Post-exploitation and Persistence Techniques Against Programmable Logic Controller
一、摘要
从对最近ICS重大事件的调查中可以看出,有针对性的后开发链对于攻击的成功起着至关重要的作用。在获得对系统的初始访问后,通常是通过以前未知(zero-day)或未修补的漏洞、弱凭据或内部协助,应用系统架构的特定知识,以在物理过程中断之前实现系统中的隐形和持久存在。本文中,我们提出了一套针对WAGO PFC200系列PLC的后开发和持久化技术,这将有助于提高对构建在CODESYS(控制器开发系统)运行时变体之上的PLC的隐蔽性和持久性威胁的认识。
二、威胁建模
远程攻击者利用控制器以前未知或未修补的漏洞进行一般攻击。然而,关于特定部署系统和物理过程的初步知识是有限的。威胁行动者通过其中一个远程暴露的接口获得对系统的访问,并寻求系统中的长期秘密持久性,这将允许收集足够的操作信息集,以对物理进程进行有针对性的攻击。
三、攻击方法
目标: 攻击者对系统进行一次性未经授权的访问是为了确保在PLC上长期隐藏恶意负载。这允许对系统及其状态变化进行被动观察,对部署的配置进行指纹识别,并确保将来的远程访问。
技术: 在PLC处于运行状态时,支持这些攻击目标的一种常见方法是在其软件组件中放置一个持久后门。我们将概述攻击周期和系统组件,它们可以执行恶意负载的调用,并且适合放置后门可执行文件。
(一)获取远程访问
未经授权访问场景:管理界面中的漏洞、身份验证缺陷、通过文件上传执行代码、易受攻击的扩展包、利用网络服务。
在未打补丁的系统中,类似于上述场景的漏洞链可使攻击者未经授权访问受影响的PFC200系统。一旦建立了一次性访问,就需要对系统有更具体的了解,以执行攻击后操作并准备对物理进程的攻击。
(二)权限提升及收集信息
权限提升:访问控制系统、特权服务中的漏洞
信息收集:日志记录、运行时配置、控制程序分析、可视化小程序提取
(三)持续化
CBM模块注入、Web组件、进程迁移候选者、通用技术、Crontab记录、终端会话
四、攻击场景
WAGO PFC200控制器运行固件版本03.01.07(13),其中包含攻击者已知的未修补漏洞。远程攻击者通过公开的TCP端口访问WBM服务,并使用身份验证漏洞来获取登录凭据(图1)。
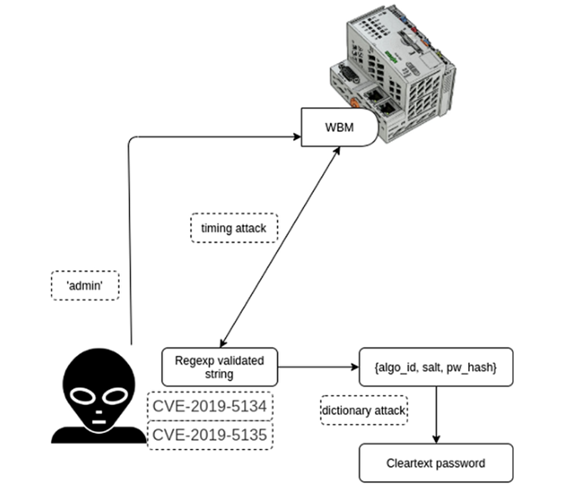
攻击者制作恶意ipk包,并使用远程代码执行漏洞在系统中执行该包,从而将权限提升到超级用户。攻击者使用相同的漏洞将为ARMv7指令集编译的特制后门上传到PLC上的永久分区(图2)。
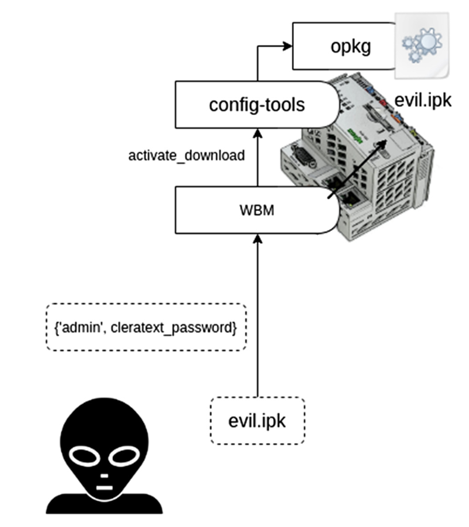
