OpenLDAP搭建
1,安装组件,开启服务。
yum install openldap-servers openldap-clients
systemctl start slapd
systemctl enable slapd
2,查看进程与服务端口:
ps xua|grep slapd
netstat -lnptp
3,在OpenLDAP server上执行如下操作,设置ldap服务密码。
#slappasswd
#{输入密码:Passw0rd}
{SSHA}QGtU8gBpI98gwBhzaLDanpAwWAeV1okQ
4,ldap服务的全局配置文件存放路径为"/etc/openldap/slapd.d/"
cd /etc/openldap/slapd.d/
cd cn\=config
5,添加密码命令和内容,添加密码其实是对文件olcDatabase={0}config.ldif进行修改
①事前查看:cat olcDatabase\=\{0\}config.ldif
②添加:
cat << EOF |ldapadd -Y EXTERNAL -H ldapi:///
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}QGtU8gBpI98gwBhzaLDanpAwWAeV1okQ
EOF
或者将修改的内容保存到一个文件中,然后通过命令ldapadd -Y EXTERANL -H ldapi:/// -f /tmp/slappasswd.ldif
6,导入基本的schema文件。
※导入基本schema文件存放路径为:/etc/openldap/slapd.d/cn=config/cn=schema
查看:
[root@necas-47 cn=config]# ls cn\=schema
[root@necas-47 cn=config]# ls /etc/openldap/schema/
执行:
[root@necas-47 cn=config]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=cosine,cn=schema,cn=config"
[root@necas-47 cn=config]# cd cn\=schema
[root@necas-47 cn=schema]# ls
cn={0}core.ldif cn={1}cosine.ldif
[root@necas-47 cn=schema]# pwd
/etc/openldap/slapd.d/cn=config/cn=schema
[root@necas-47 cn=schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/ppolicy.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=ppolicy,cn=schema,cn=config"
[root@necas-47 cn=schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=nis,cn=schema,cn=config"
[root@necas-47 cn=schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/dyngroup.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=dyngroup,cn=schema,cn=config"
[root@necas-47 cn=schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=inetorgperson,cn=schema,cn=config"
7,修改相关域名。
※其实是修改文件为olcDatabase\=\{2\}hdb.ldif和olcDatabase\=\{1\}monitor.ldif
[root@necas-47 cn=schema]# cd ..
[root@necas-47 cn=config]# ls
cn=schema olcDatabase={0}config.ldif olcDatabase={1}monitor.ldif
cn=schema.ldif olcDatabase={-1}frontend.ldif olcDatabase={2}hdb.ldif
▶事前查看:
[root@necas-47 cn=config]# cat olcDatabase\=\{2\}hdb.ldif
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 b6b7ce6c
dn: olcDatabase={2}hdb
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {2}hdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=my-domain,dc=com
olcRootDN: cn=Manager,dc=my-domain,dc=com
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
structuralObjectClass: olcHdbConfig
entryUUID: d351b79a-fca2-1039-84c7-59681c0b5be4
creatorsName: cn=config
createTimestamp: 20200317135620Z
entryCSN: 20200317135620.775687Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20200317135620Z
[root@necas-47 cn=config]# cat olcDatabase\=\{1\}monitor.ldif
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 05097e61
dn: olcDatabase={1}monitor
objectClass: olcDatabaseConfig
olcDatabase: {1}monitor
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=Manager,dc=my-domain,dc=com" read by * none
structuralObjectClass: olcDatabaseConfig
entryUUID: d351b308-fca2-1039-84c6-59681c0b5be4
creatorsName: cn=config
createTimestamp: 20200317135620Z
entryCSN: 20200317135620.775569Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20200317135620Z
[root@necas-47 cn=config]# vi /tmp/monitor.ldif
▶文件内容:
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.base="cn=Manager,dc=ldap,dc=com" read by * none
[root@necas-47 cn=config]# ldapmodify -Y EXTERNAL -H ldapi:/// -f /tmp/monitor.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={1}monitor,cn=config"
[root@necas-47 cn=config]# vi /tmp/hdb.ldif
▶输入:
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=ldap,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=ldap,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}QGtU8gBpI98gwBhzaLDanpAwWAeV1okQ
