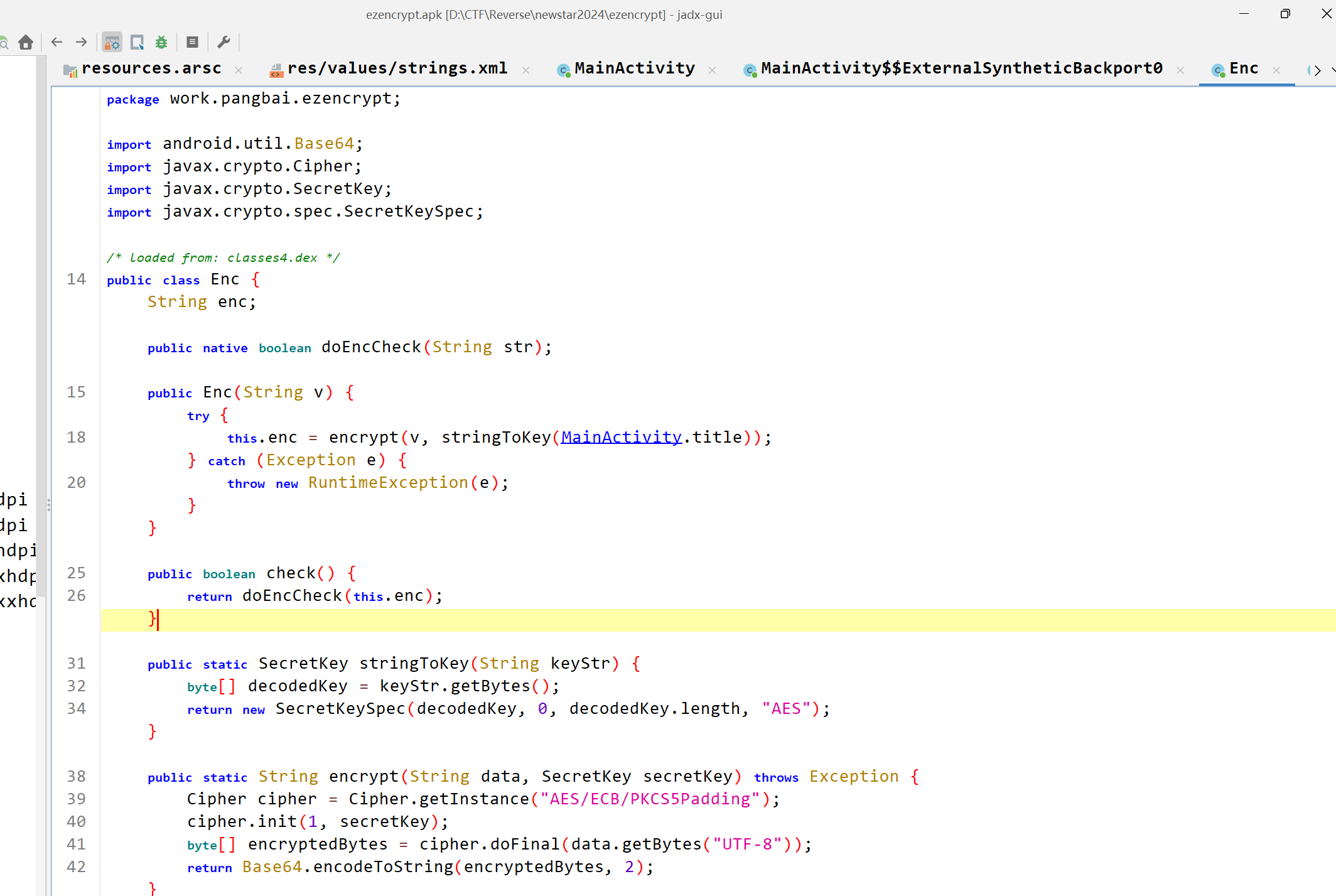
点进enc,可以看到是个aes加密
key就是title,但不知道密文在哪里
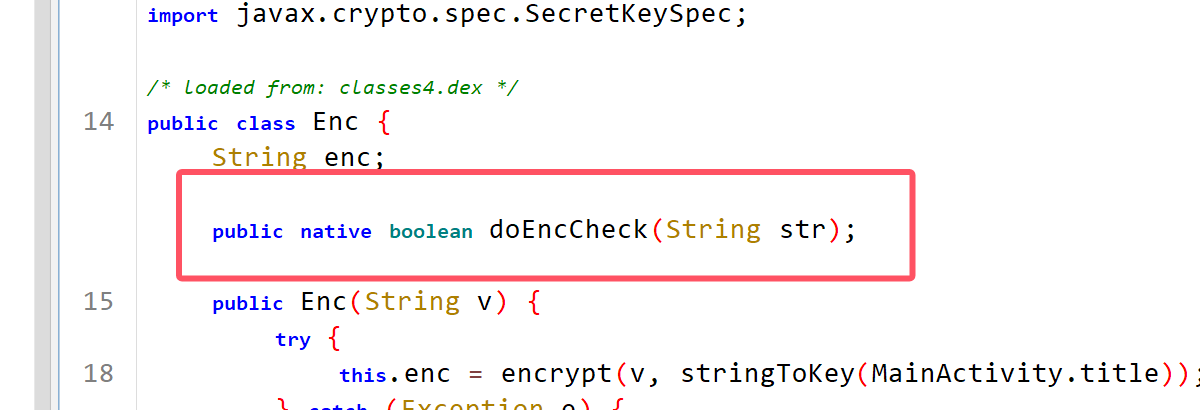
追踪函数变量即可看到密文是在so文件中(看native)
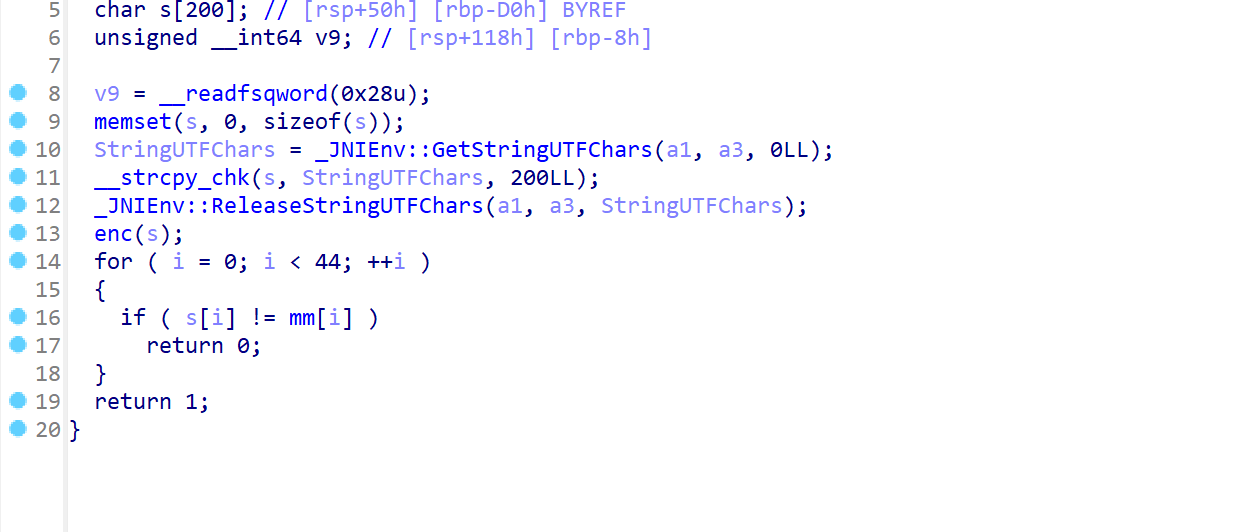
ida打开so文件
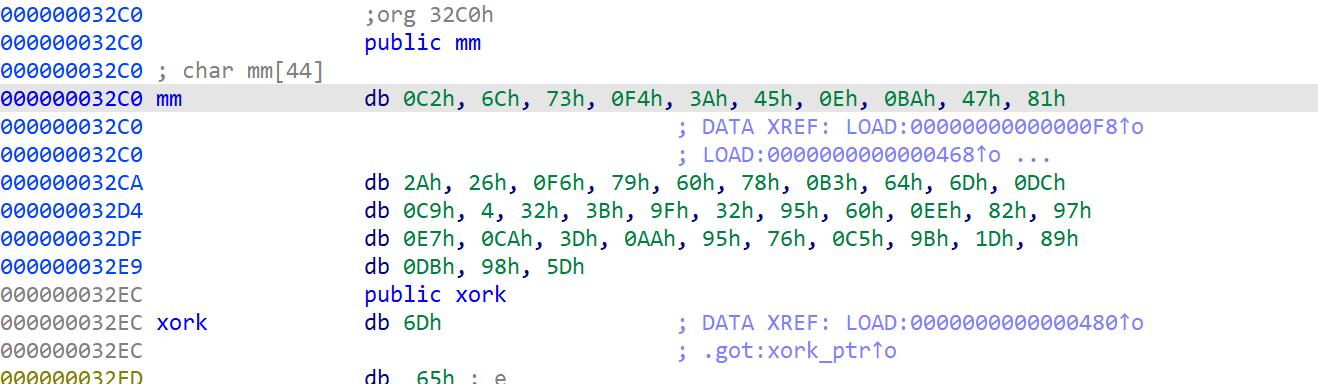
看到密文
但还有加密
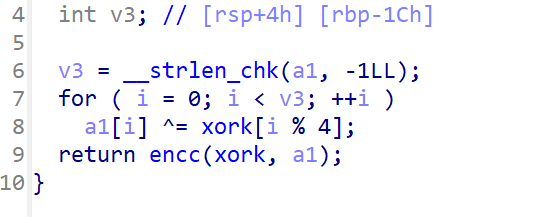
一个异或
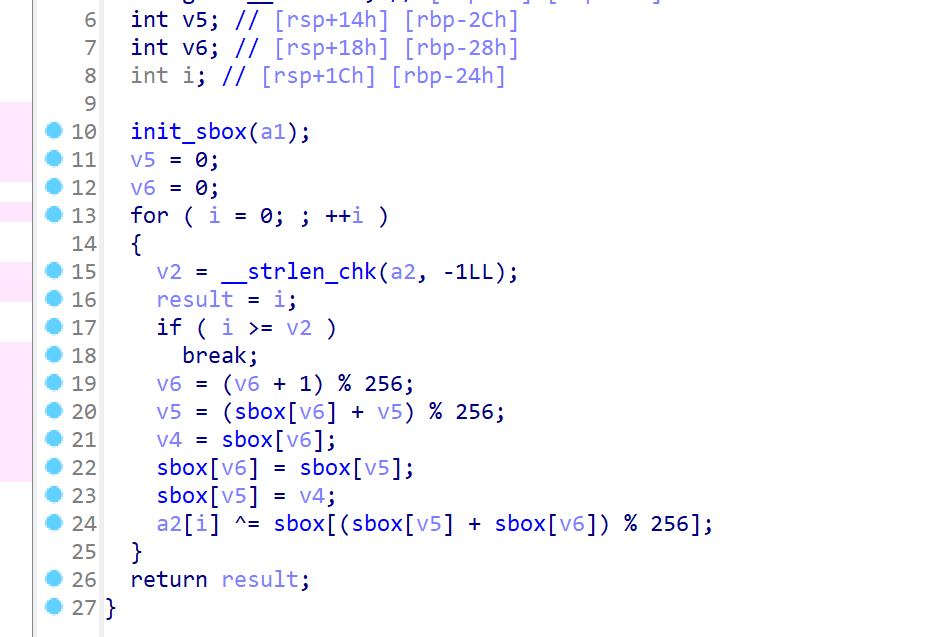
一个rc4
解密脚本:
from base64 import *
enc = [0xC2, 0x6C, 0x73, 0xF4, 0x3A, 0x45, 0x0E, 0xBA, 0x47, 0x81,