在后攻击期间,攻击者分析位于var/log/wago/wagolog.log和/var/log/messages的日志文件。观察到,系统维护是通过串行接口上的命令行会话在控制器上完成的。为了实现恶意后门的持久性,攻击者在/etc/wago screen prompt.sh中添加一条附加记录,以便在操作员每次登录时调用先前上载的二进制文件(图3)。
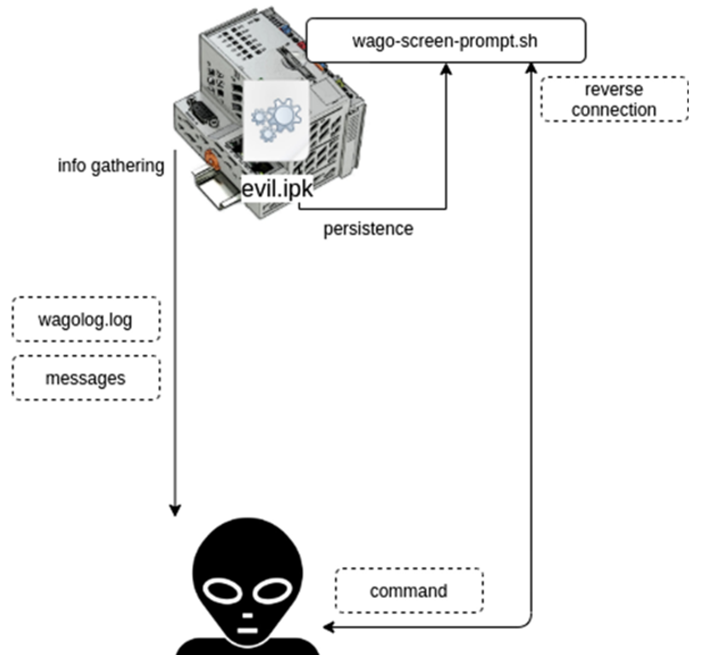
五、结论
在这项工作中,我们为WAGO PFC200系列PLC提出了一套后开发和持久化技术,并制作了攻击场景示例。考虑到持久性链使用的内部系统组件,我们进一步分析了检测和防御选项。
防御和检测:在受影响的PLC上设置持久后门的目的是从长远角度将检测风险降至最低。假设的检测机制可分为以下几类:
- 通用Linux rootkit检测实用程序
- 网络活动异常检测
- 系统行为分析
- 系统内手动调查
我们强调指出,在ICS领域,除了提供渗透系统方法的初始漏洞外,有针对性的攻击后技术在攻击成功中起着至关重要的作用。除了针对PLC的攻击外,这也与广泛的其他ICS设备有关。
1. Abbasi, A., Hashemi, M.: Ghost in the PLC: designing an undetectable pro-
grammable logic controller rootkit via pin control attack, pp. 1–35. Black
Hat, November 2016.https://research.utwente.nl/en/publications/ghost-in-the-
plc-designing-an-undetectable-programmable-logic-con
2. Ahmed, C.M., et al.: Noiseprint: attack detection using sensor and process noise
fingerprint in cyber physical systems. In: Proceedings of the 2018 on Asia Con-
ference on Computer and Communications Security. ASIACCS 2018, pp. 483–497.
Association for Computing Machinery, New York (2018).https://doi.org/10.1145/
3196494.3196532
3. Bytes, A., Adepu, S., Zhou, J.: Towards semantic sensitive feature profiling of
IoT devices. IEEE Internet Things J., (2019).https://doi.org/10.1109/JIOT.2019.
