kdc 互信
环境:
29.3.203.53(sysops00065017) 部署KDC Namnode Datanode,KDC负责TESTA.COM域的认证
29.3.203.54(sysops00065018) 部署KDC Namnode Datanode,KDC负责TESTB.COM域的认证
确保两台机器能互相使用主机名ping通
一、
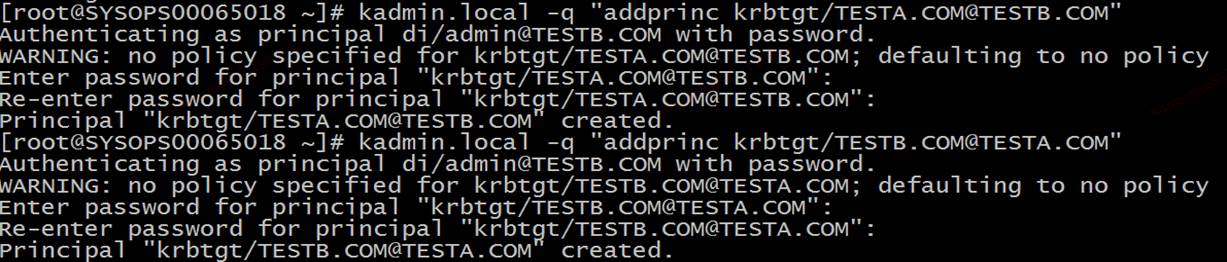
两台kdc都添加krbtgt/TESTA.COM@TESTB.COM和krbtgt/TESTB.COM@TESTA.COM
如果在TESTA.COM访问TESTB.COM上的服务,需要krbtgt/TESTB.COM@TESTA.COM
二、修改krb5.conf(红色为需要修改的地方)
TESTA.COM 29.3.203.53(sysops00065017)
[realms]
TESTA.COM = {
kdc = sysops00065017
admin_server = sysops00065017
master_kdc = sysops00065017
default_domain = .TESTA.COM
}
TESTB.COM = {
kdc = sysops00065018
admin_server = sysops00065018
master_kdc = sysops00065018
default_domain = .TESTB.COM
}
[domain_realm]
.testa.com = TESTA.COM
testa.com = TESTA.COM
.testb.com = TESTB.COM
testb.com = TESTB.COM
sysops00065017 = TESTA.COM
sysops00065018 = TESTB.COM
[capaths]
TESTA.COM = {
TESTB.COM = .
}
TESTB.COM 29.3.203.54(sysops00065018)
[realms]
TESTA.COM = {
kdc = sysops00065017
admin_server = sysops00065017
master_kdc = sysops00065017
default_domain = .TESTA.COM
}
TESTB.COM = {
kdc = sysops00065018
admin_server = sysops00065018
master_kdc = sysops00065018
default_domain = .TESTB.COM
}
[domain_realm]
.testb.com = TESTB.COM
testb.com = TESTB.COM
.testa.com = TESTA.COM
testa.com = TESTA.COM
sysops00065017 = TESTA.COM
sysops00065018 = TESTB.COM
[capaths]
TESTB.COM = {
TESTA.COM = .
