All Your PLCs Belong to Me: ICS Ransomware Is Realistic
你所有的PLC都属于我:ICS勒索软件是现实的
一、摘要
我们介绍了ICS-BROCK,一个成熟的ICS勒索软件,它可以破坏现实世界。为了演示ICS-BROCK的功能,我们使用西门子S7-300 PLC(ICSs中使用最广泛的设备之一)构建了一个真实的水处理环境。实验结果证明了在实际环境中发起ICS勒索软件攻击的可行性。最后,我们对ICS勒索软件提出了一些建议,以帮助今后的研究和防御。
二、介绍
现有的ICS勒索软件研究大多是概念性的,尚未克服上述所有挑战。例如,公共文献没有报道任何ICS勒索软件能够突破物理隔离并保持ICS稳定。如何构建能够危害现实世界ICS的ICS勒索软件尚不清楚。我们的研究填补了这一空白。
为了使研究具体化,我们在实际的水处理环境中演示了具体的攻击方法,该环境使用西门子S7-300 PLC,这是ICS中使用最广泛的设备类型之一。我们执行详细的协议逆向工程分析,并演示如何在不影响PLC扫描周期的情况下编写恶意控制逻辑程序,如逻辑炸弹。
我们的实现构建了一个ICS勒索软件ICSBROCK,它可以在监控层和PLC上完成勒索软件攻击。在监控层,ICSBROCK扫描本地网络,查找PLC和PC等设备。在PC上,ICS-BROCK像传统勒索软件一样加密文件和数据。在PLC上,ICS-BROCK锁定PLC并注入逻辑炸弹。除设备类型外,所有操作都可以在没有任何预先信息的情况下完成。我们之所以需要设备类型,是因为不同的PLC与ICS协议具有不同的通信细节。
我们作出以下贡献。
• 我们构建了第一个成熟的ICS勒索软件攻击ICS-BROCK,它克服了ICS勒索软件面临的所有独特挑战。
• 与现有的理论ICS勒索软件相比,ICSBROCK能够以较少的信息完成勒索攻击,更接近真实的攻击场景。
• 我们演示了对集成最广泛使用的PLC设备类型之一的真实水处理系统的攻击。我们对PLC的通信协议和加密算法进行了详细的逆向工程分析。
• 对于监控计算机上的勒索软件攻击,我们优化了传统勒索软件的攻击方法,以提高效率和抵抗逆向工程分析。
• 我们说明了如何在不影响ICS稳定性的情况下注入逻辑炸弹,这是现实ICS勒索软件的关键要求。
三、系统模型和威胁模型
(一)系统模型
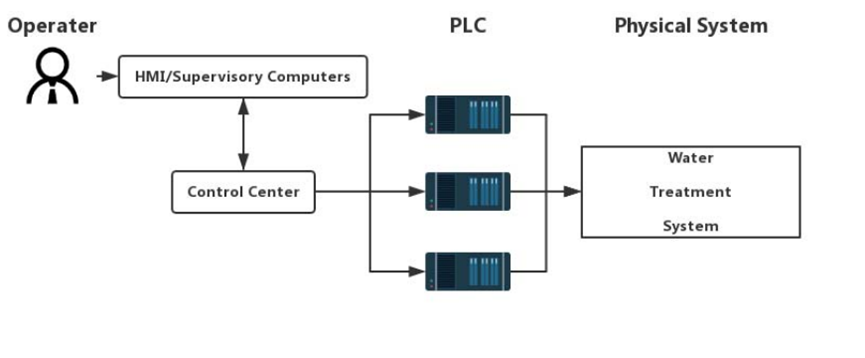
为了证明ICS-BROCK的能力,我们构建了一个水处理系统。本系统主要包括以下模块:上位机下载和编辑PLC程序;HMI主要用于水处理过程中的具体操作。电源用于向整个ICS供电,提供能量;PLC和其他工业控制设备是ICS的主要功能部件,用于模拟整个自来水处理过程。系统模型如图1所示。
(二)威胁模型
在真实ICS环境中成功的ICS勒索软件应满足以下要求。
-
隐身。隐身的目的是尽快完成勒索软件攻击,并且不被发现。在现实世界中,生产环境非常复杂,操作员几乎总是用HMI监控ICS状态。因此,如果攻击者想要快速有效地完成攻击,必须具备隐蔽性。
-
