Udemy AWS SAA - Intro and IAM
How to choose an AWS Region if you need to launch a new app
- Compliance: with data governance and legal requirement, data never leaves a region w/o your explicit permission
- Proximity: to customers, to reduce latency
- Available services: some region doesn't have all services
- Pricing: varies region to region
Availability Zones:
each region has many availability zones, usually 3, min is 2, max is 6
each AZ is 1+ discrete data centers with redundant power, networking and connectivity, they are separate from each other, but connected with high bandwidth, ultra-low latency
AWS Points of Presence (Edge Locations)网点
AWS has Global Services
- ldentity and Access Management (lAM)
- Route 53 (DNS service)
- CloudFront (Content Delivery Network)
- WAF (Web Application Firewall)
Most AWS services are Region-scoped
- Amazon EC2 (Infrastructure as a Service)
- Elastic Beanstalk (Platform as a Service)
- Lambda (Function as a Service)
- Rekognition (Software as a Service)
ldentity and Access Management (lAM)
- Root account created by default, shouldn't be used or shared
- Users are ppl in your org, and can be grouped. After getting a root user, we can create an Admin account, then create users account
- Groups only contain users, not other groups
- An user can belong to multiple groups
- We want the users to use their AWS account
- Permissions: users or groups can be assigned JSON documents called policies to grant their permissions to the AWS services. Please do Least Privilege Principle : don't give more permission than a user needs
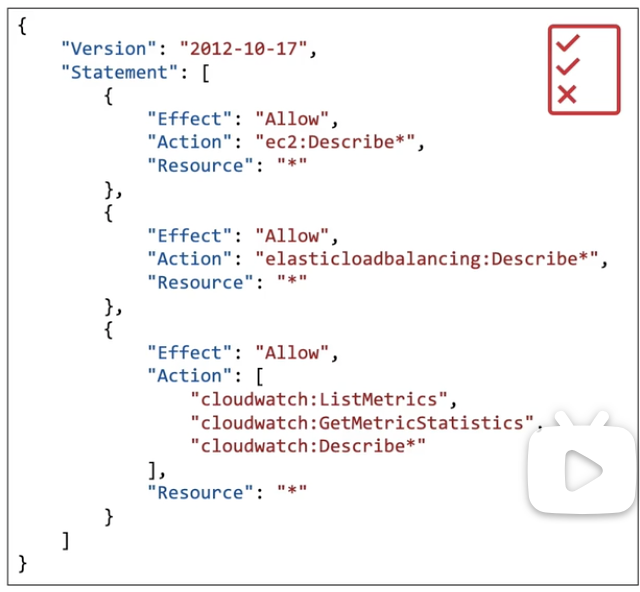
Inline policy: a policy only assigned to one person
IAM Policies Structure
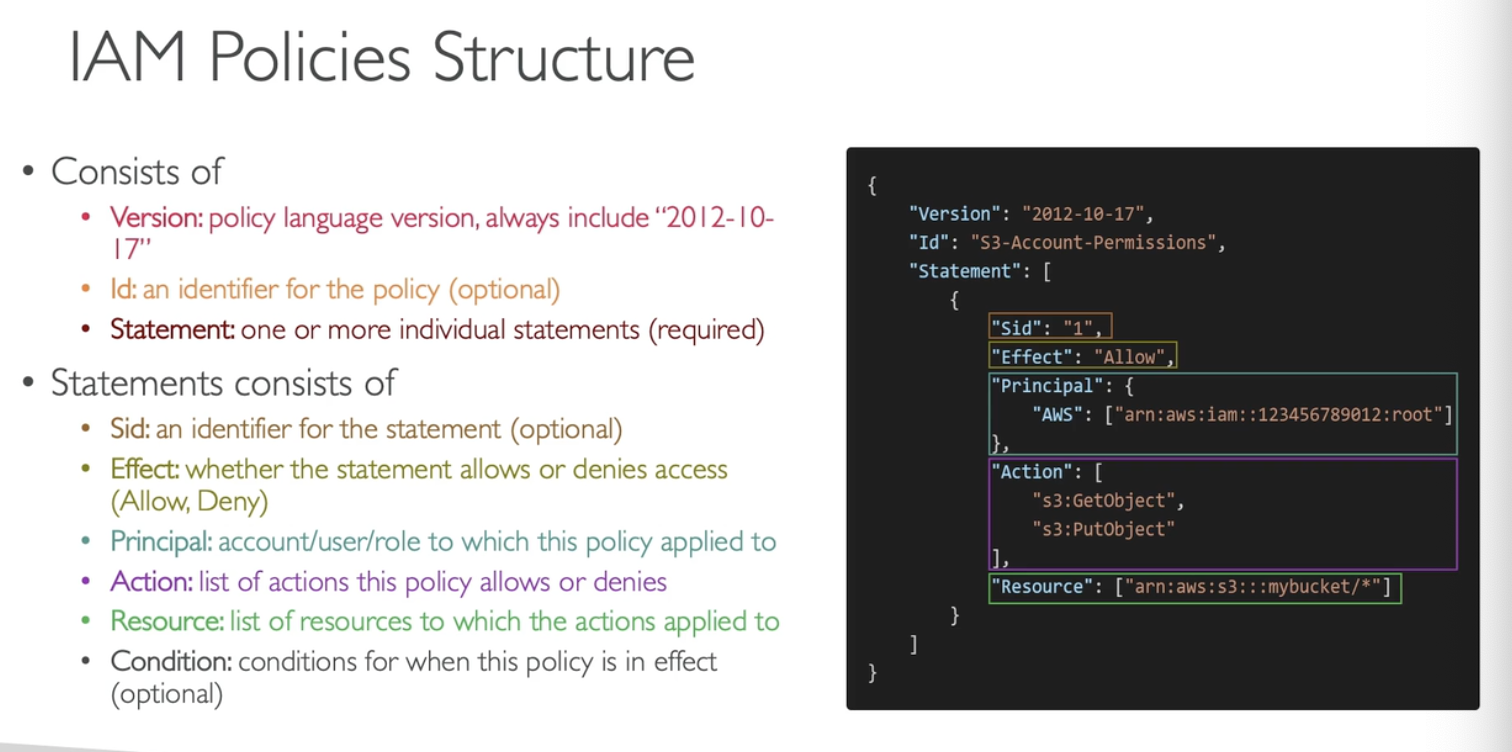
An Example for Permission JSON
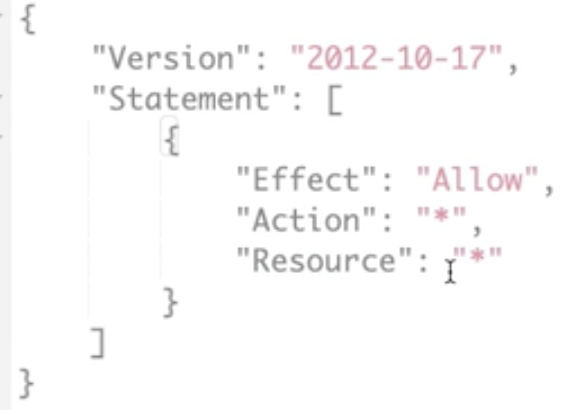
The "*" below means any, it permits any action and any resource
Two Ways to Protect Your AWS Account
Password Policy
- Strong passwords = higher security for your accountIn AWS, you can setup a password policy:
- Set a minimum password lengthRequire specific character types.including uppercase letters
- lowercase letters
- numbers
- non-alphanumeric charactersAllow all lAM users to change their own passwords
- Require users to change their password after some time (password expiration)
