Introducing a forensics data type taxonomy of acquirable artefacts from PLCs
介绍PLC可以获取人工的取证数据类型分类法
一、摘要
本文研究了存储在PLC上的特定数据类型,并描述了基于可获取人工的取证数据类型分类法。数据采集测试主要使用第三方通信库进行,该通信库利用PLC专有的工业通信协议来利用存储在每个被测PLC内存结构中的数据,对来自两个制造商的三个不同PLC进行了检查。
二、介绍
本文的贡献可以概括为:
1) 检查和定义可从PLC获取的数据,并确定这些组件中包含的特定信息;
2) 检查PLC供应商和模型之间可获取数据的差异;
3) 提供PLC数据类型分类方法,为ICS取证能力开发人员和取证调查人员提供多种优势。
三、实验评估
(一)实验台设置
我们选择了来自两个不同制造商的三个PLC;配备345-1 Profinet通信处理器的西门子S7-300 315-2 DP、西门子S7-1500 1517-3 PN/DP CPU和罗克韦尔艾伦布拉德利ControlLogix 1756-L71/B。选择这三个PLC使我们能够利用二维可获取的数据来评估差异;1) 比较PLC供应商(西门子和罗克韦尔)2) 比较同一供应商(西门子S7-300和S7-1500)的PLC型号,选择这两个制造商是因为它们在全球PLC市场中占有最大份额,然后对从每个PLC获取的数据源进行详细评估。

实验室试验台设置如图1所示,三个PLC保持不变。在西门子和罗克韦尔艾伦布拉德利PLC编程环境中设置了一个工作站;分别是西门子全集成自动化(TIA)门户网站和罗克韦尔工作室5000。为每个PLC创建了一个项目,包含一个简单的梯形图逻辑程序和PLC设置的硬件配置,包括CPU模型和PLC使用的任何通信模块。然后将这些项目下载到各自的PLC,并允许其运行至少一个小时,以便在PLC内存中生成数据,这将生成类似于ICS内实时运行流程的数据。