多终端攻击。ICS不仅包括工业设备,如PLC、RTU等,还包括PC,如监控计算机。现有的工业勒索软件主要针对PC机,而忽略了工业设备,这也是其他工业勒索软件对ICS影响有限的原因。
-
低成本。对于经验丰富的攻击者,较低的攻击成本通常意味着较高的攻击利润。目标ICS的信息收集非常重要,但由于物理隔离意味着更高的成本,因此一直很困难。
在勒索软件的传播中,我们更关注如何突破ICS的物理隔离,这是ICS的主要保护方法。在这项工作中,我们提出了一种可能的攻击方法,改进了传统的ferry攻击方法,并使用BadUSB作为攻击载体。BadUSB的攻击过程如图2所示。
四、实验评估
我们选择西门子S7-300PLC作为研究对象,S7-300采用的通信协议为S7comm协议,这是西门子开发的专用ICS协议。ICS-BROCK的大多数操作将基于S7comm协议,例如编写恶意代码和锁定PLC。ICS-BROCK的主要模块如下。
- 漏洞检测
- PLC检测
- 锁定PLC
- 逻辑炸弹
ICS-BROCK将使用随机生成的对称密钥加密文件。加密完成后,对称密钥将由公钥和清除内存数据加密。由于对称密钥是在加密过程中随机生成的,因此该攻击方法可以有效抵抗逆向分析。毕竟,时间越短越好。收到付款后,攻击者将使用私钥解密密钥,并将其与解密程序一起发送给受害者。
(一)评估指标
1. PLC评估
在计划时间内,ICSBROCK不会对ICS环境产生任何影响,因此PLC的评估主要是检测ICSBROCK是否会对生产环境产生影响。检测生产环境的影响,主要从两个方面:执行时间和PLC内存消耗。
2.监控计算机评估
与其他传统勒索软件不同,ICS-BROCK主要关注ICS设备。但监控层也是攻击目标。我们将ICS-BROCK与一些知名勒索软件进行了比较,由于ICS环境的特点,监控计算机的性能总是很差,硬件如下表所示,结果如图3所示。
(二)攻击实验
在建立水处理环境并评估ICS-BROCK后,我们在ICS环境中进行了勒索软件攻击,以测试ICS-BROCK的实战能力。具体过程如图4所示。
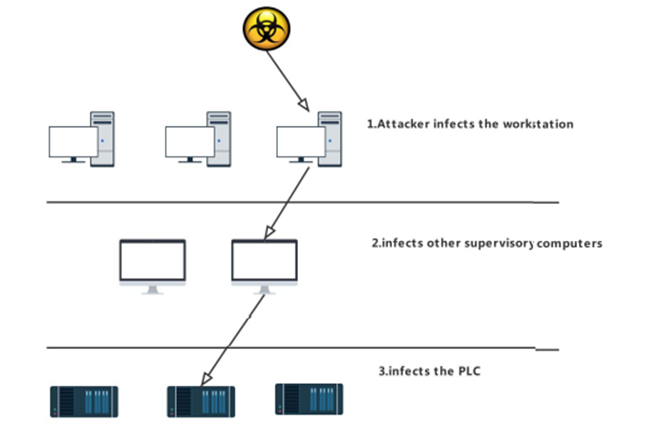
我们通过BadUSB在工作站感染ICS。ICS-BROCK将自动执行进一步的攻击,感染其他监控计算机,最后将逻辑炸弹写入PLC并锁定。
五、结论
我们介绍了第一个成熟的ICS勒索软件ICSBROCK,它可以在不影响ICS设备稳定性的情况下将逻辑炸弹悄悄地注入ICS设备。唯一需要的信息是PLC设备类型,它解决了物理隔离问题。并且,我们构建了一个真正的水处理环境,它采用了应用最广泛的PLC类型之一,我们举例说明了协议和入侵过程的逆向工程等全部细节。评估表明,ICS-BROCK能够成功地对ICS进行妥协。
[1] N. Falliere, L. O. Murchu, and E. Chien, “W32. stuxnet dossier,”White
paper , Symantec Corp., Security Response, vol. 5, no. 6, p. 29, 2011.
