ShadowPLCs A Novel Scheme for Remote Detection of Industrial Process Control Attacks
SHADOWPLCS:一种新的工业过程控制攻击远程检测方案
一、摘要
本文提出了一种检测工业过程控制攻击的新方案,称为SHADOWPLCS。该方案首先对PLC控制代码进行自动分析,然后提取PLC的关键参数,包括有效寄存器地址、有效值范围、控制逻辑规则等,作为评估攻击的依据。通过主动与PLC通信和被动监控网络流量,从不同角度实时检测攻击行为。
二、介绍
目前仍存在现有工业网络入侵检测系统(IDS)无法检测或阻止的关键攻击,IDS很难从根源上检测隐蔽的攻击。主要有三方面的原因:
- 从目标系统中并不总是观察到一致的特征,限制了检测规则的提取。
- 每个ICS都是唯一的,因此,领域专家必须密切参与检测规则的创建。但是,这个过程是非常昂贵和耗时的,可能源于专家的错误,从而错过了检测规则中的关键细节。
- 攻击者通常使用各种策略来逃避检测。
为了克服现有解决方案的局限性,我们提出了一种新的攻击检测方案SHADOWPLCS。通过分析五种具有代表性的工业过程控制攻击:非法访问地址攻击、恶意数据注入攻击、配置篡改攻击、控制逻辑感染攻击和控制程序替换攻击,激发了ICS对SHADOWPLCS的需求。
SHADOWPLCS自动分析PLC控制代码,提取PLC关键参数,包括有效寄存器地址、有效值范围、控制逻辑规则等,作为检测攻击的基本。基于这些规则SHADOWPLCS主动与PLC通信,映射其存储空间,被动监控网络流量,并从不同角度实时检测过程控制攻击。
三、攻击建模
(一)对手模型
对手可以对PLC进行远程网络攻击,如获取控制中心的控制权限或作为中间人攻击PLC。我们认为对手的目标是操纵或扰乱实际的工业控制过程。在本文中,我们将近年来针对PLC的网络攻击方法分为两类:1)虚假数据注入;2)控制逻辑注入。
虚假数据注入是指将不符合工业控制过程的恶意数据注入PLC,最终导致过程控制的破坏。例如,写反转或最小/最大,修改关键设定点变量和进程值。
控制逻辑注入是指篡改或替换在目标PLC上运行的原始控制逻辑,攻击者通过干扰正常的下载/上传控制逻辑工程操作,向目标PLC注入恶意控制逻辑。
(二)攻击场景
基于上面讨论的对手模型,我们考虑以下可能严重扰乱工业控制过程的攻击场景: 非法访问地址攻击、恶意数据注入攻击、配置篡改攻击、控制逻辑感染攻击、控制程序替换攻击。