2903739
4. Cardenas, A., Amin, S., Sastry, S.: Secure control: towards survivable cyber-
physical systems. In: 2008 28th International Conference on Distributed Comput-
ing Systems Workshops. ICDCS 2008, pp. 495–500, June 2008
5. Casey, P., Topor, M., Hennessy, E., Alrabaee, S., Aloqaily, M., Boukerche, A.:
Applied comparative evaluation of the metasploit evasion module. In: 2019 IEEE
Symposium on Computers and Communications (ISCC), pp. 1–6 (2019)
6. Castellanos, J.H., Ochoa, M., Zhou, J.: Finding dependencies between cyber-
physical domains for security testing of industrial control systems. ACM, December
2018.https://doi.org/10.1145/3274694.3274745
7. Cobb, P.: German steel mill meltdown: rising stakes in the internet
of things (2015).https://securityintelligence.com/german-steel-mill-meltdown-
rising-stakes-in-the-internet-of-things/
8. Costin, A., Zaddach, J.: Embedded Devices Security and Firmware Reverse
Engineering. ResearchGate, July 2013.https://www.researchgate.net/publication/
259642928EmbeddedDevicesSecurityandFirmwareReverseEngineering
9. Cozzi, E., Graziano, M., Fratantonio, Y., Balzarotti, D.: Understanding Linux mal-
ware. In: 2018 IEEE Symposium on Security and Privacy (SP), pp. 161–175 (2018)
10. Dragos: CRASHOVERRIDE: Analyzing the Malware that Attacks Power Grids—
Dragos, April 2019.https://dragos.com/resource/crashoverride-analyzing-the-
malware-that-attacks-power-grids. Accessed 14 Apr 2019
11. Garcia, L.A., Brasser, F., Cintuglu, M.H., Sadeghi, A.R., Zonouz, S.A.: Hey,
my malware knows physics! Attacking PLCs with physical model aware rootkit.
ResearchGate, January 2017.https://doi.org/10.14722/ndss.2017.23313
12. Govil, N., Agrawal, A., Tippenhauer, N.O.: On ladder logic bombs in industrial
control systems. In: Katsikas, S.K., et al. (eds.) CyberICPS/SECPRE -2017. LNCS,
vol. 10683, pp. 110–126. Springer, Cham (2018).https://doi.org/10.1007/978-3-
319-72817-98
13. Hsiao, S.W., Sun, Y.S., Chen, M.C., Zhang, H.: Cross-level behavioral analysis
for robust early intrusion detection. In: 2010 IEEE International Conference on
Intelligence and Security Informatics (ISI), pp. 95–100. IEEE (2010)
14. Huang, T., Zhou, J., Bytes, A.: ATG: an attack traffic generation tool for security
testing of in-vehicle CAN bus. ResearchGate, pp. 1–6, August 2018.https://doi.
org/10.1145/3230833.3230843
15. IEC 61131–3 industrial control programming standard.https://www.isa.org/
standards-publications/isa-publications/intech-magazine/2012/october
16. Firmware from Rockwell Automation - Software Download, April 2019.https://
www.rockwellautomation.com/rockwellsoftware/support/firmware.page. Accessed
15 Apr 2019
17. Operating System Update for SIMATIC S7–1200 CPU Firmware V3 - ID:
64789124 - Industry Support Siemens, April 2019.https://support.industry.
siemens.com/cs/document/64789124/operating-system-update-for-simatic-s7-
1200-cpu-firmware-v3?dti=0&pnid=13615&lc=en-WW. Accessed 15 Apr 2019
18. Support Packages for the hardware catalog in the TIA Portal (HSP) - ID: 72341852
- Industry Support Siemens, April 2019.https://support.industry.siemens.com/
cs/document/72341852/support-packages-for-the-hardware-catalog-in-the-tia-
portal-(hsp)?dti=0&pnid=13615&lc=en-US. Accessed 15 Apr 2019
19. Keliris, A., Maniatakos, M.: ICSREF: a framework for automated reverse engineer-
ing of industrial control systems binaries. In: The Network and Distributed System
Security Symposium (NDSS) (2019)
20. Krotofil, M., Gollmann, D.: Industrial control systems security: what is happen-
ing?, pp. 664–669. ResearchGate, July 2013.https://doi.org/10.1109/INDIN.2013.
