[GDOUCTF 2023]Math Problem
题目分数:451
题目标签: RSA
题目描述:
flag以NSSCTF{}形式提交附件内容:
#!/usr/bin/env sage
import secret
from Crypto.Util.number import *
p, q = getPrime(512), getPrime(512)
e, n = 0x10001, p * q
c = pow(bytes_to_long(secret.flag), e, n)
print(f"{e = }\n{n = }\n{c = }")
a, b = getPrime(512), getPrime(512)
E = EllipticCurve(GF(p), [a, b])
G = E.lift_x(ZZ(getPrime(64)))
print(f"{a = }\n{b = }\ny = {G.xy()[1]}")
'''
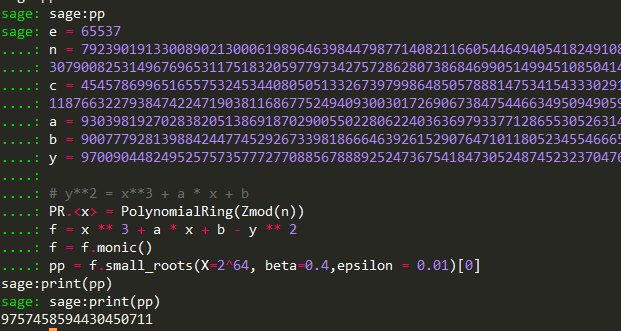
e = 65537
n = 79239019133008902130006198964639844798771408211660544649405418249108104979283858140199725213927656792578582828912684320882248828512464244641351915288069266378046829511827542801945752252863425605946379775869602719406340271702260307900825314967696531175183205977973427572862807386846990514994510850414958255877
c = 45457869965165575324534408050513326739799864850578881475341543330291990558135968254698676312246850389922318827771380881195754151389802803398367341521544667542828862543407738361578535730524976113729406101764290984943061582342991118766322793847422471903811686775249409300301726906738475446634950949059180072008
a = 9303981927028382051386918702900550228062240363697933771286553052631411452412621158116514735706670764224584958899184294505751247393129887316131576567242619
b = 9007779281398842447745292673398186664639261529076471011805234554666556577498532370235883716552696783469143334088312327338274844469338982242193952226631913
y = 970090448249525757357772770885678889252473675418473052487452323704761315577270362842929142427322075233537587085124672615901229826477368779145818623466854
'''解题过程:
1、使用SageMath
Sage下载使用链接
https://docs.qsnctf.com/qsnctf/43531.html
2、解出pp后使用脚本:
from Crypto.Util.number import long_to_bytes
from gmpy2 import invert,iroot,gcd,mpz,powmod
e = 65537
n = 79239019133008902130006198964639844798771408211660544649405418249108104979283858140199725213927656792578582828912684320882248828512464244641351915288069266378046829511827542801945752252863425605946379775869602719406340271702260307900825314967696531175183205977973427572862807386846990514994510850414958255877
c = 45457869965165575324534408050513326739799864850578881475341543330291990558135968254698676312246850389922318827771380881195754151389802803398367341521544667542828862543407738361578535730524976113729406101764290984943061582342991118766322793847422471903811686775249409300301726906738475446634950949059180072008
a = 9303981927028382051386918702900550228062240363697933771286553052631411452412621158116514735706670764224584958899184294505751247393129887316131576567242619
b = 9007779281398842447745292673398186664639261529076471011805234554666556577498532370235883716552696783469143334088312327338274844469338982242193952226631913
y = 970090448249525757357772770885678889252473675418473052487452323704761315577270362842929142427322075233537587085124672615901229826477368779145818623466854
pp = 9757458594430450711
x0 = mpz(pp)
kp = x0 ** 3 + a * x0 + b - y ** 2
p = gcd(kp,mpz(n))
q = n//p
phi = (p-1)*(q-1)
d = invert(e,phi)
m = powmod(c,d,n)
flag = long_to_bytes(m)
print(flag)flag{c4edd6d0-d1b3-cbda-95e3-a323edc35be5}




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理