ELK之elasticsearch6安装认证模块search guard
参考:https://www.cnblogs.com/marility/p/9392645.html
1,安装环境及软件版本
| 程序 | 版本 | 安装方式 |
| elasticsearch | 6.3.1 | rpm |
| kibana | 6.3.1 | rpm |
| java | 1.8.0 | tar |
2,search guard安装
2.1在elasticsearch安装
1 2 | cd /usr/share/elasticsearch/bin/./elasticsearch-plugin install com.floragunn:search-guard-6:6.3.1-24.0 |
安装的版本查看


查看

进行demo模式安装
1 2 | cd /usr/share/elasticsearch/plugins/search-guard-6/toolsbash install_demo_configuration.sh |
安说明输入3个y确认

重启elasticsearch
1 | systemctl restart elasticsearch |
web访问测试安装是否成功
1 | https://172.16.20.12:9200/_searchguard/authinfo |
注意是https而不是http
输入默认用户名和密码admin

打印admin的json格式则代表安装成功

怎么取消search guard安装
1 2 3 4 | 查看安装的插件 /usr/share/elasticsearch/bin/elasticsearch-plugin list移除安装的插件 /usr/share/elasticsearch/bin/elasticsearch-plugin remove search-guard-6 |
把配置修改为之前的即可
此时打开kibana出现输入用户名密码提示但是无法输入

2.2在kibana安装
首先停止kibana
1 | systemctl stop kibana |
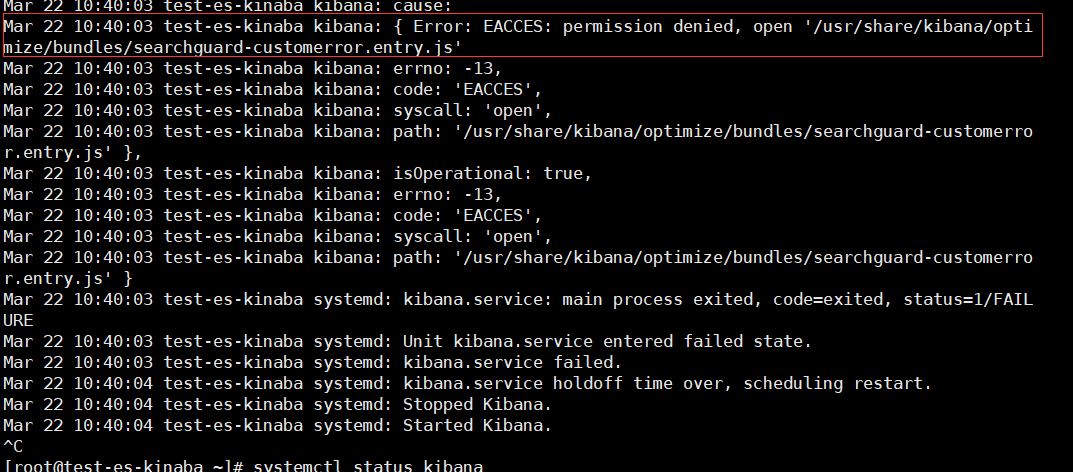
PS:如果不停止kibana直接安装,启动会报错 报错日志 /var/log/meaasge
如果启动报错了,可以删除kibana插件重新安装
1 | ./kibana-plugin remove searchguard |
1 2 | cd /usr/share/kibana/bin/./kibana-plugin install https://search.maven.org/remotecontent?filepath=com/floragunn/search-guard-kibana-plugin/6.3.1-14-beta-1/search-guard-kibana-plugin-6.3.1-14-beta-1.zip |
需要安装版本查看

修改kibana配置文件 /etc/kibana/kibana.yml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | server.port: 5601server.host: "172.16.20.12"#server.host: "0.0.0.0"server.name: "test-es-kibana"elasticsearch.url: "https://172.16.20.12:9200"kibana.index: ".kibana"elasticsearch.username: "kibanaserver"elasticsearch.password: "kibanaserver"elasticsearch.ssl.verificationMode: noneelasticsearch.requestHeadersWhitelist: [ "Authorization", "sgtenant" ]xpack.monitoring.enabled: falsexpack.graph.enabled: falsexpack.ml.enabled: falsexpack.watcher.enabled: falsexpack.security.enabled: false |
PS:elasticsearch配置为https
启动kibana通过5601端口访问,输入用户名和密码均为admin

左侧菜单栏出现search guard代表安装成功

PS:版本6.5.4配置kibana后启动报错
1 | Browserslist: caniuse-lite is outdated. Please run next command `npm update caniuse-lite browserslis |
原因为node版本低4版本,升级为8版本重启kibana即可
添加只读用户guest