}
三、修改core-site.xml(两个域都要配置)
<property>
<name>hadoop.security.auth_to_local</name>
<value>
RULE:[1:$1@$0](^.*@TESTA\.COM$)s/^(.*)@TESTA\.COM$/$1/g
RULE:[2:$1@$0](^.*@TESTA\.COM$)s/^(.*)@TESTA\.COM$/$1/g
RULE:[1:$1@$0](^.*@TESTB\.COM$)s/^(.*)@TESTB\.COM$/$1/g
RULE:[2:$1@$0](^.*@TESTB\.COM$)s/^(.*)@TESTB\.COM$/$1/g
DEFAULT
</value>
</property>
四、修改hdfs-site.xml(两个域都要配置)
<property>
<name>dfs.namenode.kerberos.principal.pattern</name>
<value>*</value>
</property>
五、 重启Namdnode\KDC服务
六、 测试
TESTA上使用hdfs/sysops00065017@TESTA.COM访问两个集群的文件:
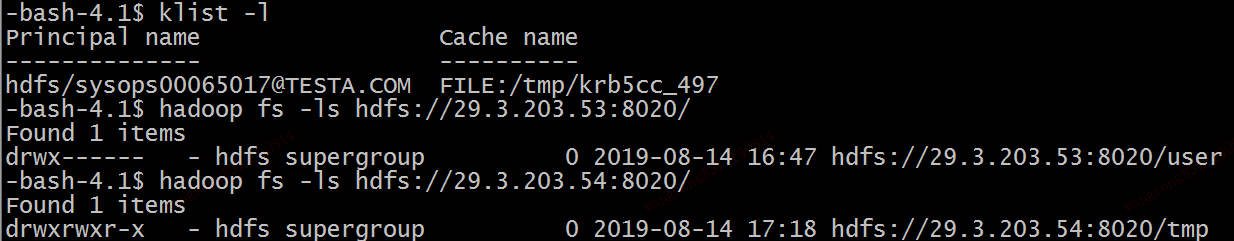
其中TESTA的KDC日志显示
Aug 15 15:49:51 SYSOPS00065017 krb5kdc[9868](info): TGS_REQ (2 etypes {16 23}) 29.3.203.53: ISSUE: authtime 1565855227, etypes {rep=16 tkt=16 ses=16}, hdfs/sysops00065017@TESTA.COM for krbtgt/TESTB.COM@TESTA.COM
TESTB的KDC日志显示
Aug 15 15:49:50 SYSOPS00065018 krb5kdc[26655](info): TGS_REQ (2 etypes {16 23}) 29.3.203.53: ISSUE: authtime 1565855227, etypes {rep=16 tkt=16 ses=16}, hdfs/sysops00065017@TESTA.COM for hdfs/sysops00065018@TESTB.COM
TESTB上使用hdfs/sysops00065018@TESTB.COM访问两个集群的文件:
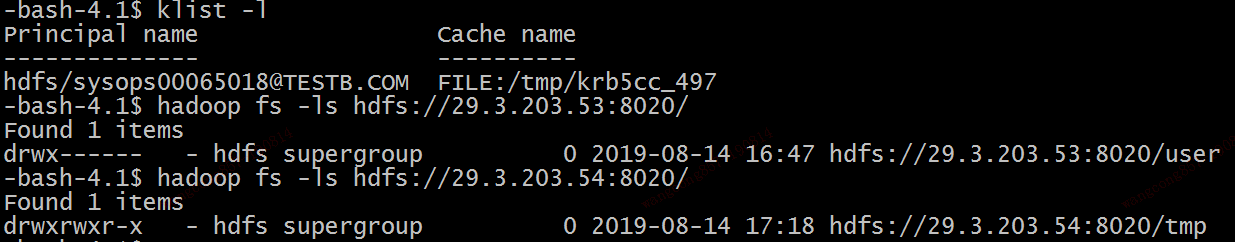
其中TESTA的KDC日志显示
Aug 15 15:51:02 SYSOPS00065017 krb5kdc[9868](info): TGS_REQ (2 etypes {16 23}) 29.3.203.54: ISSUE: authtime 1565774273, etypes {rep=16 tkt=16 ses=16}, hdfs/sysops00065018@TESTB.COM for hdfs/sysops00065017@TESTA.COM
TESTB的KDC日志显示
Aug 15 15:51:01 SYSOPS00065018 krb5kdc[26655](info): TGS_REQ (2 etypes {16 23}) 29.3.203.54: ISSUE: authtime 1565774273, etypes {rep=16 tkt=16 ses=16}, hdfs/sysops00065018@TESTB.COM for krbtgt/TESTA.COM@TESTB.COM