非法地址访问攻击。 在这个攻击场景中,假设PLC是对手的黑盒,但对手有能力远程访问PLC的寄存器空间。为了有效地攻击PLC,攻击者首先会探测PLC的寄存器空间,找到攻击的关键执行点。这种攻击很容易发动,而且对手不需要知道实际的工业流程。
恶意数据注入攻击。 假设对手已经知道PLC中的一些关键控制点,例如控制阀门打开或关闭的寄存器Q0.0。对手聚焦在这些关键控制点上,导致控制混乱。一种常见的攻击方法是强制对一个寄存器地址进行写操作,覆盖寄存器的当前值。
配置篡改攻击。 假设攻击者获得了工业流程的一些知识,他们通过恶意篡改关键程序配置信息间接地破坏了工业流程。例如,篡改计时器和计数器设置等,发动延迟攻击。
控制逻辑感染攻击。 假设对手有能力窃取PLC当前的控制程序。它们通过感染控制程序干扰实际的工业生产过程。例如,将I/O寄存器中的值替换为内存中某个地方的可控值,以控制执行器的状态。
控制程序替换攻击。 在这种攻击场景中,攻击者并不感染原PLC控制程序,而是植入恶意控制代码,试图让PLC执行。因为这种攻击完全由对手控制,摧毁任何他们想要完成的工业过程,它具有很强的隐蔽性和破坏性,随时可以发动。
四、SHADOWPLCS方案原理
(一)规则生成
利用PLC代码进行基于签名的检测规则生成。 通过分析PLC代码,可以识别的IDS签名集主要有三种白名单规则:有效地址规则、有效取值范围规则和控制逻辑规则。 如下图所示,演示如何使用PLC代码生成基于签名的检测规则。
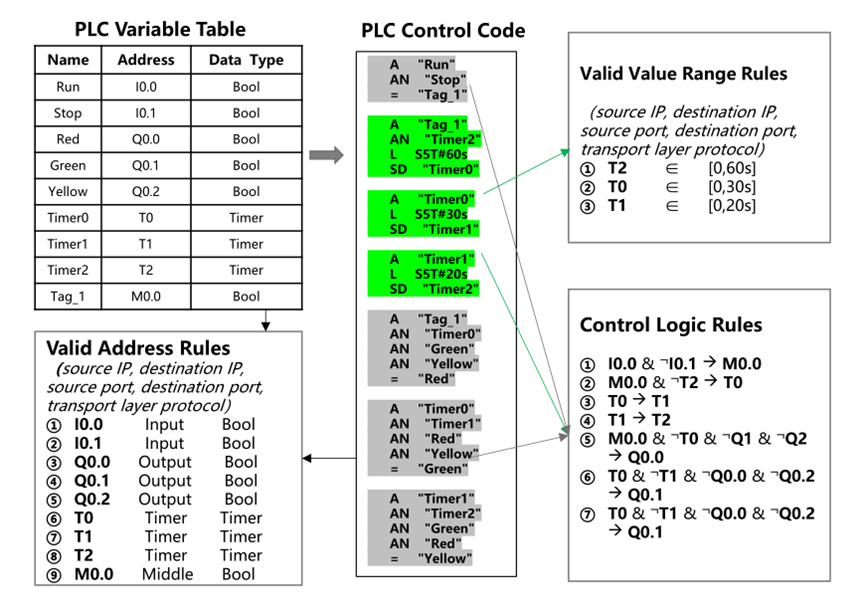

(二)攻击检测
本文提出了一种主动和被动相结合的入侵检测方案。 如下图所示,该IDS包括两个部分:被动检测引擎和主动检测引擎。被动检测引擎通过被动监控网络流量,检测非法地址操作、非法值违规等异常行为。主动检测引擎主动与PLC通信,映射低中断和轮询的PLC内存空间,实时监控工业控制过程中的异常情况。对于攻击者来说,要避免主动和被动相结合的入侵检测方案,实现隐身是非常困难和昂贵的。因为他们需要不断模拟正常的工业场状态,符合控制逻辑,甚至需要篡改设备的固件或网络通信模块,而不是通过简单的ARP欺骗和重放报文等传统手段欺骗IDS和控制中心。

①被动检测
