[FlareOn6]Overlong
[FlareOn6]Overlong
查壳
win32无壳
分析程序
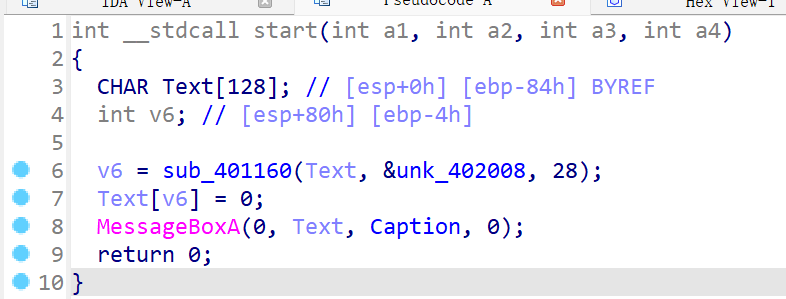
整个程序表面很简单,只是对unk_402008进行一个加密然后输出
点进加密程序,并没有发现什么端倪,也没有if比较之类的
直接运行程序看看
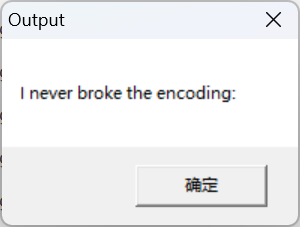
可以看到明显是输出被隐藏了
查看unk_402008内存,发现特别大,根本不止28,疑似是更改了加密长度
这个加密比较短可以直接把脚本复制过来搞
#include <iostream>
using namespace std;
int __cdecl sub_EF1000(unsigned __int8* a1, char* a2)
{
int v3; // [esp+0h] [ebp-8h]
unsigned __int8 v4; // [esp+4h] [ebp-4h]
if ((int)(unsigned __int8)*a2 >> 3 == 30)
{
v4 = a2[3] & 0x3F | ((a2[2] & 0x3F) << 6);
v3 = 4;
}
else if ((int)(unsigned __int8)*a2 >> 4 == 14)
{
v4 = a2[2] & 0x3F | ((a2[1] & 0x3F) << 6);
v3 = 3;
}
else if ((int)(unsigned __int8)*a2 >> 5 == 6)
{
v4 = a2[1] & 0x3F | ((*a2 & 0x1F) << 6);
v3 = 2;
}
else
{
v4 = *a2;
v3 = 1;
}
*a1 = v4;
return v3;
}
unsigned int __cdecl sub_EF1160(char* a1, char* a2, unsigned int a3)
{
unsigned int i; // [esp+4h] [ebp-4h]
for (i = 0; i < a3; ++i)
{
a2 += sub_EF1000((unsigned __int8*)a1, a2);
if (!*a1++)
break;
}
return i;
}
int main() {
char Text[128];
unsigned int v6;
char byte_EF2008[] =
{
0xE0, 0x81, 0x89, 0xC0, 0xA0, 0xC1, 0xAE, 0xE0, 0x81, 0xA5,
0xC1, 0xB6, 0xF0, 0x80, 0x81, 0xA5, 0xE0, 0x81, 0xB2, 0xF0,
0x80, 0x80, 0xA0, 0xE0, 0x81, 0xA2, 0x72, 0x6F, 0xC1, 0xAB,
