流量取证-流量中提取文件
以前整理的一些东西,拿出来做备忘
PCAP 报文就是抓取实际在网络中传输的图片,视频等数据,然后以PCAP 格式存储形成的文件。工作中对离线的数据包进行回溯分析,有时会遇到将 PCAP 中的码流还原成相应的图片、视频、邮件等原有格式的需求。
从流量中取证文件大部分情况下是为了提取流量中的可执行程序。
1、 tcpxtract
安装:
apt-get install tcpxtract
http://www.rpmfind.net/linux/rpm2html/search.php?query=tcpxtract # 下载对应版本
查看帮助:
root@kali:~# tcpxtract -h
Usage: tcpxtract [OPTIONS] [[-d
Valid options include:
--file, -f
--device, -d
--config, -c
--output, -o
--version, -v display the version number of this program
--help, -h display this lovely screen
下载 pcap 流量包:
wget http://forensicscontest.com/contest01/evidence01.pcap
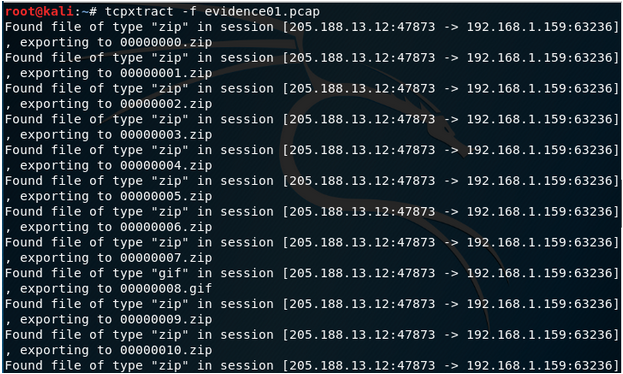
查看要恢复的文件:
tcpxtract -f evidence01.pcap
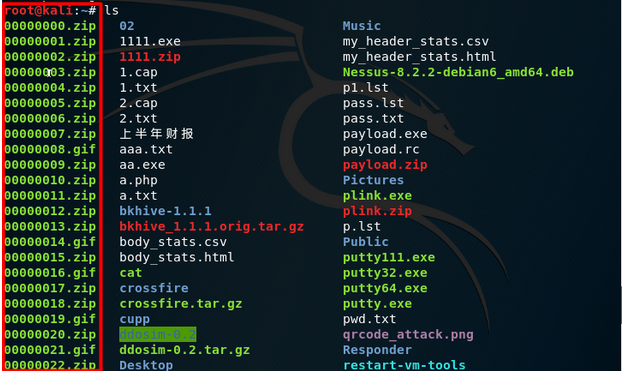
查看恢复后的文件
打开文件:
leafpad 00000042.html

2、 NetworkMiner
安装 NetworkMiner:
从 http://sourceforge.net/projects/networkminer/files/latest/download 下载
或者
https://nchc.dl.sourceforge.net/project/networkminer/networkminer/NetworkMiner-1.6.1/NetworkMiner_1-6-1.zip
打开 PCAP 文件
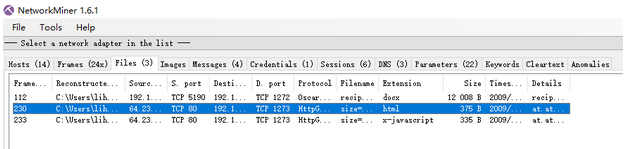
查看提取出来的文件
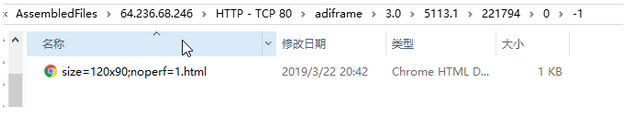
3、wireshark 还原文件
查看帮助
root@kali:~# wireshark -h
Wireshark 2.6.6 (Git v2.6.6 packaged as 2.6.6-1)
Interactively dump and analyze network traffic.
See https://www.wireshark.org for more information.