[2] F.-S. Labs, “Blackenergy & quedagh: The convergence of crimeware
and apt attacks.”
[3] N. Falliere, L. OMurchu, and E. Chien, “W32. duqu: The precursor to
the next stuxnet,”Symantec Security Response, vol. 4, 2011.
[4] J. Rrushi, H. Farhangi, C. Howey, K. Carmichael, and J. Dabell, “A
quantitative evaluation of the target selection of havex ics malware
plugin,” inIndustrial Control System Security (ICSS) Workshop, 2015.
[5] B. Zhu and S. Sastry, “Scada-specific intrusion detection/prevention
systems: a survey and taxonomy,” inProceedings of the 1st workshop
on secure control systems (SCS), vol. 11, 2010, p. 7.
[6] W. Bolton,Programmable logic controllers. Newnes, 2015.
[7] J. A. Herrera Silva, L. I. Barona López, V . Caraguay, Á. Leonardo,
and M. Hernández-Álvarez, “A survey on situational awareness of
ransomware attacks—detection and prevention parameters,”Remote
Sensing, vol. 11, no. 10, p. 1168, 2019.
[8] D.Bisson, “Half of american ransomware victims have paid the ransom,
reveals study.”http://www.tripwire.com/state-of-security/latest-security-
news/23/.
[9] Trend Micro, “Boosting Impact for Profit: Evolv-
ing Ransomware Techniques for Targeted Attacks.”
https://www.trendmicro.com/enus/research/20/i/boosting-impact-
for-profit-evolving-ransomware-techniques-for-targeted-attacks.html,
2020.
[10] OAIC, “Rapid detection, assessment and notification critical in
data breaches.”https://www.oaic.gov.au/updates/news-and-media/rapid-
detection-assessment-and-notification-critical-in-data-breaches/, 2020.
[11] Anna Delaney, “Analysis: Why Ransomware Gangs Getting Bigger
Payoffs.”https://www.databreachtoday.com/interviews/analysis-
ransomware-gangs-getting-bigger-payoffs-i-4752, 2020.
[12] Eric Avena, “Defending networks against human-operated ransomware.”
https://techcommunity.microsoft.com/t5/microsoft-defender-for-
endpoint/defending-networks-against-human-operated-ransomware/ba-
p/1384282, 2020.
[13] D. Formby, S. Durbha, and R. Beyah, “Out of control: Ransomware for
industrial control systems,”RSA, 2017.
[14] S. Amini, H. Mohsenian-Rad, and F. Pasqualetti, “Dynamic load altering
attacks in smart grid,” inInnovative Smart Grid Technologies Conference
(ISGT), 2015 IEEE Power & Energy Society. IEEE, 2015, pp. 1–5.
[15] A. Abbasi and M. Hashemi, “Ghost in the plc designing an undetectable
programmable logic controller rootkit via pin control attack,”Black Hat
Europe, pp. 1–35, 2016.
[16] K. T. Erickson, “Programmable logic controllers,”IEEE potentials,
vol. 15, no. 1, pp. 14–17, 1996.
[17] S. Etigowni, D. J. Tian, G. Hernandez, S. Zonouz, and K. Butler, “Cpac:
securing critical infrastructure with cyber-physical access control,” in
Proceedings of the 32nd Annual Conference on Computer Security
Applications. ACM, 2016, pp. 139–152.