0x2A, 0x26, 0xF6, 0x79, 0x60, 0x78, 0xB3, 0x64, 0x6D, 0xDC,
0xC9, 0x04, 0x32, 0x3B, 0x9F, 0x32, 0x95, 0x60, 0xEE, 0x82,
0x97, 0xE7, 0xCA, 0x3D, 0xAA, 0x95, 0x76, 0xC5, 0x9B, 0x1D,
0x89, 0xDB, 0x98, 0x5D]
key = [0x6D, 0x65, 0x6F, 0x77]
result = ''
def KSA(key):
S = list(range(256))
j = 0
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
return S
def PRGA(S):
i, j = 0, 0
while True:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
yield K
def RC4Decrypt(key, text):
S = KSA(key)
keystream = PRGA(S)
res = []
for char in text:
res.append(char ^ next(keystream))
return bytes(res)
enc2 = RC4Decrypt(bytes(key), bytes(enc))
for i in range(len(enc)):
result+=chr(((enc2[i] ^ key[i % 4]) & 0xff))
print(result)
#2BB+GQampKmsrfDG85+0A7n18M+kT2zBDiZSO28Ich4=
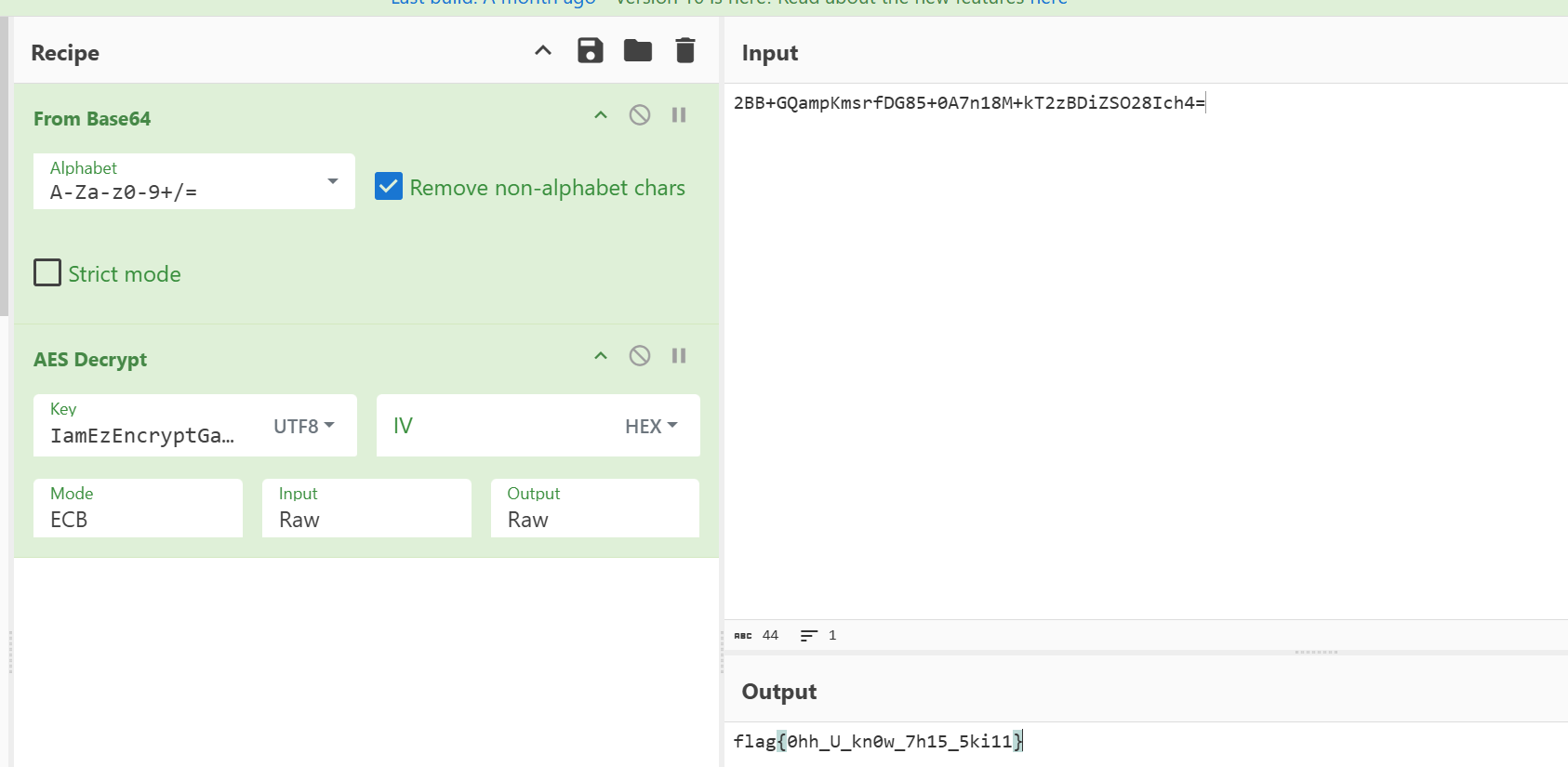
drink_tea
from ctypes import *
from Crypto.Util import *
