2023第十四届极客大挑战 — RE WP
RE方向出自:队友。
Shiftjmp
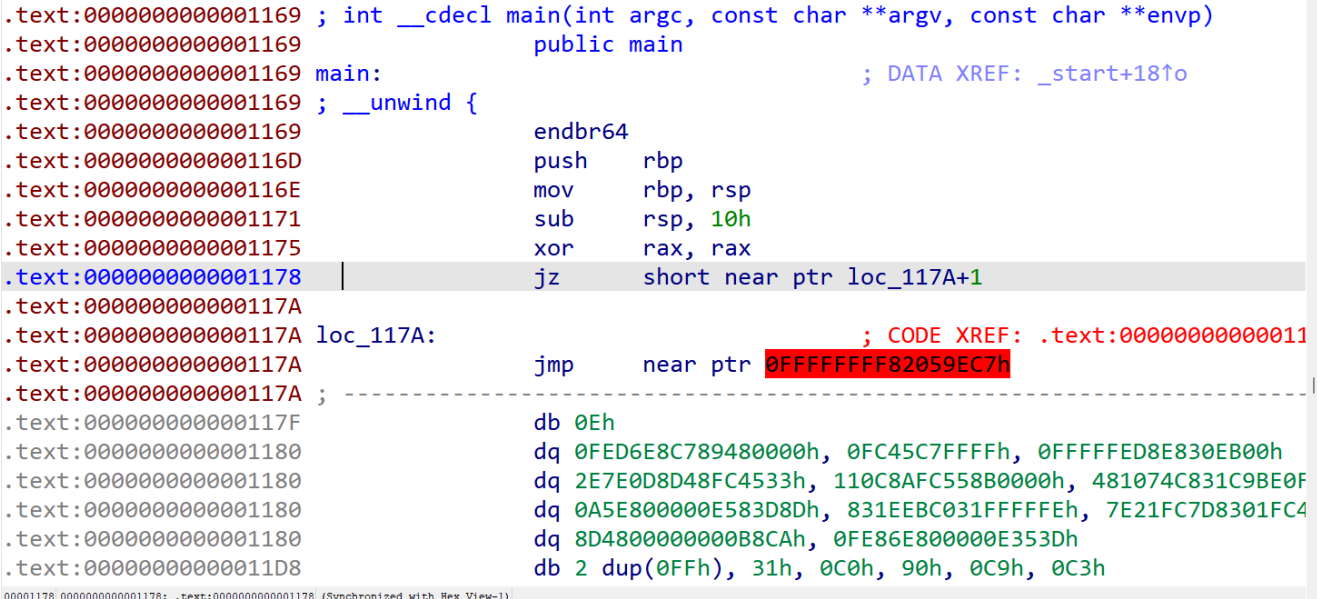
去花后按p然后再反编译
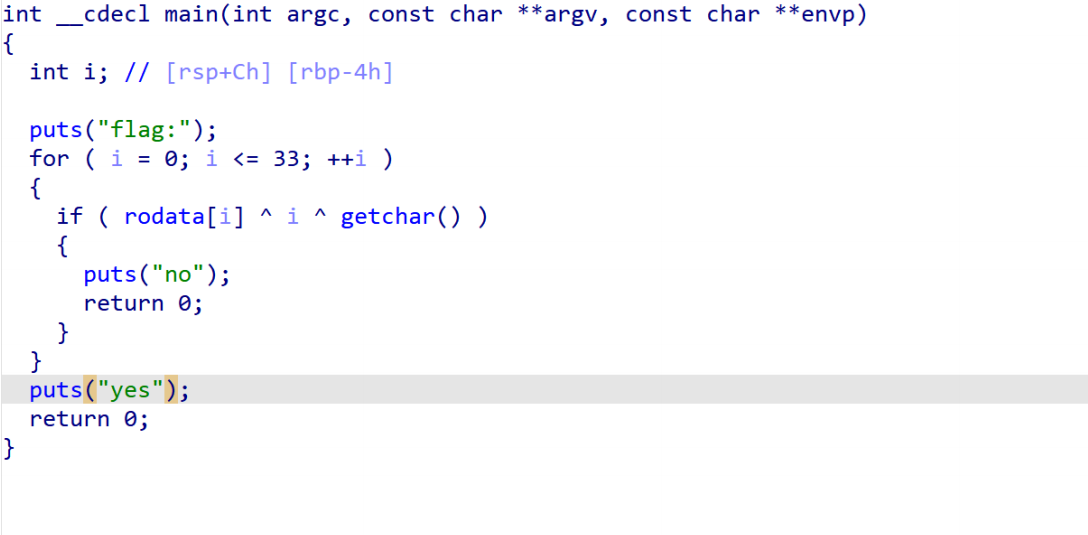
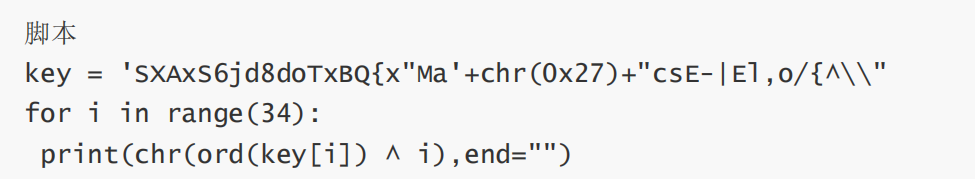
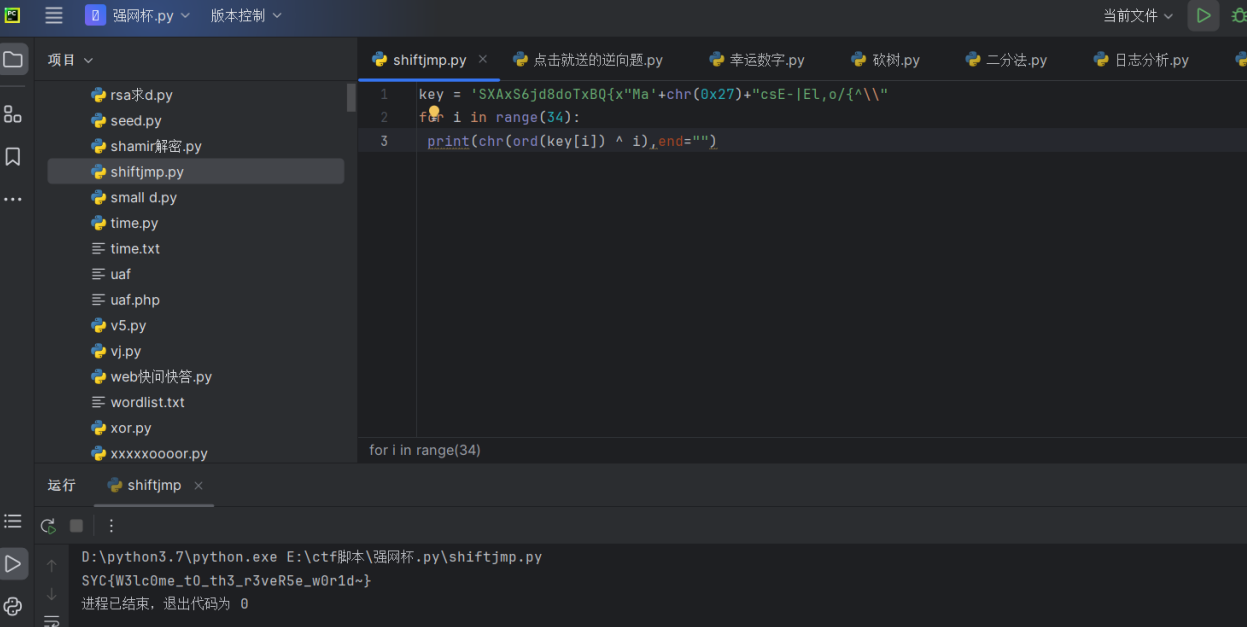
最后flag为SYC{W3lc0me_tO_th3_r3veR5e_w0r1d~}
点击就送的逆向题
gcc 1.s -o 1`
生成elf