使用用户guest登录只能读无法编辑

配置logstash输入至elasticsearch
1 | /etc/logstash/conf.d/logstash.conf |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | input { stdin{} }output { elasticsearch { hosts => [ "172.16.20.12:9200" ] ssl => true ssl_certificate_verification => false user => admin password => admin index => "logstash_%{+YYYY.MM.dd}" } stdout { codec => rubydebug }} |
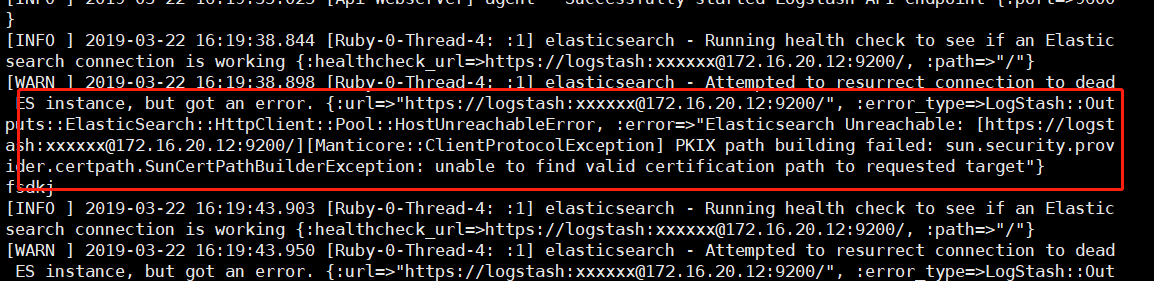
PS:测试标准输出至elasticsearch并输出至屏幕
需要增加这两个配置 否则启动报错
1 2 | ssl => true ssl_certificate_verification => false |
1 |
启动
1 | /usr/share/logstash/bin/logstash -f /etc/logstash/conf.d/logstash.conf |
以上为自动生成证书,下面使用在线生成证书安装search guard
在线生成证书,https://search-guard.com/tls-certificate-generator/