被动检测引擎首先将流经工业交换机的网络流量镜像,通过对工业控制协议的深入解析,提取出五元组信息(源IP、目的IP、源端口、目的端口、传输层协议)、操作地址、操作指令和具体值。然后检查上述信息是否符合有效地址白名单和有效值范围白名单,检测非法链接、非法地址操作、非法值等异常行为。
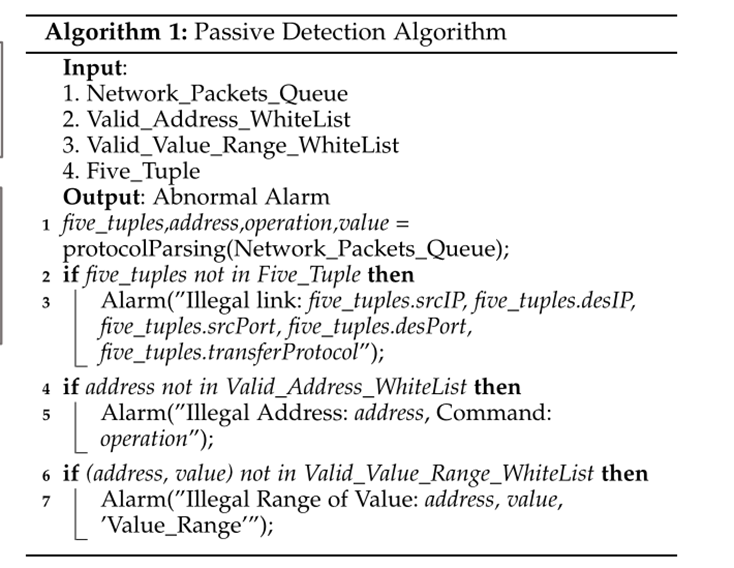
算法1给出了被动检测的过程。第1行表示一个深度解析协议,并提取五元组、地址、操作和值。第2行为非法链路检测。当网络流量中出现未知的IP、未知的端口、未知的通信时,会上报非法链路。第4行检测非法地址。当网络流量中有PLC实际未使用的地址时,会报警非法地址;第6行表示检测非法值范围。当值超出范围等,它将报警非法的值范围。
②主动检测
主动检测引擎主要检测控制逻辑异常,防止重要内存地址被恶意数据注入,防止关键配置被篡改,防止控制程序被篡改或替换。主动检测模块首先主动连接PLC并映射相应的内存空间,然后验证其是否满足有效值范围白名单和控制逻辑白名单。
主动检测引擎以主动、低干扰、轮询的方式检测PLC是否受到攻击,其核心部分如算法2所示。首先,与PLC(第1行)建立通信连接; 然后攻击检测(第2- 16行);最后,当有任务更改需求时,连接断开并销毁任务(第17行,第18行)。在攻击检测阶段,第一步是加载控制逻辑规则、有效取值范围规则和有效地址规则(第4行),获取寄存器地址和数据类型。其次,根据协议格式构建请求报文并发送给PLC(第5、6行)。第7行和第8行表示接收响应数据并解析协议以提取寄存器变量值; 最后,检查有效值范围和控制逻辑是否存在异常(第9行第15行)。第16行表示对请求频率的设置,以实现对PLC的低干扰。

五、实验评估
为了评估SHADOWPLCS对工业过程控制攻击的检测效果,我们使用两台西门子S7-300 PLC部署在一个燃气管网平台上进行实验。首先,我们验证了将S7-300 PLC的MC7代码反编译为STL源代码的准确性,我们的反编译模块可以准确的将MC7机器码反编译成STL代码,准确率达到100%。其次,分析GitHub、Shodan以及我们的燃气管网平台的的多个PLC程序并生成检测规则。然后,我们比较了SHADOWPLCS与其他四种检测模型(自回归(AR)模型、SRID、LSTM和S-IDS)的检测性能,下表是与其他异常检测模型的性能比较。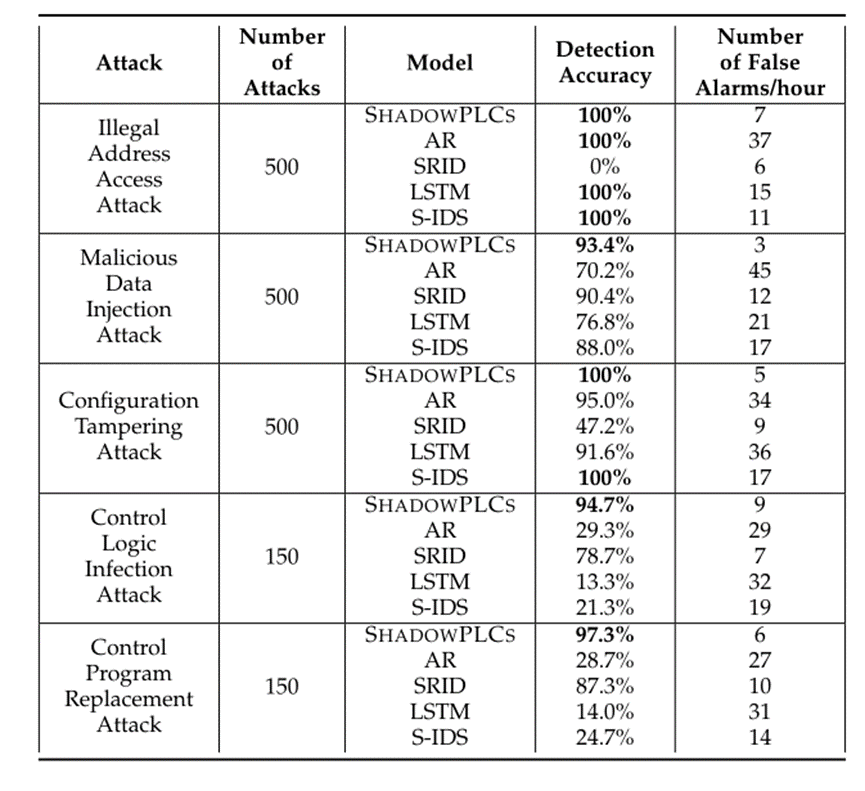
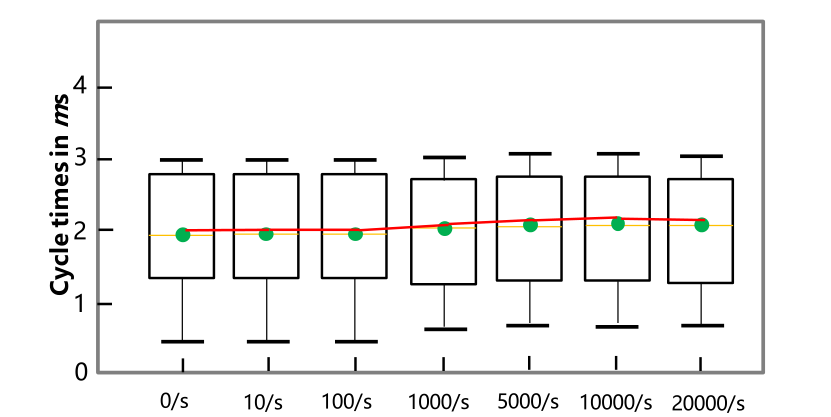