[18] D. Formby, P . Srinivasan, A. Leonard, J. Rogers, and R. A. Beyah,
“Who’s in control of your control system? device fingerprinting for
cyber-physical systems.” inNDSS, 2016.
[19] S. Cheung, B. Dutertre, M. Fong, U. Lindqvist, K. Skinner, and
A. V aldes, “Using model-based intrusion detection for scada networks,”
inProceedings of the SCADA security scientific symposium, vol. 46.
Citeseer, 2007, pp. 1–12.
[20] W. A. Arbaugh, D. J. Farber, and J. M. Smith, “A secure and reliable
bootstrap architecture,” inSecurity and Privacy, 1997. Proceedings.,
1997 IEEE Symposium on. IEEE, 1997, pp. 65–71.
[21] M. Rocchetto and N. O. Tippenhauer, “On attacker models and profiles
for cyber-physical systems,” inEuropean Symposium on Research in
Computer Security. Springer, 2016, pp. 427–449.
[22] D. Beresford, “Exploiting siemens simatic s7 plcs,”Black Hat USA,
vol. 16, no. 2, pp. 723–733, 2011.
[23] R. Spenneberg, M. Brüggemann, and H. Schwartke, “Plc-blaster: A
worm living solely in the plc,”Black Hat Asia (p. N/A), 2016.
[24] J. Rrushi, H. Farhangi, C. Howey, K. Carmichael, and J. Dabell, “A
quantitative evaluation of the target selection of havex ics malware
plugin,” inIndustrial Control System Security (ICSS) Workshop, 2015.
[25] K. Nohl and J. Lell, “Badusb–on accessories that turn evil,”Black Hat
USA, 2014.
[26] Z. Basnight, J. Butts, J. Lopez Jr, and T. Dube, “Firmware modification
attacks on programmable logic controllers,”International Journal of
Critical Infrastructure Protection, vol. 6, no. 2, pp. 76–84, 2013.
[27] A. Gomez-Exposito, A. J. Conejo, and C. Canizares,Electric energy
systems: analysis and operation. CRC press, 2018.
[28] G. Prytz, “A performance analysis of ethercat and profinet irt,” in
Emerging Technologies and Factory Automation, 2008. ETF A 2008.
IEEE International Conference on. IEEE, 2008, pp. 408–415.
[29] J. Narayan, S. K. Shukla, and T. C. Clancy, “A survey of automatic
protocol reverse engineering tools,”ACM Computing Surveys (CSUR),
vol. 48, no. 3, p. 40, 2016.
[30] M. Majdalawieh, F. Parisi-Presicce, and D. Wijesekera, “Dnpsec: Dis-
tributed network protocol version 3 (dnp3) security framework,” in
Advances in Computer , Information, and Systems Sciences, and Engi-
neering. Springer, 2007, pp. 227–234.
[31] L. Garcia, F. Brasser, M. H. Cintuglu, A.-R. Sadeghi, O. A. Mohammed,
and S. A. Zonouz, “Hey, my malware knows physics! attacking plcs with
physical model aware rootkit.” inNDSS, 2017.
[32] M. Bellare, A. Desai, E. Jokipii, and P . Rogaway, “A concrete security
treatment of symmetric encryption,” inF oundations of Computer Sci-
ence, 1997. Proceedings., 38th Annual Symposium on. IEEE, 1997,
pp. 394–403.
[33] N. Govil, A. Agrawal, and N. O. Tippenhauer, “On ladder logic bombs
in industrial control systems,” inComputer Security. Springer, 2017,
pp. 110–126.
[34] K. Heinz and A. John,IEC 61131-3: programming industrial automa-
tion systems: concepts and programming languages, requirements for
programming systems, aids to decision-making tools. Springer.
[35] J. Mulder, M. Schwartz, M. Berg, J. R. V an Houten, J. Mario, M. A. K.
