基于Haproxy+Keepalived实现Haproxy的高可用
一:实验环境
准备4台linux服务器,系统都为CentOS Linux release 7.3.1611 (Core) 版本的虚拟机,IP分别及安装服务为:
192.168.37.101:haproxy+keepalived
192.168.37.102:haproxy+keepalived
192.168.37.103:web1服务器
192.168.37.104:web2服务器
软件:haproxy-1.8.20.tar.gz,keepalived(光盘yum源),httpd(光盘yum源)
二:安装步骤:
1:在101,102机器上安装分别源码安装haproxy服务,如下
#安装相关依赖包 [root@localhost src]# yum install gcc gcc-c++ glibc glibc-devel pcre pcre-devel openssl openssl-devel systemd-devel net-tools vim iotop bc zip unzip zlib-devel lrzsz tree screen lsof tcpdump wget ntpdate -y #上传解压的haproxy源码并进入haproxy源码目录 [root@localhost src]# tar xf haproxy-1.8.20.tar.gz [root@localhost src]# cd haproxy-1.8.20 [root@localhost haproxy-1.8.20]# #编译安装 [root@localhost haproxy-1.8.20]# mkdir /data/haproxy -p [root@localhost haproxy-1.8.20]# make ARCH=x86_64 TARGET=linux2628 USE_PCRE=1 USE_OPENSSL=1 USE_ZLIB=1 USE_SYSTEMD=1 