工作站还包含三个第三方开源通信库,用于从PLC获取数据。重要的是要注意,这些开源库的开发并没有考虑取证,也不一定使用可靠的取证方法从PLC捕获数据,他们的主要贡献是提供了一个框架,该框架可用于从PLC的板载内存轮询数据,而无需根据取证有效性标准应用过滤器。
(二)取证数据分类法

通过分析从两个西门子PLC和AB ControlLogix PLC获取的数据,设计并定义了四种数据类型分类,Variable content data; PLC application code; PLC meta-data; Device diagnostics and logs。在每种数据类型中,还识别出若干人为制造的数据。这些在图2所示的PLC取证数据类型分类法中进行了说明。
(三)PLC取证数据类型

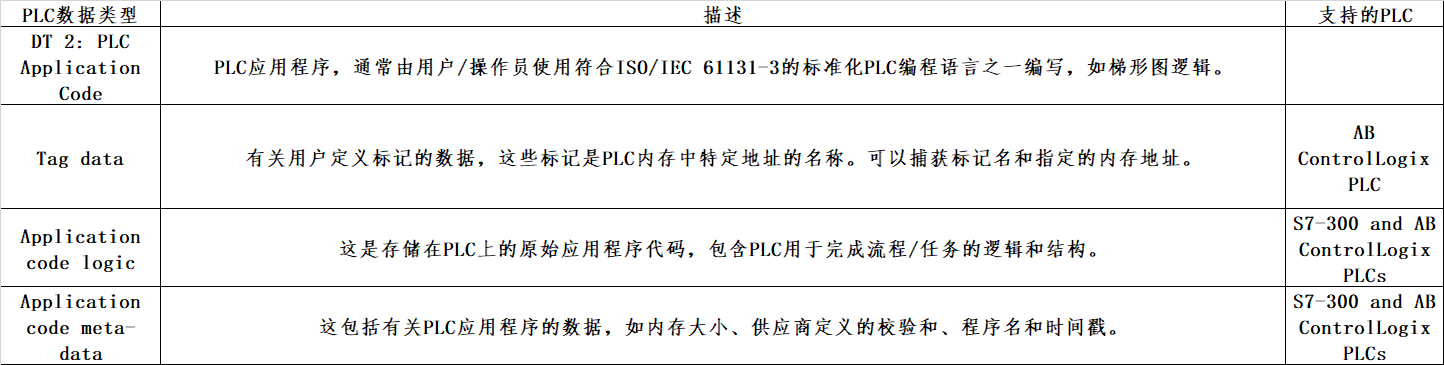
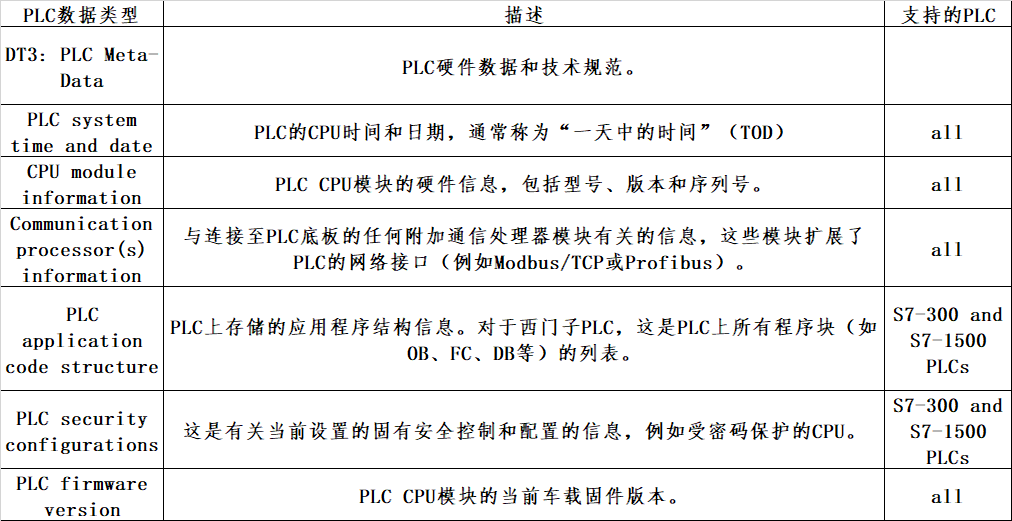
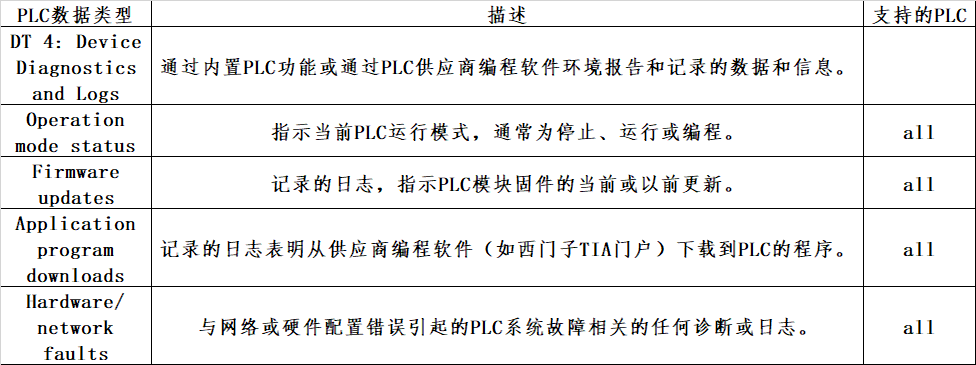
四、总结
PLC威胁评估确实强调了获取某些PLC取证数据类型的重要性,这项研究的下一个阶段将涉及探索个人定义的人为制造的数据的重要性。此外,未来的工作将探索将这些数据类型的定义形式化为结构,以检查是否可以在多个PLC之间建立公共模型和模式。更广泛地说,本文中描述的为PLC开发取证数据分类法的方法可应用于其他可编程和可配置的ICS组件,如HMI和变速驱动器(VSD)。
[1] ISO/IEC 27037.: Information technology - Security techniques - Guidelines for identifICSation, collection, acquisition and preservation of digital evidence, 2012.