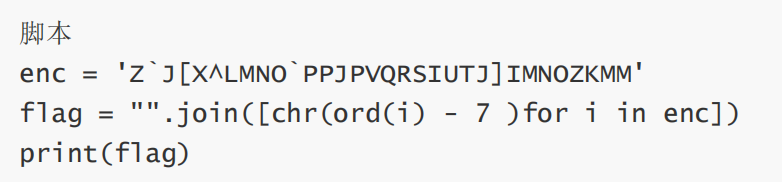

最后flag为SYC{TQWEFGHYIICIOJKLBNMCVBFGHSDFF}
幸运数字
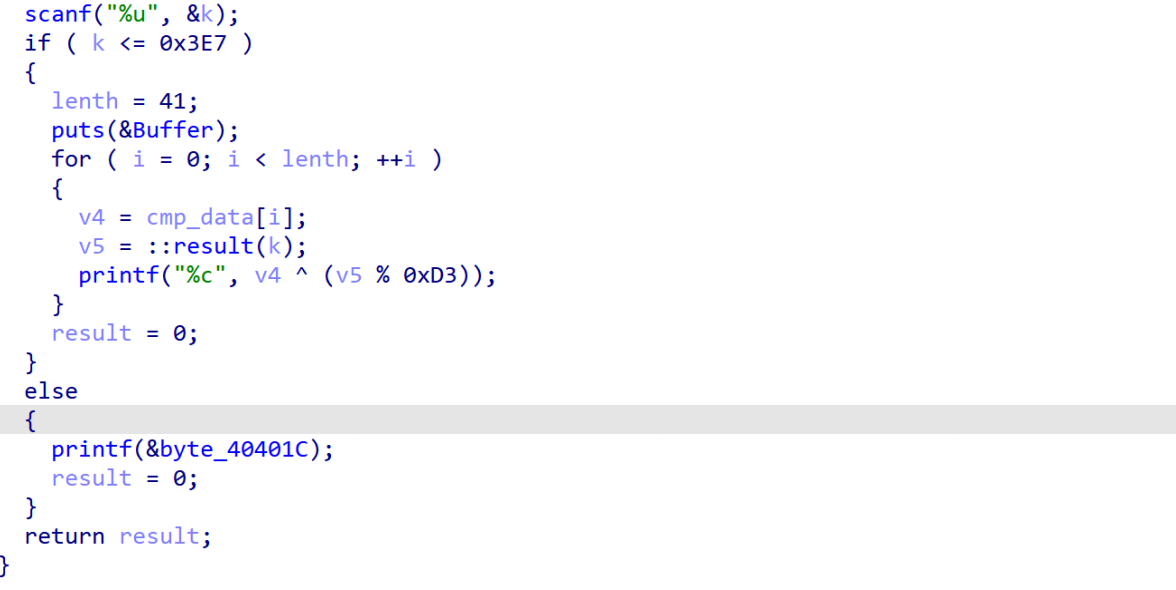
爆破v5
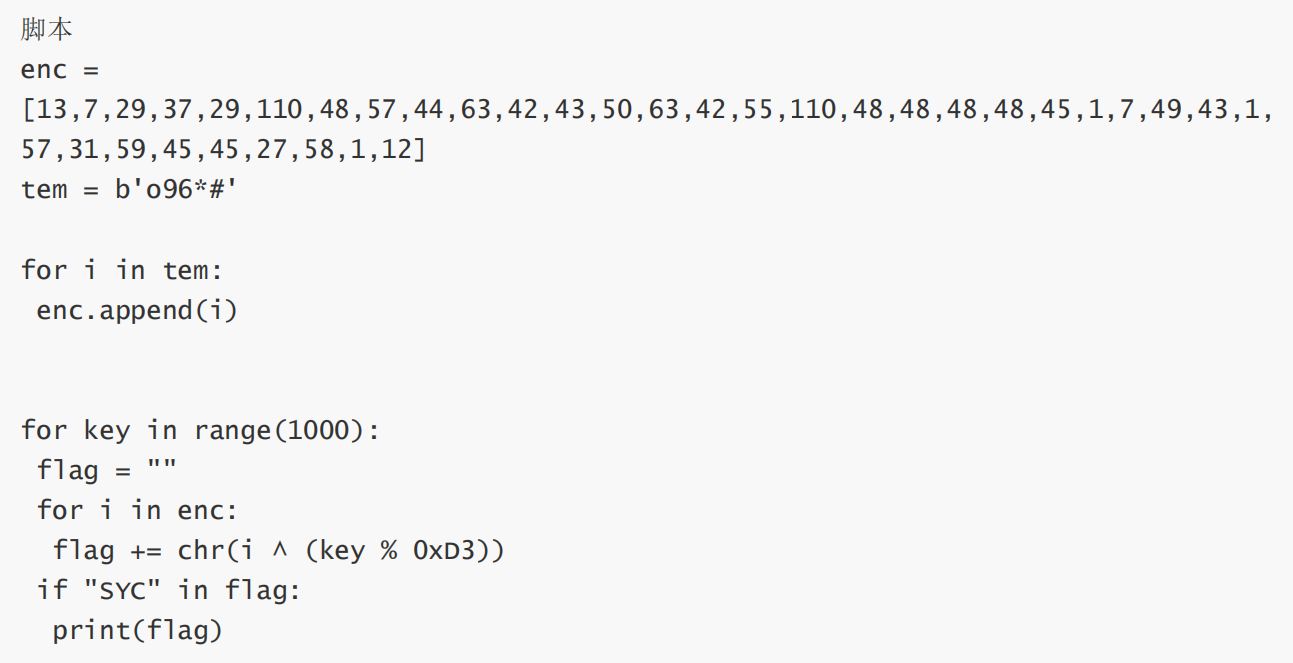
运行获得flag
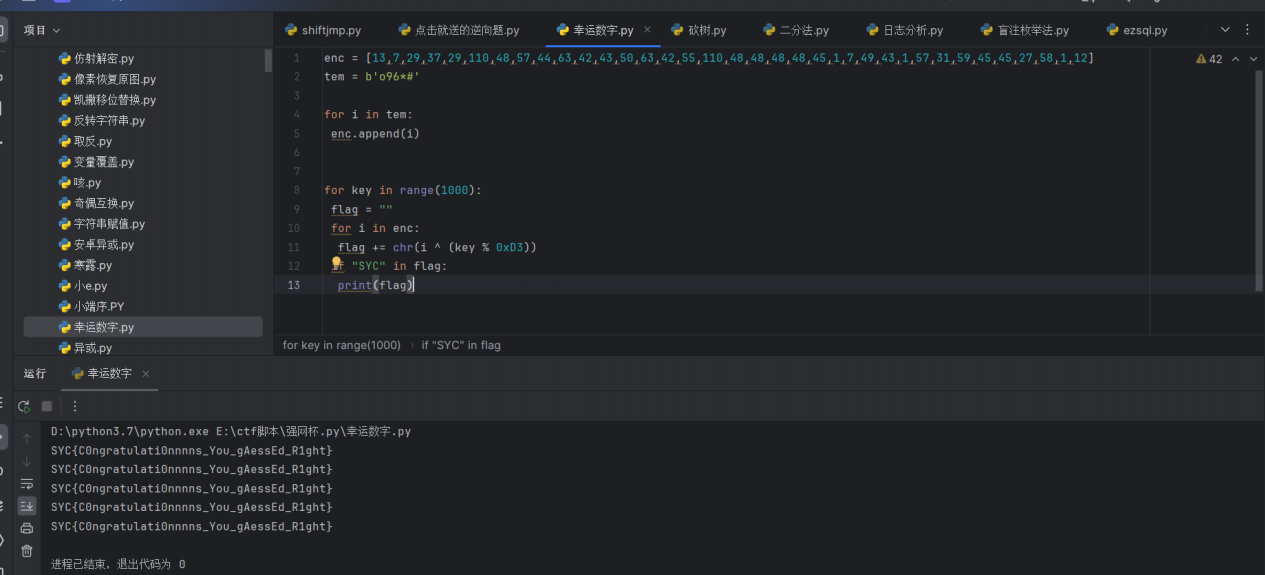
最后flag为SYC{C0ngratulati0nnnns_You_gAessEd_R1ght}
砍树
反编译
关键逻辑

