[Moectf2024 Xor(大嘘)]
[Moectf2024 Xor(大嘘)]
进入主函数
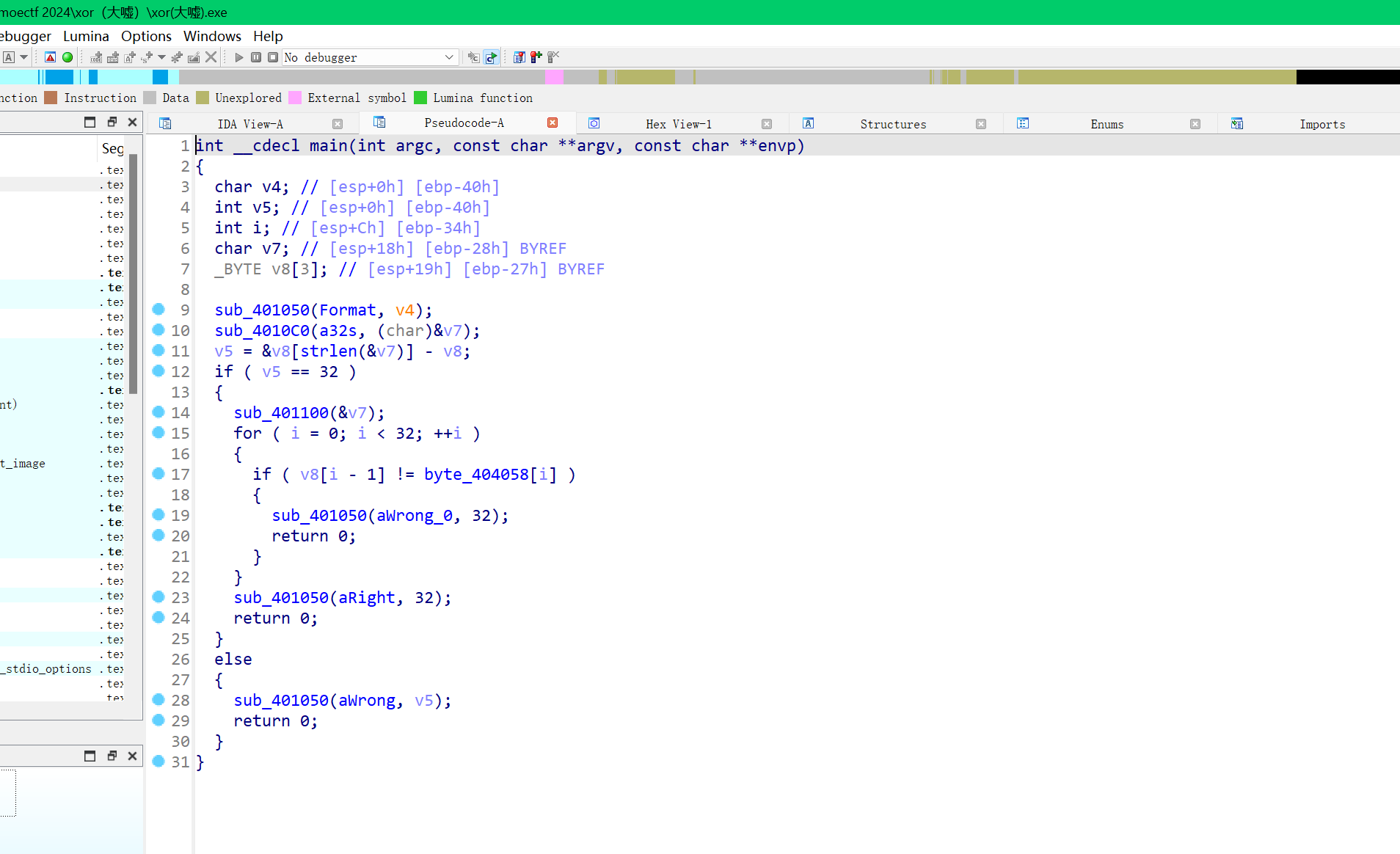
输入32长度的字节
sub_401100(&v7);进行加密
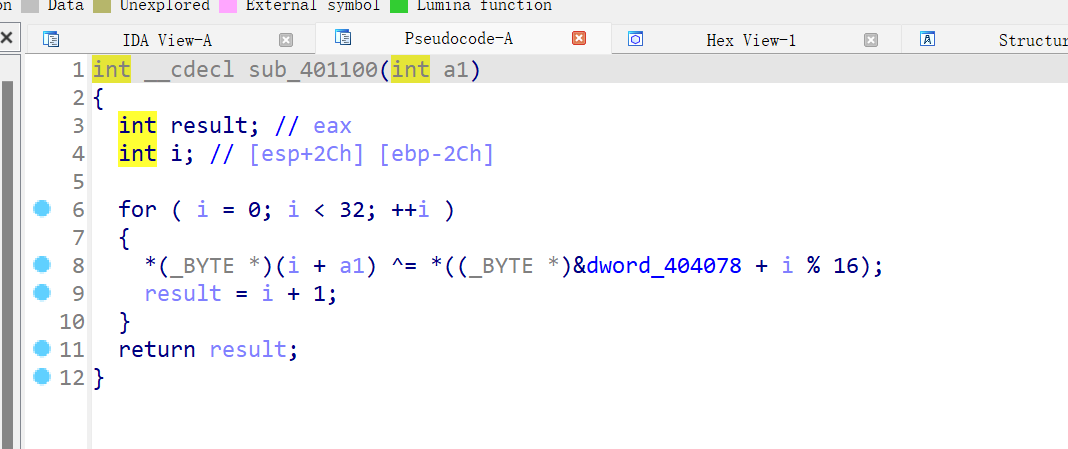
byte_404058是加密后的密文
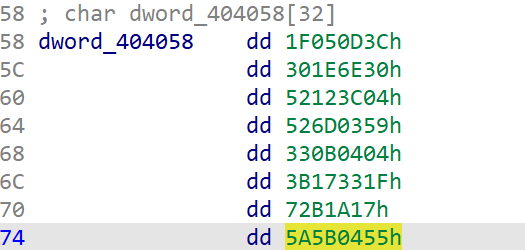
转dword
sub_401100的加密看似很简单,但其实是错的,动态调试后就会发现到return后会跳到别的函数,追到return处的汇编就会发现有花指令
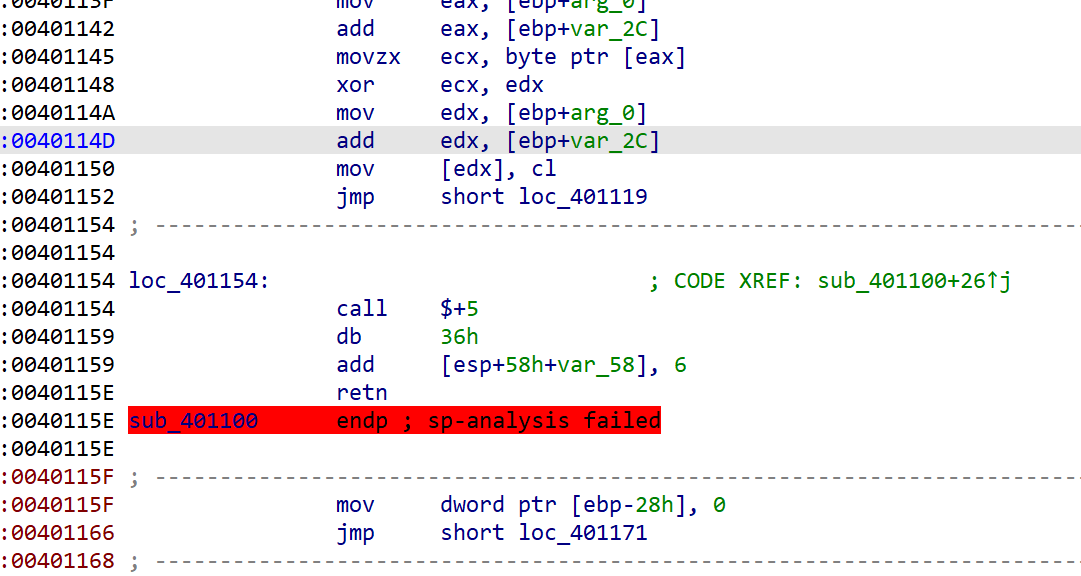
这里莫名其妙就retn了,nop掉