Usage: wireshark [options] ... [
Capture interface:
-i
-f
-s
-p don't capture in promiscuous mode
-k start capturing immediately (def: do nothing)
-S update packet display when new packets are captured
-l turn on automatic scrolling while -S is in use
-I capture in monitor mode, if available
-B
-y link layer type (def: first appropriate)
--time-stamp-type
-D print list of interfaces and exit
-L print list of link-layer types of iface and exit
--list-time-stamp-types print list of timestamp types for iface and exit
Capture stop conditions:
-c
-a
filesize:NUM - stop this file after NUM KB
files:NUM - stop after NUM files
Capture output:
-b
filesize:NUM - switch to next file after NUM KB
files:NUM - ringbuffer: replace after NUM files
Input file:
-r
Processing:
-R
-n disable all name resolutions (def: all enabled)
-N
-d <layer_type>
"Decode As", see the man page for details
Example: tcp.port
--enable-protocol <proto_name>
enable dissection of proto_name
--disable-protocol <proto_name>
disable dissection of proto_name
--enable-heuristic <short_name>
enable dissection of heuristic protocol
--disable-heuristic <short_name>
disable dissection of heuristic protocol
User interface:
-C
-Y
-g
-J
filter
-j search backwards for a matching packet after "-J"
-m set the font name used for most text
-t a|ad|d|dd|e|r|u|ud output format of time stamps (def: r: rel. to first)
-u s|hms output format of seconds (def: s: seconds)
-X
-z
Output:
-w <outfile|-> set the output filename (or '-' for stdout)
Miscellaneous:
-h display this help and exit
-v display version info and exit
-P
persdata:path - personal data files
-o
-K
--display=DISPLAY X display to use
--fullscreen start Wireshark in full screen
打开pcap文件:
wireshark evidence01.pcap
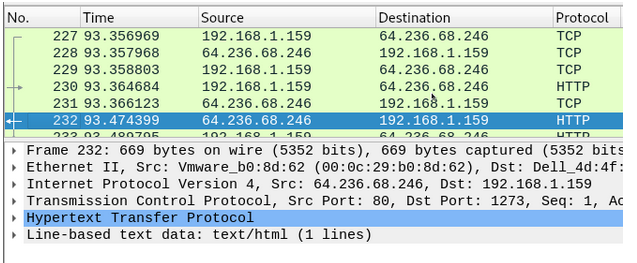
查看还原文件:
文件--》导出对象--》HTTP
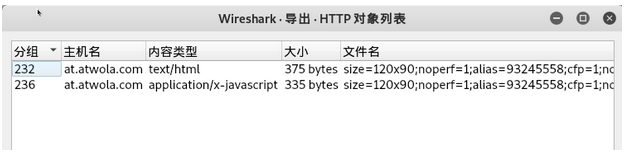
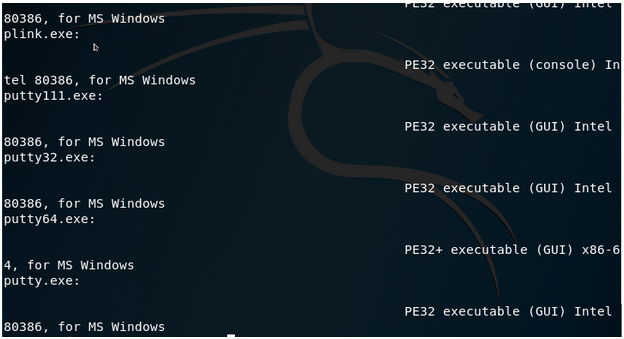
查看PE文件
file * | grep PE
- foremost
kali 2.0 默认安装
查看帮助
root@kali:~# foremost -h
foremost version 1.5.7 by Jesse Kornblum, Kris Kendall, and Nick Mikus.
$ foremost [-v|-V|-h|-T|-Q|-q|-a|-w-d] [-t
[-b
-V - display copyright information and exit
-t - specify file type. (-t jpeg,pdf ...)
-d - turn on indirect block detection (for UNIX file-systems)
-i - specify input file (default is stdin)
-a - Write all headers, perform no error detection (corrupted files)
-w - Only write the audit file, do not write any detected files to the disk
-o - set output directory (defaults to output)
-c - set configuration file to use (defaults to foremost.conf)
-q - enables quick mode. Search are performed on 512 byte boundaries.
-Q - enables quiet mode. Suppress output messages.