[root@necas-47 cn=config]# ldapmodify -Y EXTERNAL -H ldapi:/// -f /tmp/hdb.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
▶再查看:
[root@necas-47 cn=config]# cat olcDatabase\=\{2\}hdb.ldif
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 72276f5e
dn: olcDatabase={2}hdb
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {2}hdb
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
structuralObjectClass: olcHdbConfig
entryUUID: d351b79a-fca2-1039-84c7-59681c0b5be4
creatorsName: cn=config
createTimestamp: 20200317135620Z
olcSuffix: dc=ldap,dc=com
olcRootDN: cn=Manager,dc=ldap,dc=com
olcRootPW:: e1NTSEF9UUd0VThnQnBJOThnd0JoemFMRGFucEF3V0FlVjFva1E=
entryCSN: 20200318025347.916000Z#000000#000#000000
modifiersName: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
modifyTimestamp: 20200318025347Z
[root@necas-47 cn=config]# cat olcDatabase\=\{1\}monitor.ldif
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 c364c9bc
dn: olcDatabase={1}monitor
objectClass: olcDatabaseConfig
olcDatabase: {1}monitor
structuralObjectClass: olcDatabaseConfig
entryUUID: d351b308-fca2-1039-84c6-59681c0b5be4
creatorsName: cn=config
createTimestamp: 20200317135620Z
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=Manager,dc=ldap,dc=com" read by * none
entryCSN: 20200318024501.443289Z#000000#000#000000
modifiersName: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
modifyTimestamp: 20200318024501Z
8,设置组织架构。
[root@necas-47 cn=config]# cat << EOF |ldapadd -x -D cn=Manager,dc=ldap,dc=com -W
dn: dc=ldap,dc=com
objectClass: dcObject
objectClass: organization
dc: ldap
o: ldap.com
dn: ou=People,dc=ldap,dc=com
objectClass: organizationalUnit
objectClass: top
ou: People
dn: ou=Group,dc=ldap,dc=com
objectClass: organizationalUnit
ou: Group
dn: cn=Manager,dc=ldap,dc=com
objectClass: organizationalRole
cn: Manager
dn: cn=Host,ou=Group,dc=ldap,dc=com
objectClass: posixGroup
cn: Host
gidNumber: 1010
EOF
Enter LDAP Password: {输入前面设置的ldap服务密码}
adding new entry "dc=ldap,dc=com"
adding new entry "ou=People,dc=ldap,dc=com"
adding new entry "ou=Group,dc=ldap,dc=com"
adding new entry "cn=Manager,dc=ldap,dc=com"
adding new entry "cn=Host,ou=Group,dc=ldap,dc=com"
9,查看添加的条目
[root@necas-47 cn=config]# vim /etc/openldap/ldap.conf
添加:添加字段BASE和URI。
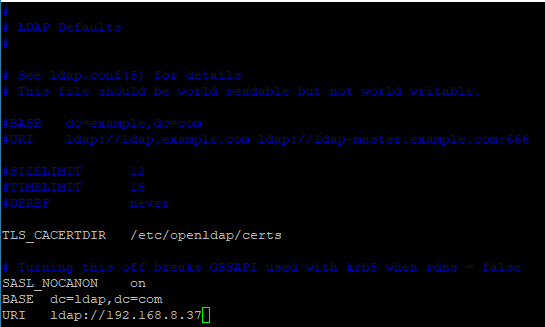
[root@necas-47 cn=config]# ldapsearch -x -LLL
dn: dc=ldap,dc=com
objectClass: dcObject
objectClass: organization
dc: ldap
o: ldap.com
dn: ou=People,dc=ldap,dc=com
objectClass: organizationalUnit
objectClass: top
ou: People
dn: ou=Group,dc=ldap,dc=com
objectClass: organizationalUnit
ou: Group
dn: cn=Manager,dc=ldap,dc=com
objectClass: organizationalRole
cn: Manager
dn: cn=Host,ou=Group,dc=ldap,dc=com
objectClass: posixGroup
cn: Host
gidNumber: 1010
10,添加用户。
[root@necas-47 cn=config]# cat << EOF |ldapadd -x -D cn=Manager,dc=ldap,dc=com -W
dn: uid=user01,ou=People,dc=ldap,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
homeDirectory: /home/user01
userPassword: {SSHA}QGtU8gBpI98gwBhzaLDanpAwWAeV1okQ #创建用户时,可换新的,也可以使用明文密码(未验证)。
loginShell: /bin/bash
cn: user01
uidNumber: 1000 #创建用户,需修改。
gidNumber: 1010 #创建用户,需修改。
sn: System Administrator
mail: user01@gmail.com
mobile: 18919191199
EOF
注意:每行的开头和末尾不能有空格,删除注释时,记得调整。
Enter LDAP Password:{输入前面设置的ldap服务密码}
adding new entry "uid=user01,ou=People,dc=ldap,dc=com"
▶常用操作
1,查看用户列表
ldapsearch -x -b "ou=People,dc=ldap,dc=com"
2,查看组列表
ldapsearch -x -b "ou=People,dc=ldap,dc=com"
3,删除用户
ldapdelete -x -D "cn=Manager,dc=ldap,dc=com" -W "uid=user01,ou=People,dc=ldap,dc=com"
提示:删除用户时,并不会删除同名的组,请记得删除同名组.
4,删除组
ldapdelete -x -D "cn=Manager,dc=ldap,dc=com" -W "cn=组名,ou=People,dc=ldap,dc=com"
例:ldapdelete -x -D "cn=Manager,dc=ldap,dc=com" -W "cn=user01,ou=People,dc=ldap,dc=com"


 浙公网安备 33010602011771号
浙公网安备 33010602011771号