登录刚刚输入的邮箱下载证书,上传至服务器的文件夹/tmp解压缩并把解压后的所有文件放置在文件夹/etc/elsaticsearch/key
1 2 3 4 5 | cd /tmprztar -xf search-guard-certificates-8d1c8141-5f8b-4932-b7e2-a7109c400330.tar.gz.tarcd /tmp/search-guard-certificatesmv * /etc/elasticsearch/key/ |
证书文件目录结构如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 | [root@prd-elk-logstash-02 key]# tree.├── chain-ca.pem├── client-certificates│ ├── CN=demouser.all.pem│ ├── CN=demouser.crtfull.pem│ ├── CN=demouser.crt.pem│ ├── CN=demouser.csr│ ├── CN=demouser.key.pem│ ├── CN=demouser.key.pkcs12│ ├── CN=demouser-keystore.jks│ ├── CN=demouser-keystore.p12│ ├── CN=demouser-signed.pem│ ├── CN=sgadmin.all.pem│ ├── CN=sgadmin.crtfull.pem│ ├── CN=sgadmin.crt.pem│ ├── CN=sgadmin.csr│ ├── CN=sgadmin.key.pem│ ├── CN=sgadmin.key.pkcs12│ ├── CN=sgadmin-keystore.jks│ ├── CN=sgadmin-keystore.p12│ └── CN=sgadmin-signed.pem├── node-certificates│ ├── CN=IP-172.16.90.24.crtfull.pem│ ├── CN=IP-172.16.90.24.csr│ ├── CN=IP-172.16.90.24.key.pem│ ├── CN=IP-172.16.90.24.key.pkcs12│ ├── CN=IP-172.16.90.24-keystore.jks│ ├── CN=IP-172.16.90.24-keystore.p12│ └── CN=IP-172.16.90.24-signed.pem├── README.txt├── root-ca│ ├── root-ca.crt│ ├── root-ca.key│ └── root-ca.pem├── root-ca.pem├── signing-ca│ ├── signing-ca.crt│ ├── signing-ca.key│ └── signing-ca.pem├── truststore.jks└── truststore.p124 directories, 36 files |
安装elsticsearch 插件
1 2 | cd /usr/share/elasticsearch/bin/./elasticsearch-plugin install com.floragunn:search-guard-6:6.5.4-24.2 |
以上为在线下载安装,也可以下载好文件使用以下命令安装
1 | /usr/share/elasticsearch/bin/elasticsearch-plugin install file:///nas/nas/softs/elk/6.6.2/search-guard-6-6.6.2-24.2.zip |
安装版本查看
配置elasticsearch支持search gurad
配置文件/etc/elasticsearch/elasticsearch.yml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 | cluster.name: hopesz-esnode.name: prd-elk-logstash-02path.data: /data/es-datapath.logs: /var/log/elasticsearchbootstrap.memory_lock: falsenetwork.host: 0.0.0.0http.port: 9200#集群个节点IP地址,也可以使用els、els.shuaiguoxia.com等名称,需要各节点能够解析#discovery.zen.ping.unicast.hosts: ["172.16.90.24", "172.16.30.55"]#集群节点数#discovery.zen.minimum_master_nodes: 2http.cors.enabled: truehttp.cors.allow-origin: "*"#search guard配置开始#证书可以在key目录下找到searchguard.ssl.transport.pemcert_filepath: key/node-certificates/CN=IP-172.16.90.24.crtfull.pemsearchguard.ssl.transport.pemkey_filepath: key/node-certificates/CN=IP-172.16.90.24.key.pem#密码可以在key下README.txt找到searchguard.ssl.transport.pemkey_password: 5ea2206b9b1e041bf052searchguard.ssl.transport.pemtrustedcas_filepath: key/chain-ca.pemsearchguard.ssl.transport.enforce_hostname_verification: falsesearchguard.ssl.http.enabled: truesearchguard.ssl.http.pemcert_filepath: key/node-certificates/CN=IP-172.16.90.24.crtfull.pemsearchguard.ssl.http.pemkey_filepath: key/node-certificates/CN=IP-172.16.90.24.key.pemsearchguard.ssl.http.pemkey_password: 5ea2206b9b1e041bf052searchguard.ssl.http.pemtrustedcas_filepath: key/chain-ca.pemsearchguard.authcz.admin_dn: - CN=sgadminsearchguard.audit.type: internal_elasticsearchsearchguard.enable_snapshot_restore_privilege: truesearchguard.check_snapshot_restore_write_privileges: truesearchguard.restapi.roles_enabled: ["sg_all_access"]cluster.routing.allocation.disk.threshold_enabled: falsenode.max_local_storage_nodes: 3xpack.security.enabled: false#search guard配置结束 |
注意:这里配置的节点密码在README.txt尾部,每一个node对应的密码不同
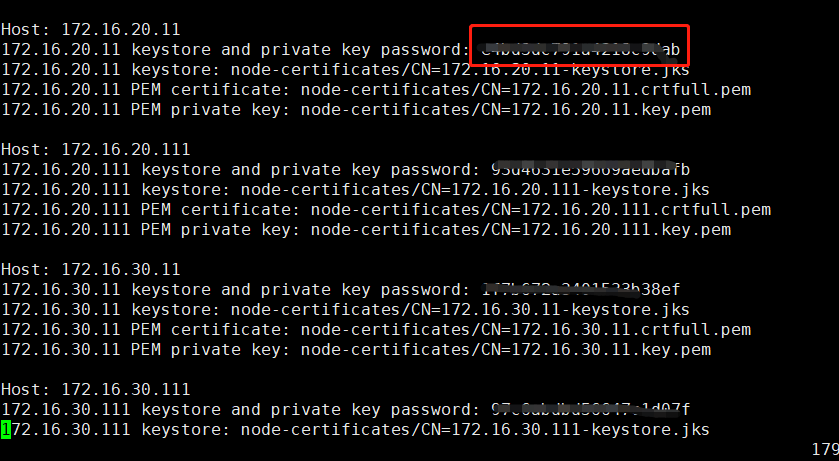
重启elasticsearch报错
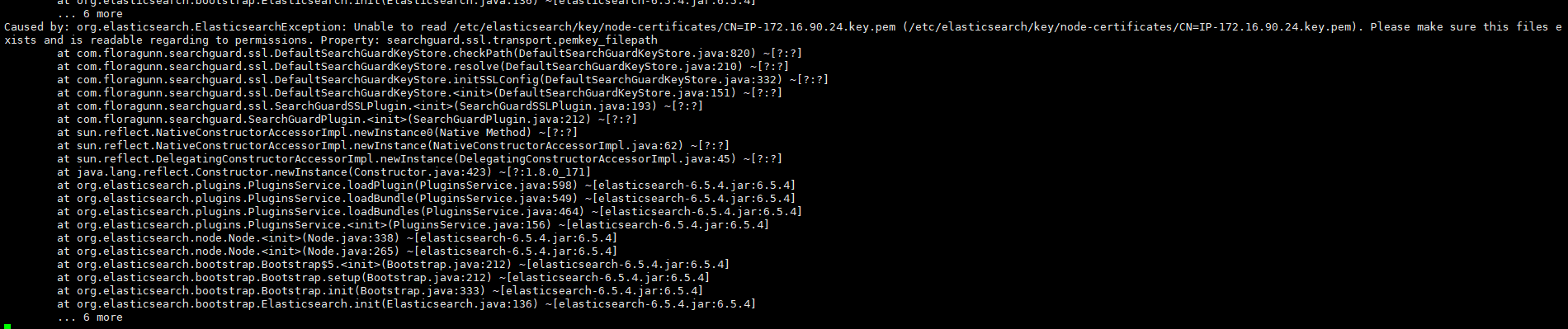
首先检查文件是否存在,如存在则设置权限组为elasticsearch
1 | chown -R elasticsearch.elasticsearch key/ |
启动报错