-v - verbose mode. Logs all messages to screen
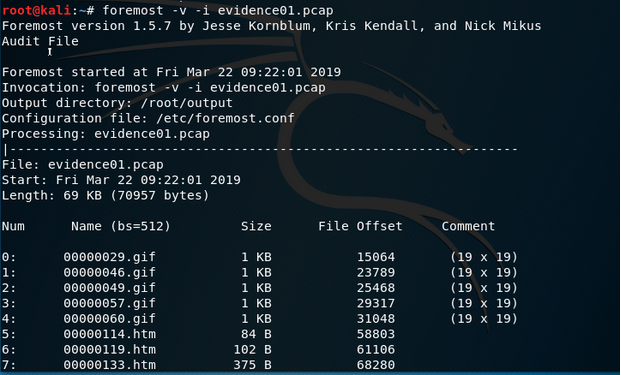
还原文件
foremost -v -i evidence01.pcap
5、Chaosreader
下载 chaosreader
wget https://github.com/brendangregg/Chaosreader/archive/master.zip
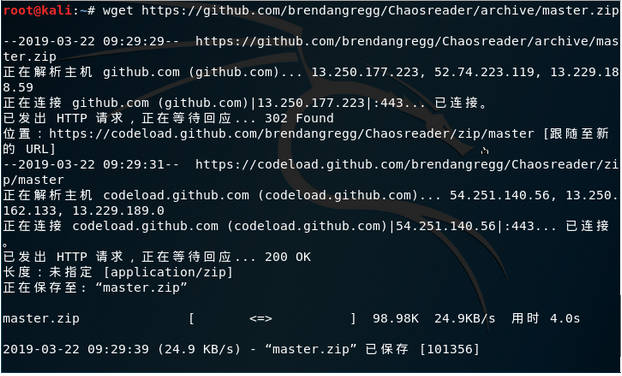
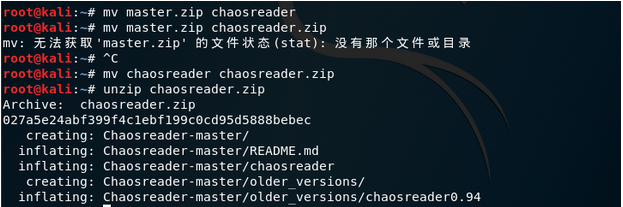
mv master.zip chaosreader.zip
unzip chaosreader.zip
还原文件:
root@kali:~# cd Chaosreader-master
root@kali:~/Chaosreader-master# ls
chaosreader older_versions README.md
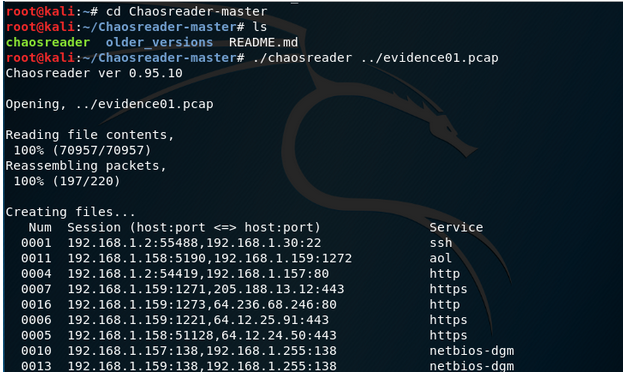
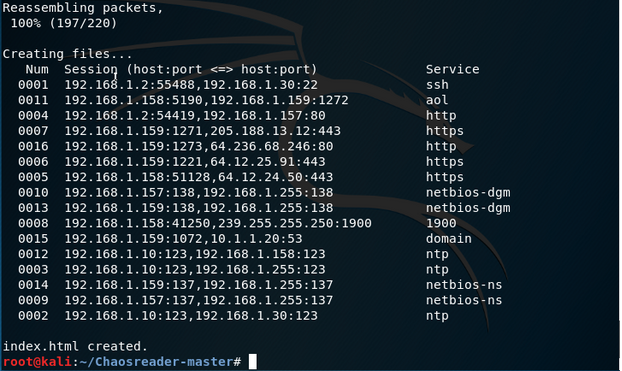
查看PE文件:
file * | grep PE
参考文档
http://blog.sina.com.cn/s/blog_e8e60bc00102vfd9.html
http://www.behindthefirewalls.com/2014/01/extracting-files-from-network-traffic-pcap.html
http://www.blackbytes.info/2012/01/four-ways-to-extract-files-from-pcaps/