0x65, 0xE0, 0x80, 0xA0, 0xE0, 0x81, 0xB4, 0xE0, 0x81, 0xA8,
0xC1, 0xA5, 0x20, 0xC1, 0xA5, 0xE0, 0x81, 0xAE, 0x63, 0xC1,
0xAF, 0xE0, 0x81, 0xA4, 0xF0, 0x80, 0x81, 0xA9, 0x6E, 0xC1,
0xA7, 0xC0, 0xBA, 0x20, 0x49, 0xF0, 0x80, 0x81, 0x9F, 0xC1,
0xA1, 0xC1, 0x9F, 0xC1, 0x8D, 0xE0, 0x81, 0x9F, 0xC1, 0xB4,
0xF0, 0x80, 0x81, 0x9F, 0xF0, 0x80, 0x81, 0xA8, 0xC1, 0x9F,
0xF0, 0x80, 0x81, 0xA5, 0xE0, 0x81, 0x9F, 0xC1, 0xA5, 0xE0,
0x81, 0x9F, 0xF0, 0x80, 0x81, 0xAE, 0xC1, 0x9F, 0xF0, 0x80,
0x81, 0x83, 0xC1, 0x9F, 0xE0, 0x81, 0xAF, 0xE0, 0x81, 0x9F,
0xC1, 0x84, 0x5F, 0xE0, 0x81, 0xA9, 0xF0, 0x80, 0x81, 0x9F,
0x6E, 0xE0, 0x81, 0x9F, 0xE0, 0x81, 0xA7, 0xE0, 0x81, 0x80,
0xF0, 0x80, 0x81, 0xA6, 0xF0, 0x80, 0x81, 0xAC, 0xE0, 0x81,
0xA1, 0xC1, 0xB2, 0xC1, 0xA5, 0xF0, 0x80, 0x80, 0xAD, 0xF0,
0x80, 0x81, 0xAF, 0x6E, 0xC0, 0xAE, 0xF0, 0x80, 0x81, 0xA3,
0x6F, 0xF0, 0x80, 0x81, 0xAD
};
v6 = sub_EF1160(Text, byte_EF2008, 128);
Text[v6] = 0;
printf("%s", Text);
return 0;
}
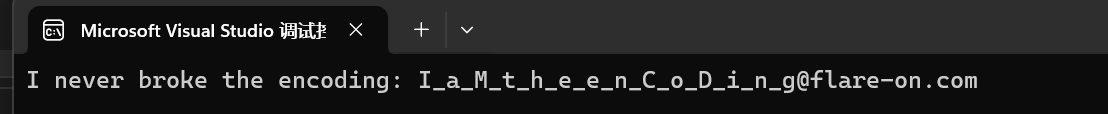
当然也可以直接写个新程序,在ida汇编界面用assmble把28改成127(改成128会溢出)
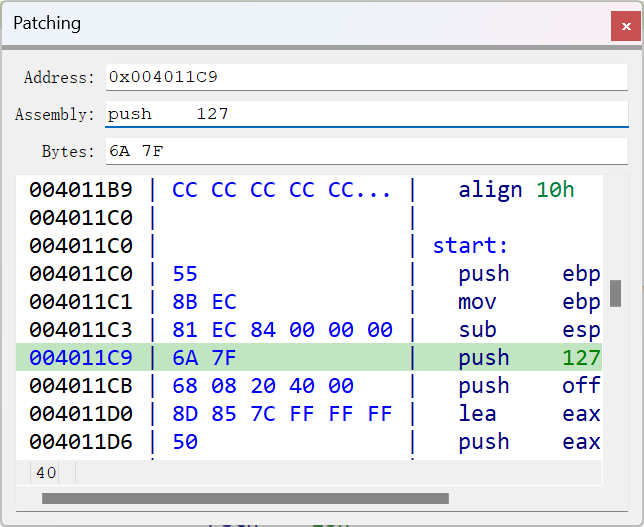
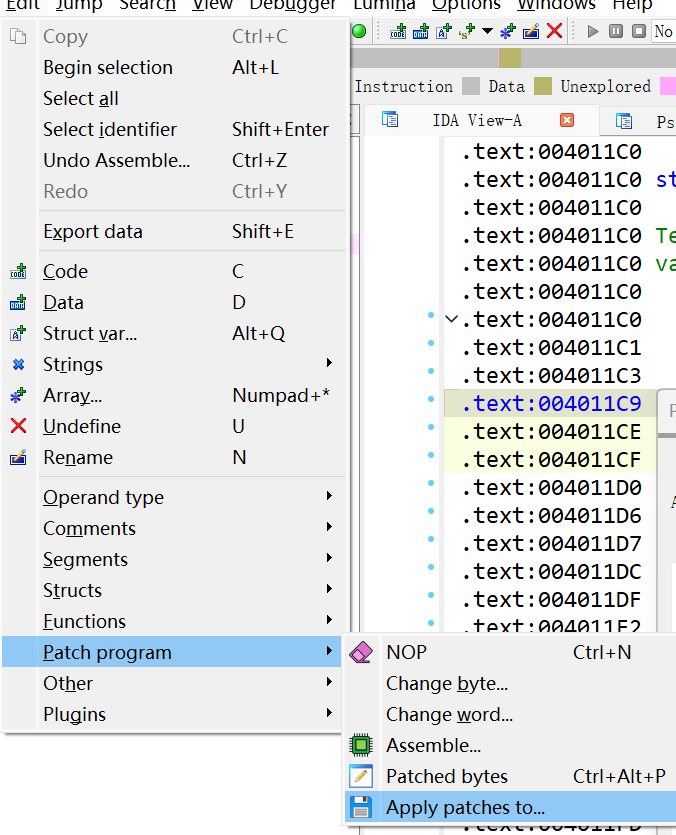
然后保存,记得命名的时候不要和原来的程序名字一样
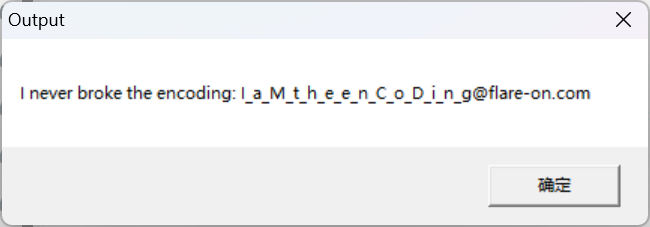
运行



 浙公网安备 33010602011771号
浙公网安备 33010602011771号