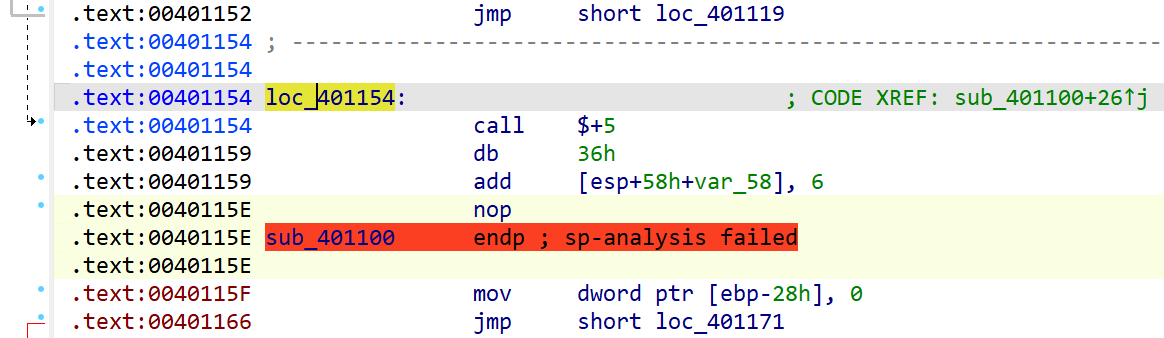
对loc_401154按u后p重新分析
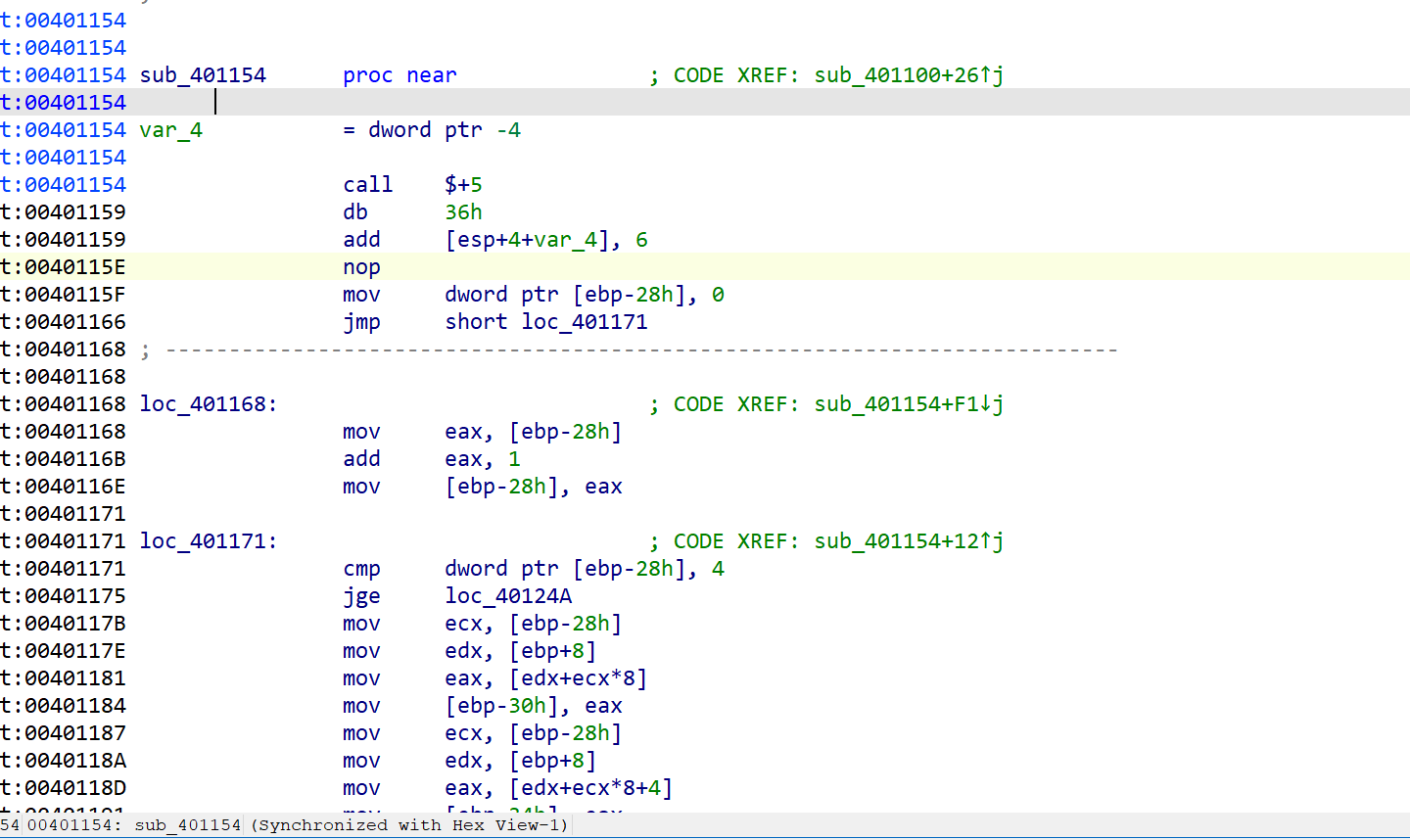
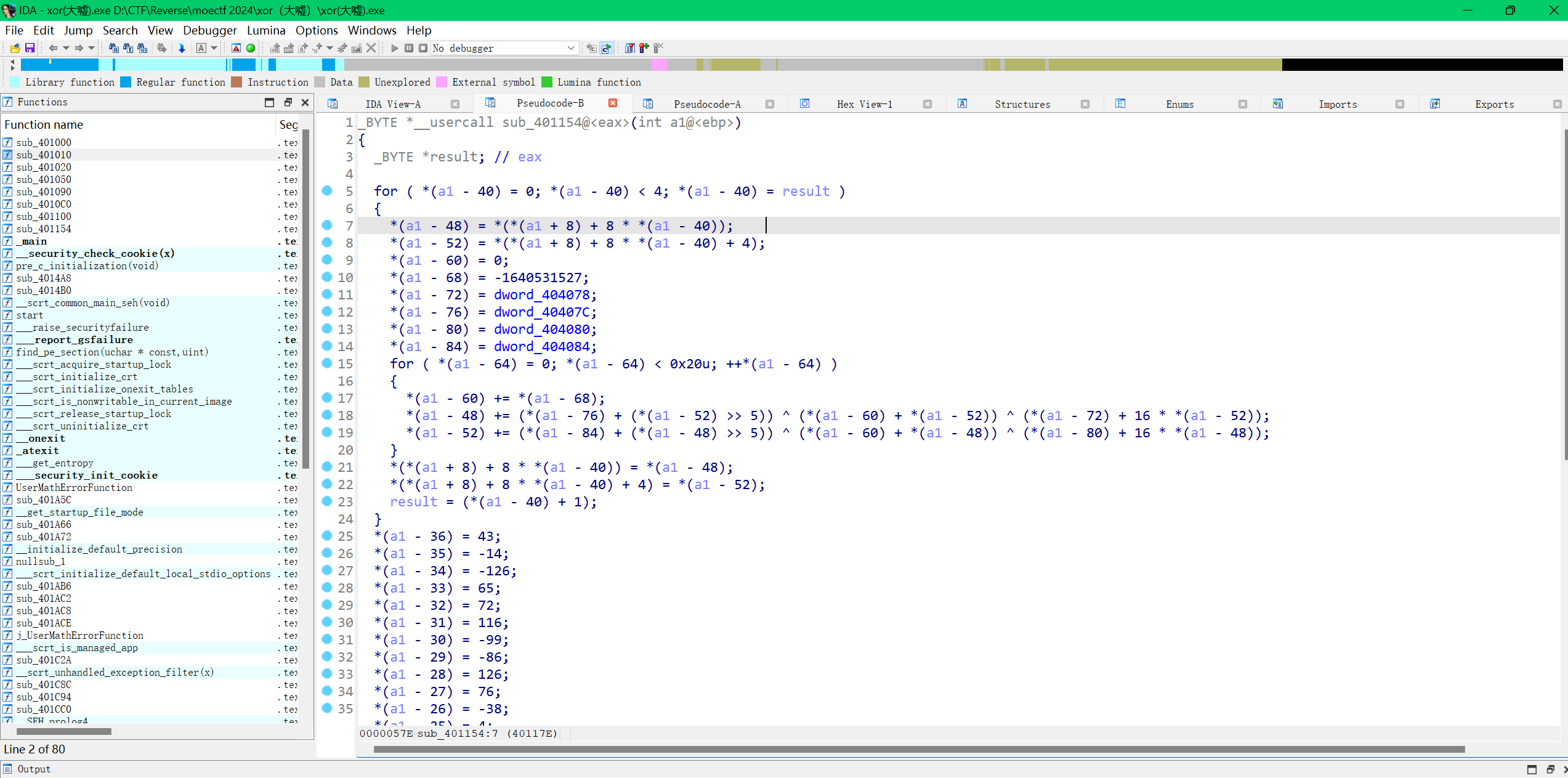
大概流程就是一个魔改delta的tea加密和一个异或,都是对dword进行操作,猜测a1的低地址处都是储存的各种变量,高地址处储存的是input(我们的输入)
解密后再进行一次异或加密
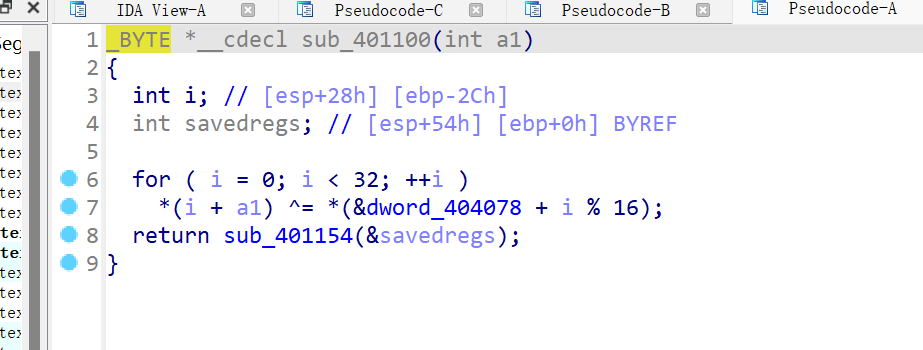
写出解密脚本:
from struct import *
from ctypes import *
key1 = [