最后,为了证明我们的方案对PLC几乎没有影响,我们在检测阶段监控PLC的运行周期变化,并通过压力测试测试PLC处理网络流量的能力。为了避免路由器的当前限制,我们直接用网线连接PLC,每秒钟向PLC发送10、100、1000、5000、10000、20000个请求包。如下图所示,在无外界干扰的情况下,燃气管网平台PLC的周期在0-3ms之间,大部分维持在2ms左右。当S7-300 PLC受到不同程度的外部干扰时,我们发现其周期时间几乎没有受到影响。
六、总结
SHADOWPLCS 通过PLC代码生成的检测规则比基于网络流量的建模和规则提取更加全面,能够充分反映真实的受控过程;通过对PLC控制代码的自动分析,自动综合生成权威的检测规则,不需要人类依靠经验和手动配置建模;该方案采用主动和被动相结合的方法,从不同的角度检测攻击行为。由于我们对受控过程有了深刻的理解,并主动映射相应的PLC寄存器变量,这使得攻击者更难进行隐蔽的攻击。为了逃避检测,攻击者需要了解真实的工业流程,并能够对IDS遵守受控流程的假数据进行实时响应。这通常需要深入PLC,攻击PLC固件并修改其网络处理模块,而不是简单地通过中间人来避免被发现。此外,根据我们提出的检测方案,我们可以定制开发不同的PLC设备,并可以实际应用,对ICS做出实质性的防御。
[1] Dell threat report claims 100 percent increase in scada at-
tacks, 2015. https://threatpost.com/dell-threat-report-claims-100-
percent-increase-inscada-attacks/112241.
[2] Borja Fernandez Adiego, Dániel Darvas, Enrique Blanco Vi˜nuela,
Jean-Charles Tournier, Simon Bliudze, Jan Olaf Blech, and V´ıctor
Manuel González Suárez. Applying model checking to industrial-
sized plc programs.IEEE T ransactions on Industrial Informatics,
11(6):1400–1410, 2015.