Urrea, A. A. Clements, and J. Jacob, “Weaselboard: zero-day exploit de-
tection for programmable logic controllers,”Sandia report SAND2013-
8274, Sandia national laboratories Google Scholar, 2013.
[36] Emsisoft, “Ransomware statistics for 2019: Q2 to q3 report,” Web-
site, 2019,https://blog.emsisoft.com/en/34335/ransomware-statistics-
for-2019-q2-to-q3-report/.
[37] F. Pasqualetti, F. Dörfler, and F. Bullo, “Cyber-physical attacks in power
networks: Models, fundamental limitations and monitor design,” in
Decision and Control and European Control Conference (CDC-ECC),
2011 50th IEEE Conference on. IEEE, 2011, pp. 2195–2201.
[38] R. Richardson and M. North, “Ransomware: Evolution, mitigation and
prevention,”International Management Review, vol. 13, no. 1, pp. 10–
21, 2017.
[39] S. Zonouz, C. M. Davis, K. R. Davis, R. Berthier, R. B. Bobba, and
W. H. Sanders, “Socca: A security-oriented cyber-physical contingency
analysis in power infrastructures,”IEEE Transactions on Smart Grid,
vol. 5, no. 1, pp. 3–13, 2013.
[40] K. R. Davis, C. M. Davis, S. A. Zonouz, R. B. Bobba, R. Berthier,
L. Garcia, and P . W. Sauer, “A cyber-physical modeling and assessment
framework for power grid infrastructures,”IEEE Transactions on smart
grid, vol. 6, no. 5, pp. 2464–2475, 2015.
[41] S. Zonouz, K. M. Rogers, R. Berthier, R. B. Bobba, W. H. Sanders, and
T. J. Overbye, “Scpse: Security-oriented cyber-physical state estimation
for power grid critical infrastructures,”IEEE Transactions on Smart
Grid, vol. 3, no. 4, pp. 1790–1799, 2012.
[42] S. Etigowni, D. J. Tian, G. Hernandez, S. Zonouz, and K. Butler, “Cpac:
securing critical infrastructure with cyber-physical access control,” in
Proceedings of the 32nd Annual Conference on Computer Security
Applications. ACM, 2016, pp. 139–152.
[43] S. E. McLaughlin, S. A. Zonouz, D. J. Pohly, and P . D. McDaniel, “A
trusted safety verifier for process controller code.” inNDSS, vol. 14,
2014.
[44] S. Zonouz, J. Rrushi, and S. McLaughlin, “Detecting industrial control
malware using automated plc code analytics,”IEEE Security & Privacy,
vol. 12, no. 6, pp. 40–47, 2014.
[45] J. Mulder, M. Schwartz, M. Berg, J. R. V an Houten, J. Mario, M. A. K.
Urrea, A. A. Clements, and J. Jacob, “Weaselboard: zero-day exploit de-
tection for programmable logic controllers,”Sandia report SAND2013-
8274, Sandia national laboratories, 2013.
[46] J. Reeves,Autoscopy Jr .: Intrusion detection for embedded control
systems. Dartmouth College, 2011.
[47] A. Hammill, “The rise and wrath of ransomware and what it means for
society,” Ph.D. dissertation, Utica College, 2017.
[48] J. Klick, S. Lau, D. Marzin, J.-O. Malchow, and V . Roth, “Internet-facing
plcs-a new back orifice,”Blackhat USA, pp. 22–26, 2015.
[49] C. D. Schuett, “Programmable logic controller modification attacks for
use in detection analysis,” AIR FORCE INSTITUTE OF TECHNOL-
OGY WRIGHT-PATTERSON AFB OH GRADUATE SCHOOL, Tech.
Rep., 2014.
[50] K. Eldefrawy, G. Tsudik, A. Francillon, and D. Perito, “Smart: Secure
and minimal architecture for (establishing dynamic) root of trust.” in
NDSS, vol. 12, 2012, pp. 1–15.