key = [0x636C6557, 0x54656D6F, 0x77654E6F, 0x72617453]
enc = [0x0B3F72078, 0x0DACE42C5, 0x1A215985, 0x595A5626, 0x0ED0D0229, 0x0EEB9A807, 0x87115936, 0x24235CFD]
for i in range(0, len(enc), 2):
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i + 1])
delta = 0x61C88647
sum = c_uint32(-delta * 32)
r = 32
for j in range(r):
v1.value -= (sum.value + v0.value) ^ (key[2] + 16 * v0.value) ^ (key[3] + (v0.value >> 5))
v0.value -= (sum.value + v1.value) ^ (key[0] + 16 * v1.value) ^ (key[1] + (v1.value >> 5))
sum.value += delta
enc[i] = v0.value
enc[i + 1] = v1.value
print(number.long_to_bytes(enc[i]).decode()[::-1],end="")
print(number.long_to_bytes(enc[i+1]).decode()[::-1],end="")
PangBai 泰拉记(1)
动调可以发现key在异或前就被修改了
X跟进程序
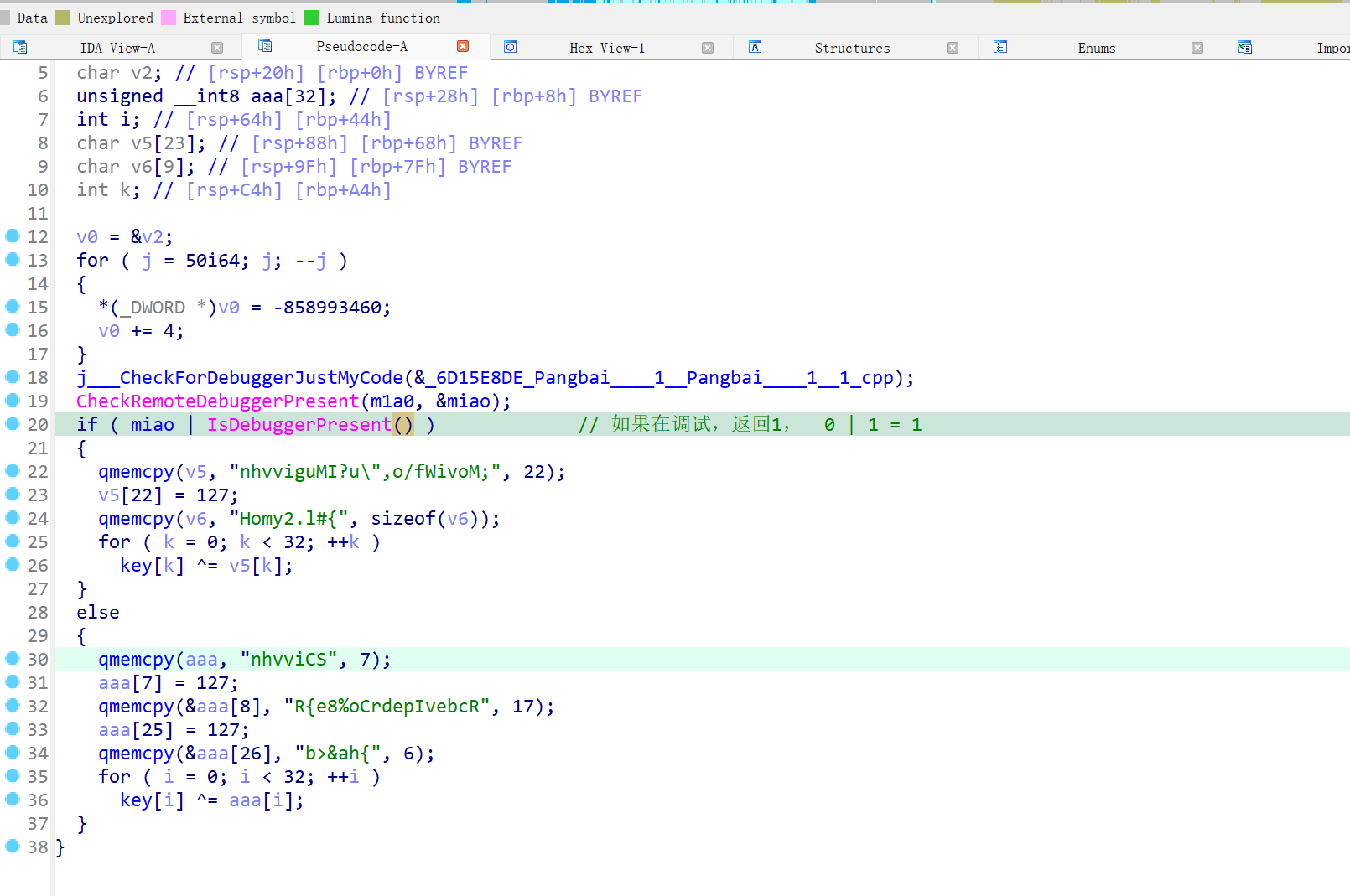
找到如下内容
法一:改jz
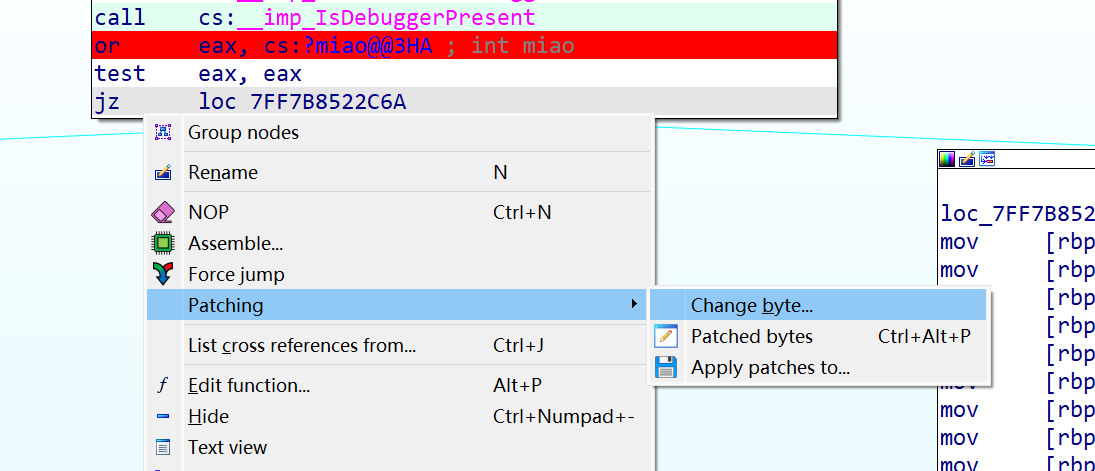
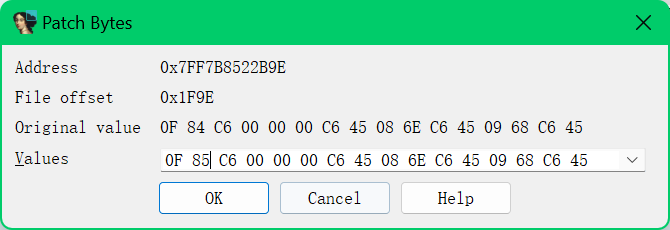
把84改85
改为jnz
011vm
去除控制流平坦化
点进其中的加密函数中的加密函数