[3] Chuadhry Mujeeb Ahmed, Martin Ochoa, Jianying Zhou, A-
ditya P Mathur, Rizwan Qadeer, Carlos Murguia, and Justin
Ruths. Noiseprint: attack detection using sensor and process noise
fingerprint in cyber physical systems. InProceedings of the 2018 on
Asia Conference on Computer and Communications Security, pages
483–497. ACM, 2018.
[4] Irfan Ahmed, Vassil Roussev , William Johnson, Saranyan Senthiv-
el, and Sneha Sudhakaran. A scada system testbed for cyberse-
curity and forensic research and pedagogy . InProceedings of the
2nd Annual Industrial Control System Security Workshop, pages 1–9.
ACM, 2016.
[5] D Alert. Cyber-attack against ukrainian critical infrastructure,
2016.
[6] Sebastian Biallas, Jörg Brauer, and Stefan Kowalewski. Arcade.
plc: A verification platform for programmable logic controllers.
InProceedings of the 27th IEEE/ACM International Conference on
Automated Software Engineering, pages 338–341. ACM, 2012.
[7] Sidi Ould Biha. A formal semantics of plc programs in coq. In2011
IEEE 35th Annual Computer Software and Applications Conference,
pages 118–127. IEEE, 2011.
[8] Sandro Bologna, Bernhard Hämmerli, Dimitris Gritzalis, and
Stephen Wolthusen. Critical information infrastructure security ,
2011.
[9] Alvaro A Cárdenas, Saurabh Amin, and Shankar Sastry . Research
challenges for the security of control systems. InHotSec, 2008.
[10] Marco Caselli, Emmanuele Zambon, and Frank Kargl. Sequence-
aware intrusion detection in industrial control systems. InPro-
ceedings of the 1st ACM Workshop on Cyber-Physical System Security,
pages 13–24. ACM, 2015.
[11] Marco Caselli, Emmanuele Zambon, Jonathan Petit, and Frank
Kargl. Modeling message sequences for intrusion detection in
industrial control systems. InInternational Conference on Critical
Infrastructure Protection, pages 49–71. Springer, 2015.
[12] ICS Cert. Incident response/vulnerability coordination in 2014.
[13] Steven Cheung, Bruno Dutertre, Martin Fong, Ulf Lindqvist, Keith
Skinner, and Alfonso Valdes. Using model-based intrusion de-
tection for scada networks. InProceedings of the SCADA security
scientific symposium, volume 46, pages 1–12. Citeseer, 2007.
[14] International Electrotechnical Commission et al.International S-
tandard IEC 61131-3: Programmable Controllers. Part 3: Programming
Languages. IEC, 2003.
[15] Dániel Darvas, Enrique Blanco Vinuela, and Borja Fer-
nández Adiego. Plcverif: A tool to verify plc programs based on
model checking techniques. 2015.
[16] Nicolas Falliere, Liam O Murchu, and Eric Chien. W32. stuxnet
dossier.White paper, Symantec Corp., Security Response, 5(6):29, 2011.
[17] Cheng Feng, Tingting Li, and Deeph Chana. Multi-level anomaly
detection in industrial control systems via package signatures
and lstm networks. In2017 47th Annual IEEE/IFIP International
Conference on Dependable Systems and Networks (DSN), pages 261–
272. IEEE, 2017.
[18] Eric Goetz and Sujeet Shenoi, editors.Critical Infrastructure Pro-
tection, Post-Proceedings of the First Annual IFIP Working Group
11.10 International Conference on Critical Infrastructure Protection,
Dartmouth College, Hanover, New Hampshire, USA, March 19-21,
2007, volume 253 ofIFIP. Springer, 2007.
[19] Dina Hadˇziosmanovi´c, Robin Sommer, Emmanuele Zambon, and
Pieter H Hartel. Through the eye of the plc: semantic security
monitoring for industrial processes. InProceedings of the 30th
Annual Computer Security Applications Conference, pages 126–135.
ACM, 2014.
[20] Ralf Huuck. Semantics and analysis of instruction list programs.
Electronic Notes in Theoretical Computer Science, 115:3–18, 2005.
[21] Sushma Kalle, Nehal Ameen, Hyunguk Yoo, and Irfan Ahmed.