6622963
21. Lee, E.A.: cyber-physical systems: design challenges. Technical report UCB/EECS-
2008-8, EECS Department, University of California, Berkeley, January 2008.
http://www.eecs.berkeley.edu/Pubs/TechRpts/2008/EECS-2008-8.html
22. Lipovsky, R.: New wave of cyber attacks against Ukrainian power industry, January
2016.http://www.welivesecurity.com/2016/01/11
23. Lufkin, D.: Programmable Logic Controllers: A Practical Approach to IEC 61131–3
using CoDeSys (12 2015)
24. McLaughlin, S.: On dynamic malware payloads aimed at programmable logic
controllers, p. 10. ResearchGate, August 2011.https://www.researchgate.net/
publication/262355936Ondynamicmalwarepayloadsaimedatprogrammable
logiccontrollers
25. McLaughlin, S., McDaniel, P.: SABOT: specification-based payload generation
for Programmable Logic Controllers, pp. 439–449. ResearchGate, October 2012.
https://doi.org/10.1145/2382196.2382244
26. McLaughlin, S., Zonouz, S., Pohly, D., McDaniel, P.: A trusted safety verifier for
process controller code. ResearchGate, January 2014.https://doi.org/10.14722/
ndss.2014.23043
27. Mulder, J., Schwartz, M., Berg, M., Van Houten, J., Urrea, J.M., Pease, A.: Analy-
sis of field devices used in industrial control systems. In: Butts, J., Shenoi, S. (eds.)
ICCIP 2012. IAICT, vol. 390, pp. 45–57. Springer, Heidelberg (2012).https://doi.
org/10.1007/978-3-642-35764-04
28. Noergaard, T.: Embedded Systems Architecture: A Comprehensive Guide for
Engineers and Programmers. Newnes (2013).https://books.google.com.sg/books/
about/EmbeddedSystemsArchitecture.html?id=piGhuAAACAAJ&source=kp
bookdescription&rediresc=y
29. Online: Wago-i/o-system codesys 2.3 webvisu password extraction (2019).
https://packetstormsecurity.com/files/127438/WAGO-I-O-SYSTEM-CODESYS-
2.3-WebVisu-Password-Extraction.html
30. Siddiqi, A., Tippenhauer, N.O., Mashima, D., Chen, B.: On practical threat sce-
nario testing in an electric power ICS testbed. In: Proceedings of the Cyber-
Physical System Security Workshop (CPSS), co-located with ASIACCS, June 2018.
https://doi.org/10.1145/3198458.3198461
31. Toolchains - eLinux.org, April 2019.https://elinux.org/Toolchains. Accessed 15
Apr 2019
32. Giraldo, J., Urbina, D., Cardenas, A.A., Tippenhauer, N.O.: Hide and seek: an
architecture for improving attack-visibility in industrial control systems. In: Deng,
R.H., Gauthier-Uma˜na, V., Ochoa, M., Yung, M. (eds.) ACNS 2019. LNCS, vol.
11464, pp. 175–195. Springer, Cham (2019).https://doi.org/10.1007/978-3-030-
21568-29
33. Urias, V., Van Leeuwen, B., Richardson, B.: Supervisory Command and Data
Acquisition (SCADA) system cyber security analysis using a live, virtual, and con-
structive (L VC) testbed. In: 2012 Military Communications Conference - MILCOM
2012, pp. 1–8 (2012)
34. Valentine, S., Farkas, C.: Software security: application-level vulnerabilities in
SCADA systems, pp. 498–499. ResearchGate, August 2011.https://doi.org/10.
1109/IRI.2011.6009603
35. Codesys. The system.https://www.codesys.com/the-system.html
36. Security for controller pfc100/pfc200 v 1.1.0, 5 December 2018.https://www.wago.
com/medias/mxxxxxxxx-CyberSecurity-0en.pdf
37. Wago controllers brochure.https://www.wago.com/infomaterial/pdf/60386168.
pdf
38. Wago ethernet web-based management authentication bypass vulnerability.
https://ics-cert.us-cert.gov/advisories/ICSA-16-357-02
39. (May 2014).https://www.wago.com/infomaterial/pdf/51236524.pdf. Accessed 15
Apr 2019
40. Vulnerabilities in W AGO PFC 200 Series (2017).https://sec-consult.com/en/blog/
advisories/wago-pfc-200-series-critical-codesys-vulnerabilities/index.html
41. (Apr 2019).https://www.wago.com/sg/download/public/IoT-Brosch%25C3
%25BCre/AU-NA-DE-DE-FP-180827001%2BIoT-Box%2BBrochureweb.pdf.