看到tea加密,动调查看里面的值,可以发现是上一个函数中的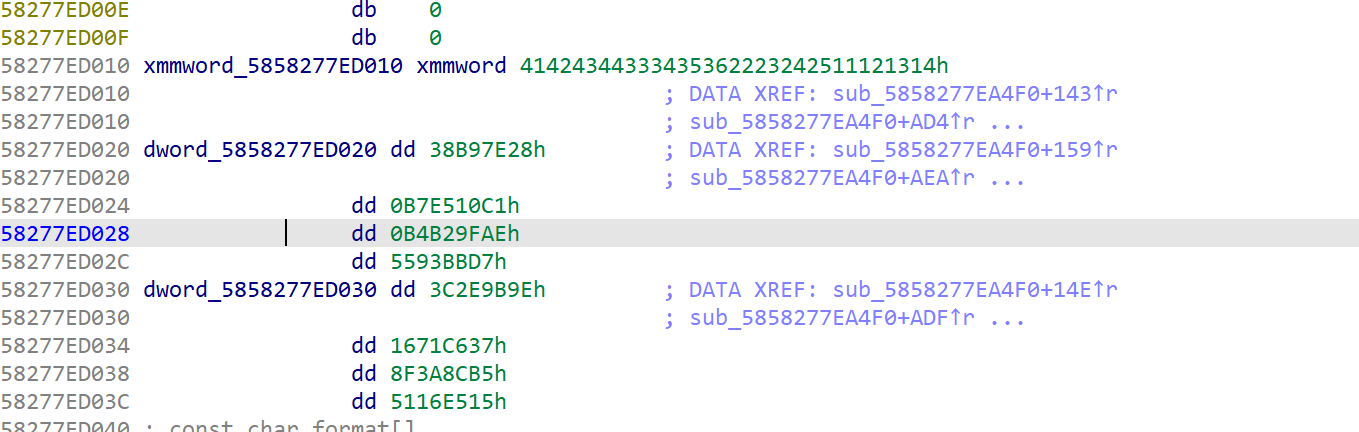
上面的是key,下面的密文(猜的,密文长度与输入一样,key是动调看内存知道的)
尝试解密
from ctypes import *
from Crypto.Util import *
key = [0x11121314, 0x22232425, 0x33343536, 0x41424344]
enc = [0x38B97E28, 0x0B7E510C1, 0x0B4B29FAE, 0x5593BBD7, 0x3C2E9B9E, 0x1671C637, 0x8F3A8CB5, 0x5116E515]
for i in range(0, len(enc), 2):
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i + 1])
delta = 0x9E3779B9
sum = c_uint32(delta * 32)
r = 32
for j in range(r):
v1.value -= (sum.value + v0.value) ^ (key[2] + 16 * v0.value) ^ (key[3] + (v0.value >> 5))
v0.value -= (sum.value + v1.value) ^ (key[0] + 16 * v1.value) ^ (key[1] + (v1.value >> 5))
sum.value -= delta
enc[i] = v0.value
enc[i + 1] = v1.value
print(number.long_to_bytes(enc[i]).decode()[::-1], end="")
print(number.long_to_bytes(enc[i+1]).decode()[::-1], end="")
#flag{011vm_1s_eZ_But_C0MP1EX_!!}