USE_CPU_AFFINITY=1 PREFIX=/data/haproxy #创建服务启动脚本 [root@localhost system]# cat haproxy.service [Unit] Description=HAProxy Load Balancer After=syslog.target network.target [Service] ExecStartPre=/usr/sbin/haproxy -f /etc/haproxy/haproxy.cfg -c -q ExecStart=/usr/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid ExecReload=/bin/kill -USR2 $MAINPID [Install] WantedBy=multi-user.target #创建用户和目录 [root@localhost ~]# mkdir /etc/haproxy [root@localhost ~]# useradd haproxy -s /sbin/nologin [root@localhost ~]# chown haproxy.haproxy /data/haproxy/ /etc/haproxy/ -R #关闭并禁用防火墙及selinux服务 [root@localhost ~]# systemctl stop firewalld [root@localhost ~]# systemctl disable firewalld [root@localhost ~]# vim /etc/selinux/config # This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. SELINUX=disabled #此处禁用 # SELINUXTYPE= can take one of three two values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls - Multi Level Security protection. SELINUXTYPE=targeted
#启动haproxy服务并验证 [root@molson ~]# systemctl enable haproxy Created symlink from /etc/systemd/system/multi-user.target.wants/haproxy.service to /usr/lib/systemd/system/haproxy.service.
#上传写好的配置文件/etc/haproxy/haproxy.cfg global maxconn 100000 chroot /data/haproxy stats socket /data/haproxy/haproxy.sock mode 600 level admin uid 99 gid 99 daemon #nbproc 4 #cpu-map 1 0 #cpu-map 2 1 #cpu-map 3 2 #cpu-map 4 3 pidfile /run/haproxy.pid log 127.0.0.1 local3 info defaults option http-keep-alive option forwardfor maxconn 100000 mode http timeout connect 300000ms timeout client 300000ms timeout server 300000ms listen stats mode http bind 0.0.0.0:9999 stats enable log global stats uri /haproxy-status stats auth haadmin:q1w2e3r4ys
启动的服务见下图:
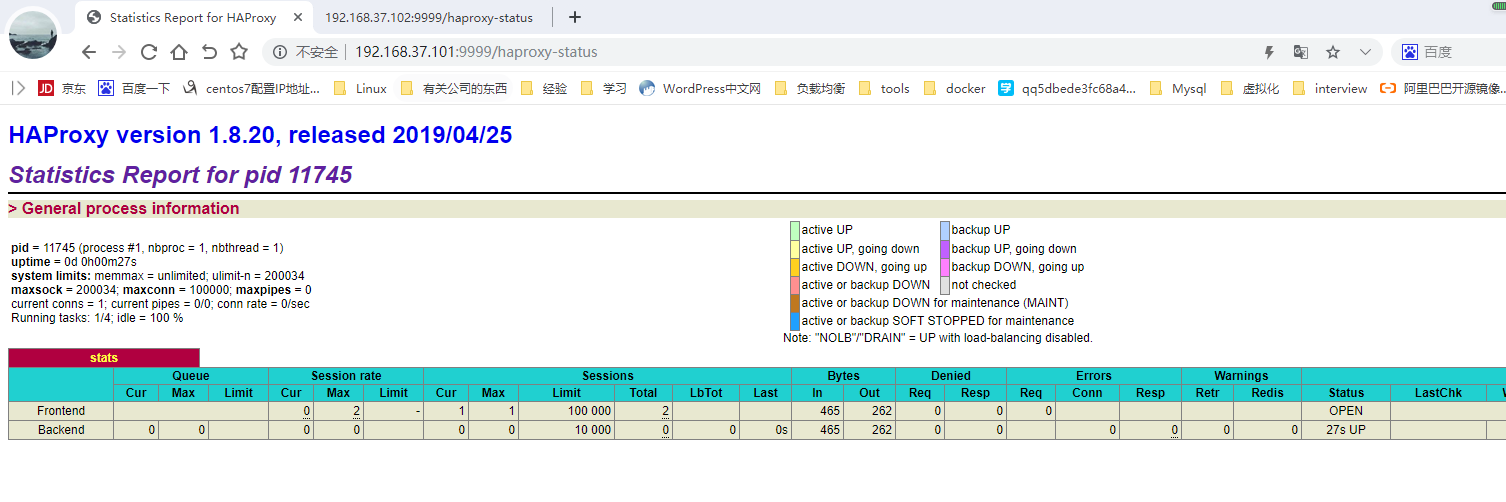