0x2B, 0xF2, 0x82, 0x41, 0x48, 0x74, 0x9D, 0xAA, 0x7E, 0x4C,
0xDA, 0x04, 0x08, 0x2C, 0xA8, 0x52, 0x97, 0x77, 0xB7, 0x3B,
0x16, 0x2D, 0xD4, 0xFC, 0x60, 0xBE, 0xC4, 0xB6, 0x73, 0x19,
0x94, 0x87]
key = [0x6C6C6568, 0x6F6D5F6F, 0x66746365, 0x34323032]
enc = [0x1F050D3C, 0x301E6E30, 0x52123C04, 0x526D0359, 0x330B0404, 0x3B17331F, 0x72B1A17, 0x5A5B0455]
enc = list(b''.join(pack('<I', i) for i in enc))
for i in range(len(enc)):
enc[i] ^= key1[i]
enc = [unpack('<I', bytes(enc[i:i + 4]))[0] for i in range(0, len(enc), 4)]
for i in range(0, len(enc), 2):
v0 = c_uint32(enc[i])
v1 = c_uint32(enc[i + 1])
delta = 0x9E3779B9
sum = c_uint32(delta * 32)
r = 32
for j in range(r):
v1.value -= (sum.value + v0.value) ^ (key[2] + 16 * v0.value) ^ (key[3] + (v0.value >> 5))
v0.value -= (sum.value + v1.value) ^ (key[0] + 16 * v1.value) ^ (key[1] + (v1.value >> 5))
sum.value -= delta
enc[i] = v0.value
enc[i + 1] = v1.value
enc = list(b''.join(pack('<I', i) for i in enc))
key = list(b''.join(pack('<I', i) for i in key))
for i in range(len(enc)):
enc[i] ^= key[i % 16]
for i in enc:
print(chr(i), end='')