由于是native 去找相关的so文件
ida打开

跟进 A0OWO0A
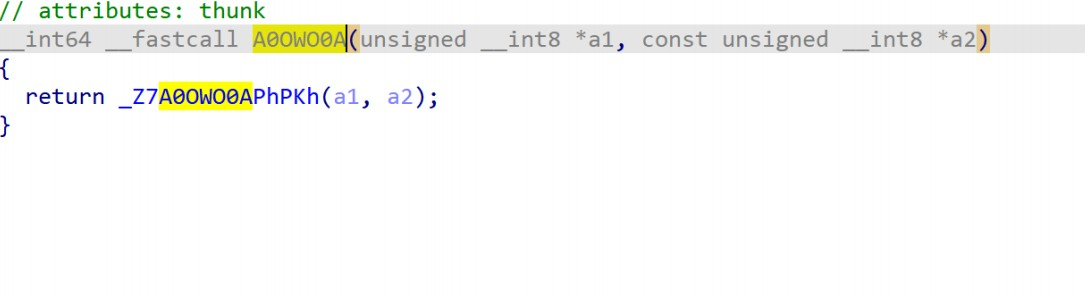
接着跟进_Z7A0OWO0APhPKh

EXP:
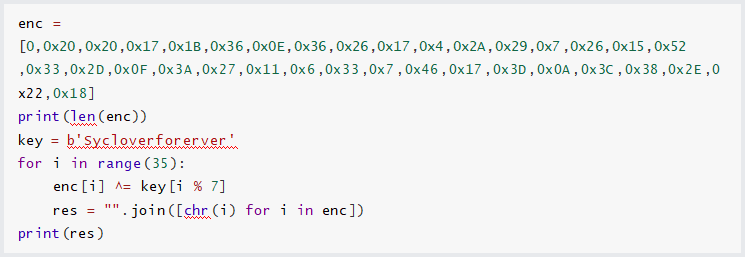

最后flag为SYC{t@ke_thE_bul1_By_the_h0rns_TAT}
easymath
exp:
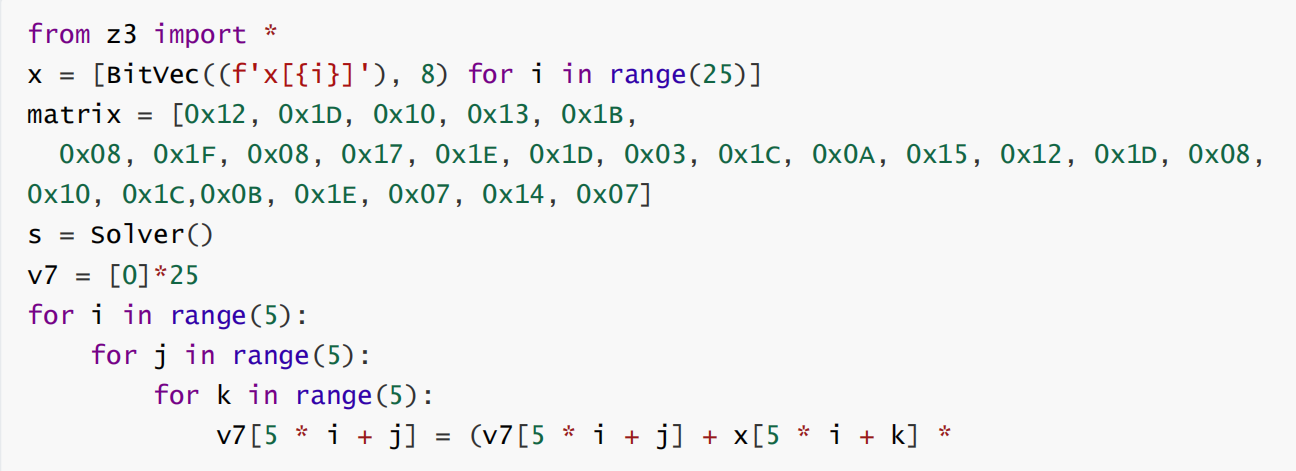

运行获得flag
最后flag为SYC{xtd4co_ymiunbbx3Aypsmbzii}
听说cpp很难?
exp:
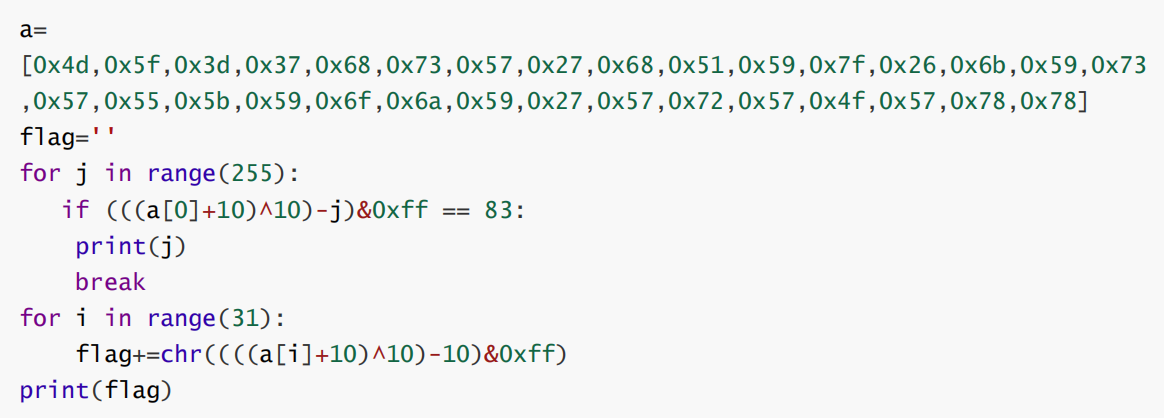
运行获得flag
加上括号
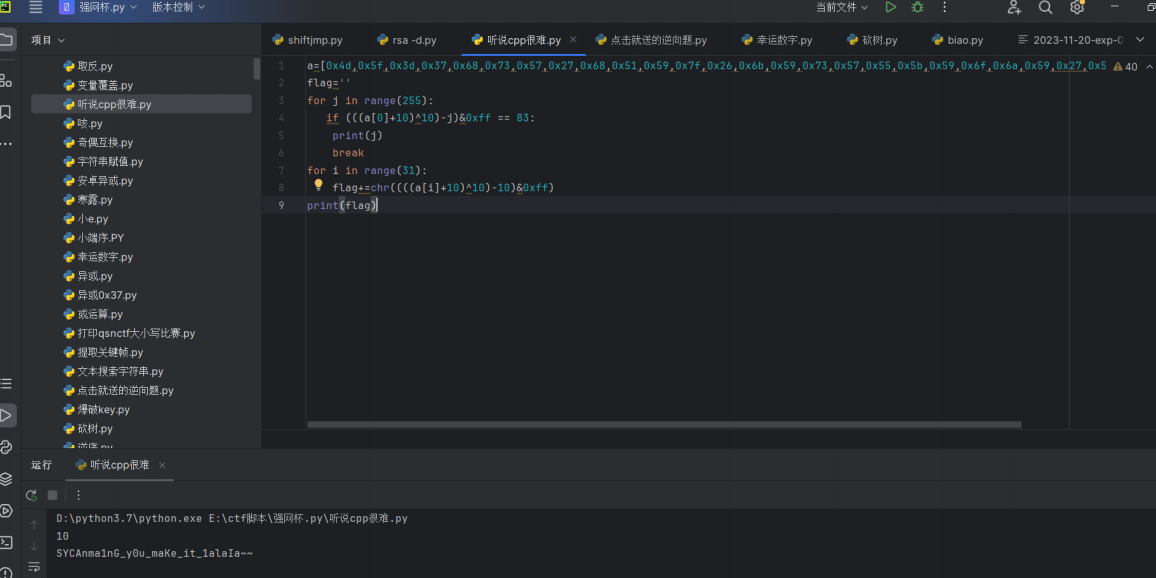
flower-or-tea
去花指令