2:在101,102主机上分别通过yun安装keepalived服务,如下
[root@molson ~]# yum install keepalived -y
在101主机上修改keepalived的配置文件,如下
[root@molson ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout 30
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VIP_1 { #实例的名称
state MASTER #主还是备
interface ens33 #网卡名称
virtual_router_id 51
priority 100 #权重
advert_int 1
authentication {
auth_type PASS
auth_pass molson #设置密码
}
virtual_ipaddress {
192.168.37.200 dev ens33 label ens33:0
}
}
102服务器上keepalived配置文件的修改
[root@localhost haproxy]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
acassen@firewall.loc
failover@firewall.loc
sysadmin@firewall.loc
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout 30
router_id LVS_DEVEL
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_iptables
vrrp_garp_interval 0
vrrp_gna_interval 0
}
vrrp_instance VIP_1 {
state BACKUP #备份
interface ens33 #网卡名
virtual_router_id 51
priority 80 #权重
advert_int 1
authentication {
auth_type PASS
auth_pass molson #密码
}
virtual_ipaddress {
192.168.37.200 dev ens33 label ens33:0 #虚拟的IP及网卡
}
}
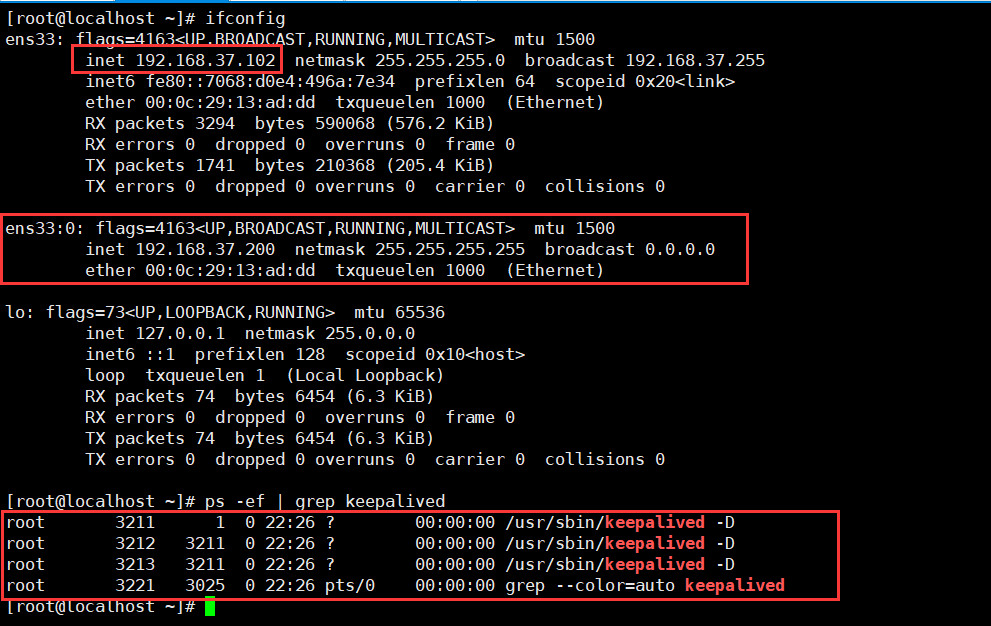
101,102上启动keepalived并验证,如下图
[root@localhost haproxy]# systemctl start keepalived
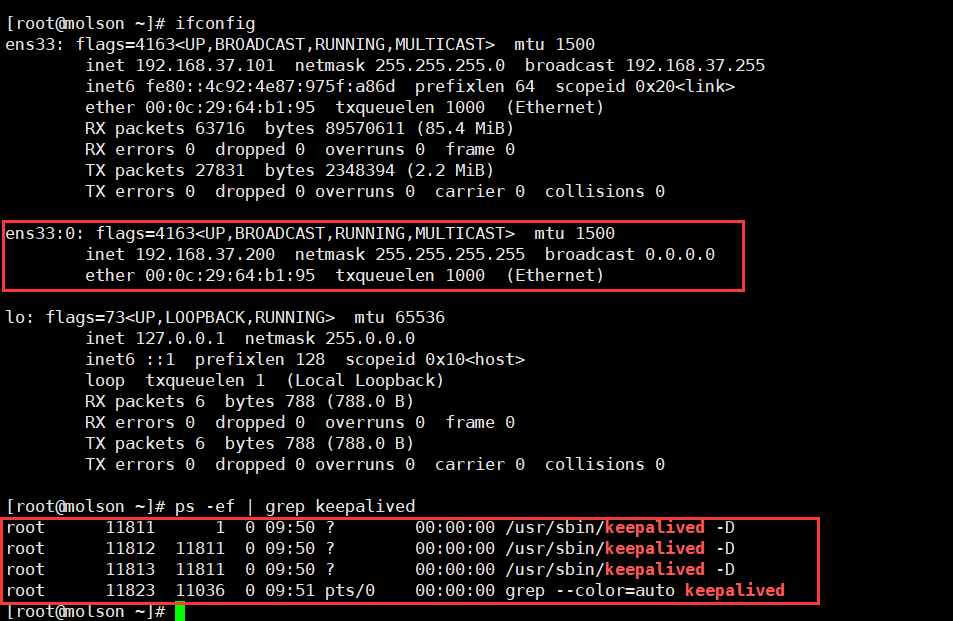
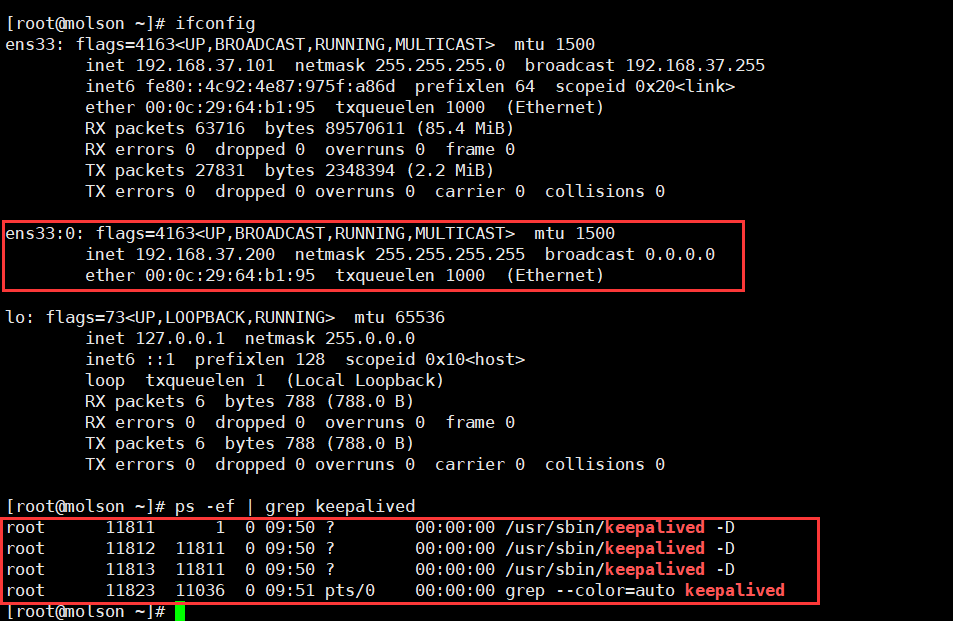
三:两外两台服务器103,104分别安装httpd服务,如下
[root@molson ~]# yum install httpd -y
四:101,102机器修改haproxy的配置文件,进行负载均衡,如下
#在之前的配置文件后增加以下内容就可以
#/etc/haproxy/haproxy.cfg
listen WEB_PORT_80
mode http
bind 192.168.37.200:80 #绑定的虚拟IP及端口
server web1 192.168.37.103:80 check #转发的地址
server web2 192.168.37.104:80 check #转发的地址
五:启动haproxy程序,如下
[root@molson ~]# ss -ntl State Recv-Q Send-Q Local Address:Port LISTEN 0 128 *:9999 LISTEN 0 128 *:22 LISTEN 0 100 127.0.0.1:25 LISTEN 0 128 :::22 LISTEN 0 100 ::1:25