- Prevent password re-use
Multi Factor Authentication - MFA
- Users have access to your account and can possibly change configurations or delete resources in your AWS account
- You want to protect your Root Accounts and lAM users
- MFA = password you know + security device you own
- You can use:
- Virtual MFA device: Google Authenticator (Phone only), Authy (multi-device);
- Universal 2nd Factor (U2F) Security Key, ex. YubiKey
- Hardware Key Fob: Gemalto
- Hardware Key Fob for AWS GovCloud(US): SurePassID
How can users access AWS ?
- AWS Management Console (protected by password + MFA)
- AWS Command Line Interface (CLl): protected by access keys. interact with AWS services in your command-line shell
- AWS Software Developer Kit (SDK) - for code: protected by access keys. Language-specific APIs, enable to access and manage AWS services programmatically
Access key ID = username, Secret Access Key = password. So DO NOT SHARE YOUR ACCESS KEY
CloudShell: it's not global, it's like a terminal on a website, can be a substitute for CLI. we have the upload and download function
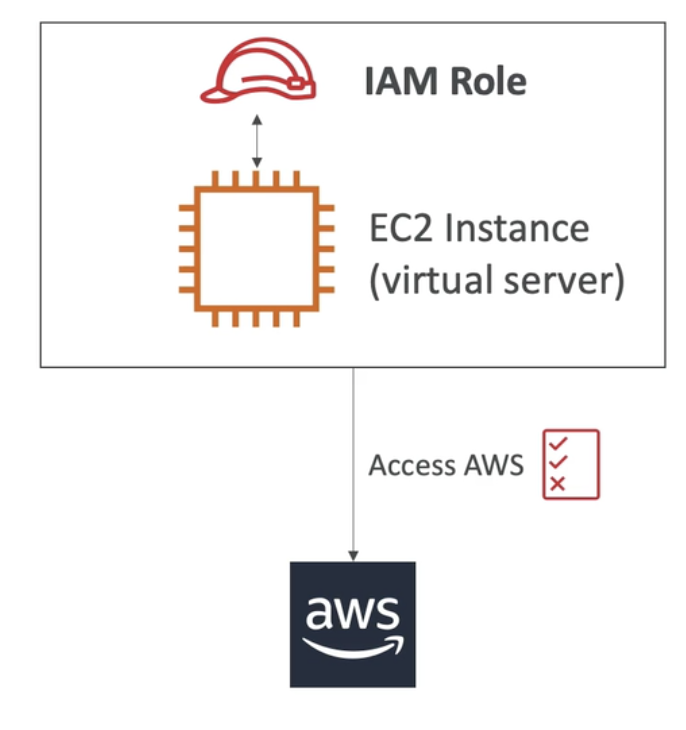
IAM Roles: some AWS service will need to perform actions on your behalf; to do so, we will assign permissions to AWS services w/ IAM Roles. ex. EC2 Instance roles, Lambda Function Roles, Roles for CloudFormation
lAM Security Tools
- lAM Credentials Report (account-level): a report that lists all your account's users and the status of their various credentials, include all accounts' passwords and permissions
- IAM Access Advisor (user-level): Access advisor shows the service permissions granted to a user and when those services were last accessed. You can use this info to revise your policies, maybe they never use this service, then we can remove this permission
IAM Guidelines & Best Practices
- Don't use the root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assign permissions to groups
- Create a strong password policy
- Use and enforce the use of Multi Factor Authentication (MFA)
- Create and use Roles for giving permissions to AWS services
- Use Access Keys for Programmatic Access (CLl / SDK)
- Audit permissions of your account with the lAM Credentials Report
AWS Budget Setup




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 三行代码完成国际化适配,妙~啊~
· .NET Core 中如何实现缓存的预热?