exp1:
#include <stdio.h>
#include <stdint.h>
#include <stdio.h>
void decrypt(uint32_t* v, uint32_t* k) {
int v7 = 0;
for (int i = 0; i < 54; i++) {
v7 += 0x31415927;
}
v7 = v7 & 0xffffffff;
uint32_t v6 = v[0], v5 = v[1], i;
uint32_t k0 = k[0], k1 = k[1], k2 = k[2], k3 = k[3];
for (i = 0; i < 54; i++) {
v7 -= 0x31415927;
v6 -= (k[(v7 & 3)] + v7) ^ (v5 + ((v5 >> 5) ^ (16 * v5)));
v5 -= v7 ^ (k[((v7 >> 11) & 3)] + v7) ^ (v6 + ((v6 >> 5) ^(16 * v6)));
}
v[0] = v6; v[1] = v5;
}
int main()
{
uint32_t key[4] = {
32,27,39,44
};
uint32_t array[38] = { 0x9af9464b, 0xc417b89e, 0xb217a713,
0xc93ba9e8, 0x94f3e44e, 0xb5cc2ab5, 0x4451e42c, 0x7a8a289a,
0x53c8d008, 0x6e117b49, 0x9bffd794, 0x5eff2df9, 0x17e72531,
0xdfbd9979, 0x8f871b3a, 0x73e8c5ac, 0xb28670a6,
0x5af6a369,0x2cf7da24, 0x347b66af,
0xb9c84d60, 0x911e912f, 0xbd5a2f9b, 0xcb96733a, 0xc59968be,
0xa00013e9, 0xc12f4ea4, 0xde863a10, 0xa0c4d594,
0x4380983c, 0x7e2f7648, 0xe54ddc89, 0x3f27a690, 0xb58d3199,
0x604ae517, 0x9c903984, 0xf4e04481, 0x3cf4edff };
uint32_t temp[2] = { 0 };
int i = 0;
for (i = 0; i < 38; i += 2)
{
temp[0] = array[i];
temp[1] = array[i+1];
decrypt(temp, key);
printf("%c%c%c%c%c%c%c%c", ((char)&temp[0] + 0), *
((char*)&temp[0] + 1), ((char)&temp[0] + 2), ((char)&temp[0] +
3), ((char)&temp[1] + 0), ((char)&temp[1] + 1), *
((char*)&temp[1] + 2), ((char)&temp[1] + 3));
}
return 0;
} 运行c代码

得到字符串 S}Y?C?{ADe0t__Yro3vw_o1liFk_ek_nTioR_d
exp2:

运行获得flag
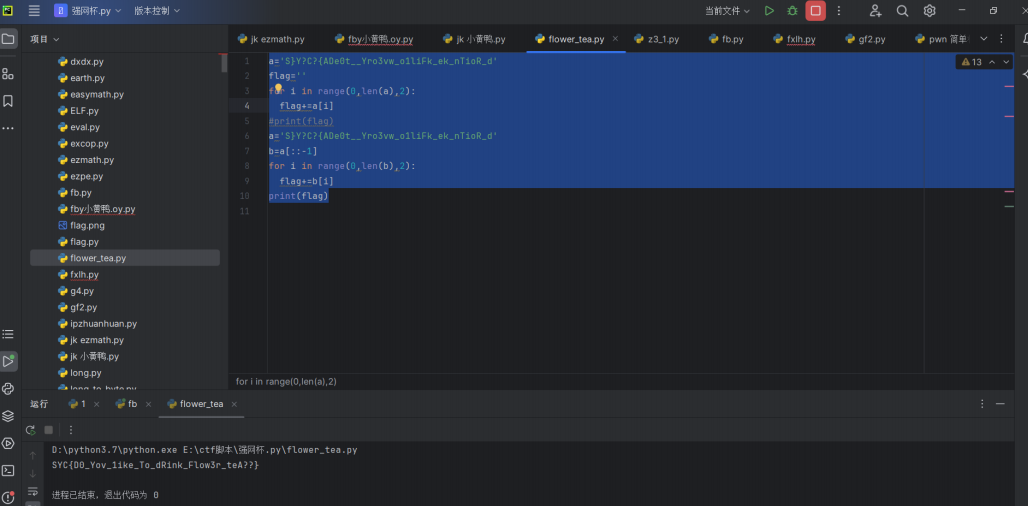
最后flag为SYC{D0_Yov_1ike_To_dRink_Flow3r_teA??}
mySelf
自解密
动调