Clik on plcs! attacking control logic with decompilation and
virtual plc. InBinary Analysis Research (BAR) Workshop, Network
and Distributed System Security Symposium (NDSS), 2019.
[22] Anastasis Keliris and Michail Maniatakos. Icsref: A framework
for automated reverse engineering of industrial control systems
binaries.arXiv preprint arXiv:1812.03478, 2018.
[23] Amit Kleinmann and Avishai Wool. Automatic construction of
statechart-based anomaly detection models for multi-threaded industrial control systems.ACM T ransactions on Intelligent Systems
and T echnology (TIST), 8(4):55, 2017.
[24] Eric D Knapp and Joel Thomas Langill.Industrial Network Security:
Securing critical infrastructure networks for smart grid, SCADA, and
other Industrial Control Systems. Syngress, 2014.
[25] Marina Krotofil, Alvaro A Cárdenas, Bradley Manning, and Jason
Larsen. Cps: driving cyber-physical systems to unsafe operating
conditions by timing dos attacks on sensor signals. InProceedings
of the 30th Annual Computer Security Applications Conference, pages
146–155. ACM, 2014.
[26] Marina Krotofil, Jason Larsen, and Dieter Gollmann. The process
matters: Ensuring data veracity in cyber-physical systems. In
Proceedings of the 10th ACM Symposium on Information, Computer
and Communications Security, pages 133–144. ACM, 2015.
[27] Ralph Langner. Stuxnet: Dissecting a cyberwarfare weapon.IEEE
Security & Privacy, 9(3):49–51, 2011.
[28] Junjiao Liu, Libo Yin, Yan Hu, Shichao Lv , and Limin Sun. A
novel intrusion detection algorithm for industrial control systems
based on cnn and process state transition. In2018 IEEE 37th
International Performance Computing and Communications Conference
(IPCCC), pages 1–8. IEEE, 2018.
[29] Stephen McLaughlin and Patrick McDaniel. Sabot: specification-
based payload generation for programmable logic controllers. In
Proceedings of the 2012 ACM conference on Computer and communica-
tions security, pages 439–449. ACM, 2012.
[30] Stephen E McLaughlin. On dynamic malware payloads aimed at
programmable logic controllers. InHotSec, 2011.
[31] Stephen E McLaughlin, Saman A Zonouz, Devin J Pohly , and
Patrick D McDaniel. A trusted safety verifier for process controller
code. InNDSS, volume 14, 2014.
[32] Brian Meixell and Eric Forner. Out of control: Demonstrating
scada exploitation.Black Hat, page 2013, 2013.
[33] Thomas Morris, Rayford Vaughn, and Yoginder Dandass. A
retrofit network intrusion detection system for modbus rtu and
ascii industrial control systems. In2012 45th Hawaii International
Conference on System Sciences, pages 2338–2345. IEEE, 2012.
[34] Matthias Niedermaier, Jan-Ole Malchow, Florian Fischer, Daniel
Marzin, Dominik Merli, V olker Roth, and Alexander V on Bodisco.
You snooze, you lose: Measuring{PLC}cycle times under attacks.
In12th{USENIX}Workshop on Offensive T echnologies ({WOOT}
18), 2018.
[35] Yong Peng, Changqing Jiang, Feng Xie, Zhonghua Dai, Qi Xiong,
and Yang Gao. Industrial control system cybersecurity research.
Journal of T singhua University Science and T echnology, 52(10):1396–
1408, 2012.
[36] Herbert Prähofer, Florian Angerer, Rudolf Ramler, Hermann
Lacheiner, and Friedrich Grillenberger. Opportunities and chal-
lenges of static code analysis of iec 61131-3 programs. InPro-
ceedings of 2012 IEEE 17th International Conference on Emerging
T echnologies & Factory Automation (ETF A 2012), pages 1–8. IEEE,
2012.
[37] Anand Handa Ujjwal Ayyangar Sandeep K Shukla Rohit Negi,
Aneet Dutta. Intrusion detection & prevention in programmable
logic controllers: A model-driven approach. InIEEE International
Conference on Industrial Cyber-Physical Systems (ICPS), pages 1–8.
IEEE, 2020.