原因:有志气demo安装的证书需要删除 路径为/etc/elasticsearch
1 2 3 4 5 | rm -rf kirk-key.pem rm -rf kirk.pem rm -rf esnode.pem rm -rf esnode-key.pem rm -rf root-ca.pem |
验证是否安装成功,web页面访问输入用户名密码admin admin
1 | https://172.16.90.24:9200/_searchguard/authinfo |

设置权限因子
权限因子密码也可以在README.txt找到

1 2 3 4 | cd /etc/elasticsearch/key/cp root-ca.pem client-certificates/CN\=sgadmin.key.pem client-certificates/CN\=sgadmin.crtfull.pem /usr/share/elasticsearch/plugins/search-guard-6/tools/cd /usr/share/elasticsearch/plugins/search-guard-6/tools/ ./sgadmin.sh -cacert root-ca.pem -cert CN=sgadmin.crtfull.pem -key CN=sgadmin.key.pem -keypass a756a037271c299fe817 -nhnv -icl -cd ../sgconfig/ -nhnv -icl -cd ../sgconfig/ |

执行如果报错

修改elaticsearch.yml
1 | network.host: 0.0.0.0 |
初始化搜索保护配置
1 2 3 4 5 | cd /etc/elasticsearch/key/cp truststore.jks /usr/share/elasticsearch/plugins/search-guard-6/tools/cp client-certificates/CN\=sgadmin-keystore.jks /usr/share/elasticsearch/plugins/search-guard-6/tools/cd /usr/share/elasticsearch/plugins/search-guard-6/tools/./sgadmin.sh -ts truststore.jks -tspass e0c2b67ecfc6dad6bc42 -ks CN=sgadmin-keystore.jks -kspass 4abdecb00e4d4891761a -nhnv -icl -cd ../sgconfig/ |

注意:以上设置权限因子及初始化搜索保护命令均在README.txt内
安装kibana控件(需要先停止kibana)
1 2 | cd /usr/share/kibana/bin/./kibana-plugin install https://search.maven.org/remotecontent?filepath=com/floragunn/search-guard-kibana-plugin/6.5.4-18/search-guard-kibana-plugin-6.5.4-18.zip |
安装版本查看
修改kibana配置文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | server.port: 5601server.host: "172.16.90.24"server.name: "prd-elk-logstash-02"#配置为httpselasticsearch.url: "https://172.16.90.24:9200"kibana.index: ".kibana"elasticsearch.username: "kibanaserver"elasticsearch.password: "kibanaserver"elasticsearch.ssl.verificationMode: noneelasticsearch.requestHeadersWhitelist: [ "Authorization", "sgtenant" ]xpack.monitoring.enabled: falsexpack.graph.enabled: falsexpack.ml.enabled: falsexpack.watcher.enabled: falsexpack.security.enabled: false |
启动kibana web页面访问需要输入用户名密码admim即可
配置logstash访问,不同于demo安装的配置需要在logstash配置文件配置如下配置output
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | output{ if "nginx-prod-log" in [type] { elasticsearch{ hosts => ["172.16.90.24:9200"] index => "nginx-prod-log-%{+YYYY.MM}" ssl => true ssl_certificate_verification => true truststore => "/etc/elasticsearch/key/truststore.jks" truststore_password => "cad3511c129704894bfc" user => "admin" password => "admin" } #stdout{ # codec => rubydebug #} } |
增加以下配置

PS:truststore密码同样在README.txt可以找到
truststore密码需要引号 用户名和密码也需要加引号 否则无法启动logstash
用户名和密码没有加引号报错信息为 ConfigurationError






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· AI编程工具终极对决:字节Trae VS Cursor,谁才是开发者新宠?
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
2018-03-22 Zabbix监控Windows主机