Accessed 15 Apr 2019
42. Codesys device directory, April 2019.https://devices.codesys.com/device-
directory.html. Accessed 15 Apr 2019
43. W AGO Global—swreglinuxc, April 2019.https://www.wago.com/global/d/
swreglinuxc. Accessed 15 Apr 2019
44. W AGO—Controllers with Embedded Linux, April 2019.https://www.wago.com/
sg/embedded-linux. Accessed 15 Apr 2019
45. W AGO—IoT PLC Controllers with MQTT Protocol for Industry 4.0, April 2019.
https://www.wago.com/sg/automation-technology/plc-mqtt-iot. Accessed 15 Apr
2019
46. W AGO—WebVisu, April 2019.https://www.wago.com/global/automation-
technology/discover-software/webvisu. Accessed 15 Apr 2019
47. Talos Vulnerability Report 2019–0923 (2020).https://talosintelligence.com/
vulnerabilityreports/TALOS-2019-0923
48. Talos Vulnerability Report 2019–0950 (2020).https://talosintelligence.com/
vulnerabilityreports/TALOS-2019-0950
49. Talos Vulnerability Report 2019–0961 (2020).https://talosintelligence.com/
vulnerabilityreports/TALOS-2019-0961
50. Talos Vulnerability Report 2019–0962 (2020).https://talosintelligence.com/
vulnerabilityreports/TALOS-2019-0962
51. Technical basics: Preempt RT (2020).https://wiki.linuxfoundation.org/realtime/
documentation/technicalbasics/start
52. W AGO e!Cockpit authentication hard-coded encryption key vulnerability (2020).
https://talosintelligence.com/vulnerabilityreports/TALOS-2019-0898
53. W AGO e!COCKPIT Firmware Downgrade Vulnerability (2020).https://
talosintelligence.com/vulnerabilityreports/TALOS-2019-0951
54. W AGO PFC 200 Web-Based Management (WBM) Code Execution Vulnerability
(2020).https://talosintelligence.com/vulnerabilityreports/TALOS-2020-1010
55. W AGO PFC100/200 Web-Based Management (WBM) FastCGI configuration
insufficient resource pool denial of service (2020).https://talosintelligence.com/
vulnerabilityreports/TALOS-2019-0939
56. W AGO PFC200 Cloud Connectivity Multiple Command Injection Vulnerabilities
(2020).https://talosintelligence.com/vulnerabilityreports/TALOS-2019-0948
57. W AGO PFC200 Cloud Connectivity Remote Code Execution Vulnerability (2020).
https://talosintelligence.com/vulnerabilityreports/TALOS-2019-0954
58. W AGO PFC200 iocheckd service “I/O-Check” getcouplerdetails remote code exe-
cution vulnerability (2020).https://talosintelligence.com/vulnerabilityreports/
TALOS-2019-0864
59. W AGO PFC200 iocheckd service “I/O-Check” ReadPCBManuNum remote
code execution vulnerability (2020).https://talosintelligence.com/vulnerability
reports/TALOS-2019-0873
60. W AGO PFC200 iocheckd service “I/O-Check” ReadPCBManuNum remote
code execution vulnerability (2020).https://talosintelligence.com/vulnerability
reports/TALOS-2019-0874
61. W AGO PFC200 iocheckd service “I/O-Check” ReadPCBManuNum remote
code execution vulnerability (2020).https://talosintelligence.com/vulnerability
reports/TALOS-2019-0863
62. W AGO PFC200 iocheckd service “I/O-Check” ReadPSN remote code execution
vulnerability (2020).https://talosintelligence.com/vulnerabilityreports/TALOS-
2019-0871
63. Weinberger, S.: Computer security: is this the start of cyberwarfare? Nature174,
142–145 (2011)
64. Zonouz, S., Rrushi, J., McLaughlin, S.: Detecting industrial control malware using
automated PLC code analytics. IEEE Secur. Priv. Mag.12(6), 40–47 (2014).
https://doi.org/10.1109/MSP.2014.113