[38] Julian Rrushi, Hassan Farhangi, Clay Howey , Kelly Carmichael,
and Joey Dabell. A quantitative evaluation of the target selection
of havex ics malware plugin. InIndustrial Control System Security
(ICSS) Workshop, 2015.
[39] Ahmad-Reza Sadeghi, Christian Wachsmann, and Michael Waid-
ner. Security and privacy challenges in industrial internet of
things. In2015 52nd ACM/EDAC/IEEE Design Automation Con-
ference (DAC), pages 1–6. IEEE, 2015.
[40] Saranyan Senthivel, Shrey Dhungana, Hyunguk Yoo, Irfan
Ahmed, and Vassil Roussev . Denial of engineering operations
attacks in industrial control systems. InProceedings of the Eighth
ACM Conference on Data and Application Security and Privacy, pages
319–329. ACM, 2018.
[41] Konstantin Serebryany , Derek Bruening, Alexander Potapenko,
and Dmitriy Vyukov . Addresssanitizer: A fast address sanity
checker. InPresented as part of the 2012{USENIX}Annual T echnical
Conference ({USENIX}{ATC}12), pages 309–318, 2012.
[42] Stefan Stattelmann, Sebastian Biallas, Bastian Schlich, and Stefan
Kowalewski. Applying static code analysis on industrial controller
code. InProceedings of the 2014 IEEE Emerging T echnology and
Factory Automation (ETF A), pages 1–4. IEEE, 2014.
[43] Keith A Stouffer, Joseph A Falco, and Karen A Scarfone. Sp 800-
82. guide to industrial control systems (ics) security: Supervisory
control and data acquisition (scada) systems, distributed control
systems (dcs), and other control system configurations such as
programmable logic controllers (plc). 2011.
[44] Grigoris Tzokatziou, Leandros Maglaras, and Helge Janicke. In-
secure by design: using human interface devices to exploit scada
systems. InProceedings of the 3rd International Symposium for ICS
& SCADA Cyber Security Research, pages 103–106. BCS Learning &
Development Ltd., 2015.
[45] David I Urbina, Jairo A Giraldo, Alvaro A Cardenas, Nils Ole
Tippenhauer, Junia Valente, Mustafa Faisal, Justin Ruths, Richard
Candell, and Henrik Sandberg. Limiting the impact of stealthy
attacks on industrial control systems. InProceedings of the 2016
ACM SIGSAC Conference on Computer and Communications Security,
pages 1092–1105. ACM, 2016.
[46] Yong Wang, Zhaoyan Xu, Jialong Zhang, Lei Xu, Haopei Wang,
and Guofei Gu. Srid: state relation based intrusion detection for
false data injection attacks in scada. InEuropean Symposium on
Research in Computer Security, pages 401–418. Springer, 2014.
[47] Huan Yang, Liang Cheng, and Mooi Choo Chuah. Detecting
payload attacks on programmable logic controllers (plcs). In2018
IEEE Conference on Communications and Network Security (CNS),
pages 1–9. IEEE, 2018.
[48] Y Yang, K McLaughlin, S Sezer, YB Yuan, and W Huang. Stateful
intrusion detection for iec 60870-5-104 scada security . In2014 IEEE
PES General Meeting— Conference & Exposition, pages 1–5. IEEE,
2014.
[49] Yi Yang, Kieran McLaughlin, Tim Littler, Sakir Sezer, Bernardi
Pranggono, and HF Wang. Intrusion detection system for iec
60870-5-104 based scada networks. In2013 IEEE power & energy
society general meeting, pages 1–5. IEEE, 2013.
[50] Hyunguk Yoo and Irfan Ahmed. Control logic injection attacks on
industrial control systems. InIFIP International Conference on ICT
Systems Security and Privacy Protection, pages 33–48. Springer, 2019.
[51] Man-Ki Yoon and Gabriela F Ciocarlie. Communication pattern
monitoring: Improving the utility of anomaly detection for indus-
trial control systems. InNDSS Workshop on Security of Emerging
Networking T echnologies, 2014.


 浙公网安备 33010602011771号
浙公网安备 33010602011771号