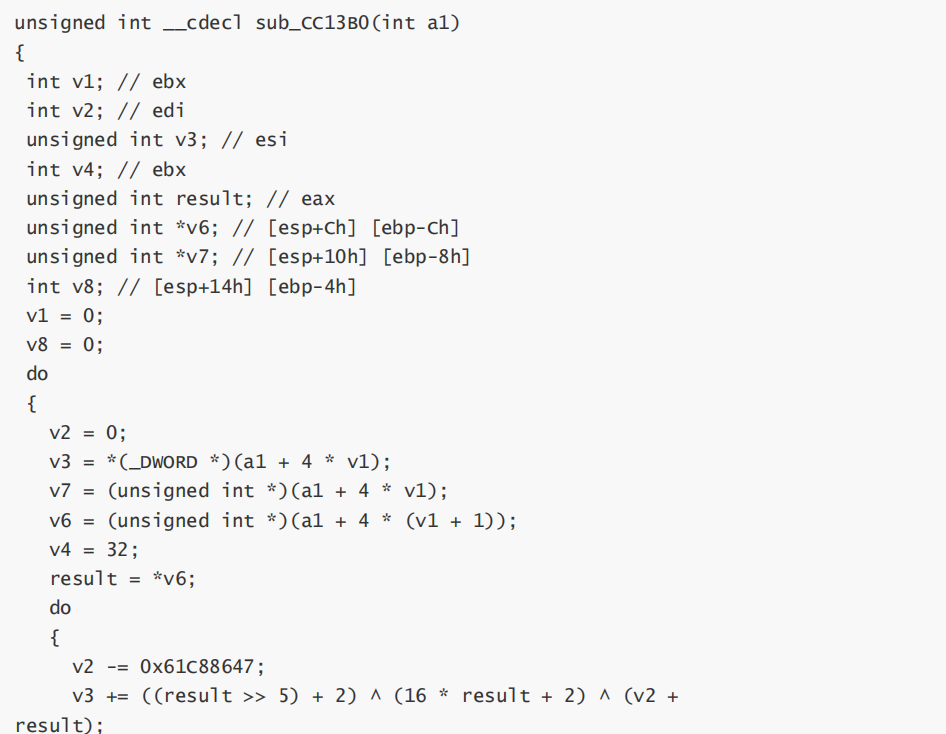
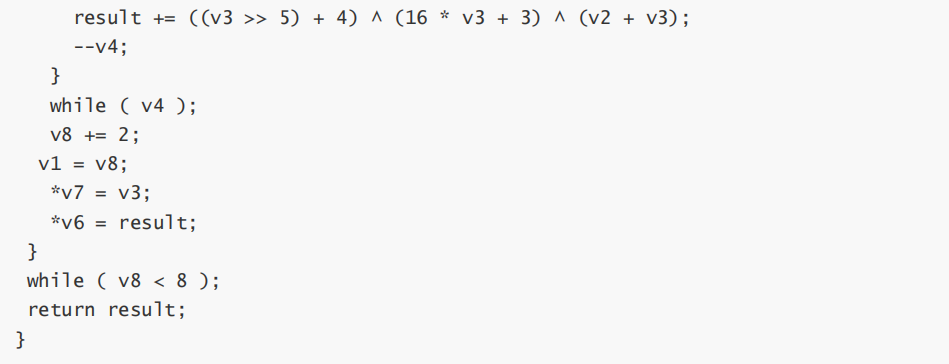
exp:
#include <stdio.h>#include <stdint.h>
#include <stdio.h>
void decrypt(uint32_t* v) {
int v2 = 0;
for (int i = 0; i < 32; i++) {
v2 -= 0x61C88647;
}
v2 = v2 & 0xffffffff;
uint32_t v3= v[0], result= v[1], i;
for (i = 0; i < 32; i++) {
result -= ((v3 >> 5) + 4) ^ (16 * v3 + 3) ^ (v2 + v3);
v3 -= ((result >> 5) + 2) ^ (16 * result + 2) ^ (v2 +
result);
v2 += 0x61C88647;
}
v[0] = v3; v[1] = result;
}
int main()
{
//uint32_t key[4] = {
//32,27,39,44
//};
uint32_t array[38] = {
0x0BDBDF9F0,0x0E26194C4,0x80799125,0x1F0FC219,0x0EB6A1815,0x84F572C5,0x40CC3A85,0x0
D2A32ABB };
uint32_t temp[2] = { 0 };
int i = 0;
for (i = 0; i < 8; i += 2)
{
temp[0] = array[i];
temp[1] = array[i + 1];
decrypt(temp);
printf("%c%c%c%c%c%c%c%c", ((char)&temp[0] + 0), *
((char*)&temp[0] + 1), ((char)&temp[0] + 2), ((char)&temp[0] +
3), ((char)&temp[1] + 0), ((char)&temp[1] + 1), *((char*)&temp[1] + 2), ((char)&temp[1] + 3));
}
return 0;
} 运行得到flag
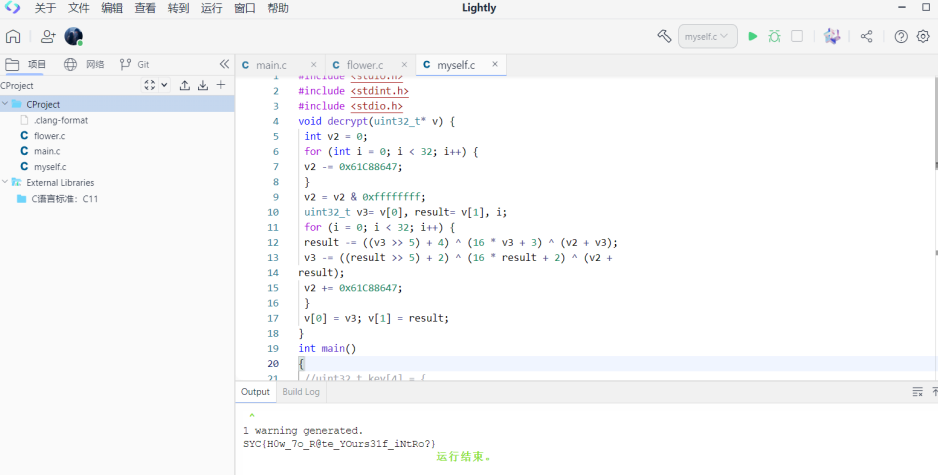
最后flag为SYC{H0w_7o_R@te_YOurs31f_iNtRo?}
rainbow
直接手撕了
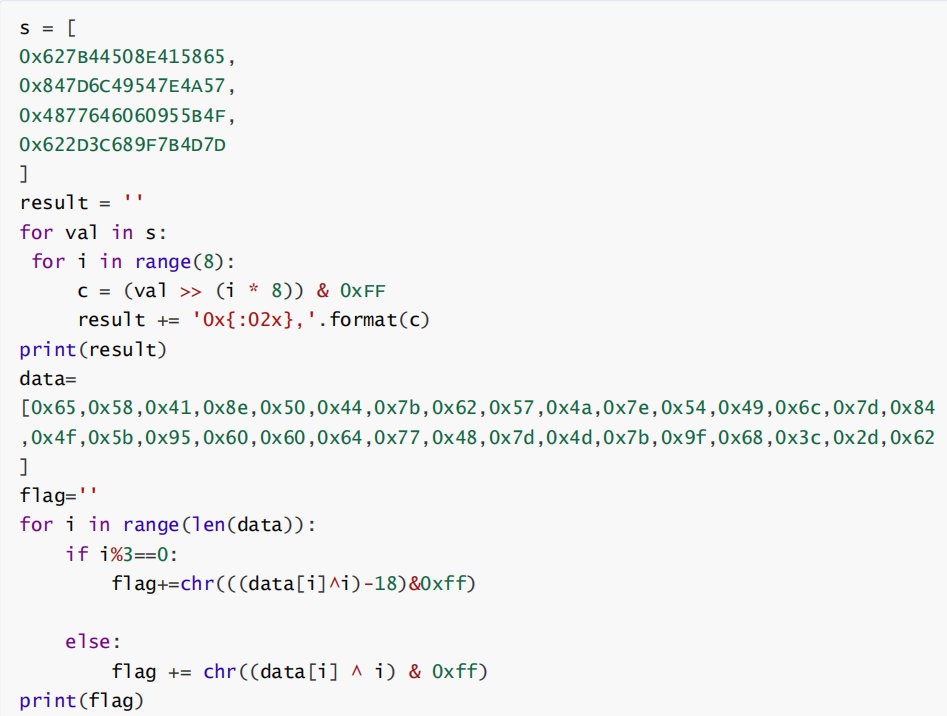
运行获得flag
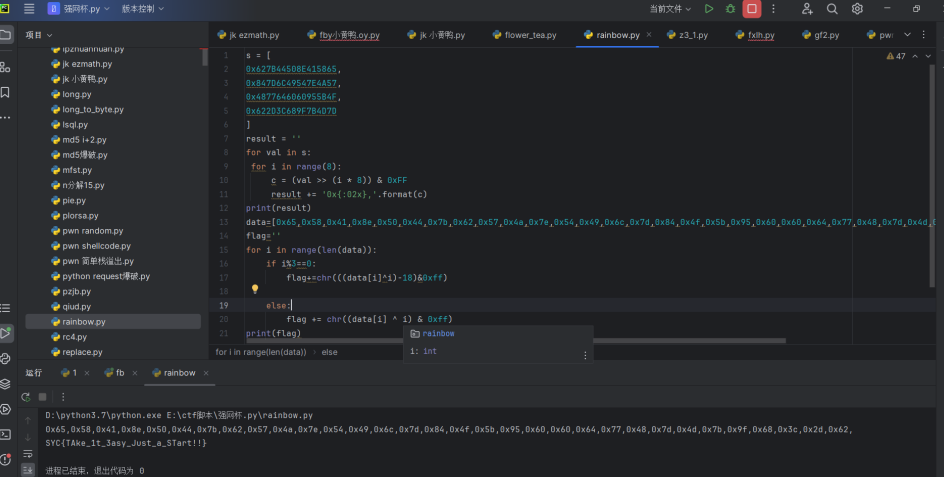
最后flag为SYC{TAke_1t_3asy_Just_a_STart!!}
小黄鸭
解包

