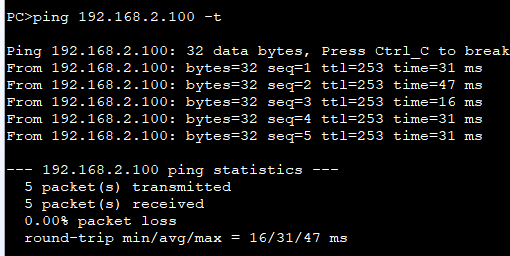
IPsec

FW1:
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.1.254 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
ipsec policy map
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
ip route-static 192.168.2.0 255.255.255.0 1.1.1.2
security-policy
default action permit
创建acl列表:
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
配置时适当修改ip和接口
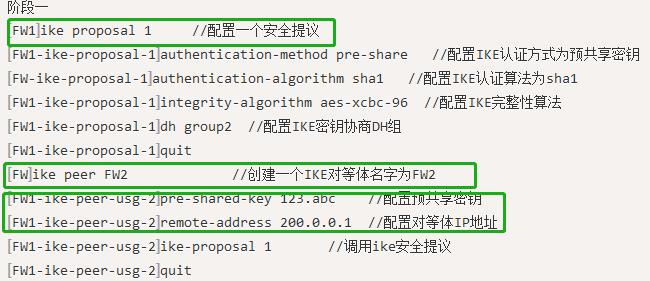
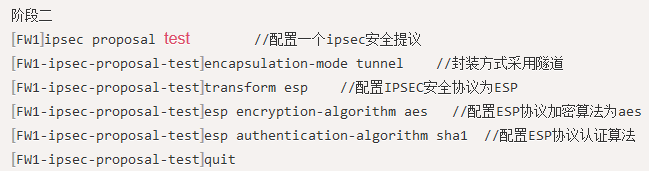
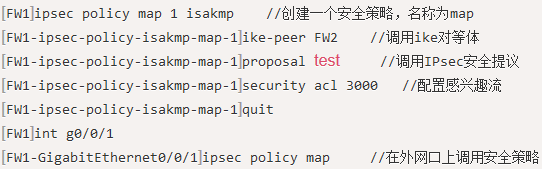
以下是策略的详细明细:
dis firewall session table ver
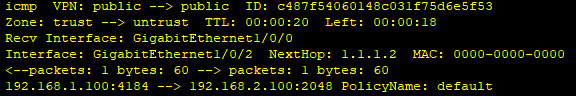
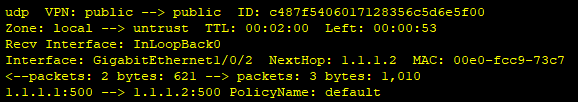

把大的策略关了,改写为详细明细
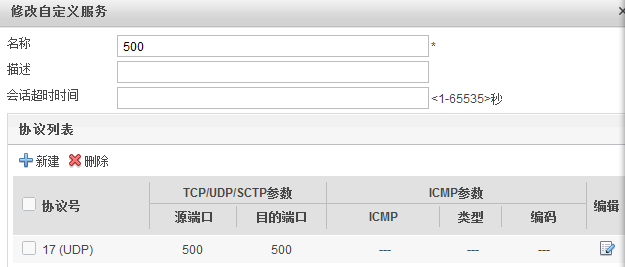
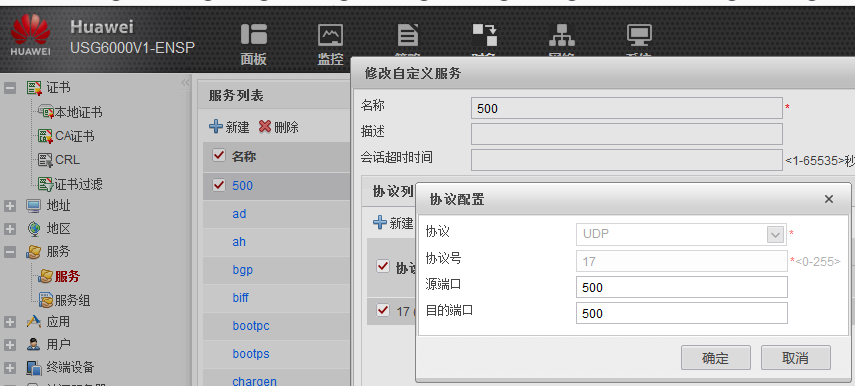
其中有UDP协议,用命令写的时候写不上,所以在浏览器里创建一个服务
在策略里写上service 500
在FW1上连一个云

FW2:
interface GigabitEthernet1/0/0
undo shutdown
ip address 1.1.1.2 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
ipsec policy map
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.2.254 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
ip route-static 192.168.1.0 255.255.255.0 1.1.1.1
security-policy
default action permit
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
IPsec和FW2一样,注意IP地址和接口
其余配置和FW1一样