通过上述信息可以看出,端口80没有打开,修改内核参数,如下
[root@molson ~]# vim /etc/sysctl.conf #添加以下两行 net.ipv4.ip_nonlocal_bind = 1 net.ipv4.ip_forward = 1 [root@molson ~]# sysctl -p #使配置生效 #102机器上一样配置
再一次启动haproxy程序,并检查端口,如下
[root@localhost ~]# ss -ntl State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:9999 *:* LISTEN 0 128 192.168.37.200:80 *:* LISTEN 0 128 *:22 *:* LISTEN 0 100 127.0.0.1:25 *:* LISTEN 0 128 :::22 :::* LISTEN 0 100 ::1:25 :::* [root@localhost ~]#
六:验证高可用服务,如下
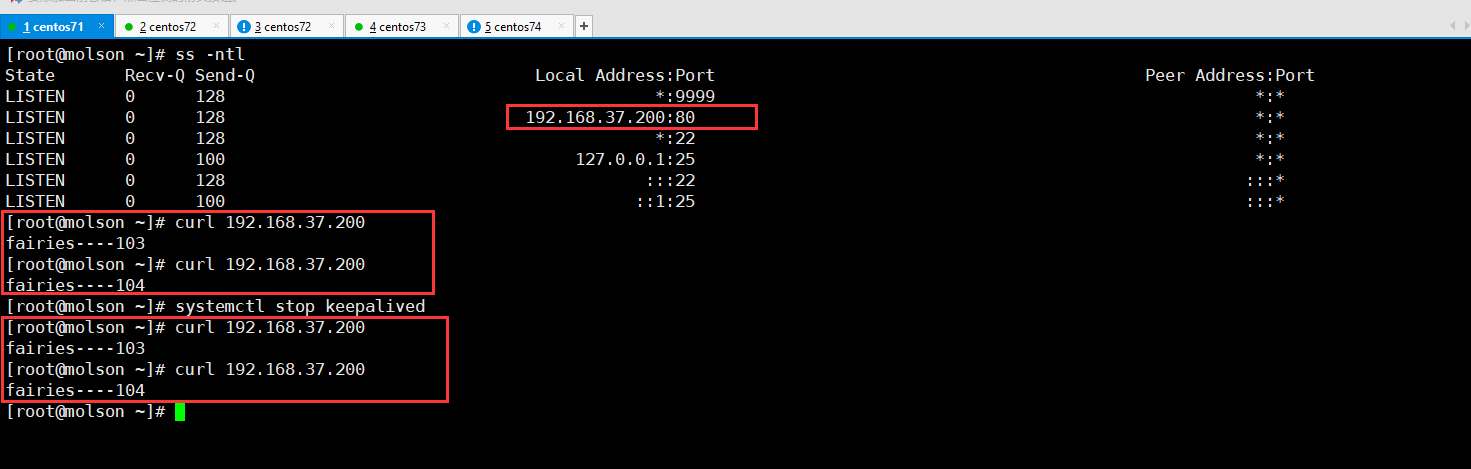
上图为101机器上验证,由上图可知,101和102组成高可以服务,只要其中一台服务停止了,还是可以正常服务的
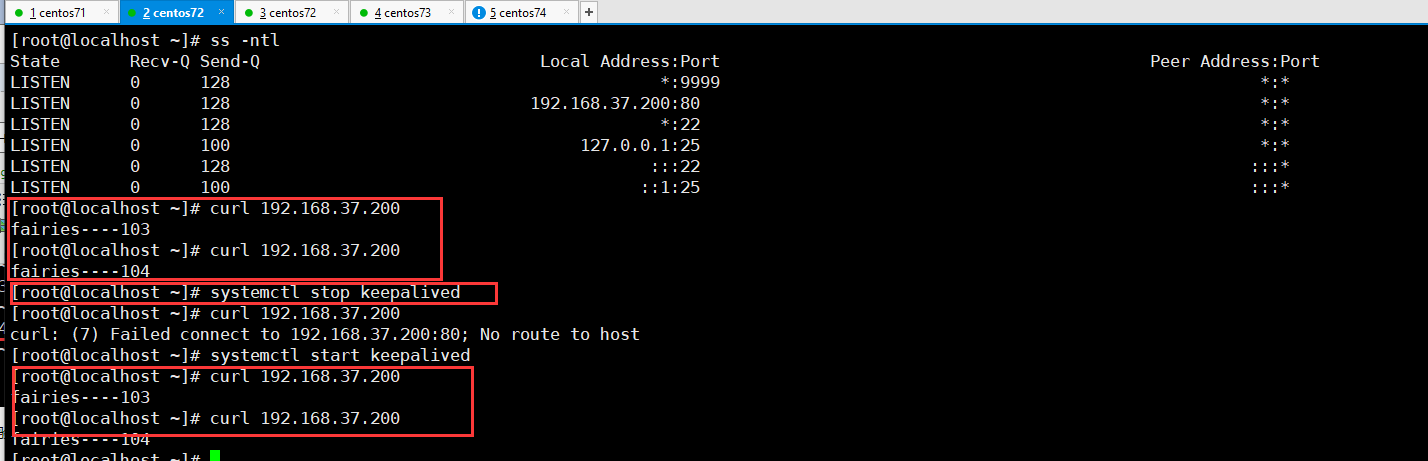
由上图可知,在101机器上keepalived服务停止了,在102机器上还是可以正常服务的,当在102机器上也停止了,服务不可访问,如下
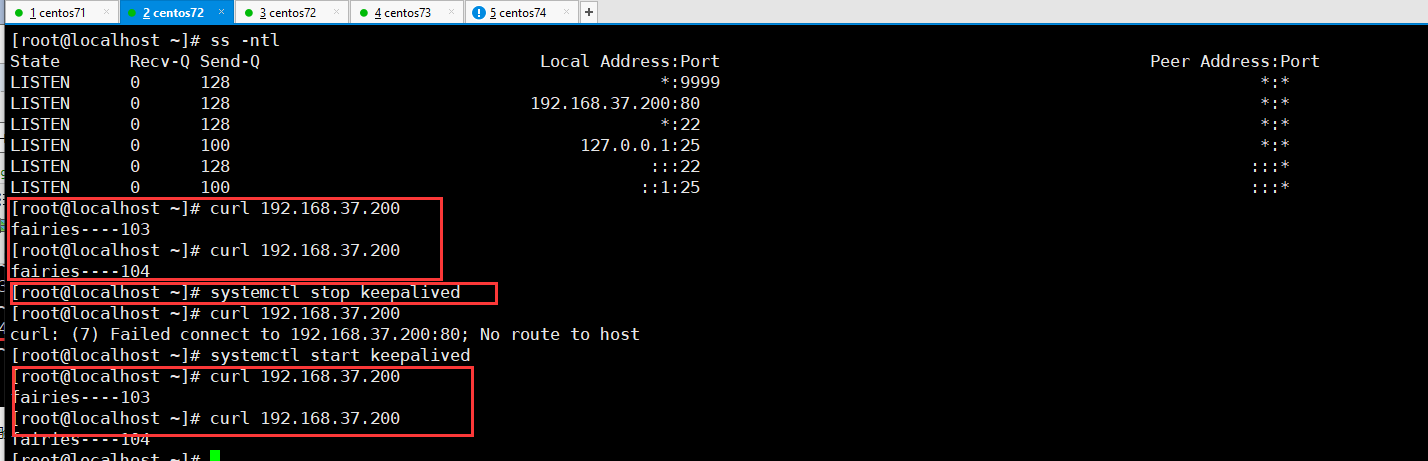
当101和102组成高可用服务的时候,主服务停止工作了,备份服务马上开启工作,见下图日志
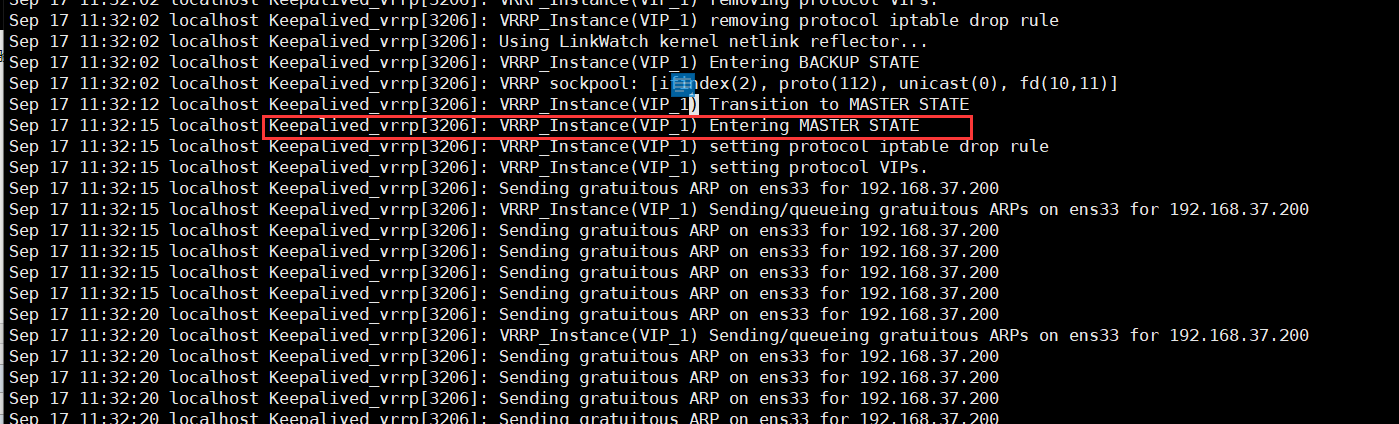
由以上可知,简单的Haproxy+keepalived高可用服务服务搭建成功



 浙公网安备 33010602011771号
浙公网安备 33010602011771号