反编译
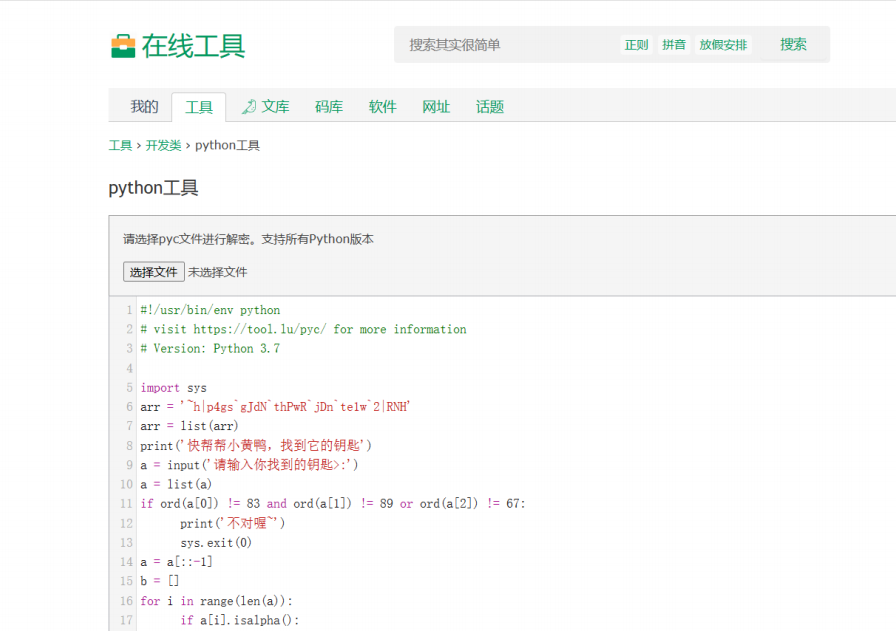
完整代码

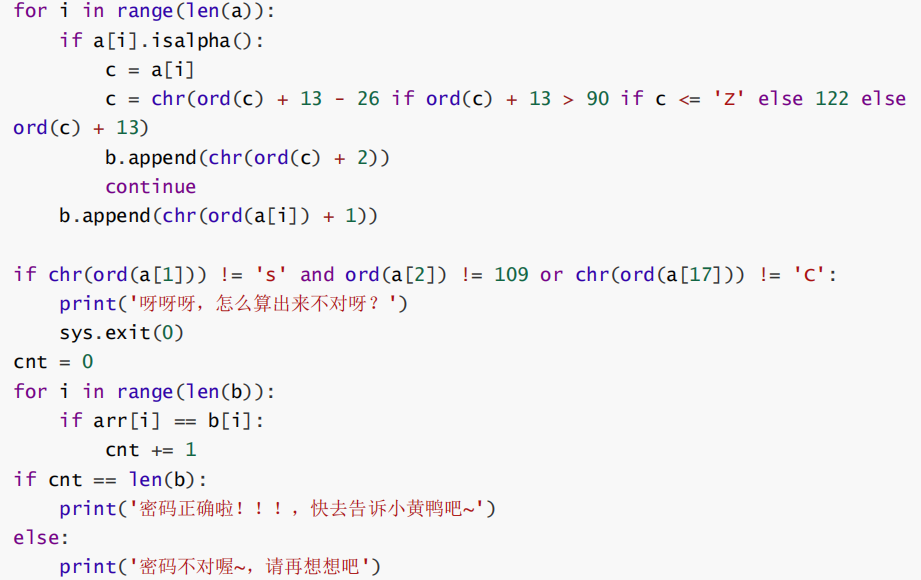
Exp:
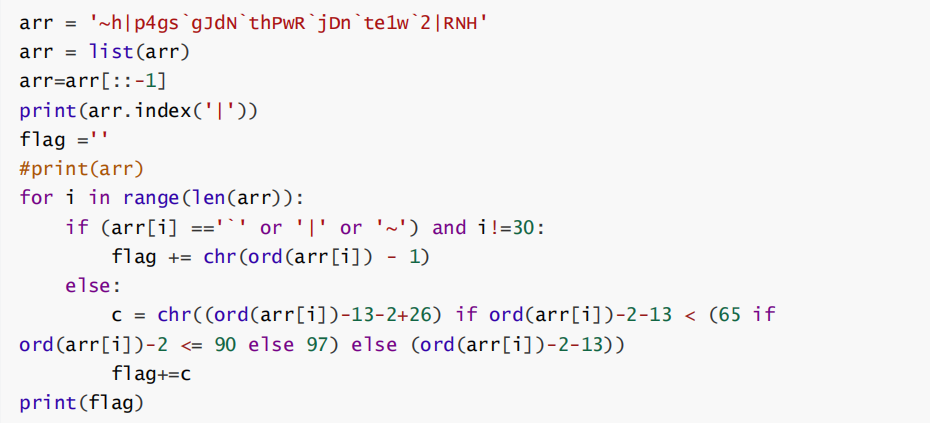
运行得到字符串GMQ{1_v0ds_mCi_QvOgs_McIf_rf3omg}
凯撒解密
保证m不变,其他凯撒位移
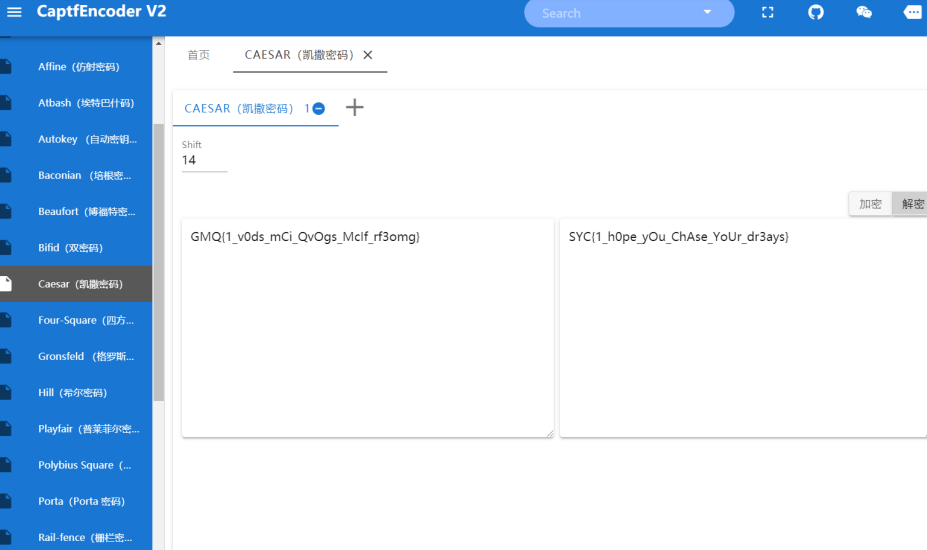
最后flag为SYC{1_h0pe_yOu_ChAse_YoUr_dr3ams}
寻找初音未来
Exp:

运行获得flag

最后flag为SYC{N0thing_1s_sEriOus_But_MIku}
ezandroid
24位或者是24的倍数,不够的使用'X'进行补齐,将其给到sb
分两组,一组给到sb4,一组给到sb5 sb4是会进行操作的,进行tea加密
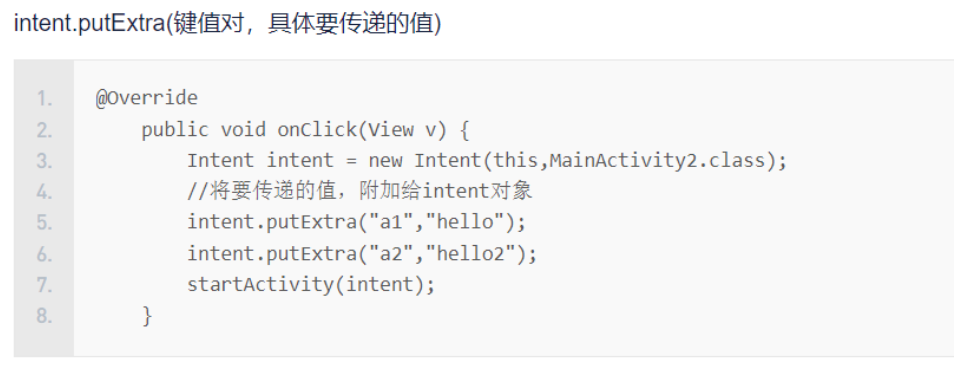
其实出现的"ad@#E!@a123"和"eCAS213@!@3"都是对象
第一部分flag:
exp:
#include <stdio.h>
#include
#include <stdlib.h>
void decrypt(int *v, int *k)
{
int v0 = v[0], v1 = v[2], v2 = v[1], sum = 0x9E3779B9 * 64, i;
/* set up */
int delta = 0x9E3779B9;
/* a key schedule constant */
int k0 = k[0], k1 = k[1], k2 = k[2], k3 = k[3];
/* cache key */
for (i = 0; i < 32; i++)
{ /* basic cycle start */
v1 -= (((v2 << 4) + k2) ^ (v2 + sum)) ^ ((v2 >> 5) + k3);
v2 -= (((v1 << 4) + k0) ^ (v1 + sum)) ^ ((v1 >> 5) + k1);
sum -= delta;
}
for (i = 0; i < 32; i++)
{ /* basic cycle start */
v1 -= (((v0 << 4) + k2) ^ (v0 + sum)) ^ ((v0 >> 5) + k3);
v0 -= (((v1 << 4) + k0) ^ (v1 + sum)) ^ ((v1 >> 5) + k1); sum -= delta;
}
v[0] = v0;
v[1] = v1;
v[2] = v2;
}
int main()
{
char encode1[12] = {-91, -8, -110, -55, -49, 75, 115, 13, -76,
-113, 102, 80};
int key[4] = {2023708229, -158607964, -2120859654, 1167043672};
char temp;
for (int i = 0; i < 3; i++)
{
temp = encode1[4 * i];
encode1[4 * i] = encode1[4 * i + 3];
encode1[4 * i + 3] = temp;
temp = encode1[4 * i + 1];
encode1[4 * i + 1] = encode1[4 * i + 2];
encode1[4 * i + 2] = temp;
}
int *flag1 = (int *)encode1;
decrypt(flag1, key);
for (int i = 0; i < 3; i++)
{
temp = encode1[4 * i];
encode1[4 * i] = encode1[4 * i + 3];
encode1[4 * i + 3] = temp;
temp = encode1[4 * i + 1];
encode1[4 * i + 1] = encode1[4 * i + 2];
encode1[4 * i + 2] = temp;
}
for (int i = 0; i < 12; i++)
{ putchar(encode1[i]);
}
system("pause");
return 0;
} 运行得到T0Vt33Tn0itr

第二部分flag
exp:
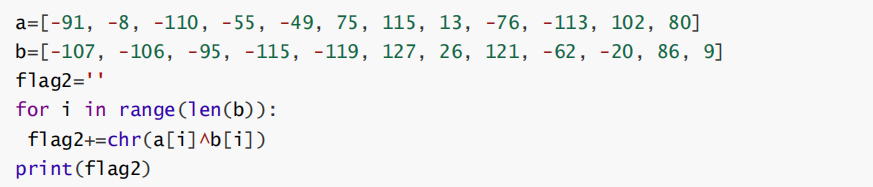
运行获得字符串0n3DF4itvc0Y
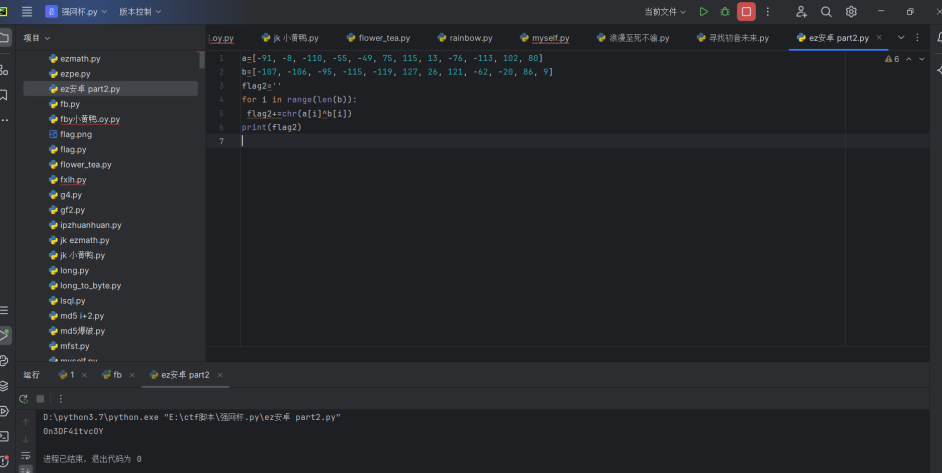
合并exp:

最后flag为SYC{T00nV3tD3F34Tint0vict0rY}
是男人就来扎针
dnspy打开
简单看一下逻辑


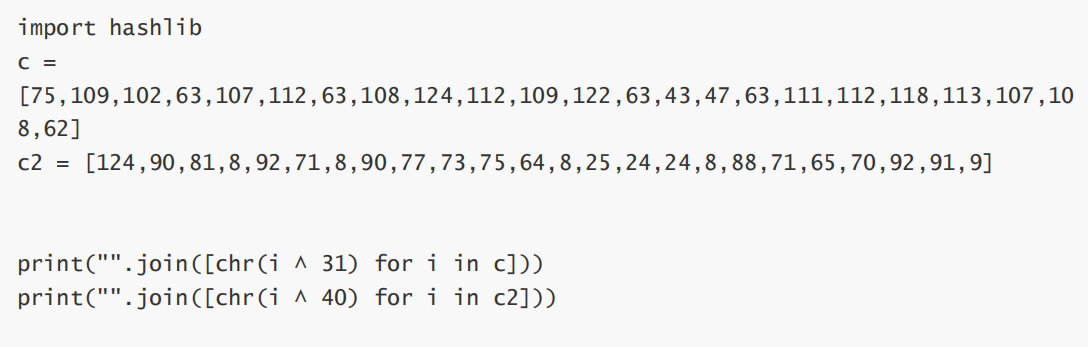
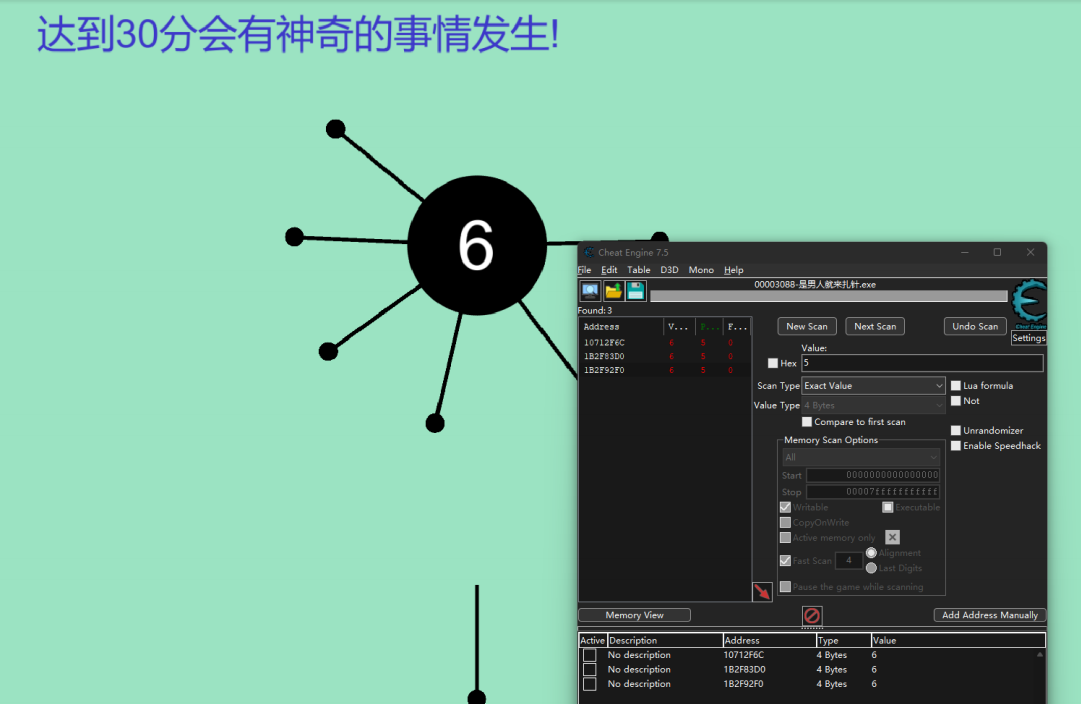
看看一下三十分和四十分输出什么

没啥用 再仔细看一遍逻辑
实际上拿30分的逻辑就能写出flag

包裹上SYC后提交
提示错误 那没辙了
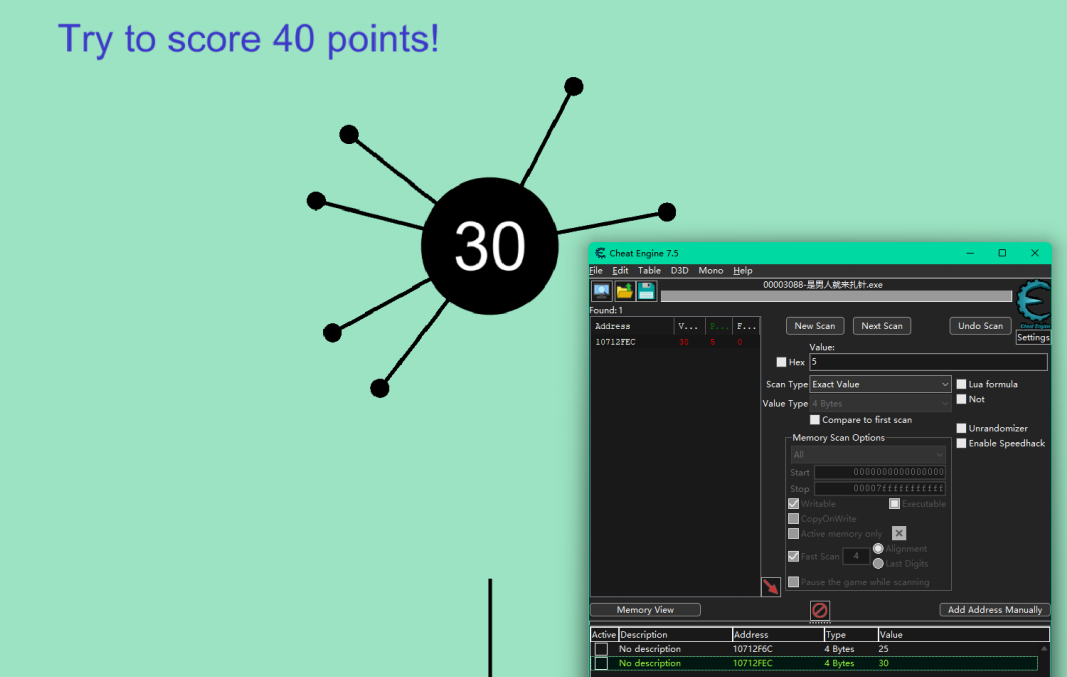
试试看CE去改数据
先定位

测试发现好像奇数轮记score的是一个地址
偶数轮是另外一个 都记下来
因为有一轮的有点问题
改29然后插针
改39然后插针
改99然后插针
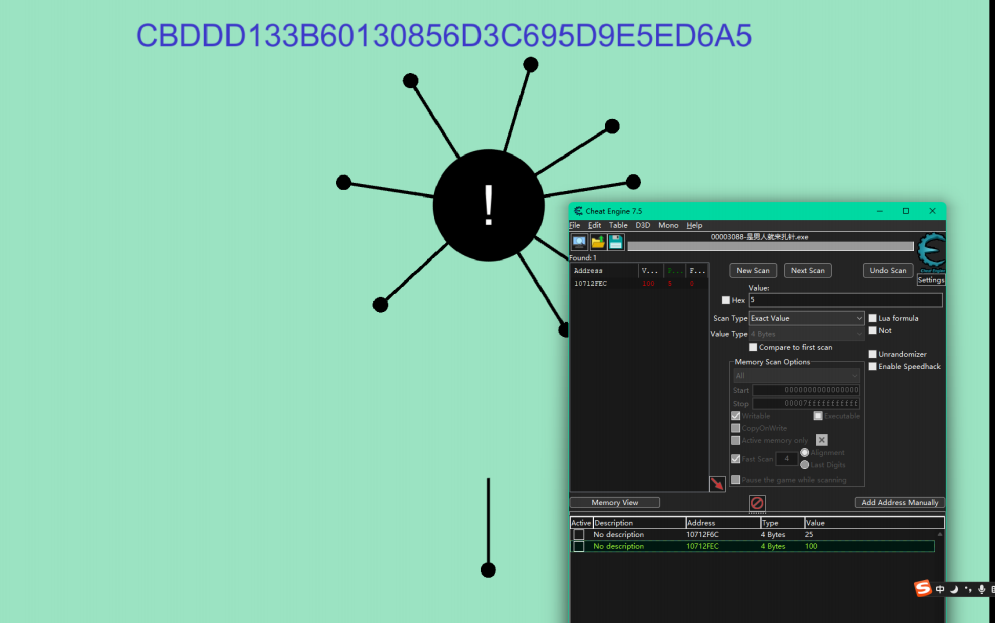
包裹后提交




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理