[2] I. Ahmed, S. Obermeier, M. Naedele and G. RICShard III, "SCADA
Systems: Challenges for ForensICS Investigators", Computer, vol. 45,
no. 12, pp. 44-51, 2012. Available: 10.1109/mc.2012.325.
[3] T. Spyridopoulos, J. May and T. Tryfonas, "Incident Analysis & Digital ForensICS in SCADA and Industrial Control Systems", 8th IET International System Safety Conference incorporating the Cyber Security Conference 2013, 2013.
[4] IEC 61131 “Programmable Controllers”, 2019.
[5] "LogICS | PLCopen", PLCopen.org, 2019. [Online]. Available: https://PLCopen.org/technICSal-activities/logICS. [Accessed: 06- Jul- 2019].
[6] G. Denton, F. Karpisek, F. Breitinger, and I. Baggili, “Leveraging the SRTP protocol for over-the-network memory acquisition of a GE Fanuc Series 90-30”, Digital Investigation, vol. 22, pp. S26–S38, Aug. 2017.
[7] S. Senthivel, I. Ahmed, and V. Roussev, “SCADA network forensICS of the PCCC protocol”, Digital Investigation, vol. 22, pp. S57–S65, Aug. 2017 [Online]. Available: http://dx.doi.org/10.1016/j.diin.2017.06.012
[8] I. Ahmed, S. Obermeier, S. Sudhakaran and V. Roussev,
"Programmable LogICS Controller ForensICS", IEEE Security &
Privacy, vol. 15, no. 6, pp. 18-24, 2017.
[9] K. Yau, K. Chow and S. Yiu, "A ForensICS Logging System for Siemens Programmable LogICS Controllers", Advances in Digital ForensICS XIV, pp. 331-349, 2018. Available: 10.1007/978-3-319-99277-8_18
[10] A. Iqbal, M. Ekstedt and H. Alobaidli, "Digital ForensICS Readiness in CritICSal Infrastructures: A Case of Substation Automation in the Power Sector", Lecture Notes of the Institute for Computer Sciences, Social InformatICS and TelecommunICSations Engineering, pp. 117-129, 2018.
[11] J. Stirland, K. Jones, H. JanICSke and T. Wu, "Developing cyber forensICS for SCADA industrial control systems", in International Conference on Information Security and Cyber ForensICS, Kuala Terengganu, Malaysia, 2014.
[12] P. Eden, P. Burnap, A. Blyth, K. Jones, H. Soulsby, and Y. Cherdantseva, ‘A ForensICS Taxonomy of SCADA Systems and Approach to Incident Response’, in 3rd International Symposium forICS & SCADA Cyber Security Research 2015, 2015 [Online]. Available: http://dx.doi.org/10.14236/ewICS/ICS2015.5
[13] R. Altschaffel, M. Hildebrandt, S. Kiltz and J. Dittmann, "Digital ForensICS in Industrial Control Systems", Lecture Notes in Computer Science, pp. 128-136, 2019.
[14] A. Robles-Durazno, N. Moradpoor, J. McWhinnie, G. Russell and I. Maneru-Marin, "PLC memory attack detection and response in a clean water supply system", International Journal of CritICSal Infrastructure Protection, vol. 26, p. 100300, 2019. Available: 10.1016/j.ijcip.2019.05.003
[15] S. Kalle, N. Ameen, H. Yoo and I. Ahmed, "CLIK on PLCs! Attacking Control LogICS with Decompilation and Virtual PLC", Proceedings 2019 Workshop on Binary Analysis Research, 2019. Available: 10.14722/bar.2019.23074
[16] A. Abbasi, M. Hashemi, "Ghost in the ple: Designing an undetectable programmable logICS controller rootkit via pin control attack", Black Hat Europe 2016, pp. 1-35, 2016.
[17] H. Yoo and I. Ahmed, "Control LogICS Injection Attacks on Industrial Control Systems", ICST Systems Security and Privacy Protection, pp. 33-48, 2019. Available: 10.1007/978-3-030-22312-0_3
[18] N. Aloui, Industrial control systems dynamICS code injection, presented at GreHack, 2015.
[19] D. Formby, S. Durbha, R. Beyah, Out of Control: Ransomware for Industrial Control Systems, 2017, [online] Available: http://www.cap.gatech.edu/PLCransomware.pdf.
[20] Z. Basnight, J. Butts, J. Lopez and T. Dube, "Firmware modifICSation attacks on programmable logICS controllers", International Journal of CritICSal Infrastructure Protection, vol. 6, no. 2, pp. 76-84, 2013. Available: 10.1016/j.ijcip.2013.04.004
[21] D. Beresford, “Exploiting Siemens SimatICS S7 PLCs”, im Black Hat USA+2011, Las Vegas, NV, USA, 3-4 Aug. 2011. [Online] Availiable: https://media.blackhat.com/bh-us-
11/Beresford/BHUS11BeresfordS7PLCsWP.pdf
[22] "Worldwide - PLC market share by manufacturer 2017 |
Statista", Statista, 2017. [Online]. Available:
https://www.statista.com/statistICS/897201/global-PLC-market-share-by-manufacturer/. [Accessed: 15- Oct- 2019].
[23] R. M. van der Knijff, “Control systems/SCADA forensICS, what’s the difference?”, Digital Investigation, vol. 11, no. 3, pp. 160–174, Sep. 2014 [Online]. Available: http://dx.doi.org/10.1016/j.diin.2014.06.007
[24] US-CERT.: Malware Analysis Report - MAR-17-352-01 HatMan—
Safety System Targeted Malware (TRITON/TRISIS), Update B,
Feburary 2019. [Online] Availiable: https://www.us-
cert.gov/sites/default/files/documents/MAR-17-352-
01%20HatMan%20-%20Safety%20System%20Targeted%20Malware%20%28Update%20B%29.pdf
[25] N. Falliere, L. O’Murchu and E. Chien, “W32.Stuxnet Dossier”, Symantec. United States of AmerICSa, February 2011. [Online] Available:
https://www.symantec.com/content/en/us/enterprise/media/security_r
esponse/whitepapers/w32_stuxnet_dossier.pdf
[26] D. Nardella, "Snap7 Homepage", Snap7.sourceforge.net, 2019. [Online]. Available: http://snap7.sourceforge.net. [Accessed: 5- Jul- 2019].
[27] “Nodes7", npm, 2019. [Online]. Available: https://www.npmjs.com/package/nodes7. [Accessed: 25- Aug- 2019].
[28] “Pylogix”, 2019. [Online]. Availiable: https://pypi.org/project/pylogix/
[29] Siemens, “Security with SIMATICS controllers”, V2.0, 2016. [Online]
Availiable:https://support.industry.siemens.com/cs/document/77431846/security-with-simatICS-s7-controllers?dti=0&lc=en-WW
[30] A. Wedgbury and K. Jones, “Automated Asset Discovery in Industrial Control Systems – Exploring the Problem”, 3rd International Symposium for ICS & SCADA Cyber Security Research, 2015.
[31] ENISA, "Can we learn from SCADA securiy incidents?", October 2013. London [Online] Availiable: https://www.enisa.europa.eu/publICSations/can-we-learn-from-scada-
security-incidents


 浙公网安备 33010602011771号
浙公网安备 33010602011771号